January 11, 2019
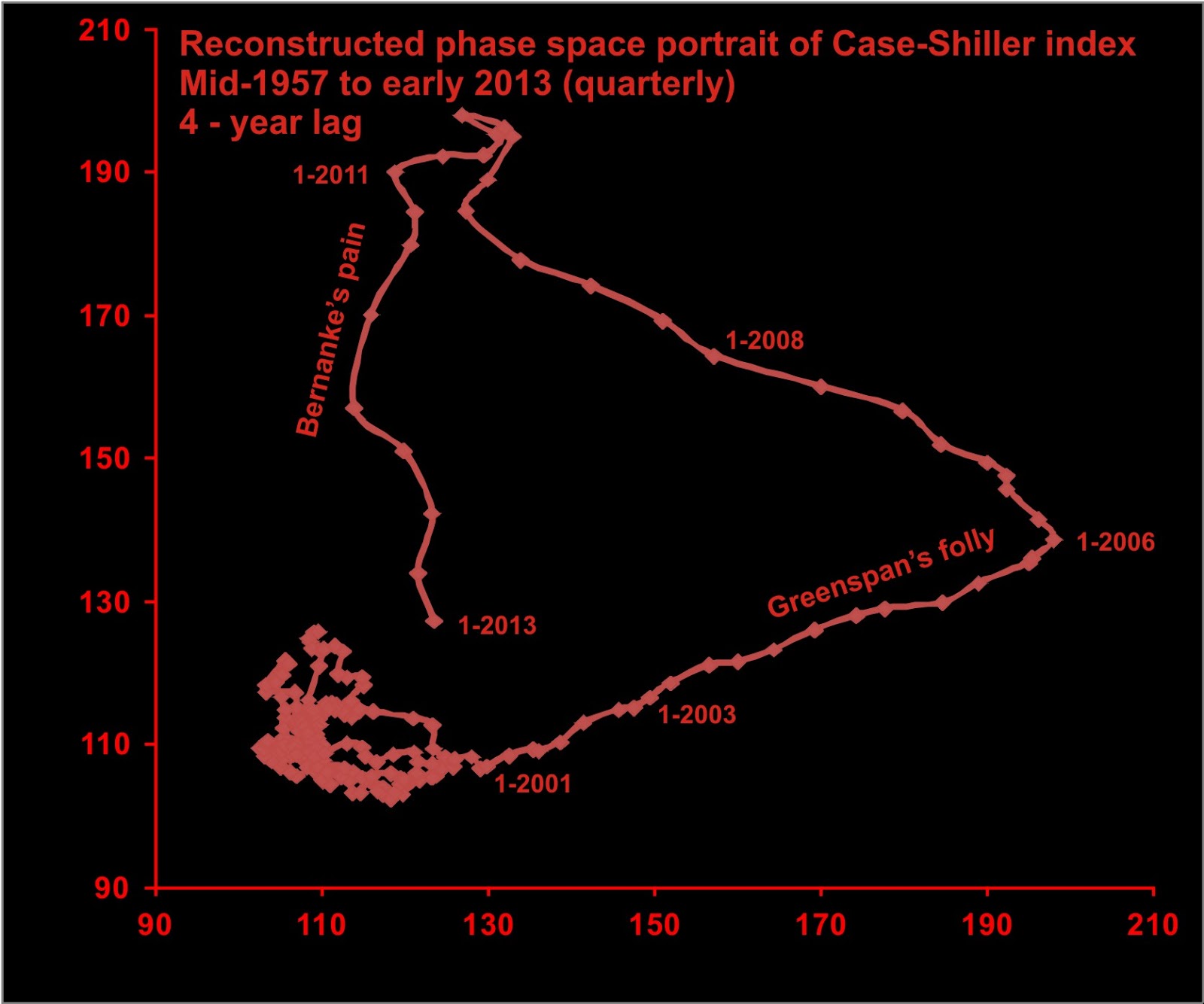
Gresham's Law thesis is back - Malware bid to oust honest miners in Monero
7 years after we called the cancer that is criminal activity in Bitcoin-like cryptocurrencies, here comes a report that suggests that 4.3% of Monero mining is siphoned off by criminals.
A First Look at the Crypto-Mining Malware
Ecosystem: A Decade of Unrestricted Wealth
Sergio Pastrana
Universidad Carlos III de Madrid*
spastran@inf.uc3m.esGuillermo Suarez-Tangil
King’s College London
guillermo.suarez-tangil@kcl.ac.ukAbstract—Illicit crypto-mining leverages resources stolen from victims to mine cryptocurrencies on behalf of criminals. While recent works have analyzed one side of this threat, i.e.: web-browser cryptojacking, only white papers and commercial reports have partially covered binary-based crypto-mining malware. In this paper, we conduct the largest measurement of crypto-mining malware to date, analyzing approximately 4.4 million malware samples (1 million malicious miners), over a period of twelve years from 2007 to 2018. Our analysis pipeline applies both static and dynamic analysis to extract information from the samples, such as wallet identifiers and mining pools. Together with OSINT data, this information is used to group samples into campaigns.We then analyze publicly-available payments sent to the wallets from mining-pools as a reward for mining, and estimate profits for the different campaigns.Our profit analysis reveals campaigns with multimillion earnings, associating over 4.3% of Monero with illicit mining. We analyze the infrastructure related with the different campaigns,showing that a high proportion of this ecosystem is supported by underground economies such as Pay-Per-Install services. We also uncover novel techniques that allow criminals to run successful campaigns.
This is not the first time we've seen confirmation of the basic thesis in the paper Bitcoin & Gresham's Law - the economic inevitability of Collapse. Anecdotal accounts suggest that in the period of late 2011 and into 2012 there was a lot of criminal mining.
Our thesis was that criminal mining begets more, and eventually pushes out the honest business, of all form from mining to trade.
Testing the model: Mining is owned by BotnetsLet us examine the various points along an axis from honest to stolen mining: 0% botnet mining to 100% saturation. Firstly, at 0% of botnet penetration, the market operates as described above, profitably and honestly. Everyone is happy.
But at 0%, there exists an opportunity for near-free money. Following this opportunity, one operator enters the market by turning his botnet to mining. Let us assume that the operator is a smart and careful crook, and therefore sets his mining limit at some non-damaging minimum value such as 1% of total mining opportunity. At this trivial level of penetration, the botnet operator makes money safely and happily, and the rest of the Bitcoin economy will likely not notice.
However we can also predict with confidence that the market for botnets is competitive. As there is free entry in mining, an effective cartel of botnets is unlikely. Hence, another operator can and will enter the market. If a penetration level of 1% is non-damaging, 2% is only slightly less so, and probably nearly as profitable for the both of them as for one alone.
And, this remains the case for the third botnet, the fourth and more, because entry into the mining business is free, and there is no effective limit on dishonesty. Indeed, botnets are increasingly based on standard off-the-shelf software, so what is available to one operator is likely visible and available to them all.
What stopped it from happening in 2012 and onwards? Consensus is that ASICs killed the botnets. Because serious mining firms moved to using large custom rigs of ASICS, and as these were so much more powerful than any home computer, they effectively knocked the criminal botnets out of the market. Which the new paper acknowledged:
... due to the proliferation of ASIC mining, which uses dedicated hardware, mining Bitcoin with desktop computers is no longer profitable, and thus criminals’ attention has shifted to other cryptocurrencies.
Why is botnet mining back with Monero? Presumably because Monero uses an ASIC-resistant algorithm that is best served by GPUs. And is also a heavy privacy coin, which works nicely for honest people with privacy problems but also works well to hide criminal gains.
October 21, 2018
ID Dox - now it's getting personal - Andreas spoofed
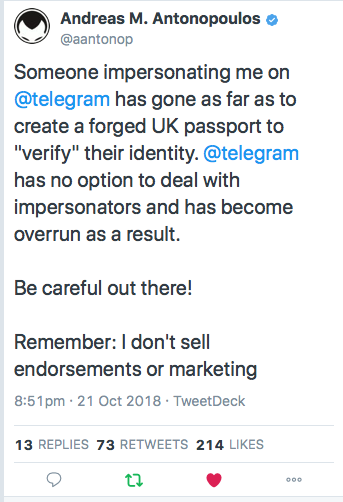 Writes Andreas Antonopolous, a noted Bitcoin commentator, that he has been impersonated with a mere scan!
Writes Andreas Antonopolous, a noted Bitcoin commentator, that he has been impersonated with a mere scan!
More than anything else this points at the fallacy of Identity Documents as the God of our Identity. AA may very well be a victim of our penultimate post on cheap-as-chips scans of your identity.
What's becoming clear is that identity is garnering more attention. Unwittingly, orgs and peoples who thought they had this under control are being dragged into the quagmire caused by firstly the Internet, then the upheavals caused by the great financial crisis and the drugs wars, and finally the devil of all devils, blockchain. Where will it end?
Meanwhile, here comes The Award-Winning David G.W. Birch @dgwbirch another understated twitter persona with slides and solutions for your identity:
The Award-Winning David G.W. Birch @dgwbirch A Short, Strategic Comment on Digital Identity by @chyppings #authentication #authorisation slideshare.net/15Mb/a-short-s… <- A short keynote for the Biometrics Congress in London. People liked it and asked for a copy so I've uploaded it to SlideShare.
I post this for debate not for endorsement ;-)
I'd also like to point out that it is unfortunate that <blockchain> is not a HTML entity, because that's what gets typed these days.
October 19, 2018
AES was worth $250 billion dollars
So says NIST...
10 years ago I annoyed the entire crypto-supply industry:
Hypothesis #1 -- The One True Cipher Suite In cryptoplumbing, the gravest choices are apparently on the nature of the cipher suite. To include latest fad algo or not? Instead, I offer you a simple solution. Don't.
There is one cipher suite, and it is numbered Number 1.
Cypersuite #1 is always negotiated as Number 1 in the very first message. It is your choice, your ultimate choice, and your destiny. Pick well.
The One True Cipher Suite was born of watching projects and groups wallow in the mire of complexity, as doubt caused teams to add multiple algorithms- a complexity that easily doubled the cost of the protocol with consequent knock-on effects & costs & divorces & breaches & wars.
It - The One True Cipher Suite as an aphorism - was widely ridiculed in crypto and standards circles. Developers and standards groups like the IETF just could not let go of crypto agility, the term that was born to champion the alternate. This sacred cow led the TLS group to field something like 200 standard suites in SSL and radically reduce them to 30 or 40 over time.
Now, NIST has announced that AES as a single standard algorithm is worth $250 billion economic benefit over 20 years of its project lifetime - from 1998 to now.
h/t to Bruce Schneier, who also said:
"I have no idea how to even begin to assess the quality of the study and its conclusions -- it's all in the 150-page report, though -- but I do like the pretty block diagram of AES on the report's cover."
One good suite based on AES allows agility within the protocol to be dropped. Entirely. Instead, upgrade the entire protocol to an entirely new suite, every 7 years. I said, if anyone was asking. No good algorithm lasts less than 7 years.
Crypto-agility was a sacred cow that should have been slaughtered years ago, but maybe it took this report from NIST to lay it down: $250 billion of benefit.
In another footnote, we of the Cryptix team supported the AES project because we knew it was the way forward. Raif built the Java test suite and others in our team wrote and deployed contender algorithms.
July 25, 2018
Zooko buys Groceries...
Zooko's tweet got me thinking, and it wasn't the flood of rejection he received.
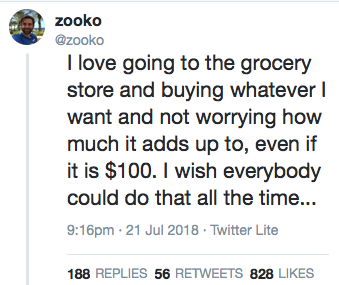 I have been in that state, and I knew exactly what he meant. Been there, done that experience where you have to add each item, you have to shop for value, drop the things you want, and live on rice & beans.
I have been in that state, and I knew exactly what he meant. Been there, done that experience where you have to add each item, you have to shop for value, drop the things you want, and live on rice & beans.
Like billions of people.
Let me share an anecdote. Once upon a time I lived in Amsterdam. We had a sort of student or groupie house with some of us on the ground floor apartment and some of us on the next floor up. It was one of those places where the crazy landlady wanted crazy non-locals because we paid in cash and didn’t cause trouble.
My startup had just failed - in 1998 nobody wanted to issue hard cryptographically-protected secure instruments that could describe any money at all. Go figure. But those weren’t my worries then, what I was worried about then was … money.
Of the sort that purchased groceries, not the sort that the cypherpunks dreamed of and had but didn’t have. I would take the money to the grocery store and buy stuff. It was my job to do chilli con carne once in a while, like every few weeks. The money was someone else’s. Therefore my actual job was like taking a little money to the grocery store, buying 6 cans of tomatoes, 3 cans of beans, 1kg of minced meat, 3 chillies, onions and a lot of rice. Then cooking it and serving it.
 That could feed about 5 adults for about 4 days.
That could feed about 5 adults for about 4 days.
For about 6 months I was in this state of poverty. It wasn’t the first time, nor the last, nor the worst - but it meant several things. I really had to watch the money. And wash clothes and iron shirts and cook chilli con carne and feed the group. I couldn’t make decisions because I couldn’t afford to make decisions. I couldn’t vary the menu because that was the cheapest.
Until I picked up a contract doing "requirements" for a local smart card money firm, I was stuck in this state. Every week or two, one of the guys from upstairs would invite me to the Bagel's 'n Beans (I think it was called) at the corner and we'd do breakfast in the sunshine and talk about financial cryptography and how to issue eCash and how to save the planet. Then he’d pay, and he’d go off to work because his startup hadn’t collapsed yet, and he still had a paycheck.
I was very conscious of the fact that if I hadn't had good friends, I'd be screwed. I was basically living for free while they were working their day jobs. It's hard to explain to those who have never faced it but there is a special hell for those who've had good paying jobs and then they get shut out. Of course, this happens to millions or billions, I'm not special.
The guy who liked Bagels was @zooko. Ever since that period I've tried to invite my poorer friends. Money didn’t matter, except when it did. Money was for living, not for making. Money was for doing, not for counting.
And I have thought a lot about what that time meant to me. It was that experience, and later experiences that led me to understand that the fabric of society isn't commerce, it isn't capitalism, it isn't profit and it very much isn't the dollar or the euro or the yen. The fabric of society is relationships. I didn't know it then, but I slowly found myself in the search for community. Not because I needed it, or not only, but because I thought that in community was the answer.
To the problem, and in 2008 I found myself again in deep poverty in the rich country of Austria. This time I had a job doing community auditing, which worked out at about €1 per hour, comfortably well below the poverty line, but alive. But, while we were building that community, we were watching the world’s financial community get into gridlock. Banks failing, countries on the verge, etc.
Since around 2000 - the dotcom crash - a lot of us had expected a real hard recession. It never happened, and we were mystified. Then in 2008 the answer was revealed. The man they called the magician, Alan Greenspan, had led bailout after bailout. Not of banks, but of the entire world system: the dotcom crash, 9/11, mutual funds scandal, fannie mae, something else... had all been rewarded with monstrous injections in liquidity. The banks or Alan Greenspan or someone had turned the entire western financial system into a bubble or a Ponzi or something.
And this last decade has been the mother of all bailouts - Quantitative Easing is nothing more than a gift to the financial system.
The problem I'm looking at then takes on a new aspect. What happens when the mother of all bubbles pops? When, not only can we not afford the groceries, but when there aren’t any grocery stores? We know something of this from Greece, from Puerto Rico, from Venezuela. How is it that people survive?
I knew it was relationship but I didn't know how. I knew people would save people, but how? My experiences in Amsterdam and Vienna and a few other episodes gave me no clear pattern - I knew that people saved people, but who, when and why in each circumstance?
Until, after a few more years skidding along the planetary row I found the how in Kenya - the chamas. It wasn’t that Kenyans were smarter than the westerners (they can be, and they’re definitely smarter than NGOs and aid workers who come to help) but it was clearer that there were two environmental factors that led them to work smarter, better, safer: poverty and corruption. It was out of these twin forces - I theorise - that they augmented their family and local trust lines into chamas.
Finding the how was pretty exciting. It was the lightbulb moment - the Eureka thing. Enough for me to quit my really safe and boring job in Australia and go to Kenya to build the first generation of chamapesa. It wasn’t because our technology spoke to chamas and chamas listened. It wasn’t because I loved Africa and the people were wonderful, it wasn’t because the business plan gasped an exponential curve to the moon. And it wasn’t because we could put a billion Africans on the blockchain, or a million blockchains on Africans.
It was because here was the solution, to everything I had not been able to work out before.
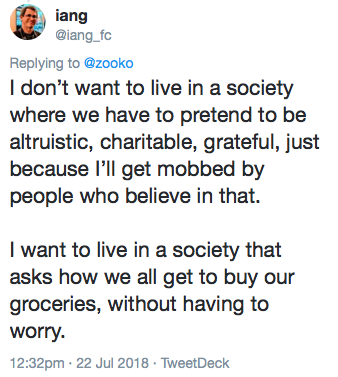 Like Zooko and a billion other people I’d spent many years in the grocery accounting trap. Like Zooko and millions of other people I’d lived the life of intelligent comfortable wealth and didn’t really care how much things cost.
Like Zooko and a billion other people I’d spent many years in the grocery accounting trap. Like Zooko and millions of other people I’d lived the life of intelligent comfortable wealth and didn’t really care how much things cost.
But like Zooko and a much smaller group of people, I've lived both those lives. That shock of poverty was burnt into our rich, educated privileged brains. And it matters. It drives us. It owns us, it changes us. I went to Kenya not for them but for all of us. To be nauseous, Chamapesa is our plan to get everyone to the grocery store so they don't care about the cost. And it is the rich west as well as the entrepreneurial Africans who'll need this.
So when Zooko posts on his experiences, and gets attacked for lack of humility or lack of gratefulness, I understand the angst that these people have, but honestly, they’ve missed the point. Having lived on both sides of the tracks, it isn’t gratefulness or humility or charity that we find or care for or should exhibit, it is clarity of thought.
And this is where we separate from those in Silicon Valley or the NGO armies or the twitter social justice warriors or regulators or other oligopolists. They’ll never understand because those people have only lived on one side of the tracks.
You can't "fight poverty" when you work for a family wealth fund. You can't "save the poor" when you live in Silicon Valley and whiteboards & google are the extent of your knowledge. You can't blockchain your way to understanding. You can't "bank the unbanked" when your entire worldview is driven by the World Bank. You can't "give charitably" and expect that money to be spent wisely by those who receive charitably.
You get your degree in poverty by living it, not by going to University and studying IMF reports. So when Zooko exhibits his particular penchant for unfiltered thought, it is not going to fit in with people's polite ways of ignoring problems - humility, gratefulness, charity are all comforting techniques to avoid the problem.
The problem that Zooko is being daily reminded of and is highlighting to a de-sensitised readership is this: at some point poverty becomes a trap such that no amount of normal or routine activity can extract you out of it. Only a serious and literally life-changing intervention can fix that problem.
And here's where I can add: chamas are the routine & normal activity that can address the trap, because they were designed to do exactly that. Which is a solution available to some, and not to others. We had it in Amsterdam in some pre-formative sense. The long term outlook for those with access to these societal techniques is far better than those without. Working to a stronger society then is why I'm working on chamas, with Africans, and not on blockchain with silicon valley types.
I understand that the cost of that is I will be called all sorts of things. But, in this game, it is more important to have clarity of thought than to be liked.
October 23, 2016
Bitfinex - Wolves and a sheep voting on what's for dinner
 When Bitcoin first started up, although I have to say I admired the solution in an academic sense, I had two critiques. One is that PoW is not really a sustainable approach. Yes, I buy the argument that you have to pay for security, and it worked so it must be right. But that's only in a narrow sense - there's also an ecosystem approach to think about.
When Bitcoin first started up, although I have to say I admired the solution in an academic sense, I had two critiques. One is that PoW is not really a sustainable approach. Yes, I buy the argument that you have to pay for security, and it worked so it must be right. But that's only in a narrow sense - there's also an ecosystem approach to think about.
Which brings us to the second critique. The Bitcoin community has typically focussed on security of the chain, and less so on the security of the individual. There aren't easy tools to protect the user's value. There is excess of focus on technologically elegant inventions such as multisig, HD, cold storage, 51% attacks and the like, but there isn't much or enough focus in how the user survives in that desperate world.
Instead, there's a lot of blame the victim, saying they should have done X, or Y or used our favourite toy or this exchange not that one. Blaming the victim isn't security, it's cannibalism.
Unfortunately, you don't get out of this for free. If the Bitcoin community doesn't move to protect the user, two things will happen. Firstly, Bitcoin will earn a dirty reputation, so the community won't be able to move to the mainstream. E.g., all these people talking about banks using Bitcoin - fantasy. Moms and pops will be and remain safer with money in the bank, and that's a scary thought if you actually read the news.
Secondly, and worse, the system remains vulnerable to collapse. Let's say someone hacks Mt.Gox and makes a lot of money. They've now got a lot of money to invest in the next hack and the next and the next. And then we get to the present day:
Message to the individual responsible for the Bitfinex security incident of August 2, 2016We would like to have the opportunity to securely communicate with you. It might be possible to reach a mutually agreeable arrangement in exchange for an enormous bug bounty (payable through a more privacy-centric and anonymous way).
So it turns out a hacker took a big lump of Bitfinex's funds. However, the hacker didn't take it all. Joseph VaughnPerling tells me:
"The bitfinex hack took just about exactly what bitfinex had in cold storage as business profit capital. Bitfinex could have immediately made all customers whole, but then would have left insufficient working capital. The hack was executed to do the maximal damage without hurting the ecosystem by putting bitfinex out of business. They were sure to still be around to be hacked again later.It is like a good farmer, you don't cut down the tree to get the apples."
A carefully calculated amount, coincidentally about the same as Bitfinex's working capital! This is annoyingly smart of the hacker - the parasite doesn't want to kill the host. The hacker just wants enough to keep the company in business until the next mafiosa-style protection invoice is due.
So how does the company respond? By realising that it is owned. Pwn'd the cool kids say. But owned. Which means a negotiation is due, and better to convert the hacker into a more responsible shareholder or partner than to just had over the company funds, because there has to be some left over to keep the business running. The hacker is incentivised to back off and just take a little, and the company is incentivised to roll over and let the bigger dog be boss dog.
Everyone wins - in terms of game theory and economics, this is a stable solution. Although customers would have trouble describing this as a win for them, we're looking at it from an ecosystem approach - parasite versus host.
But, that stability only survives if there is precisely one hacker. What happens if there are two hackers? What happens when two hackers stare at the victim and each other?
Well, it's pretty easy to see that two attackers won't agree to divide the spoils. If the first one in takes an amount calculated to keep the host alive, and then the next hacker does the same, the host will die. Even if two hackers could convert themselves into one cartel and split the profits, a third or fourth or Nth hacker breaks the cartel.
The hackers don't even have to vote on this - like the old joke about democracy, when there are 2 wolves and 1 sheep, they eat the sheep immediately. The talk about voting is just the funny part for human consumption. Pardon the pun.
The only stability that exists in the market is if there is between zero and one attacker. So, barring the emergence of some new consensus protocol to turn all the individual attackers into one global mafiosa guild, a theme frequently celebrated in the James Bond movies, this market cannot survive.
To survive in the long run, the Bitcoin community have to do better than the banks - much better. If the Bitcoin community wants a future, they have to change course. They have to stop obsessing about the chain's security and start obsessing about the user's security.
The mantra should be, nobody loses money. If you want users, that's where you have to set the bar - nobody loses money. On the other hand, if you want to build an ecosystem of gamblers, speculators and hackers, by all means, obsess about consensus algorithms, multisig and cold storage.
ps; I first made this argument of ecosystem instability in "Bitcoin & Gresham's Law - the economic inevitability of Collapse," co-authored with Philipp Güring.
March 13, 2016
Elinor Ostrom's 8 Principles for Managing A Commmons
(Editor's note: Originally published at http://www.onthecommons.org/magazine/elinor-ostroms-8-principles-managing-commmons by Jay Walljasper in 2011)
Elinor Ostrom shared the Nobel Prize in Economics in 2009 for her lifetime of scholarly work investigating how communities succeed or fail at managing common pool (finite) resources such as grazing land, forests and irrigation waters. On the Commons is co-sponsor of a Commons Festival at Augsburg College in Minneapolis October 7-8 where she will speak. (See accompanying sidebar for details.)
Ostrom, a political scientist at Indiana University, received the Nobel Prize for her research proving the importance of the commons around the world. Her work investigating how communities co-operate to share resources drives to the heart of debates today about resource use, the public sphere and the future of the planet. She is the first woman to be awarded the Nobel in Economics.
Ostrom’s achievement effectively answers popular theories about the "Tragedy of the Commons", which has been interpreted to mean that private property is the only means of protecting finite resources from ruin or depletion. She has documented in many places around the world how communities devise ways to govern the commons to assure its survival for their needs and future generations.
A classic example of this was her field research in a Swiss village where farmers tend private plots for crops but share a communal meadow to graze their cows. While this would appear a perfect model to prove the tragedy-of-the-commons theory, Ostrom discovered that in reality there were no problems with overgrazing. That is because of a common agreement among villagers that one is allowed to graze more cows on the meadow than they can care for over the winter—a rule that dates back to 1517. Ostrom has documented similar effective examples of "governing the commons" in her research in Kenya, Guatemala, Nepal, Turkey, and Los Angeles.
Based on her extensive work, Ostrom offers 8 principles for how commons can be governed sustainably and equitably in a community.
8 Principles for Managing a Commons
 1. Define clear group boundaries.
1. Define clear group boundaries.
2. Match rules governing use of common goods to local needs and conditions.
3. Ensure that those affected by the rules can participate in modifying the rules.
4. Make sure the rule-making rights of community members are respected by outside authorities.
5. Develop a system, carried out by community members, for monitoring members’ behavior.
6. Use graduated sanctions for rule violators.
7. Provide accessible, low-cost means for dispute resolution.
8. Build responsibility for governing the common resource in nested tiers from the lowest level up to the entire interconnected system.
November 15, 2015
the Satoshi effect - Bitcoin paper success against the academic review system
One of the things that has clearly outlined the dilemma for the academic community is that papers that are self-published or "informally published" to borrow a slur from the inclusion market are making some headway, at least if the Bitcoin paper is a guide to go by.
Here's a quick straw poll checking a year's worth of papers. In the narrow field of financial cryptography, I trawled through FC conference proceedings in 2009, WEIS 2009. For Cryptology in general I added Crypto 2009. I used google scholar to report direct citations, and checked what I'd found against Citeseer (I also added the number of citations for the top citer in rightmost column, as an additional check. You can mostly ignore that number.) I came across Wang et al's paper from 2005 on SHA1, and a few others from the early 2000s and added them for comparison - I'm unsure what other crypto papers are as big in the 2000s.
| Conf | paper | Google Scholar | Citeseer | top derivative citations |
|---|---|---|---|---|
| jMLR 2003 | Latent dirichlet allocation | 12788 | 2634 | 26202 |
| NIPS 2004 | MapReduce: simplified data processing on large clusters | 15444 | 2023 | 14179 |
| CACM 1981 | Untraceable electronic mail, return addresses, and digital pseudonyms | 4521 | 1397 | 3734 |
| self | Security without identification: transaction systems to make Big Brother obsolete | 1780 | 470 | 2217 |
| Crypto 2005 | Finding collisions in the full SHA-1 | 1504 | 196 | 886 |
| SIGKDD 2009 | The WEKA data mining software: an update | 9726 | 704 | 3099 |
| STOC 2009 | Fully homomorphic encryption using ideal lattices | 1923 | 324 | 770 |
| self | Bitcoin: A peer-to-peer electronic cash system | 804 | 57 | 202 |
| Crypto09 | Dual System Encryption: Realizing Fully Secure IBE and HIBE under Simple Assumptions | 445 | 59 | 549 |
| Crypto09 | Fast Cryptographic Primitives and Circular-Secure Encryption Based on Hard Learning Problems | 223 | 42 | 485 |
| Crypto09 | Distinguisher and Related-Key Attack on the Full AES-256 | 232 | 29 | 278 |
| FC09 | Secure multiparty computation goes live | 191 | 25 | 172 |
| WEIS 2009 | The privacy jungle: On the market for data protection in social networks | 186 | 18 | 221 |
| FC09 | Private intersection of certified sets | 84 | 24 | 180 |
| FC09 | Passwords: If We’re So Smart, Why Are We Still Using Them? | 89 | 16 | 322 |
| WEIS 2009 | Nobody Sells Gold for the Price of Silver: Dishonesty, Uncertainty and the Underground Economy | 82 | 24 | 275 |
| FC09 | Optimised to Fail: Card Readers for Online Banking | 80 | 24 | 226 |
What can we conclude? Within the general infosec/security/crypto field in 2009, the Bitcoin paper is the second paper after Fully homomorphic encryption (which is probably not even in use?). If one includes all CS papers in 2009, then it's likely pushed down a 100 or so slots according to citeseer although I didn't run that test.
If we go back in time there are many more influential papers by citations, but there's a clear need for time. There may well be others I've missed, but so far we're looking at one of a very small handful of very significant papers at least in the cryptocurrency world.
It would be curious if we could measure the impact of self-publication on citations - but I don't see a way to do that as yet.
Ledger - a journal for cryptocurrency papers
"Ledger" was recently announced as a journal for cryptocurrency papers, and the timing was rather spectacular. Everyone agrees this is a good idea.

Today I had a look, because I and some friends have some papers that might be published there. Several things reached out, so I thought I'd put them out here and see if they resonate.
1. The Ledger team seem to have taken on some criticism of the academic process and gone for more openness in several areas:
- Ledger has created a peer review system where reviews are publishable by authors. What Ledger have done is ensured that reviewers can be published and held accountable for their reviews. This should go some way to stopping academic cliques building up, a fate that I can attest to directly.
- Papers are CC-licensed so immediately and popularly available. Discourse is well served. I am not sure where the others are now, but I've had my arguments in the past with the proxies of Springer-Verlag wanting to own my mind. Those days are dead.
- Fast turn arounds promised.
2. Business-wise, Ledger is a direct competitor to existing forums Financial Cryptography (the conference) and to a lesser extent WEIS. Now, this is fine in my view as (a) the space has massively enlarged from the niche it once was, and we can easily support more forums, and (b) Ledger is oriented to the paper distribution process whereas others are primarily presentation-oriented and networking. Also (c) the founder and coiner of Financial Cryptography, Bob Hettinga, always made clear that this was a competitive market ;)
3. It is not immediately clear who the reviewers are. While the core might be its Editorial base, the asset of a peer-reviewed journal is its hardworking reviewers. Specifically, the asset can be attached.
4. And, immediately the attachment begins. If you look at the Editor's page, they have fallen into the same trap as the financial cryptography conference fell into in 1998 - academic control. Of the very long list of fine editors, only a tiny minority are outside the University system by either affiliation or title. Whatever you think of the academic world, it is very clear that it is a discriminatory system, and many fine contributions are squashed or stolen for it.
5. In which world, reputation and cites rule. Which leads to anonymous authorship:
Under extenuating circumstances, the journal may permit authors to publish under a pseudonym. Authors should include a statement describing why they wish to remain anonymous at the time of article submission. Only manuscripts where quality can be judged exclusively from the content presented in the paper, and where the scope of any conflict of interest problems would be limited (should they exist), will be considered for anonymous authorship.
Ledger are clearly skeptical of the notion of anonymous authorship because as academics they are so used to leaning on the reputation of the author. A bad paper by a leading author always trumps a good paper by an unknown, and it is practically the law that the profs must co-author the papers of the candidates so as to cross that barrier.
Ledger are thus clearly skeptical that the paper's words mean much independently of the author's reputation. Leaving it at odds with the Bitcoin community is as it is, as, under those rules, Satoshi's paper would not have been published, and we'd not be having these discussions. Now, it's fine for them to do this, but what I'd point out here is that this is further evidence of 4. above: academics setting themselves up to capture cites.
6. In not charging for papers, nor distribution & access, the Ledger has a clear financial business problem. It (probably) relies entirely on two sources: the volunteer time of reviewers, and the paid salary of academics.

The nature of scientific enquiry has moved on since the days of the controlled paper distribution. All papers from now on must be free of economic control, or we get the Satoshi effect - the most important paper in the field was never published in a forum, because under the rules of all the forums, it could not be published. The old forums out there had economic controls, and those controls were captured by the very people who could benefit from the controls - cites are promotions are money, and paper is trees is subscriptions.
Ledger presents the disturbing academic dilemma in a nutshell. The Internet has solved the paper-subscription economic barrier, but not the citation-peer-review circle. And, it leans very heavily on academics on salary, which is the other side of the same coin - what is the economic model that both sustains the machine, and rewards the quality?
If you're thinking I'm arguing both sides of this - you're right. I can see the problem. I don't have the answers - unless you want something superficial like "publish papers on the blockchain!" But we won't find the answers until we understand the problems.
October 25, 2015
When the security community eats its own...
If you've ever wondered what that Market for Silver Bullets paper was about, here's Pete Herzog with the easy version:
When the Security Community Eats Its Own
BY PETE HERZOG
http://isecom.org

The CEO of a Major Corp. asks the CISO if the new exploit discovered in the wild, Shizzam, could affect their production systems. He said he didn't think so, but just to be sure he said they will analyze all the systems for the vulnerability.
So his staff is told to drop everything, learn all they can about this new exploit and analyze all systems for vulnerabilities. They go through logs, run scans with FOSS tools, and even buy a Shizzam plugin from their vendor for their AV scanner. They find nothing.
A day later the CEO comes and tells him that the news says Shizzam likely is affecting their systems. So the CISO goes back to his staff to have them analyze it all over again. And again they tell him they don’t find anything.
Again the CEO calls him and says he’s seeing now in the news that his company certainly has some kind of cybersecurity problem.
So, now the CISO panics and brings on a whole incident response team from a major security consultancy to go through each and every system with great care. But after hundreds of man hours spent doing the same things they themselves did, they find nothing.
He contacts the CEO and tells him the good news. But the CEO tells him that he just got a call from a journalist looking to confirm that they’ve been hacked. The CISO starts freaking out.
The CISO tells his security guys to prepare for a full security upgrade. He pushes the CIO to authorize an emergency budget to buy more firewalls and secondary intrusion detection systems. The CEO pushes the budget to the board who approves the budget in record time. And almost immediately the equipment starts arriving. The team works through the nights to get it all in place.
The CEO calls the CISO on his mobile – rarely a good sign. He tells the CISO that the NY Times just published that their company allegedly is getting hacked Sony-style.
They point to the newly discovered exploit as the likely cause. They point to blogs discussing the horrors the new exploit could cause, and what it means for the rest of the smaller companies out there who can’t defend themselves with the same financial alacrity as Major Corp.
The CEO tells the CISO that it's time they bring in the FBI. So he needs him to come explain himself and the situation to the board that evening.
The CISO feels sick to his stomach. He goes through the weeks of reports, findings, and security upgrades. Hundreds of thousands spent and - nothing! There's NOTHING to indicate a hack or even a problem from this exploit.
So wondering if he’s misunderstood Shizzam and how it could have caused this, he decides to reach out to the security community. He makes a new Twitter account so people don’t know who he is. He jumps into the trending #MajorCorpFail stream and tweets, "How bad is the Major Corp hack anyway?"
A few seconds later a penetration tester replies, "Nobody knows xactly but it’s really bad b/c vendors and consultants say that Major Corp has been throwing money at it for weeks."
Read on for the more deeper analysis.
October 22, 2015
Iceland puts more bankers in jail... what's your solution to the financial crisis?
In the crisis that just won't go away - we're effectively in depression but no politician can stay elected on that platform - one of the most watched countries is Iceland.
Iceland sentences 26 bankers to a combined 74 years in prison James Woods October 21, 2015 Unlike the Obama administration, Iceland is focusing on prosecuting the CEOs rather than the low-level traders.In a move that would make many capitalists' head explode if it ever happened here, Iceland just sentenced their 26th banker to prison for their part in the 2008 financial collapse.
In two separate Icelandic Supreme Court and Reykjavik District Court rulings, five top bankers from Landsbankinn and Kaupping — the two largest banks in the country — were found guilty of market manipulation, embezzlement, and breach of fiduciary duties. Most of those convicted have been sentenced to prison for two to five years. The maximum penalty for financial crimes in Iceland is six years, although their Supreme Court is currently hearing arguments to consider expanding sentences beyond the six year maximum.
Now, my argument here is the same as with the audit cycle: if so much was so wrong, surely some bankers in USA and Europe should have been prosecuted and put in jail even by accident?
But, no, nothing. A few desultory insider trading hits, but on the whole, a completely clean pass for the major banks. Coupled with direct bankrupcy bailouts, and the follow-on enormous bailout of QE* which transferred capital into the banks under deception plan of "re-inflating industry", we have a rather unfortunate situation:
No punishment means no sin, right?
It is no wonder that the public at large are unhappy with banking in general and are willing to entertain such way out ideas as blockchain. Credibility is a huge issue:
When Iceland's President, Olafur Ragnar Grimmson was asked how the country managed to recover from the global financial disaster, he famously replied,"We were wise enough not to follow the traditional prevailing orthodoxies of the Western financial world in the last 30 years. We introduced currency controls, we let the banks fail, we provided support for the poor, and we didn’t introduce austerity measures like you're seeing in Europe."
A great time to be an economic historian. A middling time to be an economist. Terrible time to be a regulator?
June 28, 2015
The Nakamoto Signature
The Nakamoto Signature might be a thing. In 2014, the Sidechains whitepaper by Back et al introduced the term Dynamic Membership Multiple-party Signature or DMMS -- because we love complicated terms and long impassable acronyms.
Or maybe we don't. I can never recall DMMS nor even get it right without thinking through the words; in response to my cognitive poverty, Adam Back suggested we call it a Nakamoto signature.
That's actually about right in cryptology terms. When a new form of cryptography turns up and it lacks an easy name, it's very often called after its inventor. Famous companions to this tradition include RSA for Rivest, Shamir, Adleman; Schnorr for the name of the signature that Bitcoin wants to move to. Rijndael is our most popular secret key algorithm, from the inventors names, although you might know it these days as AES. In the old days of blinded formulas to do untraceable cash, the frontrunners were signatures named after Chaum, Brands and Wagner.
On to the Nakamoto signature. Why is it useful to label it so?
Because, with this literary device, it is now much easier to talk about the blockchain. Watch this:
The blockchain is a shared ledger where each new block of transactions - the 10 minutes thing - is signed with a Nakamoto signature.
Less than 25 words! Outstanding! We can now separate this discussion into two things to understand: firstly: what's a shared ledger, and second: what's the Nakamoto signature?
Each can be covered as a separate topic. For example:
the shared ledger can be seen as a series of blocks, each of which is a single document presented for signature. Each block consists of a set of transactions built on the previous set. Each succeeding block changes the state of the accounts by moving money around; so given any particular state we can create the next block by filling it with transactions that do those money moves, and signing it with a Nakamoto signature.
Having described the the shared ledger, we can now attack the Nakamoto signature:
A Nakamoto signature is a device to allow a group to agree on a shared document. To eliminate the potential for inconsistencies aka disagreement, the group engages in a lottery to pick one person's version as the one true document. That lottery is effected by all members of the group racing to create the longest hash over their copy of the document. The longest hash wins the prize and also becomes a verifiable 'token' of the one true document for members of the group: the Nakamoto signature.
That's it, in a nutshell. That's good enough for most people. Others however will want to open that nutshell up and go deeper into the hows, whys and whethers of it all. You'll note I left plenty of room for argument above; Economists will look at the incentive structure in the lottery, and ask if a prize in exchange for proof-of-work is enough to encourage an efficient agreement, even in the presence of attackers? Computer scientists will ask 'what happens if...' and search for ways to make it not so. Entrepreneurs might be more interested in what other documents can be signed this way. Cryptographers will pounce on that longest hash thing.
But for most of us we can now move on to the real work. We haven't got time for minutia. The real joy of the Nakamoto signature is that it breaks what was one monolithic incomprehensible problem into two more understandable ones. Divide and conquer!
The Nakamoto signature needs to be a thing. Let it be so!
NB: This article was kindly commented on by Ada Lovelace and Adam Back.
June 17, 2015
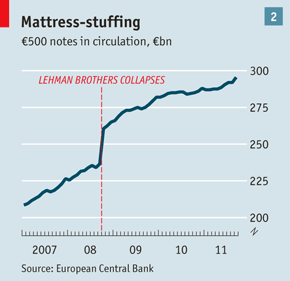
Cash seizure is a thing - maybe this picture will convince you
There are many many people who do not believe that the USA police seize cash from people and use it for budget. The system is set up for the benefit of police - budgetary plans are laid, you have no direct recourse to the law because it is the cash that defends itself, the proceeds are carved up.
Maybe this will convince you - if cash seizure by police wasn't a 'thing' we wouldn't need this chart:
June 09, 2015
Equity Crowd Funding - why it will change everything
Editor here again, picking up part 2 of the crowd funding thread. In the previous post, Vinay Gupta laid out why Coase's theorem didn't predict the tech revolution quite yet - in a nutshell, we lacked some critical components, of which one was the blockchain, being that invention that allows a dynamic membership multi-party signature (DMMS) to create a single entry that rules all others, the part I called triple entry.
But is it the only missing component? No. Actually, there's another component we are missing, and it is this: the ability to acquire the capital to build what we need and want. That hinted at, let's continue...
Vinay Gupta says:
Does everyone have a clear idea what Equity Crowd Funding looks like?
You get a bucket, everyone puts in 20 quid, everyone gets a tiny share in the company, if the company turns out to be the next eBay, you get 2000 quid back.
"Eh? Huh? What? I thought you never got anything back from most of the crowd funding sites?"
Aha! *Equity* crowd funding! Equity!
In Regular crowd funding, you put the money in and nothing comes back. In *equity* crowd funding, you put the money in and a tiny share comes back. And you can actually make some real money!
"I just missed the equity word."
Now, *equity* crowd funding is obviously a good idea. It is very very very hard to find any rational argument as to why equity crowd funding is a bad idea. The only objections you will typically see is, what if the public get conned. And that, coming from governments that actually operate national lotteries.
Right? Pardon? What are you talking about?!
"Bingo!"
You allow people to sell cigarettes, what are you talking about, "The public will get conned!" You're mad!
So, there are some quality control problems with equity crowd funding as a model. You need some way to communicate to people the level of risk in an appropriate way. You might want to talk about reputational rating systems. A Moodys or a Standard&Poors for equity crowd funding might be a good idea. There's all kinds of stuff you might want to do.
The basic idea is obviously sound. You sit there with a credit card, you swipe it, you own a tiny little share in a company that's manufacturing some weird looking device that you clip to a golf club, and if tens of millions of people like it, you make a lot of money back.
It's just not done.
Right now, the regulatory frameworks around equity crowd funding cripple it, and this is I think the key fight for the development of technology in the 21st century.
If we win equity crowd funding, I think we get pretty much a flying car each. And if we lose on equity crowd funding, I think we are potentially on a long cycle of decline, into a kind of neo-feudal patent-barren landscape.
Bold stuff!

Back to me. This pretty much nails *what* equity crowd funding is, and suggests the transition as to why it is going to be a killer app on the blockchain. (For the *why* of it you'd have to listen to the whole talk, and for the inter-relations you'd have to see a whole lot more stuff.)
The interesting thing, once we've got that understanding, that position, is to question how it will develop. We're in a race, or if we're not in it, we're watching it. At a simplistic level, it is a race between existing players trying to deregulate conventional securities issues fast enough, versus new players (we've maybe not seen yet) creating it fully openly on the blockchain.
It's not clear who is going to win. OK, what is clear is that the people win because we win more stuff for less money; but it is not clear whether we the people win all the way, or only a partial victory.
Do we get a flying car, each, or do we enter neo-feudal patent-barren secular decline?
Where are you on this race? Are you ready to bet?
May 01, 2015
Proof of Work is now being put to work - toasters!
FtAlpahville's has just revealed what revealing that 21Inc (formerly 21e6) are doing exactly that.
Its core business plan it turns out will be embedding ASIC bitcoin mining chips into everyday devices like USB battery chargers, routers, printers, gaming consoles, set-top boxes and -- the piece de resistance -- chipsets to be used by internet of things devices.21 Inc wants to put your toaster to work, forging our cryptocurrency future.
Interesting, because 21Inc currently holds the record for the biggest funding round - 116 million dollars! Here although the link will not last long.
It seems like the notion of heating ones house with residual heat from Bitcoin mining has been around for a long term, see slashdot from 2011.12.21, Gavin Andresen from 2013.04.09:
I can imagine bitcoin-mining electric hot water heaters installed in homes all across the world, installed by thousands of private companies that split the profits with homeowners.
More: FTAlphaville from 2014.09.05 which calls it "the latest fad." Vitalik Buterin also spotted the security argument in 2012.02.28:
"If miners figure out that they can dual-use their mining electricity by making their computers heat their homes during the winter, that would be a very positive change since it would decentralize mining to something every home or business does rather than a task done by centralized, specialized supercomputers and it would increase the network's hash power and thus security but it would not ultimately reduce the mining cost."
This all by the way of linking to some musings I wrote back in 2014, late to the game it seems, and maybe calling a fad was accurate. What seems clear is that the world is not happy about the efficiency of Bitcoin, and until this is addressed more comprehensively, the bitcoin core will stand at odds with the world. E.g. This might be the wrong moment in history to tell the mass market that our solution to the banking crisis is to gratuitously waste energy.
April 05, 2015
Yanis Varoufakis proposes Greek tax receipts in Ricardian Contracts on a blockchain
The answer is yes: They can create their own payment system backed by future taxes and denominated in euros. Moreover, they could use a Bitcoin-like algorithm in order to make the system transparent, efficient and transactions-cost-free. Let's call this system FT-coin; with FT standing for... Future Taxes.FT-coin could work as follows:
- You pay, say, €1000 to buy 1 FT-coin from a national Treasury's website (Spain, Italy, Ireland etc. would run their separate FT-coin markets) under a contract that binds the national Treasury: (a) to redeem your FT-coin for €1000 at any time or (b) to accept your FT-coin two years after it was issued as payment that extinguishes, say, €1500 worth of taxes.
- Each FT-coin is time stamped i.e. in its code the date of issue is contained and can be used to check that it is not used to extinguish taxes before two years have passed.
- Every year (after the system has been operating for at least two years) the Treasury issues a new batch of FT-coins to replace the ones that have been extinguished (as taxpayers use them, two years after the system's inauguration, to pay their taxes) on the understanding that the nominal value of the total number of FT-coins in circulation does not exceed a certain percentage of GDP (e.g. 10% of nominal GDP so that there is no danger that, if all FT-coins are redeemed simultaneously, the government will end up, during that year, with no taxes).
That first bullet point (my emphasis) is a legal issuance of new value, a.k.a., a bond, a.k.a. a contract of issuance. The offering concept is the same as the tally sticks of old - selling the pre-payment of taxes at a discount, the technicalities are simply how we get a legal contract into a digital framework that accounts for many similar values.
Because it's a contract in law as opposed to say a smartcontract, we need a system that can handle legal contracts. In essence, this is the Ricardian Contract -- a device that takes a human prose and encapsulates it into a hard computer-readable and human-readable document, then gives you a unique identifier in order to allow a technical system of issuance such as Bitcoin to do its job.
We're not there yet - Bitcoin directly isn't good enough, as Bitcoin is only "the one" BTC and therefore has no need to describe another. Hence no contract.
But the newer "generation 2.0" systems are more capable of including the Ricardian Contract form, and some do already while others can do so with minimal tweaking. This means that if Yanis Varoufakis is serious about his ideas, and given recent news from say IBM, there is no reason not to be, he'll be looking at a generation 2.0 system such as those described at WebFunds.
For Bitcoin itself, all is not lost, but it's more of a future deliverable: variants are looking at it but I have no definite information on that. However, there is no doubt that this will come, as Yanis Varoufakis is not the first. At least half the corporate and big players out there say "we can't use Bitcoin because it lacks a contract of issuance" or words to effect.
April 03, 2015
Training Day 2: starring Bridges & Force
 Readers might have probably been watching the amazing story of the Bridges & Force arrests in USA. It's starting to look much like a film, and the one I have in mind is this: Training Day.
Readers might have probably been watching the amazing story of the Bridges & Force arrests in USA. It's starting to look much like a film, and the one I have in mind is this: Training Day.
In short: two agents were sent in to bring down the Silk Road website for selling anything (guns, drugs, etc). In the process, the agents stole a lot of the money. And in the process, went on a rampage through the Bitcoin economy robbing, extorting, and manipulating their way to riches.
You can't make this up. Worse, we don't need to. The problem is deep, underlying and demented within our society. We're going to see much more of it, and the reason we know this is that we have decades of experience in other countries outside the OECD purview.
This is our own actions coming back to destroy us. In a nutshell here it is, here is the short story that gets me on the FATF's blacklist and you too if you spread it:
In the 1980s, certain European governments got upset about certain forms of arbitrage across nations by multinationals and rich folk. These people found a ready consensus with others in policing work who said that "follow the money" was how you catch the really bad people, a.k.a. criminals. Between these two groups of public servants they felt they could crack open the bank secrecy that was protecting criminals and rich people alike.
So the Anti Money Laundering or AML project was born, under the aegis of FATF or financial action task force, an office created in Paris under OECD. Their concept was that they put together rules about how to stop bad money moving through the system. In short: know your customer, and make sure their funds were good. Add in risk management and suspicious activity reporting and you're golden.
On passing these laws, every politician faithfully promised it was only for the big stuff, drugs and terrorism, and would never be used against honest or wealthy or innocent people. Honest Injun!
If only so simple. Anyone who knows anything about crime or wealth realises within seconds that this is not going to achieve anything against the criminals or the wealthy. Indeed, it may even make matters worse, because (a) the system is too imperfect to be anything but noise, (b) criminals and wealthy can bypass the system, and (c) criminals can pay for access. Hold onto that thought.
So, if the FATF had stopped there, then AML would have just been a massive cost on society. Westerners would paid basis points for nothing, and it would have just been a tool that shut the poor out of the financial system; something some call the problem of the 'unbanked' but that's a subject for another day (and don't use that term in my presence, thanks!). Criminals would have figured out other methods, etc.
If only. Just. But they went further.
In imposing the FATF 40 recommendations (yes, it got a lot more complicated and detailed, of course) everyone everywhere everytime also stumbled on an ancient truth of bureaucracy without control: we could do more if we had more money! Because of course the society cost of following AML was also hitting the police, implementing this wonderful notion of "follow the money" cost a lot of money.
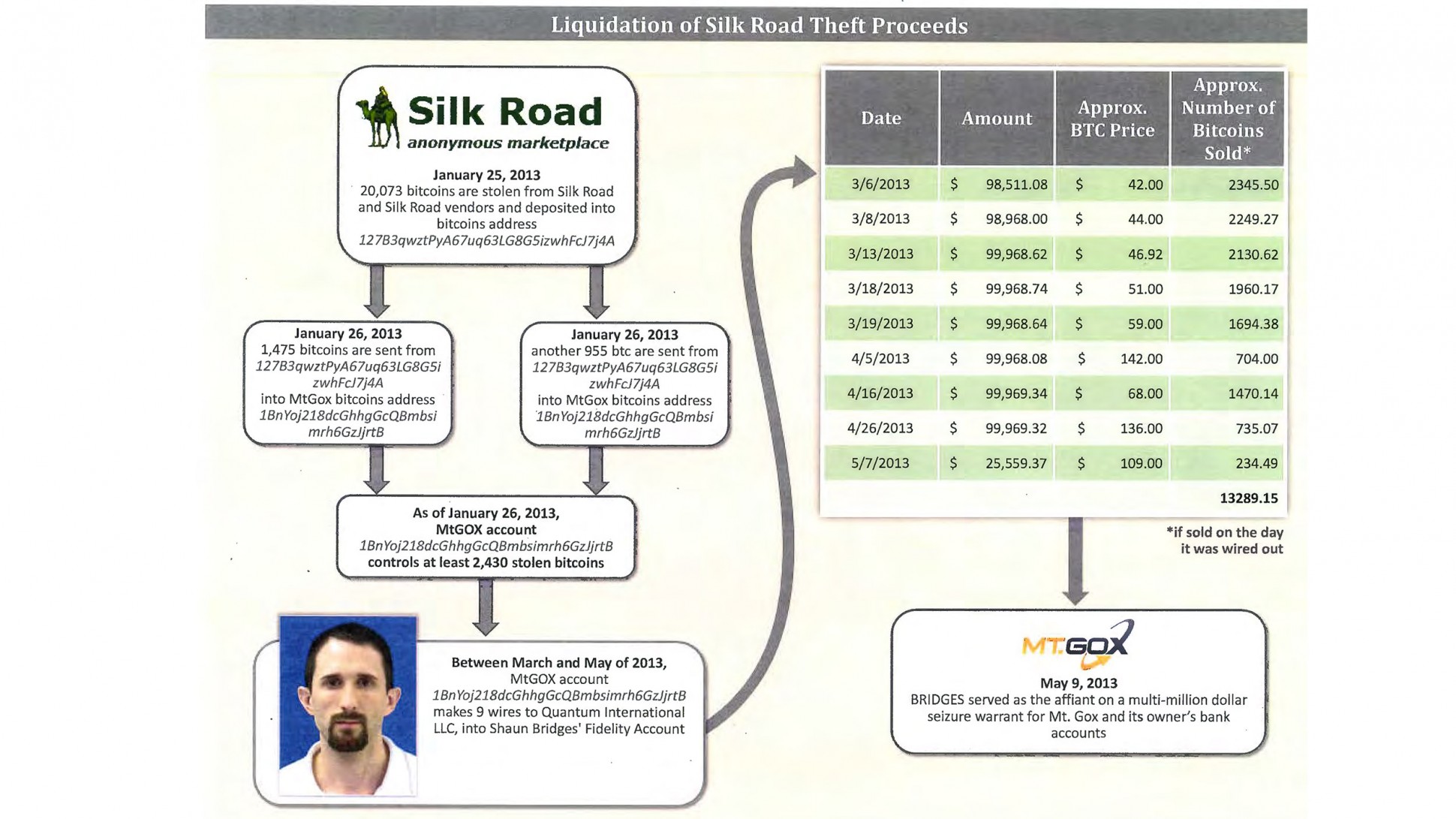 Until someone had the bright idea: if the money is bad, why can't we seize the bad money and use it to find more bad money?
Until someone had the bright idea: if the money is bad, why can't we seize the bad money and use it to find more bad money?
And so, it came to pass. The centuries-honoured principle of 'consolidated revenue' was destroyed and nobody noticed because "we're stopping bad people." Laws and regs were finagled through to allow money seized from AML operations to be then "shared" across the interested good parties. Typically some goes to the local police, and some to the federal justice. You can imagine the heated discussions about percentage sharing.
What could possibly go wrong?
Now the police were empowered not only to seize vast troves of money, but also keep part of it. In the twinkling of an eye, your local police force was now incentivised to look at the cash pile of everyone in their local society and 'find' a reason to bust. And, as time went on, they built their system to be robust to errors: even if they were wrong, the chances of any comeback were infinitesimal and the take might just be reduced.
AML became a profit center. Why did we let this happen? Several reasons:
1. It's in part because "bad guys have bad money" is such a compelling story that none dare question those who take "bad money from bad guys."
Indeed, money laundering is such a common criminal indictment in USA simply because people assume it's true on the face of it. The crime itself is almost as simple as moving a large pot of money around, which if you understand criminal proceedings, makes no sense at all. How can moving a large pot of money around be proven as ML before you've proven a predicate crime? But so it is.
2. How could we as society be so stupid? It's because the principle of 'consolidated revenue' has been lost in time. The basic principle is simple: *all* monies coming into the state must go to the revenue office. From there they are spent according to the annual budget. This principle is there not only for accountability but to stop the local authorities becoming the bandits The concept goes back all the way to the Magna Carta which was literally and principally about the barons securing the rights to a trial /over arbitrary seizure of their wealth/.
We dropped the ball on AML because we forgot history.

So what's all this to do with Bridges & Force? Well, recall that thought: the serious criminals can buy access. Which of course they've been doing since the beginning, the AML authorities themselves are victims to corruption.
As the various insiders in AML are corrupted, it becomes a corrosive force. Some insiders see people taking bribes and can't prove anything. Of course, these people aren't stupid, these are highly trained agents. Eventually they work out how they can't change anything and the crooks will never be ousted from inside the AML authorities. And they start with a little on the side. A little becomes a lot.
Every agent in these fields is exposed to massive corruption right from the start. It's not as if agents sent into these fields are bad. Quite the reverse, they are good and are made bad. The way AML is constructed it seems impossible that there could be any other result - Quis custodiet ipsos custodes? or Who watches the watchers?
Remember the film Training Day ? Bridges and Force are a remake, a sequel, this time moved a bit further north and with the added sex appeal of a cryptocurrency.
But the important things to realise is that this isn't unusual, it's embedded. AML is fatally corrupted because (a) it can't work anyway, and (b) they breached the principle of consolidated revenue, (c) turned themselves into victims, and then (d) the bad guys.
Until AML itself is unwound, we can't ourselves - society, police, authorities, bitcoiners - get back to the business of fighting the real bad guys. I'd love to talk to anyone about that, but unfortunately the agenda is set. We're screwed as society until we unwind AML.
March 30, 2015
Smart contracts are a centralising force - exactly the opposite effect to the one you hoped for?
@gendal writes on smart contracts and as usual his words are prophetic and dangerous:
Bitcoin as a currency might be to miss the pointFor me, it is a mistake to think about Bitcoin solely as a currency. Because the Bitcoin currency system is a masterclass in mirage: underneath the hood, it's a fascinating smart contract platform.
Or, as I said at the Financial Services Club, every time you make a Bitcoin payment, you're actually asking over 6000 computers around the world to run a small computer program for you... and your only task is to make sure that the computer program returns "TRUE". Within the Bitcoin community, this is well-known, of course. Indeed, the work done by Mike Hearn and others to document the platform's capabilities has been around for years. But I find most people in the broader debate are unaware that the platform is pretty much built on this capability -- it's not an add-on.
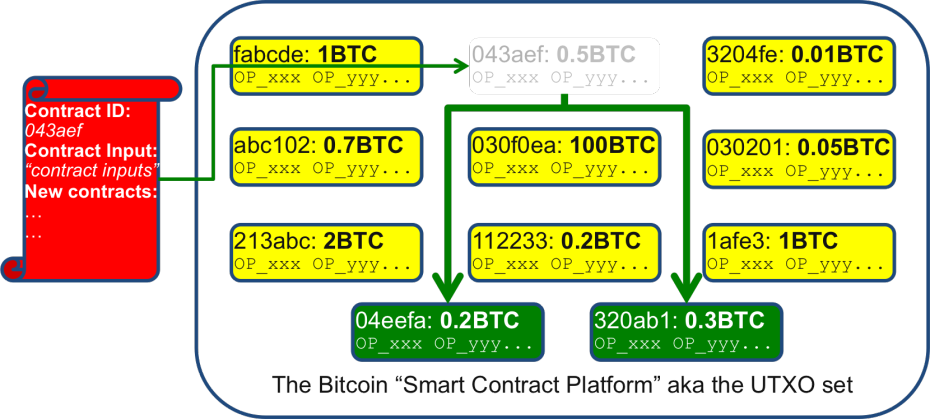 He then goes on to describe the smart contract within the Bitcoin system as two programs: one of which comes from the past, and the other of which is your proving program to say you can get access. Out of this we build payments: each new program sets up an unspent transaction output for the next program, run by your recipient, to prove she is a recipient and can further send the funds.
He then goes on to describe the smart contract within the Bitcoin system as two programs: one of which comes from the past, and the other of which is your proving program to say you can get access. Out of this we build payments: each new program sets up an unspent transaction output for the next program, run by your recipient, to prove she is a recipient and can further send the funds.
Makes sense? Do not be afraid to say it is a bit tricky, and this is the theme I'm developing on. Have a read of @gendal's description and see if you're any the wiser.
Now, I have always eschewed smart contracts because I'm a-feared of their potency "But notice how powerful this is... because the other thing you do is..." and he goes on:
So what does this have to do with smart contracts? The key is that the model I outlined above is quite generic. The programming language is (just about) powerful enough to implement some interesting business logic that goes beyond "Richard paying money to Bob". For example, you can write a program that will only return "TRUE" if you provide proof that you know the private key to multiple bitcoin addresses. This is a way to model "a majority of Board Directors must jointly sign before these funds can be spent", perhaps. The Bitcoin "contracts" wiki page goes into far more depth.
What has got the Bitcoin community so excited is that these smart contracts are *really powerful*. This has led to several rather perverse and contradictory effects which I'll try and list out:
- Firstly, geeks have gone into the smart contracts with expectations of writing very powerful things. Mike Hearn for example has gone for crowd-funding in smart contracts, a business line I heartily approve of (since 1997)!
- However, in contrast to the hype we've only really seen a very small puff of a possibility: the multisig. Not the explosion of possibilities that the hype predicts.
- Perhaps as a response to this Ethereum and others are building the blockchains to run smart contracts in the full vision as promised.
- Now let me drift along here a bit. Smart contracts are like programming, and programming is difficult. So much so that we typically send kids off to university to study the stuff for 4 years before letting them loose on small parts of commercial systems.
- This time, we've got "programming" added to "money". Indeed I call them state machines with money . Double trouble - so we can imagine that this is also going to become a very specialised and tricky area, and it was this combination of explosive elements (including the net, crypto, accounting, etc) that caused the 1990s oldtimers to coin the phrase financial cryptography.
- Now's the time to include the link to the team that writes space shuttle software, because when things go wrong in this area the consequences can be devastating.
My point here isn't that you the Bitcoin geek will find it beyond you. Actually more subtle than this: you will find that you actually do write a smart contract, and it's a lot of fun.
But, others do too. And others do better, as a consequence of the hollywood/star effect, or the grass is always greener. So, you'll be overtaken, and if you're not careful, you lose as well. Money.
This all leads to what the economists call economies of scale . Which is to say that assuming smart contracts are about to take off, we are actually not looking at an empowering technology that returns finance to the people, but quite the reverse: an arms race where the corporation that can muster the most human capital to write these complicated things will dominate.
Or, the government.
Smart contracts are a centralising force, not a decentralising force. Once they get going, they may be unstoppable. Yes you can write your own, but in the same way as you can write your own operating system. Hell, Linus did it, right? But that's part of the point, the only reason you know his name is because he actually succeeded and the other 10000 people who tried this in the 1980s are forgotten.
So in contrast to the normal libertarian rhetoric around self-empowerment, the people's finance, up against the government, what are we likely to see?
As systems start to take off, smart operators will collect groups of programmers and collect their combined effort into frameworks. Which they will sell to customers. It takes capital to do that, so VCs take note of this play, and recall that my day rate is not exorbitant.
These groups will compete and combine .. until we end up with the larger group that can do it all. Is this a market of naturally 4 players (like banks, mobile, accounting) or naturally one player (guilds, landline, governments) ? I don't know yet, but watch for the IPOs.
The libertarians and geeks will rise up and say "open source!" It will be open and empowered and free. Shrug. Have a look at SSL. It's open source, but it is totally and utterly controlled by a few huge corporations: The browsers, the CAs, the Redhats and Akamai's of the world. That's because there are such economies of scale that it takes real capital to bring together the elements to control and build these systems end-to-end. And these companies mob the committees and RFCs and make sure their apple cart is not upset.
Complexity it turns out is not only the enemy of security, it's the enemy of individual empowerment, freedom to contract and all that.
What to do about this? I've written before about the problem of funding the developers in open source projects. It may be that there is still room to "do smart contracts right." In this sense I'm envisaging something like the Blockstream play, which is a company that has collected many of the Bitcoin experts, but it has been financed explicitly by Reid Hoffman on the basis that "we have to do it right, to preserve the commons." This stands in contrast to the efforts of Ethereum and others that are building their platforms as without the limitations of the bitcoin network and without their philosophical guidance: weaponised smart contracts, ready to go.
Maybe there is a play like that which is possible for smart contracts? I don't know. But I do know that the future starts with understanding the forces pushing on the present, and the smart contract does not represent decentralisation but instead will lead to massive centralisation of programming power.
In this sense it's like every other great enabling technology: gunpowder led to cannons, steam led to railroads to WWI, the internet led to cyberwarfare, all stories of centralisation. What can we do to keep smart contracts from not turning into a future disaster against us all?
March 11, 2015
I'm so stupid - The market for aid is a Spence insufficient information market
 I just figured it out, in a flash: Aid is Spencian.
I just figured it out, in a flash: Aid is Spencian.
3 years after my Kenyan adventure started, and I feel like I've got the intellectual dexterity of a slug. But I'm leaving sonic booms running past the World Bank, so maybe relativity is a good thing.
My epiphany was triggered by the fallacy in this article, but it's just another one in a long series of pinpricks to my angst.
And now, everything is explained, or explainable. So, slowing down, take breath, take time to write some words, open the wine. Deep breathing.
Here goes.
The problem with THE AID WORLD, speaking broadly, is observed thusly: we keep doing it, and nothing much happens. In short, the aid budget is approved, carved up into tranches, and the slices and dices get scattered across the poverty-sphere like so much glitter. We sit back as happy church goers and do-gooders and believe we've done our religious duty. We wait for results.
Whatever the psychology of why we do it, what does happen is ... nothing much. The results are always short of expectations.
 OK, so there are some very rare exceptions that we all talk about, but everyone in the business knows how rare they are because they are a household name. That's why we talk about them! I speak of mPesa of course, and ... well I don't actually know another in the last decade, but hey, that's what comments are for. Corrections please.
OK, so there are some very rare exceptions that we all talk about, but everyone in the business knows how rare they are because they are a household name. That's why we talk about them! I speak of mPesa of course, and ... well I don't actually know another in the last decade, but hey, that's what comments are for. Corrections please.
Fact is, most all aid is wasted. Most all government and private sector charity is mostly dead before it gets there, to that country far far away, and what little that does get there is stolen. Often, it is stolen in ways that tick ALL the boxes, and the beneficiaries will debate vociferously that it is not stolen at all, but I will say to you now - it's literally managed out of your hands, and out of the hands of its intended beneficiaries.
Yet we keep doing it. (So do they.) Why? So there are two serious questions here, being why it doesn't work, and why we keep doing it in the face of lifetimes of experience.
And finally it clicks for me: the market for aid is a Spence market in insufficient information. Which explains *everything* I just said, but now we need to walk through what this means. Because Spence is subtlety wrapped in a riddle, encrypted within a fairy tale.
In a Spence market, there is insufficient information, on both sides. This assumes a market where there is a nominal buyer and a nominal seller, but don't get too hung up on that. It's two people and they are trading something: graduates trading with employers, security providers selling to big scared corps, military contractors selling F35s to governments. In this case, there is a donor and a recipient.
 The issue of insufficient information is symmetric -- neither side knows what is needed, nor what the other side wants. In effect, there is a vacuum of information. What happens with a vacuum? Of course, it is filled, by laws of physics. However what it is filled with is not information but "something else" being whatever is to hand.
The issue of insufficient information is symmetric -- neither side knows what is needed, nor what the other side wants. In effect, there is a vacuum of information. What happens with a vacuum? Of course, it is filled, by laws of physics. However what it is filled with is not information but "something else" being whatever is to hand.
Michael Spence postulated in his "Job Market Signalling" paper that what fills the vacuum of information insufficiency are signals. He was quite peculiar about what signals are: they were things that might say something, but actually they were not strong enough to be reliable. Importantly, signals could be misinterpreted to be "what I wanted to be told!"
Oops. We have a market where the information rushes in to fill the vacuum, but the because of the nature of this market, it isn't sufficiently confirming or disconfirming of the product as to generate a useful result. In essence, the signals are interpretable as confirming by the listener, when they may very well be the opposite: disconfirming.
Or, in other words, if we don't know what we're asking for, we shouldn't be surprised when our partner tells us what we'd like to hear. Ask your spouse about that one.
In such a market, Spence postulated that the signals can generate feedback loops which become reinforcing, over time and over cycles, even though they are not actually delivering information, or the information is irrelevant, or even wrong.
 Now - AID. We want to do aid, it's kind of an inbuilt human reflex for good people, as well as a learnt behaviour, and one that generates positive feedback from our peers. So we take a swag of money down to our nearest poor country and hand it over.
Now - AID. We want to do aid, it's kind of an inbuilt human reflex for good people, as well as a learnt behaviour, and one that generates positive feedback from our peers. So we take a swag of money down to our nearest poor country and hand it over.
What does the recipient in our model do?
Whatever the recipient does with the money isn't relevant. What is relevant is what the recipient tells us. He tells us ... what we want to hear. He feeds us the signal. Because of the nature of the market, we can't tell, so we simply are incentivised to believe what he says. Which we do, probably because our motivation is as much about feeling good about ourselves as anything else.
I mean, it's not as if anyone has a good handle on this economic growth thing in the western world, so it would be a miracle if we actually could make it go better in the developed world.
But, leaving aside how we address the paucity of approaches, the result is: neither donor nor recipient *know* anything useful. But the donor is incentivised to invest, and praise the recipient's hard work. Recipient is incentivised to do whatever he is told to, and tell the donor that which he thinks the donor wishes to hear.
In such a market, the signal is misinterpreted, but the market is stable around the signal. Including the misinterpretation; Life goes on. Every aid cycle, the same thing happens, and nobody notices that there is no real tangible confirming information.

Which explains everything: this explains why extremely smart people go to these places and prepare big programmes that cost a *lot* of money. It also explains why the programmes never work, because the information from the recipient isn't precise or rich enough to actually develop a useful programme. It explains why huge numbers of people work on programmes even knowing in their honest moments they don't know what they are doing, and that the system doesn't work.
And it explains why the western aid movement does such terrible damage to these developing peoples -- because the developing peoples keep telling us it's good, in order to get the money. But the corrupting influence of the aid money is so evident on the ground it's not even funny.
 It's utterly, viscerally the saddest thing I've ever seen; rich white people and poor africans, asians, latinos, locked in a deadly embrace of self-harm.
It's utterly, viscerally the saddest thing I've ever seen; rich white people and poor africans, asians, latinos, locked in a deadly embrace of self-harm.
But at least I now have a model to explain this to all those aid / NGOs / governments that haven't a clue. After rain, there can be a small ray of sunshine.
This post is dedicated to the man in the photos, who tore down a mountain. By himself. With no help from the west. (1, 2, 3, 4.)
March 10, 2015
Finally, someone is facing up to the critical problem of our age: Starfighter
 What is the critical problem of our age? Getting people back to productive work.
What is the critical problem of our age? Getting people back to productive work.
The economic statistics in the west are the worst in living memory, all the way back to the Great Depression. Not the official, manipulated political advertisements from the Bureau of Lies, Damn Lies & Statistics, but the anecdotes and wails of our friends and companions who are facing obscurity of unemployment or loss-of-soul with the big 5, no choice, nothing in between.
We -- in the aggregate -- have no understanding of how we got to here, what here is and how we're going to fix the issue.
I know one factor, the Spence observation that we live in an insufficient information age where employers cannot accurately predict employees, and employees likewise cannot see past plastic brand to the wholesomeness of their future career. The result is a deadly embrace of spiralling disquality.
This insight has propelled me along a partial journey to create systems that solve the core dilemma, but what I know and do is not enough. So it is with vicarious pleasure that I share with you:
Announcing StarfighterThomas Ptacek, Erin Ptacek, and I are pleased to announce Starfighter, a company that will publish CTFs (games) that are designed to develop, improve, and assess rare, extremely valuable programming skills.
Starfighter CTFs are not fantastic Hollywood-logic depictions of what programming is like. There is no "I built a GUI interface using Visual Basic to track the IP address."
You will use real technology. You will build real systems. You will face the real problems faced by the world's best programmers building the world's most important pieces of software.
You will conquer those problems. You will prove yourself equal to the very best. Becoming a top Starfighter player is a direct path to receiving lucrative job offers from the best tech companies in the world, because you'll have proven beyond a shadow of a doubt that you can do the work these companies need done.
We're not here to fix the technical interview: we're here to destroy it, and create something new and better in its place. ...
February 16, 2015
Google's bebapay to close down, Safaricom shows them how to do it
In news today, BebaPay, the google transit payment system in Nairobi, is shutting down. As predicted in this blog, the payment system was a disaster from the start, primarily because it did not understand the governance (aka corruption) flow of funds in the industry. This resulted in the erstwhile operators of the system conspiring to make sure it would not work.

How do I know this? I was in Nairobi when it first started up, and we were analysing a lot of market sectors for payments technology at the time. It was obvious to anyone who had actually taken a ride on a Matatu (the little buses that move millions of Kenyans to work) that automating their fares was a really tough sell. And, once we figured out how the flow of funds for the Matatu business worked, from inside sources, we knew a digital payments scheme was dead on arrival.
As an aside there is a play that could have been done there, in a nearby sector, which is the tuk-tuks or motorbike operators that are clustered at every corner. But that's a case-study for another day. The real point to take away here is that you have to understand the real flows of money, and when in Africa, understand that what we westerners call corruption means that our models are basically worthless.
Or in shorter terms, take a ride on the bus before you decide to improve it.
Meanwhile, in other news, Safaricom are now making a big push into the retail POS world. This was also in the wings at the time, and when I was there, we got the inside look into this field due to a friend who was running a plucky little mPesa facilitation business for retails. He was doing great stuff, but the elephant in the room was always Safaricom, and it was no polite toilet-trained beast. Its reputation for stealing other company's business ideas was a legend; in the payment systems world, you're better off modelling Safaricom as a bank.
Ah, that makes more sense... You'll note that Safaricom didn't press over-hard to enter the transit world.
The other great takeway here is that westerners should not enter into the business of Africa lightly if at all. Westerners' biggest problem is that they don't understand the conditions there, and consequently they will be trapped in a self-fulfilling cycle of western psuedo-economic drivel. Perhaps even more surprising, they also can't turn to their reliable local NGOs or government partners or consultancies because these people are trained & paid by the westerners to feed back the same academic models.
 How to break out of that trap economically is a problem I've yet to figure out. I've now spent a year outside the place, and I can report that I have met maybe 4 or 5 people amongst say 100 who actually understand the difference? Not a one of these is employed by an NGO, aid department, consultant, etc. And, these impressive organisations around the world that specialise in Africa are in this situation -- totally misinformed and often dangerously wrong.
How to break out of that trap economically is a problem I've yet to figure out. I've now spent a year outside the place, and I can report that I have met maybe 4 or 5 people amongst say 100 who actually understand the difference? Not a one of these is employed by an NGO, aid department, consultant, etc. And, these impressive organisations around the world that specialise in Africa are in this situation -- totally misinformed and often dangerously wrong.
I feel very badly for the poor of the world, they are being given the worst possible help, with the biggest smile and a wad of cash to help it along its way to failure.
Which leads me to a pretty big economic problem - solving this requires teaching what I learnt in a few years over a single coffee - can't be done. I suspect you have to go there, but even that isn't saying what's what.
Luckily however the developing world -- at least the parts I saw in Nairobi -- is now emerging with its own digital skills to address their own issues. Startup labs abound! And, from what I've seen, they are doing a much better job at it than the outsiders.
So, maybe this is a problem that will solve itself? Growth doesn't happen at more than 10% pa, so patience is perhaps the answer, not anger. We can live and hope, and if an NGO does want to take a shot at the title, I'm in for the 101th coffee.
February 03, 2015
News that's news: Kenya's M-Kopa Solar Closes $12.45m
 If there's any news worth blogging about, it is this:
If there's any news worth blogging about, it is this:
Breaking: Kenya's M-Kopa Solar Closes $12.45 million Fourth Funding Round
M-KOPA Solar has today closed its fourth round of investment through a $12.45 million equity and debt deal, led by LGT Venture Philanthropy. The investment will be used to expand the company's product range, grow its operating base in East Africa and license its technology to other markets.
Lead investor LGT Venture Philanthropy has backed M-KOPA since 2011 and is making its biggest investment yet in the fourth round, which also includes reinvestments from Lundin Foundation and Treehouse Investments (advised by Imprint Capital)and a new investment from Blue Haven Initiative.
In less than two and a half years since launch, M-KOPA Solar has installed over 150,000 residential solar systems in Kenya, Uganda and Tanzania, and is now connecting over 500 new homes each day. The company plans to further expand its distribution and introduce new products to reach an even larger customer base.
Jesse Moore, Managing Director and Co-Founder M-KOPA Solar says, "Our investors see innovation and scale in what M-KOPA does. And we see a massive unmet market opportunity to provide millions of off-gridhouseholds with affordable, renewable energy. We are just getting started in terms of the scale and impact of what we will achieve.
Oliver Karius, Partner, LGT Venture Philanthropy says, "We believe that we are at the dawn of a multi-billion dollar 'pay-as-you-go' energy industry. LGT Venture Philanthropy is a long-term investor in M-KOPA Solar because they've proven to be the market leaders,both in terms of innovating and delivering scale. We have also seen first-hand what positive impacts their products have on customers lives - making low-income households wealthier and healthier."
This deal follows the successful $20 million (KES1.8 billion) third round funding closed in December 2013 - which featured a working capital debt facility, led by the Commercial Bank of Africa.
The reason this is real news in the "new" sense is that indigenous solutions can work because they are tailored to the actual events and activities on the ground. In contrast, the western aid / poverty agenda typically doesn't work and does more harm than good, because it is an export of western models to countries that aren't aligned to those assumptions. Message to the west: Go away, we've got this ourselves.
December 27, 2014
In-depth history: "SEALAND, HAVENCO, AND THE RULE OF LAW"
Graeme tips me to a fascinating in-depth review of the law aspects of Sealand and HavenCo, which makes essential reading for the libertarian / anarchist school of Internet entrepreneurialship:
SEALAND, HAVENCO, AND THE RULE OF LAW James GrimmelmannIn 2000, a group of American entrepreneurs moved to a former World War II antiaircraft platform in the North Sea, seven miles off the British coast. There, they launched HavenCo, one of the strangest start-ups in Internet history. A former pirate radio broadcaster, Roy Bates, had occupied the platform in the 1960s, moved his family aboard, and declared it to be the sovereign Principality of Sealand. HavenCo's founders were opposed to governmental censorship and control of the Internet; by putting computer servers on Sealand, they planned to create a "data haven" for unpopular speech, safely beyond the reach of any other country. This Article tells the full story of Sealand and HavenCo -- and examines what they have to tell us about the nature of the rule of law in the age of the Internet.
The story itself is fascinating enough: it includes pirate radio, shotguns, rampant copyright infringement, a Red Bull skateboarding special, perpetual motion machines, and the Montevideo Convention on the Rights and Duties of State. But its implications for the rule of law are even more remarkable. Previous scholars have seen HavenCo as a straightforward challenge to the rule of law: by threatening to undermine national authority, HavenCo was opposed to all law. As the fuller history shows, this story is too simplistic. HavenCo also depended on international law to recognize and protect Sealand, and on Sealand law to protect it from Sealand itself. Where others have seen HavenCo's failure as the triumph of traditional regulatory authorities over HavenCo, this Article argues that in a very real sense, HavenCo failed not from too much law but from too little. The "law" that was supposed to keep HavenCo safe was law only in a thin, formalistic sense, disconnected from the human institutions that make and enforce law. But without those institutions, law does not work, as HavenCo discovered.
(Disclosure: I knew the founders of HavenCo who were all at one time residing on CryptoHill in Anguilla.)
November 21, 2014
Banking - licensed to cheat! And whether you'll get away with it.
Research into what most people will feel is so trivially true that the research wasn't needed has been conducted -- are bankers cheats?
The subjects took part in a simple experiment of flipping a coin, and involved around two hundred bankers, including 128 from a single unnamed international bank. They were divided into two groups. The people from the first were asked specifically about their jobs in banking, while the other half were asked unrelated questions."The rules required subjects to take any coin, toss it 10 times, and report the outcomes online," the researchers reported in the journal Nature. "For each coin toss they could win an amount equal to approximately $20 depending on whether they reported 'heads' or 'tails'."
The point is that the players were told ahead of the game whether "heads" or "tails" would win as well as in which case they could keep their winnings.
Given maximum winnings of $200, there was "a considerable incentive to cheat," wrote the team of researchers.
The bankers were asked to fill out questionnaires before tossing each coin. Those who were asked about things unrelated to their job hardly ever cheated in the coin toss, reporting 51.6 percent wins.
But those asked about their banking careers made the cheat rate go up - they reported 58.2 percent as wins. If everyone was completely honest, the proportion of winning tosses in each group would be 50 percent.
That's actually a stunning result. Just talking about banking made the bankers cheat! As an aside, this research is a dead cert for the IgNoble awards, a sort of faux Noble in odd science which celebrates wacky research that on the face of it should not have been conducted, but in actuality reveals some interesting results.
Back to the banking cheats. Up until now, there has been a stunning silence on the behalf of the prosecution authorities for what is likely either the #1 or #2 crisis in modern history. So bankers are confirmed in their skulduggery, they will almost certainly get away with it.
What can we as society do about this? Putting some of them in jail has been commented as what is missing, indeed the reason we're likely confirmed that banking as a whole is a poisoned pot is that nobody's gone to jail for the financial crisis.
In Britain, last month, a crown court in London announced:
"A senior banker from a leading British bank pleaded guilty at Southwark Crown Court on 3 October 2014 to conspiracy to defraud in connection with manipulating Libor," the court said in a statement."This arises out of the Serious Fraud Office investigations into Libor fixing."
And, in Iceland a world-wide first:
Nov 19 (Reuters) - The former chief executive of Landsbanki, one of three banks that racked up $75 billion in debt before collapsing and crashing the economy in 2008, was sentenced to one year in jail on Wednesday for market manipulation.Sigurjon Arnason was convicted of manipulating the bank's share price and deceiving investors, creditors and the authorities in the dying days of the bank between Sept. 29 and Oct. 3, 2008.
The Reykjavik District Court said nine months of Arnason's sentence were suspended. Ivar Gudjonsson, former director of proprietary trading, and Julius Heidarsson, a former broker, were also convicted and received nine-month sentences, six of which were suspended. All pleaded innocent to the charges.
"This sentence is a big surprise to me as I did not nothing wrong," Sigurjon Arnason told Reuters after the sentencing, adding that he and his attorney had not yet decided whether to appeal to the supreme court.
More:
In receiving a one year prison sentence, Sigurjon Arnason officially became the first bank executive to be convicted of manipulating the bank's stock price and deceiving investors, creditors and the authorities between Sept. 29 and Oct. 3, 2008, as the bank's fortunes unwound, crashing the economy with it. Landsbanki was one of three banks that had tallied nearly $75 billion in debt before the final curtain was drawn.All pleaded innocent to the charges...
November 08, 2014
Alex explains ZIRP -- why 7 years of easy central bank money didn't go far
For those who missed out on why the world's combined 7 year money splurge achieved nothing, here's an answer.

ZIRP = zero interest rate policy, as conducted by Federal Reserve and ECB.
Alex's view above is not so far from the truth. The money primarily went into direct speculation into all manner of financial assets, creating a markets bubble that all large financial players benefited from. The easy money went via hedge funds into stock markets, and then into each other's stock price. Hence, financial markets reflected nicely the 'recovery' that was not seen outside the numbers machine.
What is the case is that all the money went into the banks, but did not come out in the form of loans to industry; thus showing that the central bank's interest rate monetary tool is broken in the current financial depression.
November 01, 2014
America's other financial crisis - student debt
From the BBC, snipped:
An activist group in the United States has been carrying out deeds that some might think the stuff of dreams - buying and cancelling other people's student debts.Rolling Jubilee has purchased and abolished $3.8m (£2.35m) of debt owed by 2,700 students, paying just over $100,000 (£62,000), or as it says, "pennies on the dollar".
[snip...]
Debts can be bought and sold in the financial marketplace. But student debt, which has spiralled to an estimated $1.2 trillion (£619bn), is not usually as available to buy as other debts, such as unpaid medical bills.In this speculative secondary market, third parties buy debt for a fraction of its original cost and try to collect the full amount from debtors.
But these debt campaigners are buying debts and then writing them off.
Debts on saleThe student loan debts cleared by Rolling Jubilee were for students from Everest Colleges, a string of institutions owned by Corinthian Colleges, a for-profit education company.
[snip...]
Student debt can pursue people all through their working lives and into retirement. The United States Government Accountability Office published figures last month showing there were more than 700,000 households with people aged over 65 still repaying student debt.These pensioners still owed more than $18bn (£11bn) - and officials giving evidence to a US Senate committee said this could mean that student debt repayments could be deducted from retired people's social security benefits.
More than half of student debtors who are over 75 are in default on their loans.
'Symbolic' work
This week, the Federal Reserve chief Janet Yellen warned the quadrupling of the student loan debt since 2004 represented a barrier to social mobility.
John Aspray, national field director at the United States Student Association (USSA), said recent changes in law mean people in medical or gambling debt can declare themselves bankrupt - but to do so for student debt means satisfying an '"undue hardship" criteria, which is very difficult to prove.
"Opportunities for renegotiating are very well hidden," he says.
He says Rolling Jubilee's work was "important and symbolic" as a lot of people "don't even consider" getting rid of their debt.
As 85% of student loans are guaranteed by the national government the USSA is putting pressure on the department to "cut contracts with the worse corporations", says Mr Aspray.
In sum. Some politician's dream of everyone-a-degree has created an unsustainable bubble in student debt slavery. Coupled with the current depression in USA, this means an incredible drag on the mid-range of the middle class for the next 30 years.
Oh dear. It also likely presages the collapse of the university sector as the bubble peaks and drops; many universities will not be able to cope with the halving of student numbers.
October 12, 2014
In the Shadow of Central Banking
A recent IMF report on shadow banking places it at in excess of $70 trillion.
"Shadow banking can play a beneficial role as a complement to traditional banking by expanding access to credit or by supporting market liquidity, maturity transformation and risk sharing," the IMF said in the report. "It often, however, comes with bank-like risks, as seen during the 2007-08 global financial crisis."
It's a concern, say the bankers, it keeps the likes of Jamie Dimon up at night. But, what is it? What is this thing called shadow banking? For that, the IMF report has a nice graphic:
Aha! It's the new stuff: securitization, hedge funds, Chinese 'wealth management products' etc. So what we have here is a genie that is out of the bottle. As described at length, the invention of securitization allows a shift from banking to markets which is unstoppable.
In theoretical essence, markets are more efficient than middlemen, although you'd be hard pressed to call either the markets or banking 'efficient' from recent history.
Either way, this genie is laughing and dancing. The finance industry had its three wishes, and now we're paying the cost.
September 03, 2014
Proof of Work made useful -- auctioning off the calculation capacity is just another smart contract
 Just got tipped to Andrew Poelstra's faq on ASICs, where he says of Adam Back's Proof of Work system in Bitcoin:
Just got tipped to Andrew Poelstra's faq on ASICs, where he says of Adam Back's Proof of Work system in Bitcoin:
In places where the waste heat is directly useful, the cost of mining is merely the difference between electric heat production and ordinary heat production (here in BC, this would be natural gas). Then electricity is effectively cheap even if not actually cheap.
Which is an interesting remark. If true -- assume we're in Iceland where there is a need for lots of heat -- then Bitcoin mining can be free at the margin. Capital costs remain, but we shouldn't look a gift horse in the mouth?
My view remains, and was from the beginning of BTC when Satoshi proposed his design, that mining is a dead-weight loss to the economy because it turns good electricity into bad waste, heat. And, the capital race adds to that, in that SHA2 mining gear is solely useful for ... Bitcoin mining. Such a design cannot survive in the long run, which is a reflection of Gresham's law, sometimes expressed as the simplistic aphorism of "bad money drives out good."
Now, the good thing about predicting collapse in the long run is that we are never proven wrong, we just have to wait another day ... but as Ben Laurie pointed out somewhere or other, the current incentives encourage the blockchain mining to consume the planet, and that's not another day we want to wait for.
Not a good thing. But if we switch production to some more socially aligned pattern /such as heating/, then likely we could at least shift some of the mining to a cost-neutrality.
Why can't we go further? Why can't we make the information calculated socially useful, and benefit twice? E.g., we can search for SETI, fold some DNA, crack some RSA keys. Andrew has commented on that too, so this is no new idea:
7. What about "useful" proofs-of-work?These are typically bad ideas for all the same reasons that Primecoin is, and also bad for a new reason: from the network's perspective, the purpose of mining is to secure the currency, but from the miner's perspective, the purpose of mining is to gain the block reward. These two motivations complement each other, since a block reward is worth more in a secure currency than in a sham one, so the miner is incentivized to secure the network rather than attacking it.
However, if the miner is motivated not by the block reward, but by some social or scientific purpose related to the proof-of-work evaluation, then these incentives are no longer aligned (and may in fact be opposed, if the miner wants to discourage others from encroaching on his work), weakening the security of the network.
I buy the general gist of the alignments of incentives, but I'm not sure that we've necessarily unaligned things just by specifying some other purpose than calculating a SHA2 to get an answer close to what we already know.
Let's postulate a program that calculates some desirable property. Because that property is of individual benefit only, then some individual can pay for it. Then, the missing link would be to create a program that takes in a certain amount of money, and distributes that to nodes that run it according to some fair algorithm.
What's a program that takes in and holds money, gets calculated by many nodes, and distributes it according to an algorithm? It's Nick Szabo's smart contract distributed over the blockchain. We already know how to do that, in principle, and in practice there are many efforts out there to improve the art. Especially, see Ethereum.
 So let's assume a smart contract. Then, the question arises how to get your smart contract accepted as the block calculation for 17:20 on this coming Friday evening? That's a consensus problem. Again, we already know how to do consensus problems. But let's postulate one method: hold a donation auction and simply order these things according to the amount donated. Close the block a day in advance and leave that entire day to work out which is the consensus pick on what happens at 17:20.
So let's assume a smart contract. Then, the question arises how to get your smart contract accepted as the block calculation for 17:20 on this coming Friday evening? That's a consensus problem. Again, we already know how to do consensus problems. But let's postulate one method: hold a donation auction and simply order these things according to the amount donated. Close the block a day in advance and leave that entire day to work out which is the consensus pick on what happens at 17:20.
Didn't get a hit? If your smart contract doesn't participate, then at 17:30 it expires and sends back the money. Try again, put in more money? Or we can imagine a variation where it has a climbing ramp of value. It starts at 10,000 at 17:20 and then adds 100 for each of the next 100 blocks then expires. This then allows an auction crossing, which can be efficient.
An interesting attack here might be that I could code up a smartcontract-block-PoW that has a backdoor, similar to the infamous DUAL_EC random number generator from NIST. But, even if I succeed in coding it up without my obfuscated clause being spotted, the best I can do is pay for it to reach the top of the rankings, then win my own payment back as it runs at 17:20.
With such an attack, I get my cake calculated and I get to eat it too. As far as incentives go to the miner, I'd be better off going to the pub. The result is still at least as good as Andrew's comment, "from the network's perspective, the purpose of mining is to secure the currency."
What about the 'difficulty' factor? Well, this is easy enough to specify, it can be part of the program. The Ethereum people are working on the basis of setting enough 'gas' to pay for the program, so the notion of 'difficulty' is already on the table.
I'm sure there is something I haven't thought of as yet. But it does seem that there is more of a benefit to wring from the mining idea. We have electricity, we have capital, and we have information. Each of those is a potential for a bounty, so as to claw some sense of value back instead of just heating the planet to keep a bunch of libertarians with coins in their pockets. Comments?
July 22, 2014
How Central Banking magnifies the Crisis and ensures Depression
he current times are fantastic opportunities for a new generation of economists to cut their teeth, albeit in studying the misery of us all. Here's some of that, cutting of teeth or gnashing, you decide. H/t to Arthur, here is the punchline from "Banks, government bonds, and default: What do the data say?" from Nicola Gennaioli, Alberto Martin, Stefano Rossi:
The transmission mechanismOur results support the notion that banks’ holdings of public bonds are an important transmission mechanism from sovereign defaults to bank lending. These findings are broadly consistent with the following narrative. Public bonds are very liquid assets (e.g. Holmstrom and Tirole 1998) that play a crucial role in banks’ everyday activities, like storing funds, posting collateral, or maintaining a cushion of safe assets (Bolton and Jeanne 2012, Gennaioli et al. 2014a). Because of this, banks hold a sizeable amount of government bonds in the course of their regular business activity, especially in less financially developed countries where there are fewer alternatives. When default strikes, banks experience losses on their public bonds and subsequently decrease their lending. During default episodes, moreover, some banks deliberately hold on to their risky public bonds while others accumulate even more bonds. This behaviour could reflect banks’ reaching for yield (Acharya and Steffen 2013), or it could be their response to government moral suasion or bailout guarantees (Livshits and Schoors 2009, Broner et al. 2014). Whatever its origin, this behaviour is largely concentrated in a set of large banks, and is associated with a further decrease in bank lending.
There you have it. In short human words, the need for banks to hold the bonds of their government becomes a limit on their lending activity. As they enter crisis (the banks, the government or the economy), the banks are incentivised to hold more bonds. As they hold more bonds, their lending decreases.
Reducing lending confirms the recession, and indicates why we now see full depression in Southern Europe.
I've oft ruminated on the failure of economics that is central banking; it works until it doesn't. Central banking works thusly:
- the government wants someone to hold their bonds.
- it needs a central bank to regulate the banks,
- to insist that the banks hold their bonds.
- The quid pro quo for this is that central banks will backstop the banks.
- So, happily, the government can now issue more bonds than is good for it,
- force the banks and itself into trouble, and
- pass the cost onto the public (inflation or bailouts).
Notice that part 7 -- the cost of central banking always ends up with the citizen through either bailout (taxpayer) or inflation (money-holder). One destroys the middle classes, the other penalises the poor through their cash holdings. (The rich know that the safe money is now in owning and running the banks, who win always because they are rarely forced into real bankruptcy.)
One thing that strikes from that is the history of banking (c.f. Dowd especially) suggests that the requirement to hold state bonds is what brought the end to free banking in the USA. Now fast forward to Europe, and what brought the end was banks and governments over-extended in a deadly embrace.
The common factor is the lack of ability to inflate. The individual states in the USA weren't able to issue their own dollar, because money was competitive. The individual states in Europe are likewise unable to inflate away their trouble, because they gave that up to ECB.
What's left is bailouts.
Postscript, adding the graph that Patrick refers to in comments:
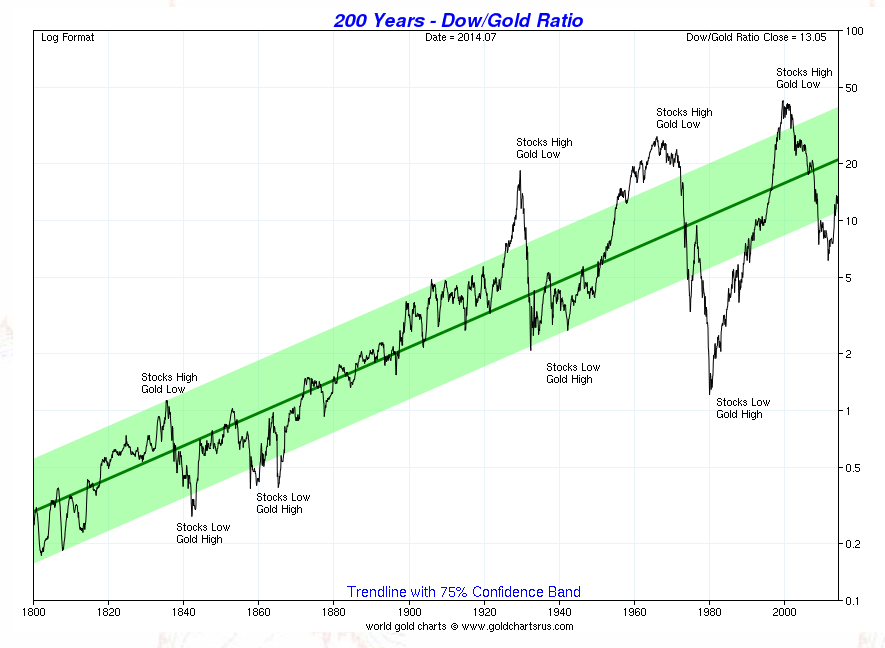
July 13, 2014
The end of Central Banking -- Germany moves on bail-in
I called the end of Central Banking many moons ago, which of course went down like a lead balloon. Now, in the post-Cyprus era, we see that one of the legs of Central Banking -- the rescue of the failed bank -- is being unwound:
BERLIN--Germany's cabinet Wednesday approved plans to force creditors into propping up struggling banks beginning in 2015, one year earlier than required under European-wide plans that set rules for failing financial institutions.The new bail-in rules are part of a package of German legislation on the European banking union--an ambitious project to centralize bank supervision in the euro zone and, when banks fail, to organize their rescue or winding-up at a European level.
Germany "leads the way" in Europe by implementing European rules quickly and "creates instruments that allow the winding-down of big systemically relevant institutions without putting the financial stability at risk," the country's finance ministry said in its draft bill seen by The Wall Street Journal.
"This ensures that in times of crisis mainly owners and creditors will contribute to solving the crisis, and not taxpayers."
It is probably clear to most Euro-skeptics that the (a) nothing has been fixed, and (b) the troika cannot handle anymore bailouts. At least, it's more clear to the Germans, who have their own problems:
I have warned that about 50% of the German municipalities are on the verge of bankruptcy. The pensions have been unfunded and are absorbing everything. As we saw in Detroit with more than 50% of current revenue going to pensions, taxes either rise, the borrow more, or they are out of business. We are in a giant bull market for taxes increases on every level. This is the real downside of Marxism – they theory that just keeps taking.
Central Banking is unsustainable in our interconnected world. It's also unnecessary, as the invention of securitization, and other financial cryptography inventions to come are removing the fundamental economics need for the banking charter.
However, the way Central Banking dies is difficult to predict. The behemoths that they allowed to grow and devour still have much fat to carry them forward, and the Central Banks themselves aren't ready to call it a day. The carnage will continue for a while.
June 20, 2014
Signalling and MayDay PAC

There's a fascinating signalling opportunity going on with US politics. As we all know, 99% the USA congress seats are paid for by contributions from corporate funders, through a mechanism called PACs or political action committees. Typically, the well-funded campaigns win the seats, and for that you need a big fat PAC with powerful corporate wallets behind.
Lawrence Lessig decided to do something about it.
"Yes, we want to spend big money to end the influence of big money... Ironic, I get it. But embrace the irony."
So, fighting fire with fire, he started the Mayday PAC:
"We’ve structured this as a series of matched-contingent goals. We’ve got to raise $1 million in 30 days; if we do, we’ll get that $1 million matched. Then we’ve got to raise $5 million in 30 days; if we do, we’ll get that $5 million matched as well. If both challenges are successful, then we’ll have the money we need to compete in 5 races in 2014. Based on those results, we’ll launch a (much much) bigger effort in 2016 — big enough to win."
They got to their first target, the 2nd of $5m will close in 30th June. Larry claims to have been inspired by Aaron Swartz:
“How are you ever going to address those problems so long as there’s this fundamental corruption in the way our government works?” Swartz had asked.
Something much at the core of the work I do in Africa.
The signalling opportunity is the ability to influence total PAC spending by claiming to balance it out. If MayDay PAC states something simple such as "we will outspend the biggest spend in USA congress today," then how do the backers for the #1 financed-candidate respond to the signal?
As the backers know that their money will be balanced out, it will no longer be efficacious to buy their decisions *with the #1 candidate*. They'll go elsewhere with their money, because to back their big man means to also attract the MayDay PAC.

Which will then leave the #2 paid seat in Congress at risk ... who will also commensurately lose funds. And so on ... A knock-on effect could rip the funding rug from many top campaigns, leveraging Lessig's measly $12m way beyond its apparent power.
A fascinating experiment.
The challenge of capturing people’s attention isn’t lost on Lessig. When asked if anyone has told him that his idea is ludicrous and unlikely to work, he answers with a smile: “Yeah, like everybody.”
Sorry, not this anybody. This will work. Economically speaking, signalling does work. Go Larry!
May 11, 2014
(B) The Business Choice of making a Business Investment in Bitcoin (part B of ABC)
Last month, I launched a rocket at those who invest in Bitcoin as the Coin or the Currency. It's bad, but I won't repeat the arguments against it.
For those of you who've survived the onslaught on your sensitivities, and are genuinely interested in how to make an investment into the cryptocurrency world, here is part B: the Business! The good news is that it is shorter.
If one was to look for a good Bitcoin investment in a business, what would it be? I think you should be asking questions like these:
- The business in question has a regulatory model. It doesn't need to be right or sustainable, more that the business owners just need to understand the word. That's because, whether they know it or not, the word is coming for them one day.
- hey have a governance model. Ditto.
- You as investor understand the difference. This is where it gets messy. Most people think the above two terms are the same thing, but they are not. A regulatory model is imposed by a regulator, and is mostly about compliance with something that protects others such as the regulator or their flock (banks). Whereas a governance model is imposed by yourself, over your own operations, to protect your assets and the assets of the customer. Completely different, and completely misunderstood in the eyes of the external stakeholder community. Therefore, likely misaligned in the eyes of the Bitcoin CEO. Do you see where this is going?
- They have a Sean Parker. By this, I mean the person with real experience of this broad Internet / money / social networking business space, the guy who's been there twice before, and this time, *he's there* at the critical juncture to that 2 kids and a fridge full of beer all the way to a big business. See the Facebook movie if this doesn't make any sense.
Signs of a bad investment:
- Wanting to be the next big exchange.
- No relevant experience in the chosen direct business model. This is distinct from the Sean Parker point above. By this I mean, if wanting to do an exchange, the people have / do not have (select one) prior experience in what a daily trading model is, what 5PM is, what governance is, what an internet security model is. E.g., Mt Gox, which traded without understanding any of these things.
- Belief that tech solves all problems.
- No knowledge of what came before the Bitcoin paper.
- Deal hinges in part on banks or regulators. For example, these guys are DITW:
Part of laying the groundwork is bringing the establishment on board, Malka said. “We need more banks participating in this. We need regulators. I’m part of the Bitcoin Foundation – we are out there trying to educate regulators.” Getting regulators on board will help get the banks to come along, Liew predicted. “If the regulators explicitly set forth rules that say, ‘Bright line, do this, you will find a bank that is willing to take on bitcoin customers,’” Liew said.
That's my B list so far. You'll note that it includes no conventional things, because you already have those. All it includes is pointers to the myths-of-doom peddled in the current bitcoin world as business talk. It's designed to separate out the happy hopefuls from the actual business possibilities, in a world where talking is deeper than walking.
Next up, when I get to it, is my A list: a point I believe so important I saved it for another post. Watch this space.
April 22, 2014
(C) The ABC of Making the Bitcoin Investment Decision - part C first - Currency, buy the Coin!
Preamble. In the last recent months I've seen a lot of interest in the question of what makes a good Bitcoin investment. I may not be the best person to make this call, but as I'm a reluctant skeptic, I may not be the worst person either. Most of the people I speak to are either confirmed believers, or they are people who are afraid of missing the boat. In either case, they haven't got a lot of critical analysis to offer, and as I've been there several times already, it seems I might have. I've been speaking on this issue at the moment in multiple fora, so I've been forced to put my thoughts in order. (Fair Warning. Long post ahead...)
Call this my ABC of Bitcoin investment. In reverse order, C for Currency. Put your coin on the table, and read on!
The first decision that hits the erstwhile investor in Bitcoin is this: to bet on the currency or to bet on the business?
Currency or business ?
can be seen as a diversification question. If you buy the coin, you are investing in the entire market, because, as the theory goes, it goes up with the fortunes of everyone, and comes down alike.
Diversification is a good strategy, and according to the efficient market hypothesis it is the only strategy that makes sense to a non-insider. In the stock market, this means buying a stock index fund, which is hated by the banks because they can't push your trades around and make fees off you. Which alone tells you diversification is a winner, and for these and other reasons, index funds typically perform in the top half of funds.
The strategy could be considered a good thing. Buying the currency could make you a smart investor!
It is also rather unique. For example, when you bought into that Internet boom in a big way in the 1990s, or the social networking of the 2000s, it wasn't possible to "buy the net!" Then, you had to make a more precise investment decision e.g., B for Business, which I leave to another post.
This time around, you can buy the coin literally, and see afar from everyone else's tall shoulders. What could make more sense?
I would however like to raise a bit of a red flag. Buying the coin might actually make a lot less sense than at first blanche. Let's work it through.
Unlike the stock market, the Bitcoin unit hasn't got the same longevity. The LSE, NASDAQ, Nikkei, etc will be around next year, in 10 years, and in some form in 100 years. Bitcoin might not be. It might be the Ripple or the Ethereum or the Bitcoin2.0 or any other strange and interesting name. Or Bitcoin might be a totally regulated thing, or it might be only traded in China, or it might be illegal or ...
The point being that there are a lot of potential futures. Which leads to issue number 1:
it's more a speculation than an investment
That part is obvious, but if it is so short-term, why does it gain in value? Bitcoin is rising in value rapidly because people are piling money into it on the expectation of future rewards.
We have a word for this: bubble.
Then, the second problem with investing in the currency, and holding it, is that you are now participating in the expectation of a rise of value for no work put in. Indeed, by deciding to invest, you are confirming that it is a bubble. Hence, caveat #2:
you are now part of the bubble!
Being part of a bubble isn't necessarily bad, yet. People participate in the stock market bubble or the real estate bubble all the time, and life goes on. Entire countries participate in the pension bubble, and nobody blinks!
As long as you don't lose money, you're fine. And, as long as you have no explaining to do, you're fine. If you're in a fund where risk taking is the idea, then this is a good thing. If however you feel that you need to explain to your upstream investors how you made your decisions on investment, and bubbles do not form part of that explanation, you might want to try an alternate strategy. Institutional or pension money might want to steer clear, whereas VC and hedgefund money might see this as the green light.
Let's assume today I am writing to angels and VCs, and let's pursue those bubble rewards.
There is, excitingly or sadly, more to come. Bitcoin is currently in a sort of early life crisis. As lifecycles go, it's discovered limbs and crawling and attempts at walking. And typically we get a lot of flailing and yelling and falling. Mt Gox is the canonical case, and it looks just like that, a toddler getting a few steps down the hall before collapsing in a heap. Then, tears.
Which highlights a particular difficulty. It is easy to buy Bitcoin, but it is harder to sell it. It turns out that the market is perhaps more illiquid than the glossy website stats indicate, for reasons of depth (lack of big buyers), fraud (which is what Mt Gox probably is) and gross mismanagement (ditto).
Unlike stock markets, if you've just put $75m of VC cash into Bitcoin currency, you have just purchased yourself a rather nasty little problem #3:
you can't sell out!
At an absolute minimum, you may not be able to shift the value without moving the market so far it loses your value, an issue investors in the HFT game know well. In practice, you may not be able to sell it at all, or you may have to wait months, or you may watch the value go down the tubes, to the point where you're left with pennies on the coin.
Or you may discover it was for sale, but now it's nowhere to be found.
Now you have more explaining to do. If you hold a cash instrument that can't be shifted, you can't mark it to market, you can't book it as liquid. You haven't got cash, it's starting to look just as liquid as holding startup stock (that is, not liquid), but without the business rationale backing it.
Did we say speculation or investment?
Worse, your upstream investors aren't going to buy that story, as they'll be watching the price on exchanges and ask you why you didn't shift it? They'll give you plenty of advice about who has the hottest exchange this month, but it will be you who is hitting the send button and relying on the promises of that shiny new website with the street address you can't pronounce.
Which leads us to the next problem:
can you pick the burst of the bubble?
Bubbles always burst. You the venture capitalist might be measured more on the fall from the peak than the rise from original investment, which will be booked as profit well before you get lucky on that score. So you are now on a very wild ride, where your decision will cast your future in an entirely positive light, or a disaster.
Let's cut to the chase: the only theory that we know of about picking the bursting of the bubble is the one of being lucky. Someone always sells just before the peak, and close investigation reveals that those people are often saying the same thing that everyone else is saying. When we strip out the factors we can scientifically identify, we're left with mostly luck.
Are you lucky?
To avoid the curse of excessive luck we typically suggest ... wait for it ... Diversification! And therein lies the rub. Although you've diversified from the risk of business collapse, you've just picked up other risks, being bubble popping, liquidity and fraud. Indeed, given the nature of Bitcoin, I think we can pretty much dismiss /buying the coin/ as a diversified strategy across the business of Bitcoin.
We are talking then not about a diversified strategy at all. Rather, buying the coin is a precise investment on a particular instrument -- the herd. Which means two things.
Firstly, blowing the bubble, as opposed to pricking the bubble. This is the pernicious issue of the mechanics of a bubble -- ever wonder why everyone in the Bitcoin community is a total believer? Now you're about to find out.
You've staked your future on the Bitcoin bubble. The only way that a bubble grows is if more people come in than go out. Or, more money, in than out.
As you are now invested in a bubble this means your incentives are now aligned with growing the bubble.
Where do those people and their money come from, once you personally are "all in"? Well, as it's not an economics simulation or a government policy, these new people do not exist in isolation or as mere statistics. You can't just push a button or wind up a knob or make a campaign promise, now you have to make it happen.
New investors are probably people you know, in your world. If you're a VC, new people are other VCs you chat to at the bar. If you're an angel, it's all the others in the angel meetup.
As you're now aligned to growing the bubble, *you want your friends in* !
And that's the crux. Having invested in a bubble, you now want people to pump up your investment. Which leads to two paths in your life:
Path one is the believer. You decide that there is no bubble, and therefore no bursting, or you consider it isn't relevant or will pass or it's a momentary hiccup or somesuch. You can comfortably turn your entire philosophy over to Bitcoinmania, and this is the future. You are a believer, and no analysis to the contrary is necessary or applicable.
Path two is the opportunist. You agree there is a bubble, and it will burst, but you are gambling that you can get out before it bursts.
Either way, in the meantime, the fundamental is true:
you have to recruit all your friends, relatives, partners, contacts, school buddies, pastor, teachers, mentors, ... EVERYONE!
This choice is a disastrous one for integrity. Every person you are selling into the market is a new victim to the eventual bubble burst. You're choice is dire. Dispose of all analytical skills and simply believe, in which case you'll never spot the top because you cannot believe and not believe at the same time;
OR, know that the top is coming, watch it ferociously, plan its every snap up and your flip out, but have to sell everyone else around you on a lie.
Sounds a bit drastic? Over the top?
Well, yes. It is drastic. But here's the clanger: the history of pyramid schemes, bubbles and ponzis predicts exactly that. We've been here before, hundreds of times. It doesn't matter where bubbles come from, when they get going, the herd phenomena is frightening. Friends trick each other, families consume themselves, businesses get sucked in, investment blows out.
And generally, what we find when we investigate the complaints is that everyone knew it was a bubble. Everyone believed. Everyone knew it was the opportunity of a life time. And everyone turned on their friends and families and pulled them into it.
This might be the sort of risk appetite that you like. If so, holding on to the currency as an investment is for you. If for example, you are a VC and you see 9 other VCs thinking seriously about going in, then there's an easy call for you -- in you go, quicker than them, and out you go if you can spot the top. You might see this as the bread and butter of your work.
And the scare reasons above might actually be just ranting or philosophising and can be ignored. Let's give it one more go.
There is one final reason why investing in the currency might actually be a bad bet. It is this: by investing in the currency, you are actually de-investing in the global Bitcoin community. Unlike buying the stock market index, by taking currency and hoarding it, it is no longer available to circulate and to provide new capital to the new business. As new capital is the only fundamental way, sans bubble, of making future investment returns, such a choice, buying the bubble, is reducing the float in the economy, and therefore reducing the overall growth, and the aggregate returns. Buy holding the currency, you are ensuring the bubble pops earlier rather than later.
Which is to say, your apparent prisoners' dilemma result of cheating not only rides on the backs of others' work, it also makes it harder to develop the market in the long run with /fundamental returns/. Only new value circulating as capital in the market can make it grow. It is a mathematical certainty that if you take money out of the market by hoarding it, you are reducing its ability to grow, and this is repeatedly demonstrated every time the central bank winds the knob to strip the cash out of the currency in order to cool it down.
Indeed, this force is so dramatic that when you as investor announce your intention to hold currency, positive investors should leave the room. They should ostracize you, they should shout at you, they should do all but shoot you! How dare you call yourself an investor when you are de-investing in Bitcoin? While everyone else is working hard to make the market work, you're dragging it down by withdrawing capital?
You are a negative investor.
You're actually doing more damage to the returns of the Bitcoin world than any government can.
I personally think that the investment in the currency is the worst of all options. In short sweet summary, it's lowering overall returns, it's not diversified at all, and it creates incentives to turn off the one thing I thought I valued above all else -- my brain. Indeed it is the sort of approach where you might have to hide your strategy because serious Bitcoiners -- those who've understood the potential of cryptocurrencies without losing sight of the reality of business investment -- are going to blackball you. And if I've learnt one thing in two decades in the financial cryptography game, it is this: In the money game, dirty hidden secrets have a way of biting you, hard.
If this all makes sense, then I'd suggest you look at the opportunity in investing directly in Bitcoin businesses, and not the currency. More on that in another post, labelled B for Business.
podcasts on pre-Bitcoin from Bitcoin UK
Bitcoin UK has done two podcasts on the cryptocurrency history before Bitcoin:
These podcasts were done at the same time as my rant as posted on the blog a little while ago, "A very fast history of cryptocurrencies BBTC -- before Bitcoin." Interesting for those that prefer to listen more than read.
February 03, 2014
FC++ -- Bitcoin Verification Latency -- The Achilles Heel for Time Sensitive Transactions
New paper for circulation by Ken Griffith and myself:
Bitcoin Verification Latency
The Achilles Heel for Time Sensitive TransactionsAbstract.Bitcoin has a high latency for verifying transactions, by design. Averaging around 8 minutes, such high latency does not resonate with the needs of financial traders for speed, and it opens the door for time-based arbitrage weaknesses such as market timing attacks. Although perhaps tractable in some markets such as peer to peer payments, the Achilles heel of latency makes Bitcoin unsuitable for direct trading of financial assets, and ventures seeking to exploit the market for financial assets will need to overcome this burden.
As with the Gresham's paper, developments moved fast on this question, and there are now more ventures looking at the contracts and trading question. For clarification, I am the secondary author, Ken is lead.
September 19, 2013
Research on Trust -- the numbers matter
Many systems are built on existing trust relationships, and understanding these is often key to their long term success or failure. For example, the turmoil between OpenPGP and x509/PKI can often be explained by reference to their trust assumptions, by comparing the web-of-trust model (trust each other) to the hierarchical CA model (trust mozilla/microsoft/google...).
In informal money systems such as LETS, barter circles and community currencies, it has often seemed to me that these things work well, or would work well, if they could leverage local trust relationships. But there is a limit.
To express that limit, I used to say that LETS would work well up to maybe 100 people. Beyond that number, fraud will start to undermine the system. To put a finer point on it, I claimed that beyond 1000 people, any system will require an FC approach of some form or other.
Now comes some research that confirms some sense of this intuition, below. I'm not commenting directly on it as yet, because I haven't the time to do more than post it. And I haven't read the paper...
'Money reduces trust' in small groups, study shows
By Melissa Hogenboom Science reporter, BBC News
People were more generous when there was no economic incentive
A new study sheds light on how money affects human behaviour.
Exchanging goods for currency is an age old trusted system for trade. In large groups it fosters co-operation as each party has a measurable payoff.
But within small groups a team found that introducing an incentive makes people less likely to share than they did before. In essence, even an artificial currency reduced their natural generosity.
The study is published in journal PNAS.
When money becomes involved, group dynamics have been known to change. Scientists have now found that even tokens with no monetary value completely changed the way in which people helped each other.
Gabriele Camera of Chapman University, US, who led the study, said that he wanted to investigate co-operation in large societies of strangers, where it is less likely for individuals to help others than in tight-knit communities.
The team devised an experiment where subjects in small and large groups had the option to give gifts in exchange for tokens.
The study
- Participants of between two to 32 individuals were able to help anonymous counterparts by giving them a gift, based solely on trust that the good deed would be returned by another stranger in the future
- In this setting small groups were more likely to help each other than the larger groups
- In the next setting, a token was added as an incentive to exchange goods. The token had no cash value
- Larger groups were more likely to help each other when tokens had been added, but the previous generosity of smaller groups suffered
Social cost
They found that there was a social cost to introducing this incentive. When all tokens were "spent", a potential gift-giver was less likely to help than they had been in a setting where tokens had not yet been introduced.
The same effect was found in smaller groups, who were less generous when there was the option of receiving a token.
"Subjects basically latched on to monetary exchange, and stopped helping unless they received immediate compensation in a form of an intrinsically worthless object [a token].
"Using money does help large societies to achieve larger levels of co-operation than smaller societies, but it does so at a cost of displacing normal of voluntary help that is the bread and butter of smaller societies, in which everyone knows each other," said Prof Camera.
But he said that this negative result was not found in larger anonymous groups of 32, instead co-operation increased with the use of tokens.
"This is exciting because we introduced something that adds nothing to the economy, but it helped participants converge on a behaviour that is more trustworthy."
He added that the study reflected monetary exchange in daily life: "Global interaction expands the set of trade opportunities, but it dilutes the level of information about others' past behaviour. In this sense, one can view tokens in our experiment as a parable for global monetary exchange."
'Self interest'
Sam Bowles, of the Santa Fe Institute, US, who was not involved with the study, specialises in evolutionary co-operation.
He commented that co-operation among self-interested people will always occur on a vast scale when "helping another" consists of exchanging a commodity that can be bought or sold with tokens, for example a shirt.
"The really interesting finding in the study is that tokens change the behavioural foundations of co-operation, from generosity in the absence of the tokens, to self-interest when tokens are present."
"It's striking that once tokens become available, people generally do not help others except in return for a token."
He told BBC news that it was evidence for an already observed phenomenon called "motivational crowding out, where paying an individual to do a task which they had already planned to do free of charge, could lead people to do this less".
However, Prof Bowles said that "most of the goods and services that we need that make our lives possible and beautiful are not like shirts".
"For these things, exchanging tokens could never work, which is why humans would never have become the co-operative species we are unless we had developed ethical and other regarding preferences."
July 01, 2013
Why I am a fan of Alan Greenspan, still.
In comments to the last post, Glyph poses a hard question:
I'm curious: why, at this point, would you be a fan of Alan Greenspan?He's the epitome of everything that went wrong with our financial system: a demagogue who substituted ideology for critical thought. He spoke as if he were an entrepreneur who understood the creation of real wealth by use of the free market, but whose real power and influence came from being a bureaucrat with the keys to the largest fiat money machine in the history of mankind.
...
A simple answer is found in rephrasing the question -- what is the alternative?
Let me expand on that. I'm not a fan of Central Banking, as many readers will know from my frequent posts. I see Central Banking as inevitably enslaved to the banks, the regulated consumes the regulator (something known in economic literature as the Stigler Conjecture).
But the realpolitik of the 20th century was that Central Banking was the structure of finance. Granted, that we have a central bank, who then is best to lead it?
In the trade, knowledge of monetary policy would probably stand out as the first and highest metric. But, also known as important to Central Banking is the quality of "independence".
Alan Greenspan was a notorious goldbug who became a boutique investment banker. He retained his suspicion of all fiat currencies until the end, and it is this skepticism of Central Banking that established his credentials as an independent thinker. In my book, picking someone who was already suspicious of Central Banking was probably an inspired choice, and this is borne out by his incredibly long career.
If we look for example at Mark Carney, the current most-talked about Central Banker who last month took post at the Bank of England, we see something of the same flavour. He is suspicious of banks by nature, as well as having been a banker with Goldman-Sachs. As I hear it, his time in Canadian public service was marked by keeping the banks on a tight leash, while those south of the border ran roughshod.

To paraphrase the above, Mark Carney thus represents a least bad choice among many worse choices. Need we present examples of the worse choices?
The fundamental problem is still the failure of Central Banking, and its history of protecting the TBTFs and allowing them to bring the system down.
It would be far better if we as a society and economy could ease away from Central Banking, TBTF and all that, but that is likely to take decades. In the meantime, who better to lead Central Banks than people naturally suspicious of banks?
June 27, 2013
Did Alan Greenspan blow the bubble that blew up the world?
If you, like me, are a fan of Alan Greenspan, you'd also be wondering what went wrong in the 2000s. His book is enlightening, but not conclusive. Observations that there were a series of heart-starting adrenalin injections into the economy -- the dotcom crash, 9/11, Fannie Mae, Bear-Stearns and Lehman Brothers, 2007, etc -- are illuminating but again not conclusive.
Even to establish that the train ran off the tracks is hard. Here comes a graph from WorldComplex blog (h/t to Zerohedge) that pretty much nails it:
The train not only ran off the tracks, it left the reservation. The beauty of these graphs is that you don't even have to understand them to realise that something really crazy happened after 2000.
But that said, let's try and interpret them. The graph shows accelerating USA housing prices beyond the norm. The pre-2000 blob(s) on the bottom left corner shows stability over the long run, which is to say that housing prices were stable across the USA, over time. For the norm, housing prices were a direct reflection of the rest of the economy, and in stability.
Then, movement to the right shows rapidly increasing prices, as it measures the index of prices for a given year over 4 years before. Movement to the left shows rapid collapse, the reverse. Movement up&right shows overall (sustained?) increase in prices, movement down& left shows overall (sustained?) lowering.
 I think then, this is compelling evidence. There was a bubble blown from the year 2000 to 2006 of epic proportions. It then collapsed between 2006 and 2013, still on-going (we're still 20 points above long run stability).
I think then, this is compelling evidence. There was a bubble blown from the year 2000 to 2006 of epic proportions. It then collapsed between 2006 and 2013, still on-going (we're still 20 points above long run stability).
Only the Federal Reserve could blow such a bubble. And, it was done on Alan Greenspan's watch.
I'm still a fan of the magician. He did, overall, a far better job than Bernanke is doing right now. But, there is no doubt that the Federal Reserve lost the plot while under Greenspan's watch.
Which, for future economic historians, leaves a compelling research project: what went wrong? And for the rest of us, a mess.
June 25, 2013
2 ways out of crushing debt
 From Chris's FinancialServicesClub,
From Chris's FinancialServicesClub,
(I’m a bank teller at a large national bank. A customer in her mid-twenties comes up to my till.)Me: “Welcome to [bank name]! How can I help you today?”
Customer: “Yeah, can I find the total amount I owe for my student loans?”
Me: “Sure, what is your full name?”
(She gives me her name, and I give her the amount owed. It is a fairly large amount.)
Customer: “Perfect!”
(With a large smile, she hands me a cashier check from another bank, for the exact amount, totally paying off all loans she has with this bank. I enter the info, and print her receipt. I quickly run to the back to see my manager.)
Me: “Can I give this customer a couple of the promotional items that we usually give to people that open checking accounts?”
(My manager see the amount that she is paying, and that this means the customer has totally paid off the loans.)
Manager: “You can give her whatever you want!”
(I grab some items, and bring them back up to the till.)
Me: “Congratulations on paying off all your loans. Here’s your receipt, and a few gifts for paying off such a large loan amount.”
Customer: “Thank you very much! What I’m about to say has nothing to do with you; you are a great person, and thank you very much for the free gift. So, just go with everything I’m about to do.”
Me: “…Okay?”
(She holds up the receipt above her head, and speaks in a loud voice.)
Customer: “Ha! Six years ago I sold my soul to this bank! But after going through the nine circles of hell, I have finally gotten free of it! I now owe you nothing, zip, zero, nada! I am free; no more bills, payments, fees, nothing. I’M FREEEEEEE!”
(Even as she walks out the doors, she’s yelling and dancing. The dozen or so other customers and workers watch her the whole time. Another customer speaks loud enough so just about everyone can hear him.)
Customer #2: “Raise your hand if you wish you could do that.”
(Just about everyone else in the bank raises their hand.)
Strange and contradictory notions, indeed. In contrast, the impatient bears over at ZeroHedge point to Iceland:
Iceland Debt Forgiveness Reaches $2 Billion Since Crisis By Omar R. Valdimarsson - 2013-06-24T15:26:26ZIceland’s lenders have forgiven household debt equal to about 12.4 percent of gross domestic product since the island’s 2008 financial collapse.
Lenders had written off 212.2 billion kronur ($1.7 billion) in household debt through the end of 2012, the Icelandic Financial Services Association said in a letter to parliament. The group estimated a further 35.3 billion kronur will be forgiven this year after they recalculate loan agreements to meet a Supreme Court ruling.
About 141.2 billion kronur of that follows a ruling from the island’s top court stating that mortgage loans indexed to foreign exchange rates were illegal, it said.
The island’s biggest banks failed in October 2008, after defaulting on about $85 billion in debt. The collapse plunged the island’s economy into a crisis that sent unemployment surging nine-fold and triggered a recession.
The association said that of the total, 45.8 billion kronur in private debt was forgiven as part of an agreement that stipulated that debts exceeding 110 percent of a property’s value must be written off.
This is germane because, as ZeroHedge do not hesitate to remind us, "Iceland is so far the only success story in the continent of Europe, which continues sliding into an ever deeper depressionary black hole, as a result of the complete destruction of its financial sector and its subsequent rise from the ashes..."
If you're still interested, here's Chris's generational perspective and his gentle reminders that Britain has a "a £27.1 billion capital shortfall in the UK banking system" and a few random other troubled bank reports. Probably unimportant in the scheme of things.
Wait, one of those is a third way to get out of crushing debt:
Taped telephone recordings (from the bank's own systems) from inside doomed Anglo Irish Bank reveal for the first time how the bank's top executives lied to the Government about the true extent of losses at the institution. ...Anglo itself was within days of complete meltdown – and in the years ahead would eat up €30bn of taxpayer money. Mr Bowe speaks about how the State had been asked for €7bn to bail out Anglo – but Anglo's negotiators knew all along this was not enough to save the bank.
...The plan was that once the State began the flow of money, it would be unable to stop. Mr Bowe is asked by Mr Fitzgerald how they had come up with the figure of €7bn. He laughs as he is taped saying: "Just, as Drummer (then-CEO David Drumm) would say, 'picked it out of my arse'."
And a picture makes 4. I should change the title, but who cares about numerical accuracy these days?

May 05, 2013
Extraordinary revelations of British Banks, Bad Behaviour, Fraud, FSA un-regulation, and more!
A series of posts over on Chris Skinner's Financial Services Club has amounted to a whistleblowing expose par excellence!
 First up, a victims organisation called BullyBanks has collected over a thousand cases of mis-selling of Interest Rate Swap Agreements (IRSAs) to small / medium businesses (SMEs). To dispose of the essentials quickly, these were complex derivatives that were mis-sold to businesses that had no clue what they were about:
First up, a victims organisation called BullyBanks has collected over a thousand cases of mis-selling of Interest Rate Swap Agreements (IRSAs) to small / medium businesses (SMEs). To dispose of the essentials quickly, these were complex derivatives that were mis-sold to businesses that had no clue what they were about:
The FSA accepted that the mis-selling of IRSAs had occurred ...
You can see the details on the posts. Chris estimates the potential damage as such:
Jeremy was a victim of the process and has been championing the cause ever since. He now counts 1,200 companies in his group, Bully Banks, out of the 40,000 cases that have been identified so far.It does not sound like much, but if each case averages £2.5 million compensation, this is a £100 billion exposure and is far bigger than the PPI mis-selling scandal we all know about already.
Did the banks do anything wrong? Chris asks exactly that, rhetorically:
Have banks behaved badly or are customers a little bit stupid?
BullyBanks lays it out:
The substantial majority of the complaints of the business men and business women who are members of Bully-Banks have most of the following elements:
- The complainant is dependent upon finance provided by their Bank. Without that finance they could not continue in business.
- Their Bank sold them the IRSA when loan facilities were being granted or extended.
- Their Relationship Manger advised that the Bank believed interest rates were at an historic low and were going to rise in the medium term.
- Their Relationship Manager warned that the Bank was concerned about the complainant’s ability to finance their loan if interest rates were to rise significantly.
- The Relationship Manager introduced the concept of the IRSA to the complainant – an IRSA is normally outside the knowledge or experience of the complainant.
- The Relationship Manager stated that the IRSA was something that the Bank wanted the complainant to enter into and either made this recommendation as part of the grant of the loan facilities or stipulated it as a requirement as part of the grant of the loan facilities.
- The Relationship Manager then introduced an expert from the appropriate division of the Bank to arrange the IRSA. The expert was introduced as an advisor. No mention was made of the fact that in fact the expert was a salesman earning significant levels of commission on the sale of the IRSA. (No mention was made of the fact that in many cases the Relationship Manager also had annual targets to sell IRSAs.)
- The Bank typically booked a significant profit on the sale of the IRSA even though no mention of this profit to the Bank was made at the time the complainant was advised that the Bank wanted the complainant to enter into an IRSA.
Those are claimed facts from BullyBanks, and the presentation at the Financial Services Club was even harsher.
Rhetorically, we can look at it from a perspective of law. The high-bar charge here would be fraud. In order to show fraud, prosecutors would generally test on three elements: Intent, deception & damages.
In reading all of the information so far published by BullyBanks and FSC, I would say either there is a charge of fraud to be answered, OR, BullyBanks is simply wrong, barking mad and up its tree. Whether their claims were sustainable in court, before a jury, would answer which of the two.
 Which brings us to the following paraphrased comment:
Which brings us to the following paraphrased comment:
“I wonder when the banks will be taken to court for not protecting customers from interest rate rises?”
The question was asked in sarcasm, but it is precisely on point. BullyBanks has made a claim, in effect, that the banks told the customer the IRSA was to protect them from interest rate rises, but their evidence suggests it was a rort to sell the customer an explosive derivative.
In short, a deception, one of the three elements of fraud.
So why didn't the banks get taken to court? Well, it turns out that the above poster is not the only one mystified:
Mainly because of the Parliamentary investigation, the Financial Services Authority was kicked into action and, on June 29 2012, announced that it had found "serious failings in the sale of IRSAs to small and medium sized businesses and that this has resulted in a severe impact on a large number of these businesses.”
So it seems that the FSA initially ignored the complaints. Then because of parliamentary bullying, it investigated, and agreed there was a case to answer for. What did it do next?
However, [the FSA] then left the banks to investigate the cases and work out how to compensate and address them.
Promptly handed the case back to the banks to deal with! Are those words for real? What we have here is ... fraud. Now, either the FSA lied and there wasn't any mis-selling, or there was a bona fide case to be answered.
Worse, the banks agreed:
The banks response was released on January 31 2013, and it was notable that between the June announcement and bank response in January that the number of cases rose from 28,000 to 40,000. It was also noteworthy that of those 40,000 cases investigated, over 90% were found to have been mis-sold. That’s a pretty damning indictment.Even then the real issue, according to Jeremy, is that the banks are in charge of the process
 Even if there is no case found in court, it is still the prosecutor's job to try it. It is not the FSA's job, not the banks' job, and it is certainly not the FSA's role to hand the mess across to the perpetrators.
Even if there is no case found in court, it is still the prosecutor's job to try it. It is not the FSA's job, not the banks' job, and it is certainly not the FSA's role to hand the mess across to the perpetrators.
BullyBanks also smells a rat:
Our lobbying campaign is now focused on addressing this failure by the FSA. ... Bully-Banks has already made a substantial contribution to the raising of this issue in the UK. Bully-Banks is now working hard on the next phase of its campaign in the UK: a submission to the Treasury Select Committee and further lobbying of Members of Parliament. It is also beginning to address a number of legal issues in the UK which have arisen in connection with the mis-selling of IRSAs.
Which reminds me of the mess the Reserve Bank of Australia got into. In short: they were formally advised of a serious suspicion of crime by one of their executives. RBA decided to take legal advice on this claim, and the advice from a notable law practice was that no Australian crime had been committed. So, armed with a legal opinion, the RBA did ... nothing. Fast forward to a media expose, the police investigated, and laid charges against some 8 or 9 people.
It transpires in Australia at least, a federal agency has to by law refer suspicion of crimes to the police. It doesn't have an option of deciding itself.
One wonders then if the FSA knows what it is doing? Open question for British readers: is it a requirement in the UK for Crown Agencies to refer crimes to the prosecutor? Or is the FSA in possession of some magical get-out-of-jail card?
Back to the rhetorical question:
Have banks behaved badly or are customers a little bit stupid?
If, still by way of rhetorical evidence so far presented, fraud were indicated, then the customer doesn't need to be a little bit smart - they are entitled to rely on the banks for banking expertise and fair dealing.
So it seems pretty clear: the banks behaved badly. QED. (If you are still not convinced, check out the bad behavior in the other whistleblowing post ... combine the two!)
But what is more disturbing still is that the FSA behaved even worse. This is a rather damning indictment that British Banks are unregulated. Penultimate word to Chris:
...the industry is known for selling you an umbrella when the sun is shining, only to find the umbrella full of holes when it rains. Is this true? Are we working in an industry purely focused upon ripping off our customers or do we work in a business that is customer focused and honestly trying to help?I believe it is the latter and, for all the shenanigans of LIBOR, swaps, PPI and more, it is purely a few rotten eggs and ill-judged deeds that have resulted in where we are today, and not a systematically focused industry trying to rip off their customers.
Don’t you agree?
For me: No.
May 01, 2013
MayDay! MayDay! British Banking Launches new crisis of titanic proportions...
 Yes, it's the first of May, also known as May Day, and the communist world's celebration of the victory over capitalism. Quite why MayDay became the international distress message over radio is not known to me, but I'd like to know!
Yes, it's the first of May, also known as May Day, and the communist world's celebration of the victory over capitalism. Quite why MayDay became the international distress message over radio is not known to me, but I'd like to know!
Meanwhile, the British Banking sector is celebrating its own version of MayDay:
The bank went through their customer base and identified which businesses were asset rich and cash poor.Typically, the SME (small to medium enterprise) would require funding for expansion or to cover short term exposures, and the bank’s relationship manager would work with the business owner on a loan funding cover.
The loan may be for five or ten years, and the relationship manager would often call the client after a short time and say “congratulations, you’ve got the funding”.
The business owner would be delighted and would start committing the funds.
Only then would the relationship manager call them back and say, “ah, we have a concern here about interest rates”.
This would start the process of the disturbance sale of the IRSA.
The rest you can imagine - the bank sold an inappropriate derivative with false information, and without advising the customer of the true costs. This time however the costs were more severe, as it seems that many such businesses went out of business in whole or in part because of the dodgy sale.
In particular, the core issue is that no-one has defined whether the bank will be responsible for contingent liabilities.The liabilities are for losses made by those businesses that were mis-sold these products and, as a result, have now gone into bankruptcy or been constrained so much that they have been unable to compete or grow their business as they would have if they had not taken these products.
 Ouch! I have to applaud Chris Skinner and the Financial Services Club here for coming forth with this information. It is time for society to break ranks here and start dealing with the banks. If this is not done, the banks will bring us all down, and it is not clear at all that the banks aren't going to do just that.
Ouch! I have to applaud Chris Skinner and the Financial Services Club here for coming forth with this information. It is time for society to break ranks here and start dealing with the banks. If this is not done, the banks will bring us all down, and it is not clear at all that the banks aren't going to do just that.
Meanwhile back to the scandal du jour. We are talking about 40k businesses, with average suggested compensation of 2.5 million quid - so we are already up to a potential exposure of 100 billion pounds. Given this, there is no doubt that even the most thickest of the dumbest can predict what will happen next:
Mainly because of the Parliamentary investigation, the Financial Services Authority was kicked into action and, on June 29 2012, announced that it had found "serious failings in the sale of IRSAs to small and medium sized businesses and that this has resulted in a severe impact on a large number of these businesses.”However, it then left the banks to investigate the cases and work out how to compensate and address them .
The banks response was released on January 31 2013, and it was notable that between the June announcement and bank response in January that the number of cases rose from 28,000 to 40,000. It was also noteworthy that of those 40,000 cases investigated, over 90% were found to have been mis-sold. That’s a pretty damning indictment.
Even then the real issue, according to Jeremy [of Bully Banks], is that the banks are in charge of the process.
Not only is the fox in charge of the chickens, it's also paying off them off for their slaughter. Do we really need to say more? The regulators are in bed with the banks in trying to suppress this scandal.
Obviously, this cunning tactic will save poor banks money and embarrassment. But the emerging problem here is that, as suggested many times in this blog (e.g., 2, 3, 4, ...) and elsewhere, the public is now becoming increasingly convinced that banks are not healthy, honest members of society.
 Which is fine, as long as nothing happens.
Which is fine, as long as nothing happens.
But I see an issue emerging in the next systemic shock to hit the financial world: if the public's patience is exhausted, as it appeared to be over Cyprus, then the next systemic shock is going to cause the collapse of some major banks. For right or wrong, the public is not going to accept any more talk of bailouts, taxpayer subsidies, etc etc.
The chickens are going to turn on the foxes, and they will not be satisfied with anything less than blood.
One hopes that the old Lady's bank tear-down team is boned up and ready to roll, because they'll be working hard soon.
April 22, 2013
On banks dumping ties to dodgy corrupt practices...
The Economist talks about corruption in sport, and how to deal with it:
For sponsors like ING, disassociating the company or a brand from corruption in sport simply makes good business sense, protecting reputation and image from the negative perceptions of consumers. For banks, this matters especially. Domestic banking is built upon customer trust; how then could such an organisation be associated with a team that was demonstrably untrustworthy? It is such incongruence that is at the heart of the newly emerging market-driven morality: sponsors do not want to be associated with corruption and hence recoil from it.
That was easy...
Now, what about those within? Front-running, Libor, PPI over-selling, robo-signing, MBS pushing, bonuses, off-balance sheet liabilities, risk-free sovereign debt, audit failures, secret bailouts, ... plenty of life left in this game!
Amusing addendum on Chris's blog: FLS fattening. And IRSA misselling.

Chris says Image sourced from Catholic in Brooklyn
March 27, 2013
NATO opines on cyber-attacks -- Stuxnet was an act of force
We've all seen the various rumours of digital and electronic attacks carried out over the years by the USA on those countries it targets. Pipelines in Russia, fibre networks in Iraq, etc. And we've all watched the rise of cyber-sabre rattling in Washington DC, for commercial gain.
What is curious is whether there are any limits on this behaviour. Sigint (listening) and espionage are one thing, but outright destruction takes things to a new plane.
Which Stuxnet evidences. Reportedly, it destroyed some 20% or so of the Iranian centrifugal capacity (1, 2). And, the tracks left by Stuxnet were so broad, tantalising and insulting that the anti-virus community felt compelled to investigate and report.
But what do other countries think of this behaviour? Is it isolated? Legal? Does the shoe fit for them as well?
Now comes NATO to opine that the attack was “an act of force”:
The 2009 cyberattack by the U.S. and Israel that crippled Iran’s nuclear program by sabotaging industrial equipment constituted “an act of force” and was likely illegal under international law, according to a manual commissioned by NATO’s cyber defense center in Estonia.“Acts that kill or injure persons or destroy or damage objects are unambiguously uses of force,” according to “The Tallinn Manual on the International Law Applicable to Cyber Warfare.”
Michael N. Schmitt, the manual’s lead author, told The Washington Times that “according to the U.N. charter, the use of force is prohibited, except in self-defense.”
That's fairly unequivocal. What to make of this? Well, the USA will deny all and seek to downgrade the report.
James A. Lewis, a researcher at the Center for Strategic and International Studies, said the researchers were getting ahead of themselves and there had not been enough incidents of cyberconflict yet to develop a sound interpretation of the law in that regard.“A cyberattack is generally not going to be an act of force. That is why Estonia did not trigger Article 5 in 2007,” he said, referring to the coordinated DDoS attacks that took down the computer networks of banks, government agencies and media outlets in Estonia that were blamed on Russia, or hackers sympathetic to the Russian government.
Cue in all the normal political tricks to call white black and black white. But beyond the normal political bluster and management of the media?
Under the U.N. charter, an armed attack by one state against another triggers international hostilities, entitling the attacked state to use force in self-defense, and marks the start of a conflict to which the laws of war, such as the Geneva Conventions, apply.
What NATO might be suggesting is that if the USA and Israel have cast the first stone, then Iran is entitled to respond. Further, although this conclusion might be more tenuous, if Iran does respond, this is less interesting to alliance partners. Iran would be within its rights:
[The NATO Manual] makes some bold statements regarding retaliatory conduct. According to the manual's authors, it's acceptable to retaliate against cyberattacks with traditional weapons when a state can prove the attack lead to death or severe property damage. It also says that hackers who perpetrate attacks are legitimate targets for a counterstrike.
Not only is Iran justified in targetting the hackers in Israel and USA, NATO allies might not ride to the rescue. Tough words!
Now is probably a good time to remind ourselves what the point of all this is. We enter alliances which say:
Article 5 of the NATO treaty requires member states to aid other members if they come under attack.
Which leads to: Peace. The point of NATO was peace in Europe, and the point of most alliances (even the ones that trigger widespread war such as WWI) is indeed peace in our time, in our place.
One of the key claims of alliances of peace is that we the parties shall not initiate. This is another game theory thing: we would not want to ally with some other country only to discover they had started a war, to which we are now dragged in. So we all mutually commit to not start a war.
And therefore, Stuxnet must be troubling to the many alliance partners. They see peace now in the Middle East. And they see that the USA and Israel have initiated first strike in cyber warfare.
This is no Pearl Harbour scenario. It's not even an anticipatory self-defence, as, bluster and goading aside, no nation that has developed nuclear weapons has ever used them because of the mechanics of MAD - mutually assured destruction. Iran is not stupid, it knows that use of the weapons would result in immediate and full retaliation. It would be the regime's last act. And, as the USA objective is regime change, this is a key factor.
So it is entirely welcome and responsible of NATO -- in whatever guise it sees fit -- to stand up and say, NO, this is not what the alliance is about. And it can't really be any other way.
March 25, 2013
After a decade of bad banking, finally some Good News: Cyprus forced to shut down a bad bank!
 From the ghoulish department of "good news unless you're affected" comes the story that the Cyprus government has agreed to the terms of the Troika:
From the ghoulish department of "good news unless you're affected" comes the story that the Cyprus government has agreed to the terms of the Troika:
Cypriot President Nicos Anastasiades agreed to shut the country’s second-largest bank under pressure from a German-led bloc in a night-time negotiating melodrama that threatened to rekindle the debt crisis and rattle markets....
The revised accord spares bank accounts below the insured limit of 100,000 euros. It imposes losses that two EU officials said would be no more than 40 percent on uninsured depositors at Bank of Cyprus Plc, the largest bank, which will take over the viable assets of Cyprus Popular Bank Pcl (CPB), the second biggest.
Cyprus Popular Bank, 84 percent owned by the government, will be wound down. Those who will be largely wiped out include uninsured depositors and bondholders, including senior creditors. Senior bondholders will also contribute to the recapitalization of Bank of Cyprus.
This is how it should be. In order to avoid moral hazard - the laziness from complete insurance - the people responsible must suffer the consequences of their judgement. The bond holders must be left short. The creditors -- uninsured depositors [0] -- must lose. The shareholders must be wiped out. The employees must be sacked, and officers in positions of material decision making must be pursued.
Only when that message gets out across Europe, and the world, will the people who choose to do business with their bank begin to regulate their bank.
Or withdraw their funds; which is the safety mechanism in a sound system against bad banking [1]:
Second, the commitment to the convertibility would provide an effective discipline against goldsmith-bankers who issued an excess of notes. When banks issued convertible notes, their circulation would be limited by the demand to hold them. That demand would depend on such factors as the precise features of the convertibility contract (for example, whether the depositor had to give notice when he wanted to withdraw his deposit), the bank's reputation, the familiarity of its notes, the number of branches it maintained, and so on. Any notes issued beyond the demand to hold them would be returned for redemption.
The law for banks might have changed, but the laws of banking do not.
[0] Should the insured depositors be wiped out? That is a more subtle issue. Maybe another day.
[1] This is not the end to the Cyprus story. Although the remedy is correct there are still questions to ask. Who owns the bonds? It turns out that a large part of the bonds have been put as collateral for emergency lending to the ECB. Which is then guaranteed by the national central bank. Oops. Story yet to unfold.
March 19, 2013
How much for an island in the sun, Mr Putin?
The Cyprus news flows in, thick and fast. There are only a few major points. As expected from any nation made of /ellos con cajones/, the Cypriots slapped down the European offer, 36 to nothing (much). The problem here can be seen as the curse of a small democratic nation -- which is to say, the representatives probably still have to answer to their constituency, unlike their more sophisticated northern counterparts.
Meanwhile, the Europeans are perhaps left bemused at the fail of the bid. They gave it their best shot, non? What now?
There is another offer on the table.
Cypriot Finance Minister Michael Sarris flew to Moscow on Tuesday to seek Russian financial assistance. He denied by text message reports that he had resigned, which rattled nerves as lawmakers were poised to vote.
Let's sum up the friendship. The Russians already loaned in 2.5bn, sans Eursury. They're hopping mad at being excluded from the conference of debtors. They're also a bit red faced -- slap slap -- at repeated allegations of hot money. Further, although the media plays shy on this one, it turns out that Cyprus has become a nice little center for serious, legal, solid Russian business. As well as a destination for that soon to be listed endangered species: English common law.
The din of criticism from Moscow signaled the importance of Cypriot offshore financing for the Russian economy. The island has long served as an escape valve for Russian businessmen. Some are surely dodging local taxes. Others, paradoxically, are seeking better courts in the British law system practiced in Cyprus.Offshore domiciles are so ingrained in the post-Soviet way of doing business in Russia that Cypriot shell companies are linked not only with money launderers and organized crime, but well-established companies like the metals giant Norilsk Nickel.
H/T to naked capitalism and Lynn in comments on that one. Naked capitalism does not go so far on this, but I wonder: This is one hell of a friendship.
For some number around 10bn, plus/minus, perhaps the Russians get to buy into Europe. As long as they (a) respect the english common law tradition, (b) leave the islanders to live out their happy sun-kissed lives, and (c) sort out the banks, what objection could there be, nyet?
Not to mention, Nota bene to students of long Russian strategy & short Middle Eastern futures, pay no attention to the hands,... Cyprus is a warm weather port.
Bank Holiday in Cyprus
 It's official - there is a Bank Holiday in Cyprus:
It's official - there is a Bank Holiday in Cyprus:
Cypriots woke up on March 16 to find bank transfers frozen as the country's authorities prepared to remove the tax from accounts before banks were scheduled to reopen on March 19. The Cypriot central bank has since declared bank holidays until March 21 to avert the prospect of account-holders withdrawing all their savings.
The economics term 'bank holiday' is historically synonymous with the banking system being bankrupt, at least.
Meanwhile, the European Finance Ministers have held strong on the need for Cyprus to raise the cash, but left open flexibility in just who for the Cypriots.
What a dilemma! The obvious answer is "just deposits over 100k" but that will cause massive withdrawals of those same massive deposits from the massive Russian Oligarchs, and put the banking sector into crisis as its revenues and profits are pretty much dependent on those things. (e.g.) The more subtle answer is they have to move broader afield ... and hit the bond holders.
Which will not please the Europeans. Why not? Same reason different channel: the bond holders are the European banks. And the root asset failure of the banking sector is that they are all left holding each others' junk bonds. Wipe out a class of bonds anywhere, and contagion is an issue.
The Europeans have fought to keep the bonds good, but it is an open question how long the game of Russian Roulette goes on. This is exactly how Cyprus got into this mess in the first place: Greek bonds. Which, as all who have studied real banking (a.k.a. free banking) know well, points to the root cause of most banking crises: state intervention in the quality of banking reserves:
One of the US's major criticisms of IFRS (International Financial Reporting Standards) is that it is subject to political intervention.They're right to be concerned, said Mr Andrew. "We had regulators and governments telling us not to write down Greek debt in certain countries. They were refusing to allow accounting firms to adjust, saying they would underwrite a portion of the debt but refusing to put [that commitment] in writing," he said.
In short, banks are required to list state bonds as risk-free. When they are not. Cyprus is one step closer to leaving the euro zone, and declaring default on its bonds. Like Iceland.
March 18, 2013
Cyprus deposit holders to take a 7-10% loss -- perversely this the right Cure, and it may Kill the Patient
 News over the weekend has it that Cyprus has agreed to a bailout, but in exchange for the most terrible of conditions: Cypriot depositors are to be taxed at rates from 6.75% to 9.9% of their deposits.
News over the weekend has it that Cyprus has agreed to a bailout, but in exchange for the most terrible of conditions: Cypriot depositors are to be taxed at rates from 6.75% to 9.9% of their deposits.
This is utter madness, and the reasons are legion. Speaks the Economist:
EVERYONE agrees that taxpayers should be protected from the cost of bailing out failing banks. But imposing blanket losses on creditors is still taboo. Depositors have escaped the financial crisis largely unscathed for fear of sparking panic, which is why the idea of hitting uninsured depositors in Cypriot banks has caused policymakers angst.
You muck around with deposit holders or your own people at your peril. There is now a fair chance of a bank run in Cyprus, and a non-trivial chance of riots.
Further, the bond holders don't get hit. Not even the unprotected ones!
Worse, yet, the status of deposit is enshrined in a century of law, decisions and custom. It is not going to be clear for years whether the law will sustain ahead of legal challenges. Consider the mess about Greek bonds in London, and that allegedly big powerful Russian oligarchs are involved? A legal challenge is a dead certainty.
Finally, and what is the worst reason of all - the signal has been sent. What happened to the Cypriots can and will happen to the Spanish. And the Italians. And if them, the French. And finally, those safe in the north of Europe will now see that they are not safe.
The point is not whether this will happen or not: the point is whether you as an individual saver wish to gamble your money in your bank that it won't happen?
The direction of efforts to improve banks’ liquidity position is to encourage them to hold more deposits; the aim of bail-in legislation planned to come into force by 2018 is to make senior debt absorb losses in the event of a bank failure. The logic behind both of these reform initiatives is that bank deposits have two, contradictory properties. They are both sticky, because they are insured; and they are flighty, because they can be pulled instantly. So deposits are a good source of funding provided they never run. The Cyprus bail-out makes this confidence trick harder to pull off.Other than that, it is a really good deal.
In short words, Cyprus bail out means: start a run on European banks. Only time will tell how this goes on.
What's to take solace? Perversely, there is an element of justice in this decision. Moral hazard is the problem that has pervaded the corpus bankus for a decade now, and has laid low the financial system.
Moral hazard has it that if you fully insure the risk, then nobody cares. And indeed, nobody in the banking world cares, it seems, since they've all acquired TBTF status. None of the people care, either, as they happily deposited at those banks, even knowing that the financial sector of Cyprus was many times larger.
Go figure ... here comes a financial crisis, and our banks are bigger than our country? What did the Cypriot people do? Did they join the dots and wind back their risk?
However the figures are massaged down, the nub of the problem will remain: a country with a broken banking model. Unlike Greece, brought low by its unsustainable public finances, Cyprus has succumbed to losses in its oversize banks. By mid-2011 the Cypriot banking sector was eight times as big as GDP; its three big commercial banks were five times as large.
No. Moral hazard therefore has it the stakeholders must be punished for their errors. And the stake holders of last resort are the Cypriot people, or at least their depositors. And their pensioners, it seems:
In practice the main answer will be to dragoon Cyprus’s pension funds and domestic banks into financing the €4.5 billion of government bonds due to be redeemed over the next three years.
It is highly likely that Cypriot pensioners will lose the lot, as it worked for Spain.
Which does nothing to obviate the other arguments listed above. Regardless of this sudden and surprising display of backbone by the Troika, it is still madness. While we may actually be on the cusp of cure to the disease, the patient might die anyway.
European leaders could at long last bite the bullet and insist on a bail-in of bank creditors to cover expected losses. The snag is that any such action would set alarm-bells ringing for investors with serious money at stake in banks elsewhere in the euro area. Mario Draghi, the ECB’s president, said on March 7th that “Cyprus’s economy is a small economy but the systemic risks may not be small.”
Watch Cyprus with interest, as if your future depends on it. It does.
February 01, 2013
We need banks to fail. What other language speaks?
The obvious problem with TBTF - too big to fail - is that banks that successfully manoeuvre governments into awarding them with the honoured right of printing money for nothing (aka bonuses, and chicks for free) also set the governments up for the eventual fall.
Although bank failure is traumatic, the alternate is far worse, at every possible level. Economic theory has it quite simply: if a bank fails, then all the directors must be punished, all the shareholders be set to zero, and the creditors must lose. No other reminder is sufficient to instill in the public's minds the need to treat their banks with skepticism.
But western, socialist or community minded governments often fall into the Misean trap of thinking they can do better than the market. And at times, they can -- central banks have successfully taken over many banks, fixed them, and returned them to the market. At a profit, even.
But the market always reasserts in time. They only thing that changes is who pays for the folly. And so comes Icesave - against who's creditors a European court has ruled:
The ruling, delivered in Luxembourg by the European Free-Trade Association Court, dealt with the collapse of Icesave, an online subsidiary of Iceland’s Landsbanki. Before the crisis Icesave had used a European “passport” to open branches abroad and collected deposits in Britain and the Netherlands with almost no oversight from regulators in those countries. One condition of its passport was that it promised that its deposits were backed by a national deposit-insurance scheme in Iceland. Yet when the bank collapsed Iceland’s deposit scheme was overwhelmed. Icelandic depositors in the bank ended up getting their money back; the British and Dutch governments both had to step in to compensate depositors in their countries.Many observers had expected the court to rule that Iceland was obliged to stand behind its national deposit-protection plan and not to discriminate against foreign depositors. Instead the court found that Iceland was obliged only to make sure that it had a deposit-insurance scheme. The state was not required to pay out if the scheme had no money because of a banking crisis. Oddly, the court also found that Iceland had not breached an obligation not to discriminate between domestic and foreign depositors, even though it made only the domestic ones whole.
As an individual who had lost money in such a case, I would be yelling for blood. But as an economist, this is the wrong approach -- I the individual should be yelling for blood at the shareholders' meeting while the bank is still solvent, not after it is obviously dead.
The way the Economist writes the above story is common sense, and can get no better. Obviously, a national deposit-insurance only insures the nationals, or more precisely the residents. It's that word - "national" - which was curiously not extended to "community".
Obviously, such a scheme was in place. What is not clear is, in the sad event that it failed, why would one imply that there was another scheme behind it? Or why would one imply that a given "national deposit scheme" was a bottomless pit of value for tapping? A scheme has a value, right?
Only if one can suspend any judgement as to the credibility and creditworthiness of the players, can one assume that a fund would never fail, but this is what people typically do. If Wikipedia knows the number for Germany, why don't the people?
This assumption flies in the face of evidence that is presented daily. Well, yesterday at least: Six of the big Canadian banks are now downgraded:
"Today's downgrade of the Canadian banks reflects our ongoing concerns that Canadian banks' exposure to the increasingly indebted Canadian consumer and elevated housing prices leaves them more vulnerable to unpredictable downside risks facing the Canadian economy than in the past," said Moody's vice president David Beattie.
We need more of it. Meanwhile, in not so sensible news, the Greeks have gone precisely backwards and declared war on themselves:
Any transaction in excess of 500 euros will soon only be allowed via credit or debit card or by check, according to a plan by the Finance Ministry aimed at combating tax evasion.The ceiling for cash transactions is to be lowered from 1,500 euros today to 500 euros and could be reduced further over in the course of 2013. Ministry sources say that in the first quarter of the new year all companies and certain self-employed individuals will have to obtain the POS (point-of-sale) terminals that provide for card transactions.
The problem with this is that, although the Greek problem of taxation failure is well known, there is another larger problem: the Greek economy is dying. And this is a problem for the whole population, not just the sub-sector know as "the government".
People need to eat. If the economy is failing, they need to resort to themselves, their local communities, their families and their long standing local trade relationships. They need small trades, efficient trades, hand to hand and barter.
Trust at a local level, because there is nothing else. It is no longer a question of savings, or deposit schemes, or even taxation - it's about survival. People need the cash.
Instead of assisting this process, and serving the very survival of their People, the government of Greece is assisting the banks which everyone knows to be bankrupt. Which then is a shot across the bows of the Greek People.
So one has to ask a question - are the People of Greece irretrievably stupid? Will they rush in droves to place their cash in banks, and trust in the Greek Government to make them whole if there are any failures? Is their national deposit scheme a bottomless pit of value?
Or, are they possibly like the now chastened British and Dutch - a little more skeptical of offers endorsed by a regulator who's best idea for repairing an economy is to strip raw circulating cash out of the economy. Or, the Spanish, who are moving (their cash and sometimes themselves).
Coincidentally, stripping the cash out of the economy is an idea championed to great effect in the 1930s by none other than the USA Federal Reserve.
When banks are bankrupt, we need them to fail. What other language will get the message through?
January 11, 2013
Women make us smarter?
In yet another "that's a bad gender term" debate somewhere, this article popped up: "Evidence for a Collective Intelligence Factor in the Performance of Human Groups," Woolley et al, Science 2010. Massacring it to extract its core message:
"However, three factors were significantly correlated with c [Group Intelligence]. First, there was a significant correlation between c and the average social sensitivity of group members.... Second, c was negatively correlated with the variance in the number of speaking turns by group members.... In other words, groups where a few people dominated the conversation were less collectively intelligent than those with a more equal distribution of conversational turn-taking.Finally, c was positively and significantly correlated with the proportion of females in the group (r = 0.23, P = 0.007). However, this result appears to be largely mediated by social sensitivity (Sobel z = 1.93, P = 0.03), because (consistent with previous research) women in our sample scored better on the social sensitivity measure than men [t(441) = 3.42, P = 0.001]. In a regression analysis with the groups for which all three variables (social sensitivity, speaking turn vari- ance, and percent female) were available, all had similar predictive power for c, although only social sensitivity reached statistical significance (b = 0.33, P = 0.05) (12)."
The lobby for women may simply be missing a few marketing tricks. Instead of detecting "differences" and assuming them to be discrimination, there are positive things that can be highlighted.
Maybe it is as simple as coming up with a slogan or aphorism that captures the positive? That article suggests in a very solid and cohesive way that women make groups more intelligent. This is a message that could make even the most hardened geeks and misogynists take pause.
December 23, 2012
Why Central Banking will fail in the next N years -- and how Central Bankers might prepare us for it.
I think I have already predicted the apogee of Central Banking in claiming that the 20th century was theirs. It is not entirely clear what happens next; we won't know that until we (or they) build that future, and CBs themselves lose all their power such that they step aside and allow banks to fail.
That said, it is a rather dramatic prediction. So it behoves to review it from time to time. And to seek other opinion! With that in mind, I present a long essay from BullionVault's Paul Tustain, who starts out by saying:
I'VE ALWAYS been fairly sure you can't print money and get away with it indefinitely. But I couldn't well answer the question "Why not?"
It turns out the recent head of the British financial services regulator is similarly uncertain. He recently suggested the Bank of England write off half of the government's debt, which comes to exactly the same thing as printing money. How wonderfully simple. Of course it must be wrong, but why?
You can read the whole thing for the fuller answer. I'm just going to cherry pick. Firstly, show that a reminder that we need money:
CHIMPANZEES don't barter, but they trade a variety of delayed favours we won't go into here. South American vampire bats are more sophisticated, and run a small credit economy. The little darlings have such a need for blood that they lend, borrow and pay back amongst themselves rather than let a relative go bloodless for a whole night. They somehow manage to do the whole thing without plastic cards. A credit card – of course – is a device which creates both credit and debt, and you can spend the credit bit, which unfortunately leaves the debt bit overhanging, though oddly absent from the device's name.Pure, distilled credit usually arises from us doing some work (labour), or transferring our property to someone else (selling goods). Either way, we generate an unreturned favour. So I'm going to call a unit of credit an 'Uf', and wherever possible I'll use the word 'Uf' instead of credit. Somehow it makes it much easier to understand what the hell is going on.
Chimps and vampires show that credit occurs naturally, just as it would have for the earliest humans. Beyond the smallest number of transactions it would have quickly become hard to agree who owed unreturned favours (Ufs) and to whom. Then somebody had the smart idea of using tokens to represent Ufs.
It is quite an important observation that money is simply an accounting system for favour returns. If we were to formalise this notion, money would be an accounting system that works in a world of many parties, where each are individual actors. (Some would say byzantine actors, others would say crooks.) In contrast, the accounting systems we actually call accounting systems, the ones we normally have occasion to use, are more simply which work well with only one party, self or or our employer, and there is a reasonable expectation that self does not steal from self.
The point here is that when we create money we are building an accounting system. And we might have different ways of doing that... Indeed we might set up an accounting system where someone stands in the center and lets users pay each other:
Vampires bats can't do what we can which is to formalise our simple transaction onto an account by booking two payments through the bank. If your friend were to pay you through the bank for the original favour you did then you could spend your Uf anywhere. Banking is useful, like Uf tokens are, because an Uf you earn from your friend, then record at your bank, becomes available for you to pay anyone who's got a bank account.
And now I'd like to step in and reveal a crucial distinction. Where Paul has started talking about banks, he has now drifted to payment systems. Pin this point on your wall above your monitor or laptop - there are banks and there are payment systems.
Banks happen to have payment systems, but banks also have credit. Why and how does credit exist? He explains it in some detail, but here's a succinct para:
It is pure nonsense to say that a gold standard means all money should be backed by vaulted gold. Suppose it was. It would prevent a man with a paid up £100 million property portfolio from borrowing £10,000 from his bank to pay someone £10,000 to build a garden shed. A monetary obstruction to this deal just isn't going to be tolerated, and it's a stupid idea to suggest the deal should be blocked simply because the consumer (rich property owner) or his bank currently has no gold at hand. It was precisely this sort of economic blockage that caused people to create money in the first place, and if you try to stop willing and credible exchangers from using one type of money they'll simply abandon your money, and either use someone else's or create their own.
Which is to say - people with wealth will work with credit, and credit will arise naturally to assist those people, in exactly the same way that money itself arose (which is nothing more than a credit system for favours done in the past).
Credit is natural. Now the question turns to how we deal with the industrialisation of credit in a banking system, and the more particular point of what happens when a bank over-extends. In a stable banking system, other banks knock on the door and get their agreed collateral back. In a Central Banking system, the banks pass their combined position to the CB who nets it. Paul introduces Brad's bank, one that acts badly, and is enouraged to act more badly:
....When his bank deposits its balance at Brad's bank to Central, then it clears away its risk of Brad's bank's failure. It is Central which will now be exposed to the failure of Brad's bank.
The role of Central Banking is (or has become) to take on the risk of any bank failng.
....It also explains that the last bank in the chain is accepting the risk that Brad's bank can't return the Ufs, and because banks can get off that risk by drawing a cheque on Brad's bank and depositing it into Central, the Ufs created by Brad's bank usually end up owed by Brad's bank directly to the Central Bank.
And banks take on that role with relish.
These days Central is feeble, and frightened of the political consequences of any bank failure, so it lets Brad's bank run up an ever growing balance on ever weaker collateral. Other banks can deposit any of Brad's bank's junk at Central. Central's bluff (that it might close down a dodgy bank like Brad's) has been well and truly called. If you are a sound bank you can now do stupid business with a bad bank which you know can never pay you properly, and it won't hurt you.Because Central's Governor has made it known he won't let banks fail, he has set himself up as the patsy.
To ground this story, Paul puts it in today's financial speak:
The resulting huge Uf balances at Central can be made grand and confusing by saying "The Bank of England's Balance Sheet is expanding" which I'm sure makes everyone think it's doing a remarkably important job. What it really means is that the Governor won't demand that a busted bank pays up or shuts down, so Central just runs up an ever bigger deposit balance at an ever weaker bank. While Central permits this Brad's bank really is being allowed to 'create money out of thin air'.
In short: Banks ran ever bigger loan exposures, because they had to compete on dividends. They cleared them through the Central Banks, which declined to shut any down. Therefore the Central Banks expanded their balance sheets to hold the risk, thus further encouraging the banks to do more and more.
Indeed the current set up – where banks are not allowed to fail – turns out to be even worse than I previously thought. It does much more than offer succour to the odd unfortunate bank which steps over the limit of safety. It actually forces banks to be dumb. They have no choice but to approach the safety limit until they are bound to step over it. Any bank which does not step up to the plate will underperform all the others, and be subsumed by a more aggressive competitor. It's how evolution works; the survival of the fittest, where fitness means adapted to the prevailing environment. If you do not compete in the skewed environment where the Central Bank is a wimp you will expire because of it.That's why banks are forced to make rosy judgments on the value of collateral.
Precisely. The regulatory environment *requires* banks to compete in badness. They cannot innovate (take on risk not understood by the CB), and they cannot seek to avoid being commoditised. Thus the only thing they can do is compete on dividends to their shareholders, who are guaranteed by the CB patsy.
If all of them act like this, they must all overstep the bounds, and the system must fail.
Central Banking is thus the problem NOT the solution. And therefore has grave difficulty in being any part of the solution, even if all the actors in the Central Banking world are honest, hard-working and try their darndest to avoid the inevitable.
Once we understand the theory of why Central Banking must fail, in the end, we all naturally reach for predictions and solutions. That's tough. Nobody who is in control has an interest in stopping the rot, all of us outside have no power. So the result will be unpredictable.
But maybe some good things can be snuck through to prepare for the inevitable.
Let's now return to the events of 2007-2008 because it brings forth a singular lesson. When the crisis of Lehman Brothers hit Britain, panic spread through the banks, and in a knee-jerk reaction to protect themselves, they refused to deal with each other.
Bad idea. In an effort to keep the banks working, some banks turned to new teams. E.g., sack the executives. But, as the story is widely told in private banking circles, one man held a gun to the banks' collective head and refused to go.
So long did he hold that gun that it was estimated that his bank was 2 hours from shutting down their ATM network. And if that bank's ATM network was shut down, all the others follow suit.
The entire British payments systems were 2 hours from freezing solid.
People in power in London well know what the people outside London, outside of power, are capable of doing - recall the Poll Tax riots? Or more recently?
So we now see the real fear behind the deadly embrace that Paul outlined: Central Banking will fail and take the banks with them, the banks operate the payment systems and the failure of them will cause society to screech to a halt.
The silver lining that can be brought out of this is that payment systems, and indeed other innovations, can be allowed to emerge out of society. Payment systems can be divorced from banks, and to a large extent this direction can be see in the European monetary regulations of the last decade (PSD and eMoney directive).
Central Banks cannot get off their rollercoaster ride to credit-fueled doom, but they can ensure that newer innovations are not coupled to their journey to destruction.
Consider Kenya and Tanzania, countries that now have THREE mostly independent payment systems: cash, banks and mPesa. If all banks were to fail, shut the doors and the ATMs were to go broke, then the people can turn to the other two. Cash transactions will suddenly be king. And as long as the mPesa system is able to operate divorced from the banks, it will become queen.
mPesa already handles something like 20-30% of the GDP of Kenya, and something similar in Tanzania; if it can pick up more load, then this society might survive. As long as cash and electronic can still circulate, people can eat. Credit will be frozen, the middle classes will be screwed, but as long as people can eat, the bloodshed will be less pronounced.
A country like Britain which has long handed the monopoly of payments to the banks will not have this option, and remains in its deadly banking embrace. Hence, their better bet would be nurture and encourage the innovations: BullionVault and their close cousin GoldMoney. Zopa. Alternative payments systems under the eMoney directive, and independent systems under PSD. They should pray for an mPesa.
The question then to the Bank of England is not how much governance they wish to load onto these innovations, but rather do you dare run the risk without them?
November 13, 2012
More STOP PRESS: A Ratings Agency has been brought to task!
In another outstanding development in the new normal of the post-GFC world, a bad actor has been brought to task:
The ruling in the Federal Court of Australia on November 5th held Standard & Poor’s (S&P) jointly liable with ABN AMRO, a bank, for the losses suffered by local councils that had invested in credit derivatives that were designed to pay a high rate of interest yet were also meant to be very safe.
What in effect does this mean? If you put your name on something as good, then you have to carry the consequences of it being bad. And the courts will hold you to it, or, they did in this case. As shareholders held Deloitte accountable in at least one Auditor case recently.
This is one of the essential, unavoidable causes of the GFC (marks I and II) -- that powerful players may take the upside of profitable participation in risky trades, but declare themselves non-liable for the downsides.
Was, in this case, S&P just caught out by a statistical bad apple, or was it raking it in? The Economist goes on to report:
The derivatives in question were “constant proportion debt obligations” (CPDOs). These instruments make even the most ardent fans of complex financial engineering blush: they are designed to add leverage when they take losses in order to make up the shortfall. S&P’s models, which the court said blindly adopted inputs provided by ABN AMRO, gave the notes a AAA rating, judging they had about as much chance of going bust as the American government.
That's a slam dunk. Adding that local councils are unsophisticated investors (and generally can't tell their elbow from their posterior) it is no surprise that they routinely invest in AAA ratings, and only AAA ratings. Hence, they rely on AAA.
Hence, S&P must be held liable for their good word on the meaning of AAA, assuming of course that the Economists' reporting is fair representation of the evidence presented.
Further, as S&P clearly did not do the diligence due to a statement with the gravitas of "as safe as the American government," the question of gross or criminal negligence looms large.
November 01, 2012
Price Discovery is Hard.
Seen on the net, copied as is, from James A. Donald:
On 2012-11-01 7:18 PM, CodesInChaos wrote:
> 3) You need to figure out an appropriate price. In the simplest case
> the uploaders simply send to the offer with the highest payment
> attached.
That just offloads the problem of price discovery somewhere else in the system.
Price discovery is hard.
Price discovery in micro transactions needs to be substantially automated - at both ends. People will not invest the effort needed for manual price discovery.
Bad, incompetent, or buggy price discovery has killed every previous effort to solve this group of problems.
Price information is probabilistic, thus a price discovery mechanism has to support a full Bayesian model, recursive probabilities estimating the probability that the true probability is p, performing maximum entropy modeling. This is the sort of work that gets very smart engineers hired at astronomical salaries by wall street.
[James A. Donald]
October 23, 2012
Finally, the media gets it: The cyber-jihad that the NSA bought to hometown America
I have struggled to write this story for a long time, and now Business Insider has written it for us:
In a world where you can watch cyberattacks happen in real-time, it's no wonder that nation-states are doing little to hide the cyber arms race and low-grade cyberwar that's taking place. However, what's surprising is that the country leading the charge — the U.S. — may also be the one with the most to lose."There is a world of bytes and a world of atoms, and increasingly the world of bytes is driving the world of atoms," Dr. Jarno Limnell, director of cyber security at Stonesoft, told us. "This is a whole new capability for these state-actors — previously there was no way to touch the U.S."
(fast forward to the crux of the issue)
Capabilities vary. China, which began its Information Warfare (IW) plan in 1995, has been stealing America's business secrets for more than a decade. Russia recently stated that it's "not making a secret of their plans to gain offensive [cyber] technologies."The U.S. isn't in the best position to invite cyberwar. As RedSeal Chief Technology Officer Dr. Mike Lloyd told us when he described how easy it would be to attack the physical U.S. infrastructure: "People in glass houses shouldn't throw stones. [And] unfortunately, it's not just that—very simple stones can break our glass windows. We have very thin defenses."
OK, I'll spell it out - the USA has the most developed computer base of all countries, and is also the most attractive target. It is also as badly defended as anyone else, and may be the worst. E.g., it is the home of phishing, DDOS, breaching, and BotNet nodes. In particular, the record of breaches and phishing suggest that the USA is the country that was most at risk and had most losses from these attacks. (Question for all - Europe missed out on phishing, Russia got Kaspersky - why did USA get the worst of it?)
So in this environment, what is the Pentagon thinking? Good question. Here's an example of what the Pentagon is thinking:
The big question is whether a cyberattack can trigger a "real world" attack. Last year the Pentagon concluded that cyberattacks would justify a traditional military response. And in August BBC reported on a leaked Israeli memo that spelled out the hybrid use of cyber and military warfare in a proposed assault on Iran."This is the most troubling aspect of developing these weapons," said Limnell. "What is the action of the president if an attack happens, does it immediately become kinetic?"
Limnell said the difference between traditional warfare and cyberwarfare is that often cyberwarfare includes, indeed even prioritizes, civilian targets. And like the situation with the nuclear weapons in the 50s and 60s, there are no international rules for how we can use these weapons.
"Cyberwarfare is like Wild West right now, there’s a huge lack of norms and rules," Limnell said. "We will experience some type of major problem before we learn how to use weapons in the cyber domain."
Dumb. We already know that cyber attacks are mostly unattributable - the Chinese have been spying using these techniques for decades and China has not been caught. We now know the Pentagon generals are justifying their position by saying "it's cool, we'll just go kinetic if they dare throw a packet our way."
Dumber. So who do they throw their bombs at? Other than a country, their stuck - they have to go to the world and say "bad Iranians hurt us with packets, now we want to bomb them back into the stone age." That doesn't work, because the world saw the Iraqi debacle and won't play stupid again, but it seems that the Pentagon didn't get the memo. Worse - their casus belli is already known to be outright fraud because the USA has admitted launching StuxNet against the Iranians.
Can it possibly get any dumber?
The U.S. isn't in the best position to invite cyberwar. As RedSeal Chief Technology Officer Dr. Mike Lloyd told us when he described how easy it would be to attack the physical U.S. infrastructure: "People in glass houses shouldn't throw stones. [And] unfortunately, it's not just that—very simple stones can break our glass windows. We have very thin defenses."
Oh yeah -- it gets leveraged dumb. It's because the equation is stacked against the USA. The Pentagon have launched what is probably the dumbest attack of all time. The Stuxnet attack that they might see as an exchange of a pawn, letting their kinetic queen rove free, is actually exposing their entire board. Dumbest of all.
The reason for this is politely called the equity question in NSA circles. When it came to cyber defence, the NSA decided in the early 1990s that it was more important to make the Internet weak and vulnerable to spying, than to let the Internet be able to defend itself. This decision was prosecuted publically through crypto export regulations -- remember the crypto wars -- but also through a host of other interventions into the IETF, corporates, critical infrastructure (to them) and other places. When thinking about why USA banking suffered the brunt of phishing and breach losses, a large part of the big picture goes back to the NSA.
So the biggest dumb mistake of them all is that the Pentagon wants any excuse to go kinetic against the Iranians, but they've not defended their home ground over the last 20 years. The gates to the cyber-kingdom are not only wide open, they're 6 inches high and guarding a line of warning signs.
October 14, 2012
It's now official - Central Banks are not working to save the economy
Long time readers of this blog will recall that I predict that the era of Central Banking is now over. We are now in the process of watching the Central Banks destroy their legacy from within. Here is more evidence:
A review of evidence into Quantitative Easing (QE) has shown that the Government's hope that it will pull the UK out of recession may be unfounded.Professor Chris Martin, from the University of Bath's Department of Economics, has looked at the impact of QE not just on financial markets but also the 'real' economy of jobs, inflation and output and concluded that there is no lasting benefit in continuing to pursue the policy.
He concludes that QE has produced a limited but temporary gain for the financial sector, but it has been of no help to the wider business community or individuals and families struggling against inflation and unemployment.
His review has looked at studies of the performance of QE by central banks, including numerous historical studies of small scale QE purchases and studies of the large contemporary QE programmes.
Now, it may be that the Central Banks find themselves convinced of having to prop up the financial sector, in order to save the rest of industry. But this logic doesn't impress for very long because (a) they are only succeeding in undermining the financial sector, rather than making banks more robust for the future, and (b) the populace isn't comfortable with paying the price of this worsening.
Realpolitik will reassert itself. As more time goes on, and more trouble is stored for the future, the potential for massive systemic failure increases. And it is the Central Banks themselves that are driving that systemic risk higher and higher, so they necessarily have to pay the cost when it comes around.
Still, the problem with predicting that the Central Banks are diligently removing themselves from the game is that we do not know what happens next. The end of the century of Central Banking is then a prediction of only small value. The far better question is what arises to re-structure finance in the future?
August 30, 2012
Four Planks to support the next evolution in secure browsing
There are now all the preliminary planks in place for the next step in evolution in the business of browser security.
A federal judge has rejected BancorpSouth's plan to use contractual agreements with customers as a shield against liability claims stemming from an online heist of some $440,000 that was illegally wire-transferred from the account of one of the bank's commercial customers in March 2010.
The first plank was an aggressive environment, this turned up in 2011 (by my reckoning).
The second plank was the decision by participants to avoid liability issues and to document that they had avoided liability issues.
The third plank was recognition by experts (as determined by courts) that online banking was insecure. Although I've pointed at this advice for years ("use another browser") courts don't recognise bloggists as experts. However, e.g., Lynn points in comments to USA federal regulatory advice that a single-purpose dedicated PC be used. That's recognised!
The fourth plank was sufficient clarity on how the courts would deal with the question, by means of actual rulings. This was never in doubt, because the courts always go that way in the long run, but while there were no rulings, people could "reasonably" argue that it was cool.
In his four-page ruling, Magistrate Judge John Maughmer says he based his decision about contractual obligations between banks and commercial customers on his interpretation of the UCC. And he acknowledges the waters are murky. "The court, having read the briefing of the parties, finds this to be a very close call," he says.Nevertheless, Maughmer finds that the UCC does not provide blanket protections for banking institutions, in spite of indemnity noted in the contract.
"As enacted in Missouri and other jurisdictions, the Funds Transfers Act (UCC 4A) was not intended to preempt or displace all causes of action between a bank and its customers engaging in money transfers," Maughmer writes. "The uniformity and certainty sought by the statute for these transactions could not possibly exist if parties could opt to sue by way of pre-Code remedies where the statute has specifically defined the duties, rights and liabilities of the parties."
Other Cases. Inherent in the magistrate judge's findings is the question "What is reasonable?" regardless of whether that reasonableness comes from the bank or the commercial customer. What's contained within the contract and what is deemed "commercially reasonable" often are at odds, Navetta says.
The point being that the courts will find fault with an unreasonable contract. Those rulings we are now seeing, as quoted. As somewhat less than coincidentally, close analogues will inform the courts as to how to deal with liability in other browsing security issues. E.g., PKI certificates.
Smarter participants have seen the writing on the wall. VeriSign sold their CA to Symantec, correctly IMHO judging that the business was going to face increasing risks, while not generating the synergies across to other areas of its business to take on those risks. This confirms the truism of the industry - Others acquired market share, VeriSign understood the market.
All that remains is a headline high-value target to serve as the channel of forces. All of the trouble in the marketplace for certificates - a.k.a. secure browsing - has so far been against non-monetary uses of certificates. Paradoxically, the saving grace for the business may be that it never really got used for such high commercial value things as to be relied upon.
July 23, 2012
¡Olé! Privacy Between a pair of star-crossed lovers
Stories about new ideas in social networking are like snails after rain. Here's "Between," a smartphone app that works for couples only:
"So we turned our eyes to unmarried couples who need such a private relationship platform more than any other groups."Between lets them share photo timelines, send messages and mark anniversaries, birthdays and other dates on each other's calendars.
Connection to the service is completed when both parties enter each other's phone numbers after registering.
However what gets interesting is when the sparks of anger not romance fly:
If a couple breaks up, one of them may disconnect the service and all the data will be deleted.
¡Olé! Stories about the hard problems in privacy are as rare as bullfighting at the RSPCA's annual garden party.
If there is a privacy and security problem that has so bedevilled the worlds thinkers -- even to the extent of most of them not recognising the problem -- it's this: if a couple shares stuff in the purest essence of romantic privacy, what happens when the alliance flips and the lovers-until-death become plaintiffs-to-the-death?
"Between in a way represents a commitment made by couples, so we rarely see teenagers using the service...their relationship usually doesn't last long enough to take full advantage of it," said Park.That is why VCNC's engineers plan to develop a system which backs up data for up to one month after a breakup, just in case lovers decide to reunite and reopen their accounts.
"Think of it as an adjustment period for couples," said Park, adding users quite often complain when data is wiped under the current system.
"users quite often complain" must be evidence of Korean shyness -- if launched in America, the complaints would take hard filed copy form, at STBX's local court.
Still, notwithstanding that date with reality, my hat's off to this brave effort to deal with the *hard problems* of privacy - ¡Olé!
June 20, 2012
Banks will take responsibility for online fraud
Several cases in USA are resolving in online theft via bank account hackery. Here's one:
Village View Escrow Inc., which in March 2010 lost nearly $400,000 after its online bank account with Professional Business Bank was taken over by hackers, has reached a settlement with the bank for an undisclosed amount, says Michelle Marsico, Village View's owner and president.As a result of the settlement, Village View recovered more than the full amount of the funds that had been fraudulently taken from the account, plus interest, the company says in a statement.
And two more:
Two similar cases, PATCO Construction Inc. vs. Ocean Bank and Experi-Metal Inc. vs. Comerica Bank, raised questions about liability and reasonable security, yet each resulted in a different verdict.In 2010, PATCO sued Ocean Bank for the more than $500,000 it lost in May 2009, after its commercial bank account with Ocean Bank was taken over. PATCO argued that Ocean Bank was not complying with existing FFIEC requirements for multifactor authentication when it relied solely on log-in and password credentials to verify transactions.
Last year, a District Court magistrate found the bank met legal requirements for multifactor authentication and dismissed the suit.
In December 2009, EMI sued Comerica after more than $550,000 in fraudulent wire transfers left EMI's account.
In the EMI ruling, the court found that Comerica should have identified and disallowed the fraudulent transactions, based on EMI's history, which had been limited to transactions with a select group of domestic entities. The court also noted that Comerica's knowledge of phishing attempts aimed at its clients should have caused the bank to be more cautious.
In the ruling, the court required Comerica to reimburse EMI for the more than $560,000 it lost after the bank approved the fraudulent wire transfers.
Here's how it happens. There will be many of these. Many of the victims will sue. Many if the cases will lose.
Those that lose are irrelevant. Those that win will set the scene. Eventually some precedent will be found, either at law or at reputation, that will allow people to trust banks again. Some more commentary.
The reason for the inevitability of this result is simple: society and banks both agree that we don't need banks unless the money is safe.
Online banking isn't safe. It behoves to the banks to make it safe. We're in the phase where the court of law and public opinion are working to get that result.
March 04, 2012
Trust me, I'm a banker - how do Alice and Bob trade in a trust-failed world?
A friend proposed a problem with international trust - how do Alice and Bob swap currencies where trust in trade has broken down. Both parties want to complete the transaction, but have no support from 'the system'.
Ordinarily the parties could go to their banks and ask for e.g., letters-of-credit, but in this particular case banking services are frozen or drying up or unreliable. How then to do a swap of value when the only thing left is the basic payments system (one assumes that the banks have managed to keep that running...).
Imagine Alice has 1m of A$ to swap with Bob's 1m of B$. The quantities and currencies are uninteresting. What is interesting is that both parties have committed, but one will lose their head if the other does not follow through.
To borrow an idea from cryptographic bit-commit protocols, they could do it in tranches, which is what financial people call bits. It would go like this: Alice sends 10k to Bob. Bob returns with his 10k. And so on, until it is all done, 200 transactions in all.
This would work, but it might be possible to do better. Notice above that Alice is always neutral or at risk, while Bob is always neutral or positive. Also, Bob is learning to trust Alice, but Alice has no such reward.
Overall, we are talking about both risk & trust. On taking a risk, successfully, trust is built. With equal tranches, we have reduced the total risk overall, and increased trust, but we've done it in an asymmetric fashion. We could talk about balancing and benefiting from this.
How about this: Alice goes first, and this puts Bob in the driver's seat, so right now he is taking no risk! So Bob could return the favour. To do that, he could return with 20k. Bob now has matched Alice's contribution, and has now taken on the same risk as Alice had in her first round.
What does Alice return? She is now ahead by 10k. But she has received 20k, so her risk is actually not so bad. If she were to likewise double up, she could send 20k. Alice and Bob have now entered tit-for-tat, each taking on a risk of half their tranche.
Perhaps we could ramp it up more? Consider taking each risk position and rewarding it by ramping it up by a positive multiplier:
- Alice sends 10k. Bob sends 30k - his risk is now at 20k, greater than Alice's original risk, so she is rewarded for her initial play.
- Alice now holds 30k for only 10k exposure. So she should send 20k to catch up to Bob, 20k to meet his risk, and another 20k to double the risk, being 60k in total.
- Bob now holds 70k received and has sent 30k. He should send 40k + 40k +40k = 120k.
- Alice holds 150k and has sent 70k. She should send 80k * 3 = 240k.
- Bob holds 310k, has sent 180k. He sends (H - S) * 3 = 390k.
- Alice now holds H = 540, and has sent S = 310. She sends 690.
- Bob now holds 1m. He should send 460, which is the lesser of outstanding balance and her straight formula.
From the above, a formula emerges. Each round (except first and last) should transmit (H - S) * R where H is the sender's holdings, S is the receiver's holdings, and R is the risk multiplier.
Risk multipliers are interesting. With R of 1, the initiator is always at risk, the follower is always with zero risk, catching up. But with R of 2, the follower matches her risk, not however extending it, so it quickly moves to balanced, symmetric exposure - tit-for-tat in a positive way. This is perhaps the comfortable compromise.
With R of 3, Bob extends and rewards Alice's initial risk, by taking on new risk that goes well beyond what he need do. This has the advantage of reducing the transactions from o(100) to o(10), and giving the economists an enjoyable chance to show the precise logarithmic reduction that applies.
Some comments on wider issues.
Each exchange could agree on what R or risk parameter they desire. And here we reach some interesting questions in negotiation -- who goes first? Who selects R? Also who selects the initial amount I? Mechanism design might suggest that out of such a negotiation, a fair split in parameters might emerge. E.g., like cut & choose. Or maybe it is a matter for parties to choose.
Also, there is a last round issue. The person who sends the last payment has an incentive to hold. Therefore the formula above might be modified to take account of the ceiling in payments, perhaps reducing the penultimate payments so as to require more trust as it gets closer. Especially for R = 3. It could also be balanced such that Alice as initiator is also the last to send.
This would be the game theory way of looking at it. It is important to recognise that contractual aspects would bring in protection as well. For example, I would be looking to publish any parties who do not complete, perhaps making this compulsory with a 3rd party agency. Also one might refer the thing to binding Arbitration, with rights to full publication and fines, including liens on any future transaction on any other member.... Finally, there should be clauses to include the players and their executioners - names and all - so as to limit the cuts in case the other party begs off.
Of course, the game theory aspects should be as strong as we can make them ... leaving the final exceptions to a short sharp dispute resolution process.
February 18, 2012
The Convergence of PKI
Last week's post on the jaws of Trust sparked a bit of interest, and Chris asks what I think about Convergence in comments. I listened to this talk by Moxie Marlinspike, and it is entertaining.
The 'new idea' is not difficult. The idea of Convergence is for independent operators (like CAcert or FSFE or FSF) to run servers that cache certificates from sites. Then, when a user browser comes across a new certificate, instead of accepting the fiat declaration from the CA, it gets a "second opinion" from one of these caching sites.
Convergence is best seen as conceptually extending or varying the SSH or TOFU model that has already been tried in browsers through CertPatrol, Trustbar, Petnames and the like.
In the Trust-on-first-use model, we can make a pretty good judgement call that the first time a user comes to a site, she is at low risk. It is only later on when her relationship establishes (think online banking) that her risk rises.
This risk works because likelihood of an event is inversely aligned with the cost of doing that attack. One single MITM might be cost X, two might be X+delta, so as it goes on it gets more costly. In two ways: firstly, in maintaining the MITM over time against Alice costs go up more dramatically than linear additions of a small delta. In this sense, MITMs are like DOSs, they are easier to mount for brief periods. Secondly, because we don't know of Alice's relationship before hand, we have to cast a very broad net, so a lot of MITMs are needed to find the minnow that becomes the whale.
First-use-caching or TOFU works then because it forces the attacker into an uneconomic position - the easy attacks are worthless.
Convergence then extends that model by using someone else's cache, thus further boxing the attacker in. With a fully developed Convergence network in place, we can see that the attacker has to conduct what amounts to being a perfect MITM closer to the site than any caching server (at least at the threat modelling level).
Which in effect means he owns the site at least at the router level, and if that is true, then he's probably already inside and prefers more sophisticated breaches than mucking around with MITMs.
Thus, the very model of a successful mitigation -- this is a great risk for users to accept if only they were given the chance! It's pretty much ideal on paper.
Now move from paper threat modelling to *the business*. We can ask several questions. Is this better than the fiat or authority model of CAs which is in place now? Well, maybe. Assuming a fully developed network, Convergance is probably in the ballpark. A serious attacker can mount several false nodes, something that was seen in peer2peer networks. But a serious attacker can take over a CA, something we saw in 2011.
Another question is, is it cheaper? Yes, definately. It means that the entire middle ground of "white label" HTTPS certs as Mozilla now shows them can use Convergence and get approximately the same protection. No need to muck around with CAs. High end merchants will still go for EV because of the branding effect sold to them by vendors.
A final question is whether it will work in the economics sense - is this going to take off? Well, I wish Moxie luck, and I wish it work, but I have my reservations.
Like so many other developments - and I wish I could take the time to lay out all the tall pioneers who provided the high view for each succeeding innovation - where they fall short is they do not mesh well with the current economic structure of the market.
In particular, one facet of the new market strikes me as overtaking events: the über-CA. In this concept, we re-model the world such that the vendors are the CAs, and the current crop are pushed down (or up) to become sub-CAs. E.g., imagine that Mozilla now creates a root cert and signs individually each root in their root list, and thus turns it into a sub-root list. That's easy enough, although highly offensive to some.
Without thinking of the other ramifications too much, now add Convergance to the über-CA model. If the über-CA has taken on the responsibility, and manages the process end to end, it can also do the Convergence thing in-house. That is, it can maintain its set of servers, do the crawling, do the responding. Indeed, we already know how to do the crawling part, most vendors have had a go at it, just for in-house research.
Why do I think this is relevant? One word - google. If the Convergence idea is good (and I do think it is) then google will have already looked at it, and will have already decided how to do it more efficiently. Google have already taken more steps towards ueber-CA with their decision to rewire the certificate flow. Time for a bad haiku.
Google sites are pinned now / All your 'vokes are b'long to us / Cache your certs too, soon.
And who is the world's expert at rhyming data?
Which all goes to say that Convergence may be a good idea, a great one even, but it is being overtaken by other developments. To put it pithily the market is converging on another direction. 1-2 years ago maybe, yes, as google was still working on the browser at the standards level. Now google are changing the way things are done, and this idea will fall out easily in their development.
(For what it is worth, google are just as likely to make their servers available for other browsers to use anyway, so they could just "run" the Convergance network. Who knows. The google talks to no-one, until it is done, and often not even then.)
February 09, 2012
PKI and SSL - the jaws of trust snap shut
As we all know, it's a right of passage in the security industry to study the SSL business of certificates, and discover that all's not well in the state of Denmark. But the business of CAs and PKI rolled on regardless, seemingly because no threat ever challenged it. Because there was no risk, the system successfully dealt with the threats it had set itself. Which is itself elegant proof that academic critiques and demonstrations and phishing and so forth are not real attacks and can be ignored entirely...
Until 2011.
Last year, we crossed the Rubicon for the SSL business -- and by extension certificates, secure browsing, CAs and the like -- with a series of real attacks against CAs. Examples include the DigiNotar affair, the Iranian affair (attacks on around 5 CAs), and also the lesser known attack a few months back where certificates may have been forged and may have been used in an APT and may have... a lot of things. Nobody's saying.
Either way, the scene is set. The pattern has emerged, the Rubicon is crossed, it gets worse from here on in. A clear and present danger, perhaps? In California, they'd be singing "let's partly like it's 2003," the year that SB1386 slid past our resistance and set the scene for an industry an industry debacle in 2005.
But for us long term observers, no party. There will now be a steady series of these shocks, and journalists will write of our brave new world - security but no security.
With one big difference. Unlike the SB1386 breach party, where we can rely on companies not going away (even as our data does), the security system of SSL and certificates is somewhat optional. Companies can and do expose their data in different ways. We can and do invent new systems to secure or mitigate the damage. So while SB1386 didn't threaten the industry so much as briskly kicked it around, this is different.
At an attacks level, we've crossed a line, but at a wider systems level, we stand on the line.
Which brings us to this week's news. A CA called Trustwave has just admitted to selling a sub-root for the explicit purpose of MITM'ing. Read about that elsewhere.
Now, we've known that MITMing for fun and profit was going on for a long time. Mozilla's community first learnt of it in the mid 2000s as it was finalising its policy on CAs (a ground-breaking work that I was happy to be involved with). At that time, accusations were circulating against unknown companies listing their roots for the explicit purpose of doing MITMs on unwitting victims. Which raised the hairs, eyebrows and heckles on not a few of us. These accusations have been repeated from time to time, but in each case the "insiders" begged off on the excuse: we cannot break NDA or reputation.
Each time then the industry players were likewise able to fob it off. Hard Evidence? none. Therefore, it doesn't exist, was they industry's response. We knew as individuals, yet as an industry we knew not.
We are all agreed it does exist and it doesn't. We all have jobs to preserve, and will practice cognitive dissonance to the very end.
Of course this situation couldn't last, because a secret of this magnitude never survives. In this case, the company that sold the MITM sub-root, Trustwave, has looked at 2011, and realised the profit from that one CA isn't worth the risk of the DigiNotar experience (bankruptcy). Their decision is to 'fess up now, take it on the chin, because later may be too late.
Which leads to a dilemma, and we the players have divided on each side, one after the other, of that dilemma:
 To drop the Trustwave root, or not?
To drop the Trustwave root, or not?
That is the question. First the case for the defence: On the one hand, we applaud the honesty of a CA coming forward and cleaning up house. It's pretty clear that we need our CAs to do this. Otherwise we're not going to get anywhere with this Trust thing. We need to encourage the CAs to work within the system.
Further, if we damage a CA, we damage customers. The cost to lost business is traumatic, and the list of US government agencies that depend on this CA has suddenly become impressive. Just like DigiNotar, it seems, which spread like a wave of mistrust through the government IT departments of the Netherlands. Also, we have to keep an eye on (say) a bigger more public facing CA going down in the aftermath - and the damage to all its customers. And the next, etc.
Is lost business more important than simple faith in those silly certificates? I think lost business is much more important - revenue, jobs, money flowing keeping all of the different parts of the economy going are our most important asset. Ask any politician in USA or Europe or China; this is their number one problem!
Finally, it is pretty clear and accepted that the business purpose to which the sub-Root was put was known and tolerated. Although it is uncomfortable to spy on ones employees, it is just business. Organisations own their data systems, have the responsibility to police them, and have advised their people that this is what they are going to do. SSL included, if necessary.
This view has it that Trustwave has done the right thing. Therefore, pass. And, the more positive proponents suggest an amnesty, after which period there is summary execution for the sins - root removal from the list distributed by the browsers. It's important to not cause disruption.
Now the case for the Prosecution! On the other hand, damn spot: the CA clearly broke their promise. Out!
Three ways, did they breach the trust: It is expressed in the Mozilla policy and presumably of others that certificates are only issued to people who own/control their domains. This is no light or optional thing -- we rely on the policy because CAs and Mozilla and other vendors and auditors and all routinely practice secrecy in this business.
We *must rely on the policy* because they deny us the right to rely on anything else!
Secondly, it is what the public believe in, it is the expectations of any purchaser or user of the product, written or not. It is a simple message, and brooks no complicated exceptions. Either your connection is secure to your online bank, and nobody else can see it *including your employer or IT department*. Or not.
Try explaining this exception to your grandmother, if the words do not work for you.
Finally, the raison d'être: it is the purpose and even the entire goal of the certificate design to do exactly the opposite. The reason we have CAs like TrustWave is to stop the MITM. If they don't stop the MITM, then *we don't need the heavyweight certificate system*, we don't need CAs, and we don't need Mozilla's root list or that of any other vendor.
We can do security much more cost-effectively if we drop the 100% always-on absolutist MITM protection.
Given this breach of trust, what else can we trust in? Can we trust their promises that the purpose was maintained? That the cert never left the building? That secret traffic wasn't vectored in? That HSMs are worth something and audits ensure all is well in Denmark?
This rather being a problem with trust. Lie once, lose it.
There being two views presented, it has to be said that both views are valid. The players are lining up on either side of the line, but they probably aren't so well aware of where this is going.
Only one view is going to win out. Only one side wins this fight.
And in so-doing, in winning, the winner sews the seeds for own destruction.
Because if you religiously take your worldview, and look at the counter-argument to your preferred position, your thesis crumbles for the fallacies.
The jaws of trust just snapped shut on the players who played too long, too hard, too profitably.
Like the financial system. We are no longer worried about the bankruptcy of one or two banks or a few defaults by some fly specks on the map of European. We are now looking at a change that will ripple out and remove what vestiges of purpose and faith were left in PKI. We are now looking at all the other areas of the business that will be effected; ones that brought into the promise even though they knew they shouldn't have.
Like the financial system, a place of uncanny similarity, each new shock makes us wonder and question. Wasn't all this supposed to be solved? Where are the experts? Where is the trust?
We're about to find out the timeless meaning of Caveat Emptor.
January 21, 2012
the emerging market for corporate issuance of money
As an aside to the old currency market currently collapsing, in the now universally known movie GFC-2 rolling on your screens right now, some people have commented that perhaps online currencies and LETS and so forth will fill the gap. Unlikely, they won't fill the gap, but they will surge in popularity. From a business perspective, it is then some fun to keep an eye on them. An article on Facebook credits by George Anders, which is probably the one to watch:
Facebook’s 27-year-old founder, Mark Zuckerberg, isn’t usually mentioned in the same breath as Ben Bernanke, the 58-year-old head of the Federal Reserve. But Facebook’s early adventures in the money-creating business are going well enough that the central-bank comparison gets tempting.
Let's be very clear here: the mainstream media and most commentators will have very little clue what this is about. So they will search for easy analogues such as a comparison with national units, leading to specious comparisons of Zuckerberg to Bernanke. Hopeless and complete utter nonsense, but it makes for easy copy and nobody will call them on it.
Edward Castronova, a telecommunications professor at Indiana University, is fascinated by the rise of what he calls “wildcat currencies,” such as Facebook Credits. He has been studying the economics of online games and virtual worlds for the better part of a decade. Right now, he calculates, the Facebook Credits ecosystem can’t be any bigger than Barbados’s economy and might be significantly smaller. If the definition of digital goods keeps widening, though, he says, “this could be the start of something big.”
This is a little less naive and also slightly subtle. Let me re-write it:
If you believe that Facebook will continue to dominate and hold its market size, and if you believe that they will be able to successfully walk the minefield of self-issued currencies, then the result will be important. In approximate terms, think about PayPal-scaled importance, order of magnitude.
Note the assumptions there. Facebook have a shot at the title, because they have massive size and uncontested control of their userbase. (Google, Apple, Microsoft could all do the same thing, and in a sense, they already are...)
The more important assumption is how well they avoid the minefield of self-issued currencies. The problem here is that there are no books on it, no written lore, no academic seat of learning, nothing but the school of hard-knocks. To their credit, Facebook have already learnt quite a bit from the errors of their immediate predecessors. Which is no mean feat, as historically, self-issuers learn very little from their forebears, which is a good predictor of things to come.
Of the currency issuers that spring up, 99% are destined to walk on a mine. Worse, they can see the mine in front of them, they successfully aim for it, and walk right onto it with aplomb. No help needed at all. And, with 15 years of observation, I can say that this is quite consistent.
Why? I think it is because there is a core dichotomy at work here. In order to be a self-issuer you have to be independent enough to not need advice from anyone, which will be familiar to business observers as the entrepreneur-type. Others will call it arrogant, pig-headed, too darned confident for his own good... but I prefer to call it entrepreneurial spirit.
*But* the issuance of money is something that is typically beyond most people's ken at an academic or knowledge level. Usage of money is something that we all know, and all learnt at age 5 or so. We can all put a predictions in at this level, and some players can make good judgements (such as Peter Vodel's Predictions for Facebook Credits in 2012).
Issuance of money however is a completely different thing to usage. It is seriously difficult to research and learn; by way of benchmark, I wrote in 2000 you need to be quite adept at 7 different disciplines to do online money (what we then called Financial Cryptography). That number was reached after as many years of research on issuance, and nearly that number working in the field full time.
And, I still got criticised by disciplines that I didn't include.
Perhaps fairly...
You can see where I'm heading. The central dichotomy of money issuance then is that the self-issuer must be both capable of ignoring advice, and putting together an overwhelming body of knowledge at the same time; which is a disastrous clash as entrepreneurs are hopeless at blindspots, unknowns, and prior art.
There is no easy answer to this clash of intellectual challenges. Most people will for example assume that institutions are the way to handle any problem, but that answer is just another minefield:
If Facebook at some point is willing to reduce its cut of each Credits transaction, this new form of online liquidity may catch the eye of many more merchants and customers. As Castronova observes: “there’s a dynamic here that the Federal Reserve ought to look at.”
Now, we know that Castronovo said that for media interest only, but it is important to understand what really happens with the Central Banks. Part of the answer here is that they already do observe the emerging money market :) They just won't talk to the media or anyone else about it.
Another part of the answer is that CBs do not know how to issue money either; another dichotomy easily explained by the fact that most CBs manage a money that was created a long time ago, and the story has changed in the telling.
So, we come to the the really difficult question: what to do about it? CBs don't know, so they will definately keep the stony face up because their natural reaction to any question is silence.
But wait! you should be saying. What about the Euro?
Well, it is true that the Europeans did indeed successfully manage to re-invent the art and issue a new currency. But, did they really know what they were doing? I would put it to you that the Euro is the exception that proves the rule. They may have issued a currency very well, but they failed spectacularly in integrating that currency into the economy.
Which brings us full circle back to the movie now showing on media tonight and every night: GFC-2.
January 08, 2012
Why we got GFC-2
And so it came to pass that, after my aggressive little note on GFC-1's causes found in securitization (I, II, III, IV), I am asked to describe the current, all new with extra whitening Global Financial Crisis - the Remix, or GFC-2 to those who love acronyms and the pleasing rhyme of sequels.
Or, the 2nd Great Depression, depending on how it pans out. Others have done it better than I, but here is my summary.
Part 1. In 2000, European countries joined together in the EMU or European Monetary Union. A side-benefit of this was the Bundesbank's legendary and robust control of inflation and stiff conservative attitude to matters monetary. Which meant other countries more or less got to borrow at Bundesbank's rates, plus a few BPs (that's basis points, or hundredths of percentage points for you and I).
Imagine that?! Italy, who had been perpetually broke under the old Lira, could now borrow at not 6 or 7% but something like 3%. Of course, she packed her credit card and went to town, as 3% on the CC meant she could buy twice as much stuff, for the same regular monthly payments. So did Ireland, Portugal, Greece and Spain. Everyone in the EMU, really.
The problem was, they still had to pay it back. Half the interest with the same serviceable monthly credit card bill means you can borrow twice as much. Leverage! It also means that if the rates move against you, you're in it twice as deep.
And the rates, they did surely move. For this we can blame GFC-1 which put the heebie-jeebies into the market and caused them to re-evaluate the situation. And, lo and behold, the European Monetary Union was revealed as no more than a party trick because Greece was still Greece, banks were still banks, debt was still debt, and the implicit backing from the Bundesbank was ... not actually there! Or the ECB, which by charter isn't allowed to lend to governments nor back up their foolish use of the credit card.
Bang! Rates moves up to the old 6 or 7%, and Greece was bankrupt.
Now we get to Part 2. It would have been fine if it had stopped there, because Greece could just default. But the debt was held by (owed to) ... the banks. Greece bankrupt ==> banks bankrupt. Not just or not even the Greek ones but all of them: as financing governments is world-wide business, and the balance sheets of the banks post-GFC-1 and in a non-rising market are anything but 'balanced.' Consider this as Part 0.
Now stir in a few more languages, a little contagion, and we're talking *everyone*. To a good degree of approximation, if Greece defaults, USA's banking system goes nose deep in it too.
So we move from the countries, now the least of our problems because they can simply default ... to the banks. Or, more holistically, the entire banking system. Is bankrupt.
In its current today form, there is the knowledge that the banks cannot deal with the least hiccup. Every bank knows this, knows that if another bank defaults on a big loan, they're in trouble. So every bank pulls its punches, liquidity dries up, and credit stops flowing ... to businesses, and the economy hits a brick wall. Internationally.
In other words, the problem isn't that countries are bankrupt, it is that they are not allowed to go bankrupt (clues 1, 2).
We saw something similar in the Asian Financial Crisis, where countries were forced to accept IMF loans ... which paid out the banks. Once the banks had got their loans paid off, they walked, and the countries failed (because of course they couldn't pay back the loans). Problem solved.
This time however there is no IMF, no external saviour for the banking system, because we are it, and we are already bankrupt.
Well, there. This is as short as I can get the essentials. We need scholars like Kevin Dowd or John Maynard Keynes, those whos writing is so clear and precise as to be intellectual wonders in their own lifetimes. And, they will emerge in time to better lay down the story - the next 20 years are going to be a new halcyon age of economics. So much to study, so much new raw data. Pity they'll all be starving.
December 31, 2011
Causes of GFC-1 - the death of the partner
In a short cycle on banking(I, II, III, IV), I point the crooked finger of blame for the first great financial crisis at securitization, as the contractual and markets innovation that gave the USA property bubble the legs to consume society. Now, it seems that I'm just one guy, and everyone has their favourite theory, leading to a fairly long list of hopeful causes. By way of example, Roger Garrison crooks the Austrian finger unwaveringly at central banking:
As my colleague Leland Yeager puts it, "Each cyclical episode is a unique historical event." True enough, but my attention to the central bank as turbocharger helps to keep separate the particulars and the commonalities of the different cyclical episodes.
 True enough, although I think it will take a decade or two before the economists sort through the contenders and come to consensus. Garrison wrote the above in a review of a new book from Kevin Dowd and Martin Hutchinson, Alchemists of Loss: How Modern Finance and Government Regulation Crashed the Financial System, which claims to be a comprehensive treatment of the many causes. Here's one that was new to me:
True enough, although I think it will take a decade or two before the economists sort through the contenders and come to consensus. Garrison wrote the above in a review of a new book from Kevin Dowd and Martin Hutchinson, Alchemists of Loss: How Modern Finance and Government Regulation Crashed the Financial System, which claims to be a comprehensive treatment of the many causes. Here's one that was new to me:
As Dowd and Hutchinson make clear, the redistribution of wealth and income away from business and industrial families meant the demise of the "old partnerships" and the rise of "managerial capitalism." It meant the separation of ownership and control. In an earlier time and without the limited liability that virtually defines the modern corporation, the owners of large-scale industrial and business concerns had plenty of "skin in the game." They had a strong incentive to watch the bottom line, all things considered, and they were in it for the long run. Individual businesses, both large and small, could rise and fall with changing circumstances, but for the economy as a whole the underlying concern for preserving capital value over the long run translated into a degree of macroeconomic stability. Precisely this critical source of stability has been continuously eroded over the years by the federal tax code and regulatory schemes.So with the atrophy of the partnership form of business enterprises, the incentives to maintain long-run profitability have been continuously weakened. It follows, almost as a corollary, that the window for exploiting short-run profit opportunities at the expense of long-run viability has been continuously widened. Managerial capitalism has given rise to a whole class of traders in securities markets and especially in derivatives markets who get in and out of markets in pursuit of short-run gains. The opportunity for these cumulative short-run gains would not have been available (or would have been available on a much smaller scale) had it not been for the absence of "old partnerships" whose vigilance and long-run perspective would have provided an effective counterbalance.
This aspect of Dowd and Hutchinson's storyline rings true. ...
My Audit cycle (I, II, III, IV, V, VI, VII) hints at the very same effect, as the entire Audit industry moved from meticulous to loss-leader in the same 2 decades that mirrored the death of the partnership model. Further, as Professor Dowd's long and prolific career in Free Banking will testify, the disappearance of robust long-term retail banking and the rise of central banking is inherently tied up with the end of partnership banking (c.f., White's Free Banking in Britain).
Why did we as society replace the owner-manager with the salaried managerial trader?
Dowd and Hutchinson date the origins of modern finance to a theorem that Franco Modigliani and Merton Miller introduced in 1958, demonstrating the underlying equivalence of debt financing and equity financing, and to Harry Markowitz's ground-breaking work (a 1952 University of Chicago Ph.D. dissertation) that formalized the relationship between risk and rate of return. Modern financial theory became operational during the 1960s in the form of the Capital Asset Pricing Model (CAPM) and allowed for significant leveraging in the 1970s after Fischer Black and Myron Scholes extended the approach to the pricing of options. Still later developments in information technology and the strategic placement of computer hardware gave rise to flash trading, putting CAPM-based trading strategies on steroids.Outside the context of booms and busts, modern financial theory can be the basis for an overall gain to society. Apart from flash trading, which appears to have no socially redeeming features, trading on the basis of a comprehensive assessment of alternative investment portfolios allows the risks that are inherent in a market economy to be borne by those who are most willing to bear them. A risk/rate-of-return assessment more generally can help tailor an investment portfolio to an individual's risk preferences. The problem, as Dowd and Hutchinson point out, is that the risks that the CAPM takes into account do not include systemic risks. The risk metric that was widely adopted in the 1990s, called "Value-at-Risk" (VaR), quantifies the riskiness of a particular portfolio - on the assumption that the market as a whole is stable. With this metric, you may assure yourself, for example, that you have a 95 percent chance that this portfolio will suffer no greater one-day loss than the calculated VaR (Dowd and Hutchinson 2010, 113). But what if the market as a whole is not stable? And what if the use of the CAPM, the reliance on the VaR, and the proliferation of derivatives serve to leverage both short-run profits and the market's instability?
Boom! Cycle back into the volatility & ignorance theory of financial markets, and we seem to be taking our first steps towards understanding where we are today. To summarise, the elimination of the partnership allowed short-termism to dominate in the modern bonus-fuelled trading enterprises, and it was precisely this worldview that supported the rise of VaRism. Or, systemic risk ain't my problem, boss, now about that bonus...
That's a hell of a contribution. Still, it's early days yet, and to be fair, reviewer Garrison reminds us:
The dot-com crisis of the 1990s occurred because a credit expansion took place during a time when technological innovations associated with the digital revolutions created a strong demand for investment funds in that sector. The housing crisis in 2008 occurred because a credit expansion took place during a time when the federal government was pushing hard for increased home ownership for low-income families. We understandably identify these different cyclical episodes (the dot-com crisis, the housing crisis) with "what was going on at the time." The common denominator, however, is the Fed's propensity to expand credit.At this point, we might ask, "Will the real Alchemist please stand up?"
Which brings us full circle: Systemic Risk is the central bank's problem! So where were the central banks when the partners were selling out of the investment banks and the VaRists were running rampant on bonus steroids? They were pumping up the machine in mini-crisis after mini-crisis, so setting the stage for the mother of all systemic collapses.
From an academic point of view, this is a lot of fun! Aside from the fact that we're so deep in it we can only poke our nose above the smelly brown stuff, I would suggest the next 20 years will be a grand time to be an economist.
December 11, 2011
Why (my, all) financial systems fail -- information complexity
I spent over a decade building the snappiest financial system around. In that time I pursued one goal of efficiency: reduction of complexity. This wasn't only goodness in an angelic sense, it was a pragmatic goal to reduce my own costs in building systems.
The result was pretty spectacular: we were settling trades in seconds and doing so with every leg firmly fastened to the ground. That is, the whole thing was running with direct concrete ties to assets.
But, the big players weren't interested. Indeed they were more than uninterested, they were highly interested in making sure this would never ever happen. Time after time, the message was delivered: Never. Other companies received the same message, so after a few years, I started to take it seriously.
At the time I hypothesised that the reason for this was insider fraud, or at least profits capture. The complexities were endemic and there were very few people who could see the whole picture. So, I theorised that those who could understand the complexities were cashing in on their advantage; from the inside. And some very few who cashed in were also driving the information agenda, as their success made them both wealthy and influential:
more complexity!
Of course such a hypothesis is unlikely to find proof. By its very nature, how do you prove such a tendency towards chaos? Here comes an alternate perspective from ZeroHedge, citing two papers (1, 2):
And the punchline: "Liquidity requires symmetric information, which is easiest to achieve when everyone is ignorant. This determines the design of many securities, including the design of debt and securitization." Reread the last statement as it explains perhaps better than anything, the true functioning of modern capital markets and why they are terminally broken: in order to preserve the system, the banking cartel need to make everything of virtually infinite complexity so that no one has a clear understanding of what is going on!
Consider the perfect market hypothesis: the market already has all the information priced in, so you yourself cannot beat the market. Or, more politely, you get to earn the market rate of return, so you may as well invest in a unit fund that covers the entire market.
Although this hypothesis is proven, and proved time and time again (look at the averaged hedge fund returns against stock market returns over time), it is also clear that, at the limit, the hypothesis is impossible: if the market already knows, no new information will come to the market. In which case it gums up. (Leaving aside temporal arguments for now.)
So, the market also defends itself by creating reasons to bring in new information. ZeroHedge highlights Gorton & Metrick's punchline:
"Liquidity requires symmetric information, which is easiest to achieve when everyone is ignorant. This determines the design of many securities, including the design of debt and securitization."
The market promotes impenetrable securities, which promotes Ignorance, which generates symmetric information, and hence liquidity. QED.
Well, we're all on the same page. Banks support e.g., OTC or over-the-counter market, and will kill to preserve it, because it creates symmetric information. a.k.a ignorance, leading to profits. Meanwhile, I invented the Ricardian Contract which created an excessively visible and tangible chain of contract. These two concepts are at war, opposite poles of complexity versus transparency.
Which is where sites like Zero Hedge step in - to expose "shadowy" places where things are best left unseen.
Yeah. That's what I thought, too. As we watch the complexity-driven system implode it would be easy to assume that now is the time for transparency to rise from the ashes of Europe, thus to be renamed Phoenix.
But, such a thought would be facile and naive in the extreme. A forlorn hope. The implosion of the world financial system doesn't make people any wiser, just poorer. Since when has the world responded to a crisis by getting smart?
What Zero Hedge is really discovering is that rewards are there if you participate in being aware of the complexity. It is a proof of the hypothesis: wisdom emerges in understanding where the masses, the herd, have it wrong. It is not in itself an absolute, nor a way to save them. For anything good to arise, something else is needed.
November 15, 2011
Mexico sends the war into Texas, but it's too late to call out the National Guard
Over the Atlantic, where the Americans struggle with their own financial crisis, we have a real case of money laundering:
LAREDO — The high walls of Alexander Estates, an affluent development nestled near this border city’s country club and golf course, were supposed to keep the narcotics world at bay. But when federal agents raided the stately home of a downtown perfume salesman in January, it reinforced a notion that is feared by Texas leaders: the drug war spillover from Mexico is much broader than shootouts and kidnappings — it is cloaked in the seemingly routine business transactions of the border economy.
In this case, the alleged crime was the back-wash of dollars from drugs sales, laundered through a perfume dealer.
The Black Market Peso Exchange has been on the federal government’s radar for years. The system was perfected by Colombian drug lords and later adopted by Mexican drug cartels: When drugs are sold in the United States, the proceeds, in American dollars, are smuggled back into Mexico or Colombia, where they are exchanged for pesos at a discounted rate.The peso-exchange businesses then use the dollars to buy products in the United States — in Mr. Datta’s case, millions of dollars worth of perfume — and have them shipped to purchasers in Mexico or Colombia.
Yeah. Of course, they have the money to corrupt any business (see Lynn's comments about drugs money and CDOs) and now that times are tight, they can find plenty of incentive.
I've previously written of the process of mexicanization. It begins with an aggressive prosecution by police of drug business; then the value of the illicit business rises, creating profits for the "businessmen" which leads them to fight the authorities. Pretty soon they realise the best way is to corrupt them.
This starts with the police. But pretty quickly spreads. In Mexico, bringing in the soldiers to police the police was a monumental step, and a mistake. Now the Mexican Army is criminalised. With the loss of the judiciary, civil society moves to collapse.
Think it can't happen here? Think again:
The FBI has released a new gang assessment announcing that there are 1.4 million gang members in the US, a 40 percent increase since 2009, and that many of these members are getting inside the military (via Stars and Stripes).The report says the military has seen members from 53 gangs and 100 regions in the U.S. enlist in every branch of the armed forces. Members of every major street gang, some prison gangs, and outlaw motorcycle gangs (OMGs) have been reported on both U.S. and international military installations. ...
The report notes that while gang members have been reported in every branch of service, they are concentrated in the U.S. Army, Army Reserves, and the Army National Guard.
Many street gang members join the military to escape the gang lifestyle or as an alternative to incarceration, but often revert back to their gang associations once they encounter other gang members in the military. Other gangs target the U.S. military and defense systems to expand their territory, facilitate criminal activity such as weapons and drug trafficking, or to receive weapons and combat training that they may transfer back to their gang. Incidents of weapons theft and trafficking may have a negative impact on public safety or pose a threat to law enforcement officials.
Make no mistake: the mexicanization of the USA is happening, and will keep happening. What's it about?
US-based gangs have established strong working relationships with Central American and MDTOs to perpetrate illicit cross-border activity, as well as with some organized crime groups in some regions of the United States. US-based gangs and MDTOs are establishing wide-reaching drug networks; assisting in the smuggling of drugs, weapons, and illegal immigrants along the Southwest Border; and serving as enforcers for MDTO interests on the US side of the border.
One word: Drugs. One acronym: MDTO stands for Mexican Drugs Trafficking Organization.
Violence in Mexico—particularly in its northern border states—has escalated with over 34,000 murders committed in Mexico over the past four years.
One policy: the war on drugs. For brutal comparison with real wars, USA lost 53,402 combat deaths in WWI and 47,424 in Vietnam.
The USA no longer has an option of exporting its miserable war on people south of the border. They're sending it back.
November 13, 2011
Confidence in banking: the €500 supernote, or, we're all money launderers now
Chart of the day comes from the Economist:
Another sign of strain may be found in demand for €500 bills. These are too large for everyday transactions and are mainly used for mattress-stuffing or money laundering, say bankers. Demand for them surged after the collapse of Lehman Brothers in 2008, and it has ticked up again in recent months (see chart 2).
I don't know about you, but use of these unfortunate and economically nonsensical terms by bankers against their customers has always troubled me. Now however, I sense more than a slight cognitive dissonance with the suggestion that money launderers or mattress stuffers are surging.
During the Lehman Brothers Affair, the people lost a huge amount, possibly $150 billion.
The shockwave triggered all sorts of issues; one observer put it that, due to the response of banks like RBS to the crisis, the British ATM network was only hours from being shut down. And, that could have led within a day or to an outbreak of 'shopping with violence'.
In this sense, the people are not so much stuffing mattresses or money laundering, as unstuffing the bank's mattress or getting the money out before the financial system launders it down the tubes. The Lehmans uptick looks to be about 15bn, which looks pretty tame compared to the losses. Or if you take the financial community in Europe who potentially knew 1st hand about the meltdown, and divide by the size of the Lehman Brothers uptick, it's only a handful of supernotes for each aware banker...
To spell out what the Economist didn't put in words: we're looking at a run on the banks.
Even if we take it broader, by eyeball, the period of that chart shows an increase of 40% in demand for the supernote, from say 210 billion euros in 2007 to 295 now. Crudely put, we could imagine the initial starting value as a normal and stable state, and attribute any increase to a shift by the people into safer money stores.
40% is a pretty significant vote against the banks of Europe. Demand for the supernote might just be an inverse signal of confidence in banking.
In this sense, the euphemisms such as 'mattress stuffers' and 'money launderers/ backfire: although bankers in the past were keen to apply these terms to their cash-using customers, it now appears that the shoe is on the other foot. The bankers need to explain to the people in which mattress is the missing trillion euros, or whatever the final bill for Europe's financial meltdown ends up being.
Saving the euro requires more pain for some, more generosity from others and fundamental change for all. Is it worth it? Sooner or later, citizens must be asked. Without their support, no reform can last. And a real choice must include the option of leaving the euro. Now that this taboo has been breached, the euro zone should start thinking about how best to arrange the departure of those that cannot, or will not, live by Germanic rules.
Else, if this explanation isn't provided, and the money found, demand for supernotes is likely to increase as confidence in the banking system suffers from more 'strain', to use another euphemism. Or, in other words, we're all money launderers now, and the only question left is who runs fastest to who's fat mattress, the bankers or the people?
Either way, one to watch!
October 31, 2011
_Currency Wars_
 If you want some view on the future, James Turk reviews a new book: Currency Wars, by Jim Rickards:
If you want some view on the future, James Turk reviews a new book: Currency Wars, by Jim Rickards:
.... the first part being almost surreal because it reads more like a novel than non-fiction. It details Rickards’ participation in an exercise at the Warfare Analysis Laboratory near Washington D.C. This group is one of the Defense Department’s leading venues for war games and strategic planning, but in a first-ever event, the game in which Rickards joined was not a war-fighting simulation. Rather, several dozen people from the military, academic and intelligence communities fought a global financial war using currencies and capital markets to support national interests. Rickards and two colleagues were invited to give the simulation some real-world, Wall Street expertise about markets, which they certainly did.I guarantee that when you start reading this part, you won’t put the book down until you learn the outcome of the war. It reads better than a suspense novel, even though the ending is somewhat anti-climactic and predictable. While I won’t spoil it for you by divulging the ending, I will note that gold has a big role to play. In fact, gold reappears throughout the whole book.
In the second section, Rickards analyzes the first two currency wars (CWI and CWII). ...
From the "you read it here first" department:
The final section of the book explains why the world is now fighting Currency War III, which Rickards believes began in 2010. He speculates that there are three possible outcomes from CWIII – paper, gold or chaos. Each of these alternatives is analyzed in detail, providing readers with much food for thought.
Actually, the scenes of this war go back to the issuance of the Euro as a credible alternative, and play their part in the great Financial Crisis of the 21st century. For confirmation of the thesis, Goldmoney's blog also pointed at The Real Contagion Risk which makes the same point: watch for the Central Banks to shift out of US Treasuries:
Step 1: As the global growth story frays, global trade decelerates, and the sovereign and total debt burdens of various countries drag at economic growth, fewer and fewer dollars will be accumulated and stored by various foreign central banks. The typical way dollars are stored is in the form of Treasury holdings. Because of this, several years of record-breaking Treasury accumulation by these foreign banks will grind to a halt and foreign Treasury holdings will begin to decline.
So what's our prediction? Well, it'll be a long slow decline from the dollar as reserve currency. The Euro looked good for a decade, but that's off it's shine now. Expect Central Banks to get back into the currency trading game -- and keep reserves of their bigger partners. And, the next shot in the war will be related to energy -- which is typically priced in dollars.
Gold? Well, everyone expects that to come up. James Turk says:
The harmful effects from abandoning gold still impair economic activity today because the necessary discipline has been removed from the monetary system, creating the global imbalances, debt loads, insolvent banks, risky derivatives and other problems that plague our world. So as economic activity sinks ever deeper into an abyss, think about the cause.
Yeah, and we used to say that governments should go back to the gold standard because we don't trust them with their own units.
Very proven true, no doubt, these days, but there has been a bit of a shift in thinking of late. For me, it was signalled by Alan Greenspan as far back as 1995 (?) when he said "nobody's listening any more." (In response to being asked why he didn't talk about gold anymore.) Fact is, governments will issue their own currencies, whether we trust them or not:
Namely, governments have created this mess, so we cannot rationally expect governments to get us out of it, which is something I have intuitively understood for some time but was also the main conclusion I reached from Rickards’ book.
And, the clanger is this: We don't trust governments, period. We don't trust them to issue their own inflation-protected currency, and we don't trust them to issue a gold-based unit either.
 So, gold goes free. Economists are no longer advising governments to base off gold, because we know it won't work. Gold therefore will remain the independent watchdog it has since the closing of the gold window by Nixon; a three-way tussle between central bankers, gold banks and the buying public.
So, gold goes free. Economists are no longer advising governments to base off gold, because we know it won't work. Gold therefore will remain the independent watchdog it has since the closing of the gold window by Nixon; a three-way tussle between central bankers, gold banks and the buying public.
The future is a world of competitive currencies, USD, Euros, Yen, the Chinese unit ... and gold. With a very slow long decline of the power of the USD.
Disclosure: Author is long gold, and short fingernails.
October 26, 2011
Phishing doesn't really happen? It's too small to measure?
Two Microsoft researchers have published a paper pouring scorn on claims cyber crime causes massive losses in America. They say it’s just too rare for anyone to be able to calculate such a figure.Dinei Florencio and Cormac Herley argue that samples used in the alarming research we get to hear about tend to contain a few victims who say they lost a lot of money. The researchers then extrapolate that to the rest of the population, which gives a big total loss estimate – in one case of a trillion dollars per year.
But if these victims are unrepresentative of the population, or exaggerate their losses, they can really skew the results. Florencio and Herley point out that one person or company claiming a $50,000 loss in a sample of 1,000 would, when extrapolated, produce a $10 billion loss for America as a whole. So if that loss is not representative of the pattern across the whole country, your total could be $10 billion too high.
Having read the paper, the above is about right. And sufficient description, as the paper goes on for pages and pages making the same point.
Now, I've also been skeptical of the phishing surveys. So, for a long time, I've just stuck to the number of "about a billion a year." And waited for someone to challenge me on it :) Most of the surveys seemed to head in that direction, and what we would hope for would be more useful numbers.
So far, Florencio and Herley aren't providing those numbers. The closest I've seen is the FBI-sponsored report that derives from reported fraud rather than surveys. Which seems to plumb in the direction of 10 billion a year for all identity-related consumer frauds, and a sort handwavy claim that there is a ration of 10:1 between all fraud and Internet related fraud.
I wouldn't be surprised if the number was really 100 million. But that's still a big number. It's still bigger than income of Mozilla, which is the 2nd browser by numbers. It's still bigger than the budget of the Anti-phishing Working Group, an industry-sponsored private thinktank. And CABForum, another industry-only group.
So who benefits from inflated figures? The media, because of the scare stories, and the public and private security organisations and businesses who provide cyber security. The above parliamentary report indicated that in 2009 Australian businesses spent between $1.37 and $1.95 billion in computer security measures. So on the report’s figures, cyber crime produces far more income for those fighting it than those committing it.
Good question from the SMH. The answer is that it isn't in any player's interest to provide better figures. If so (and we can see support from the Silver Bullets structure) what is Florencio and Herley's intent in popping the balloon? They may be academically correct in trying to deflate the security market's obsession with measurable numbers, but without some harder numbers of their own, one wonders what's the point?
What is the real number? Florencio and Herley leave us dangling at that point. Are they are setting up to provide those figures one day? Without that forthcoming, I fear the paper is destined to be just more media fodder as shown in its salacious title. Iow, pointless.
Hopefully numbers are coming. In an industry steeped in Numerology and Silver Bullets, facts and hard numbers are important. Until then, your rough number is as good as mine -- a billion.
October 18, 2011
Liability & disclosure - the end of an era is in sight?
Liability is increasing slowly for cyber-exposed companies. We're in an exploratory court phase as litigants try different things. For a while, we'll see these filings in USA courts, which won't get far ... but then one will find the formula, and a company will be hit by a huge judgement.
"The US Department of Defense has been hit with a $4.9 billion (£3.1 billion) lawsuit over a recently disclosed data breach involving TRICARE , a healthcare system for active and retired military personnel and their families."
Meanwhile, pressure for breach disclosure increases. Now the SEC is in on the act:
"The SEC guidance clarifies a long-standing requirement that companies report 'material' developments, or matters significant enough that an investor would want to know about them. The guidance spells out that cyberattacks are no exception.For example, the SEC says, a company probably will need to report on costs and consequences of material intrusions in which customer data are compromised. The company's revenue could suffer, and it could be forced to spend money to beef up security or fight lawsuits. In addition, if a company is vulnerable to cyberattack, investors may need to be informed of the risk, the SEC said."
This is also a first step that has increasing and more costly ramifications. May as well get used to it: disclosure will be part of the future. Liabilities are coming.
Perhaps the great age of software freedom is coming to an end, in more ways than one?
September 23, 2011
Global Jobbing
Blast from the past. The Economist talks about the great economic problem of our time. No, not global warming but global jobbing.
To understand why these changes are so exciting for some people and so scary for others, a good place to start is the oConomy section on the website of oDesk, one of several booming online marketplaces for freelance workers. In July some 250,000 firms paid some 1.3m registered contractors who ply their trade there for over 1.8m hours of work, nearly twice as many as a year earlier.ODesk, founded in Silicon Valley in 2003, is a "game-changer", says Gary Swart, its chief executive. His marketplace takes outsourcing, widely adopted by big business over the past decade, to the level of the individual worker. According to Mr Swart, this "labour as a service" suits both employers, who can have workers on tap whenever they need them, and employees, who can earn money without the hassle of working for a big company, or even of leaving home.
It is still small, but oDesk shows how globalisation and innovation in information technology, the two big trends that have been under way for some time, are moving the world nearer to a single market for labour. Much of the work on oDesk comes from firms in rich economies and goes to people in developing countries, above all the Philippines and India. Getting a job done through oDesk can bring the cost down to as little as 10% of the usual rate. So the movement of work abroad in search of lower labour costs is no longer confined to manufacturing but now also includes white-collar jobs, from computer programming to copywriting and back-office legal tasks. That is likely to have a big impact on pay rates everywhere.
It puts the whole thing into context of the current 2nd dip in USA and Europe. My first contribution to this debate was to predict the above in a paper & implementation of a jobs market in 1997. Because this used a sort of variation on Ricardian Contracts, and turned the global jobbing market into a financial system, it qualifies as FC.
(My second contribution was equally exciting, built in 2009-2010, and I guess someone will overtake it in 14 years as well. If you are in the angel business, you can find out about it sooner...)
Oh, and in case you didn't quite understand the oTalk above ... here's some hard econ data:
Michael Spence, another Nobel prize-winning economist, in a recent article in Foreign Affairs agrees that technology is hitting jobs in America and other rich countries, but argues that globalisation is the more potent factor. Some 98% of the 27m net new jobs created in America between 1990 and 2008 were in the non-tradable sector of the economy, which remains relatively untouched by globalisation, and especially in government and health care -- the first of which, at least, seems unlikely to generate many new jobs in the foreseeable future. At the same time, says Mr Spence, the mix of jobs available to Americans in the tradable sector (including manufacturing) that serves global markets is shifting rapidly, with a growing share of the positions suitable only for skilled and educated people.
(Readers will recognise Prof. Spence as the man who wrote the paper that inspired the silver bullets hypothesis.)
August 17, 2011
How Liability is going to kill what little is left of Internet security…
Long term readers will know that I have often written of the failure of the browser vendors to provide effective security against phishing. I long ago predicted that nothing will change until the class-action lawsuit came. Now signs are appearing that this is coming to pass:
That's changing rapidly. Recently, Sony faced a class action lawsuit for losing the private information of millions of users. And this week, it was reported that Dropbox is already being sued for a recent security breach of its own.It's too early to know if these particular lawsuits will get anywhere, but they're part of a growing trend. As online services become an ever more important part of the American economy, the companies that create them increasingly find that security problems are hitting them where it really hurts: the bottom line.
See also the spate of lawsuits against banks over losses; although it isn't the banks' direct fault, they are complicit in pushing weak security models, and a law will come to make them completely liable. Speaking of laws:
Computer security has also been an area of increasing activity for the Federal Trade Commission. In mid-June, FTC commissioner Edith Ramirez testified to Congress about her agency's efforts to get companies to beef up their online security. In addition to enforcing specific rules for the financial industry, the FTC has asserted authority over any company that makes "false or misleading data security claims" or causes harm to consumers by failing to take "reasonable security measures." Ramirez described two recent settlements with companies whose security vulnerabilities had allowed hackers to obtain sensitive customer data. Among other remedies, those firms have agreed to submit to independent security audits for the next 20 years.
Skip over the sad joke at the end. Timothy B. Lee and Ars Technica, author of those words, did more than just recycle other stories, they actually did some digging:
Alex Halderman, a computer science professor at the University of Michigan, to help us evaluate these options. He argued that consumer choice by itself is unlikely to produce secure software. Most consumers aren't equipped to tell whether a company's security claims are "snake oil or actually have some meat behind them." Security problems therefore tend not to become evident until it's too late.But he argued the most obvious regulatory approach—direct government regulation of software security practices—was also unlikely to work. A federal agency like the FTC has neither the expertise nor the manpower to thoroughly audit the software of thousands of private companies. Moreover, "we don't have really widely regarded, well-established best practices," Halderman said. "Especially from the outside, it's difficult to look at a problem and determine whether it was truly negligent or just the kind of natural errors that happen in every software project."
And when an agency found flaws, he said, it would have trouble figuring out how urgent they were. Private companies might be forced to spend a lot of time fixing trivial flaws while more serious problems get overlooked.
(Buyers don't know. Sellers don't know.)
So what about liability? I like others have recognised that liability will eventually arise:
This is a key advantage of using liability as the centerpiece of security policy. By making companies financially responsible for the actual harms caused by security failures, lawsuits give management a strong motivation to take security seriously without requiring the government to directly measure and penalize security problems. Sony allegedly laid off security personnel ahead of this year's attacks. Presumably it thought this would be a cost-saving move; a big class action lawsuit could ensure that other companies don't repeat that mistake in future.
But:
Still, Halderman warned that too much litigation could cause companies to become excessively security-conscious. Software developers always face a trade-off between security and other priorities like cost and time to market. Forcing companies to devote too much effort to security can be as harmful as devoting too little. So policymakers shouldn't focus exclusively on liability, he said.
Actually, it's far worse. Figure out some problem, and go to a company and mention that this issue exists. The company will ignore you. Mention liability, and the company will immediately close ranks and deny-by-silence any potential liability. Here's a variation written up close by concerning privacy laws:
...For everything else, the only rule for companies is just “don’t lie about what you’re doing with data.”The Federal Trade Commission enforces this prohibition, and does a pretty good job with this limited authority, but risk-averse lawyers have figured out that the best way to not violate this rule is to not make explicit privacy promises at all. For this reason, corporate privacy policies tend to be legalistic and vague, reserving rights to use, sell, or share your information while not really describing the company’s practices. Consumers who want to find out what’s happening to their information often cannot, since current law actually incentivizes companies not to make concrete disclosures.
Likewise with liability: if it is known of beforehand, it is far easier to slap on a claim of gross negligence. Which means in simple layman's terms: triple damages. Hence, companies have a powerful incentive to ignore liability completely. As above with privacy: companies are incentivised not to do it; and so it comes to pass with security in general.
Try it. Figure out some user-killer problem in some sector, and go talk to your favourite vendor. Mention damages, liability, etc, and up go the shutters. No word, no response, no acknowledgement. And so, the problem(s) will never get fixed. The fear of liabilities is greater than the fear of users, competitors, change, even fear itself.
Which pretty much guarantees a class-action lawsuit one day. And the problem still won't be fixed, as all thoughts are turned to denial.
So what to do? Halderman drifts in the same direction as I've commented:
Halderman argued that secure software tends to come from companies that have a culture of taking security seriously. But it's hard to mandate, or even to measure, "security consciousness" from outside a company. A regulatory agency can force a company to go through the motions of beefing up its security, but it's not likely to be effective unless management's heart is in it.
It's completely meaningless to mandate, which is the flaw behind the joke of audit. But it is possible to measure. Here's an attempt by yours truly.
What's not clear as yet is how is it possible to incentivise companies to pursue that lofty goal, even if we all agree it is good?
August 07, 2011
Regulating the future financial system - the double-entry headache needs a triple-entry aspirin
How to cope with a financial system that looks like it's about to collapse every time bad news turns up? This is an issue that is causing a few headaches amongst the regulators. Here's some musings from Chris Skinner over a paper from the Financial Stability gurus at the Bank of England:
Third, the paper argues for policies that create much greater transparency in the system.This means that the committees worldwide will begin “collecting systematically much greater amounts of data on evolving financial network structure, potentially in close to real time. For example, the introduction of the Office of Financial Research (OFR) under the Dodd-Frank Act will nudge the United States in this direction.
“This data revolution potentially brings at least two benefits.
“First, it ought to provide the authorities with data to calibrate and parameterise the sort of network framework developed here. An empirical mapping of the true network structure should allow for better identification of potential financial tipping points and cliff edges across the financial system. It could thus provide a sounder, quantitative basis for judging remedial policy actions to avoid these cliff edges.
“Second, more publicly available data on network structures may affect the behaviour of financial institutions in the network. Armed with greater information on counterparty risk, banks may feel less need to hoard liquidity following a disturbance.”
Yup. Real time data collection will be there in the foundation of future finance.
But have a care: you can't use the systems you have now. That's because if you layer regulation over policy over predictions over datamining over banking over securitization over transaction systems … all layered over clunky old 14th century double entry … the whole system will come crashing down like the WTC when someone flies a big can of gas into it.
The reason? Double entry is a fine tool at the intra-corporate level. Indeed, it was material in the rise of the modern corporation form, in the fine tradition of the Italian city states, longitudinal contractual obligations and open employment. But, double entry isn't designed to cope with the transactional load of of inter-company globalised finance. Once we go outside the corporation, the inverted pyramid gets too big, too heavy, and the forces crush down on the apex.
It can't do it. Triple entry can. That's because it is cryptographically solid, so it can survive the rigours of those concentrated forces at the inverted apex. That doesn't solve the nightmare scenarios like securitization spaghetti loans, but it does mean that when they ultimately unravel and collapse, we can track and allocate them.
Message to the regulators: if you want your pyramid to last, start with triple entry.
PS: did the paper really say "More taxes and levies on banks to ensure that the system can survive future shocks;" … seriously? Do people really believe that Tobin tax nonsense?
June 11, 2011
Bitcoin and tulip bulbs
 Many people are asking me about BitCoin, and I've put off writing about it because I need to be clear on why I think it is not a long term player. Of course, I've been wrong before ... Anyway, it looks like John Levine has done the job for me:
Many people are asking me about BitCoin, and I've put off writing about it because I need to be clear on why I think it is not a long term player. Of course, I've been wrong before ... Anyway, it looks like John Levine has done the job for me:
Bitcoin and tulip bulbsBitcoin, for anyone who's not up on their techno-trends, is this year's hot trendy digital payment system. Its main claim to fame is that it is peer-to-peer, not depending on a central bank to issue or validate the "coins", actually blobs of cryptographically signed bits. This makes it both fairly anonymous and hard to manipulate (at least in the ways that real money is manipulated), making it a darling of anarcho-libertarians.
A lot of people have opined on its merits, most notably this Quora message.
I took a look at the design of Bitcoin, which is credited to "Satoshi Nakamoto". Nobody seems to know who he is (or who they are), but he definitely knows his crypto. As a piece of cryptographic software design, it's quite clever. As a system you might want to use to pay for stuff, it's hopeless.
To somewhat adapt the arguments in the Quora message, Bitcoins suffer from two problems, one technical and the other economic. [techo-issue elided]
The other problem is economic. A year ago, you could buy bitcoins for about 1¢ apiece. In January, they cost about $1. Now they're about $10. We have a name for that -- it's a bubble. (Bitcoin fans tend to assume that bitcoins are money, and describe what's happending as deflation, but you'll have to look pretty hard to find any real-world examples of 1000 to 1 deflation.) Since there's no central bank to manage exchange rates, nor can you pay your taxes with them, which is the practical definition of money, a bitcoin is only worth what the next sucker thinks it's worth. So what we have here is a system that lets you pay for stuff with tulip bulbs, or perhaps shares of stock in theglobe.com.
John's rant mostly covers it, but for the hardcore monetarists I'll add: money is expected to be a store of value. BitCoin doesn't speak to value at all, and it is the antithesis of the Ricardian Contract, which describes its value in glorious and legal detail. So it's whatever value we as holders want it to be.
Typically such a bubble bursts when we run out of speculators who agree on its appeal. In this case, it is eerily familiar with history of last decade. It shares something of the media hype of DigiCash, and also the user-base of e-gold. So it will burst when we run out of cypherpunks, and when the user base reaches a tipping point.
And, as Lynn Bell pointed out, last decade was the decade of the alternative issuers. This decade, facebook, apple and google will try it, and may succeed (if that is they can keep the geeks at a distance and build an integrated team with some monetarists in it)...
Entries in the BitCoin Log
- Bitcoin and tulip bulbs
- Is BitCoin a triple entry system?
- BitCoin - the bad news
June 09, 2011
1st round in Internet Account Fraud World Cup: Customer 0, Bank 1, Attacker 300,000
More grist for the mill -- where are we on the security debate? Here's a data point.
In May 2009, PATCO, a construction company based in Maine, had its account taken over by cyberthieves, after malware hijacked online banking log-in and password credentials for the commercial account PATCO held with Ocean Bank. ....
There are two ways to look at this: the contractual view, and the responsible party view. The first view holds that contracts describe the arrangement, and parties govern themselves. The second holds that the more responsible party is required to be <ahem> more responsible. PATCO decided to ask for the second:
A magistrate has recommended that a U.S. District Court in Maine deny a motion for a jury trial in an ACH fraud case filed by a commercial customer against its former bank. According to the order, which must still be reviewed by the presiding judge, the bank fulfilled its contractual obligations for security and authentication through its requirement for log-in and password credentials. ....At issue for PATCO is whether banks should be held responsible when commercial accounts, like PATCO's, are drained because of fraudulent ACH and wire transfers approved by the bank. How much security should banks and credit unions reasonably be required to apply to the commercial accounts they manage?
"Obviously, the major issue is the banks are saying this is the depositors' problem," Patterson says, "but the folks that are losing money through ACH fraud don't have enough sophistication to stop this."
And lost.
David Navetta, an attorney who specializes in IT security and privacy, says the magistrate's recommendation, if accepted by the judge, could set an interesting legal precedent about the security banks are expected to provide. And unless PATCO disputes the order, Navetta says it's unlikely the judge will overrule the magistrate's findings. PATCO has between 14 and 21 days to respond."Many security law commentators, myself included, have long held that *reasonable security does not mean bullet-proof security*, and that companies need not be at the cutting edge of security to avoid liability," Navetta says. "The court explicitly recognizes this concept, and I think that is a good thing: For once, the law and the security world agree on a key concept."
My emphasis added, and it is an important point that security doesn't mean absolute security, it means reasonable security. Which from the principle of the word, means stopping when the costs outweigh the benefits.
But that is not the point that is really addressed. The question is whether (a) how we determine what is acceptable (not reasonable), and (b) if the Customer loses out when acceptable wasn't reasonable, is there any come-back?
In the disposition, the court notes that Ocean Bank's security could have been better. "It is apparent, in the light of hindsight, that the Bank's security procedures in May 2009 were not optimal," the order states. "The Bank would have more effectively harnessed the power of its risk- profiling system if it had conducted manual reviews in response to red flag information instead of merely causing the system to trigger challenge questions."But since *PATCO agreed to the bank's security methods when it signed the contract*, the court suggests then that PATCO considered the bank's methods to be reasonable, Navetta says. The law also does not require banks to implement the "best" security measures when it comes to protecting commercial accounts, he adds.
So, we can conclude that "reasonable" to the bank meant putting in place risk-profiling systems. Which it then bungled (allegedly). However, the standard of security was as agreed in the contract, *reasonable or not*.
That is, *reasonable security* doesn't enter into it. More on that, as the observers try and mold this into a "best practices" view:
"Patco in effect demands that Ocean Bank have adopted the best security procedures then available," the order states. "As the Bank observes, that is not the law."
(Where it says "best" read "best practices" which is lowest common denominator, a rather different thing to best. In particular, the case is talking about SecureId tokens and the like.)
Patterson argues that Ocean Bank was not complying with the Federal Financial Institutions Examination Council's requirement for multifactor authentication when it relied solely on log-in and password credentials to verify transactions. Navetta agrees, but the court in this order does not."The court took a fairly literal approach to its analysis and bought the bank's argument that the scheme being used was multifactor, as described in the [FFIEC] guidance," Navetta says. "The analysis on what constitutes multifactor and whether some multifactor schemes [out of band; physical token] are better than others was discussed, and, to some degree, the court acknowledged that the bank's security could have been better. Even so, it was technically multifactor, as described in the FFEIC guidance, in the court's opinion, and "the best" was not necessary."
Navetta says the court's view of multifactor does not jibe with common industry understanding. Most industry experts, he says, would not consider Ocean Bank's authentication practices in 2009 to be true multifactor. "Obviously, the 'something you have' factor did not fully work if hackers were able to remotely log into the bank using their own computer," he says. "I think that PATCO's argument was the additional factors were meaningless since the challenge question was always asked anyway, and apparently answering it correctly worked even if one of the factors failed. In other words, it appears that PATCO was arguing that the net result of the other two factors failing was going back to a single factor."
This problem has been known for a long time. When the "best practices" approach is used, as in this FFIEC example, there is a list of things you do. You do them, and you're done. You are encouraged to (a) not do any better, and (b) cheat. The trick employed above, to interpret the term "multi-factor" in a literal fashion, rather than using the security industry's customary (and more expensive) definition, has been known for a long long time.
It's all part of the "best practices" approach, and the court may have been wise to avoid further endorsing it. There is now more competition in security practices, says this court, and you'll find it in your contract.
Caveat: as with all such cases, this is a preliminary ruling, and it can be overturned including several times... before we see a precedent.
June 03, 2011
Declaration of Cyberwar - emerging hype cycle or growing nightmare?
Just when you thought it couldn't get any worse for infosec, there's more bad news on the horizon.
WASHINGTON—The Pentagon has concluded that computer sabotage coming from another country can constitute an act of war, a finding that for the first time opens the door for the U.S. to respond using traditional military force. ....In part, the Pentagon intends its plan as a warning to potential adversaries of the consequences of attacking the U.S. in this way. "If you shut down our power grid, maybe we will put a missile down one of your smokestacks," said a military official.
Recent attacks on the Pentagon's own systems—as well as the sabotaging of Iran's nuclear program via the Stuxnet computer worm—have given new urgency to U.S. efforts to develop a more formalized approach to cyber attacks. A key moment occurred in 2008, when at least one U.S. military computer system was penetrated. This weekend Lockheed Martin, a major military contractor, acknowledged that it had been the victim of an infiltration, while playing down its impact.
Cyberwarfare is becoming more than just another talking point for the US Military, it's becoming a plank in government policy.
How significant is this? Well here's a data point. Lieutenant-General David Hurley has just been appointed as the new Chief of the Australian Defence Force. In a TV interview that night, he stated that one of the top four priorities for his term is cyberwarfare [1]. He called each of the other three as gamechangers (to which I concur) but did not elaborate on his one-word declaration of cyberwar.
What does that mean, other than a scurrilous lead for Australia's infosecarrazi press to follow up on? *Cyberwarfare is now top drawer stuff*. While us infosec types are scrabbling around trying to figure out what all the fuss is about (theories including:
- media hype
- excuse for new divisions,
- just new lingo for what was once known as EW or Electronic Warfare,
- a more cost-effective way to extend foreign policy, where cost is equated to dead diggers on TV,
- interference in civilian affairs,
- landgrab for the new Big Brother state,
- domestic battle with the NSA, DSD, GCHQ and friends,
- etc etc, inter alia...)
the military has put it on the agenda. On the *top of the agenda* of a force of 58,000 permanent warmakers, now with new improved government sanction to go out and bomb some electrons.
 If the normally sensible Australians have bought into cyberwarfare, that means typically that the Americans are long gone down that path, and the British and Canadians have their walking shoes on as well. NATO won't be far behind, and NZ will join after their routine decade of protest.
If the normally sensible Australians have bought into cyberwarfare, that means typically that the Americans are long gone down that path, and the British and Canadians have their walking shoes on as well. NATO won't be far behind, and NZ will join after their routine decade of protest.
The future of information security may well travel down a government / compliance path as we're squeezed between the 363kg gorilla of cyberwarfare on the one side, and the general incompetence of vendors on the other side. This will see all the vendors drawn over to cyberwar side, and an inevitable loss of innovative work on in the private sector. Not that we saw a lot, but there was always hope.
The end result will be more wrong threat models leading to more best practices and ultimately more compliance directed out of a military/political agenda. The compliance cycle that we saw stifling the American anti-phishing efforts will be the beginning, not the end, it will become the sad norm, not the upsetting exception.
Curiously however, there may be new common sense over on the other side of the Pacific. Lt Gen Hurley's opposite number in USA has also just been appointed as the new Chair of the Joint Chiefs of Staff:
[General Martin] Dempsey is “deeply skeptical” of technology being able to alter the basic nature of combat. He wrote recently in the introduction to the Army’s main operating concept, “We operate where our enemies, indigenous populations, culture, politics, and religion intersect and where the fog and friction of war persists.” In the end, it comes down to boots on the ground performing their jobs under competent command leadership.His critics claim he doesn’t think as much as he should about future warfare and that he is too narrowly focused on the wars in Iraq and Afghanistan. ...
If anything's clear, the entry of the war machine into civilian cybersecurity affairs is likely to be bad news. Business and trade is far too delicate a thing to clobber with the heavy, blunt weapon of state responses. Maybe we need an old soldier to remind the futurists that war is actually a brutal thing?
No matter what the futurists have said over the last several centuries, it is always the grunts on the ground who are called upon to go in and make the job real. And it is always the people who bear the brunt of desk-flying futurists.

[1] Of the other three top priorities, one is the new fighter plane, the JSF or F35, which is Australia's largest defence purchase ever (ditto USA!). Another is the incorporation of the two new mini-carrier or logistical lift ships, which signals that Australia is going for integrated force projection, somewhat like Gen. Douglas MacArthur's island hopping in the Pacific campaign. In short, Australia is now building capacity to engage in the odd island invasion or two.
The third priority was equally big, but I don't recall it because I was too busy picking my jaw off the ground from hearing him slide that single neoligism into the middle of his conservative and comprehensive priorities.
June 01, 2011
#1 Censored Story - Dropping the Dollar
Someone pointed me to Project Censored, which has a list for the "25 top censored stories," and up there, right on top was "Global Plans to Replace the Dollar."
In July 2009, President Medvedev illustrated his call for a supranational currency to replace the dollar by pulling from his pocket a sample coin of a “united future world currency.” The coin, which bears the words “Unity in Diversity,” was minted in Belgium and presented to the heads of G8 delegations.In September 2009, the United Nations Conference on Trade and Development proposed creating a new artificial currency that would replace the dollar as reserve currency. The UN wants to redesign the Bretton Woods system of international exchange. Formation of this currency would be the largest monetary overhaul since World War II. China is involved in deals with Brazil and Malaysia to denominate their trade in China’s yuan, while Russia promises to begin trading in the ruble and local currencies.
Additionally, nine Latin American countries have agreed on the creation of a regional currency, the sucre, aimed at scaling back the use of the US dollar.
 Avid readers of FC will know this has been going on for a long time (long list here), and it's nice to see the news from the last 2 years concisely rendered.
Avid readers of FC will know this has been going on for a long time (long list here), and it's nice to see the news from the last 2 years concisely rendered.
Question of some pondering for me was, then, why is this *the number 1 censored story* ? Well, if one thinks about it some, the connection is clear.
In order to maintain the powerbase of Washington DC, the USD must remain supreme, because it is by the power of the dollar that economic force is wielded around the world, and it is the power of the dollar that buys the military machine at the pointy end of Ferguson's comment.
Except, this party's over. Outside the media eye, for a decade now, the world has been easing gently over to a multicurrency future. Here's just more latest news:
Mexico has quietly purchased nearly 100 tons of gold bullion, as central banks embark on their biggest bullion buying spree in 40 years. The purchase, reported in monthly data published by Mexico’s central bank, is the latest in a series of large gold buys by emerging market economies intent on diversifying reserves away from the faltering US dollar. China, Russia and India have acquired large amounts of gold in recent years, while Thailand, Sri Lanka and Bolivia have made smaller purchases.*Central banks became net buyers of gold last year after two decades of heavy selling* – a reversal that has helped propel the price of bullion to a series of record highs. On Wednesday gold was trading at about $1,510 a troy ounce, down 4 percent from a nominal record high of $1,575.79 reached on Monday.
As a result of Mexico’s purchase, central banks, sovereign wealth funds and other so-called “official sector” buyers are on track to record their largest collective purchase of gold since the collapse of the Bretton Woods system, which pegged the value of the dollar to gold, in 1971. GFMS, a precious metals consultancy, had predicted that the official sector would make net gold purchases of 240 tons this year, compared with a post-Bretton Woods peak of 276 tons in 1981.
 So why slap the heavy stamp of censorship on such a boring finance story? No bodies, no blood, no bombs.
So why slap the heavy stamp of censorship on such a boring finance story? No bodies, no blood, no bombs.
Because every day this story is unknown is another day without currency flight, and another day the current regime avoids the tough questions. It buys more time for *everything else* that is going on. E.g., one supposes, Obama's efforts to balance his budget, contain inflation, withdraw forces from land wars in Asia, and other tasks in the struggle for peace.
So, it's the number one story to censor because it is the number one story to those who are in a position to censor. For the rest of us, it isn't, it's just more humdrum and drone and 1 percent this and 2 percent that.
"And," as my local TV station closes every day without fail, "that's finance."
May 31, 2011
Gold can only be bought with cash. Please Select!
Chris Skinner talks about his surreal experience with a gold ATM:
The idea is that you put cash in and get gold out.So nice.
I plumped for the cheapest gold nugget priced at £100 and inserted my MasterCard.
Oh no, it didn’t work.
I guess that’s because you need to go to the other ATM to get cash to come back and get your gold.
With gold now enjoying its resurgence in notoriety as the alternate world currency, it's probably time to refresh our memory of the May Scale, reproduced below.
Fig. 1. The May Scale
With such a scale at hand, it is easy to see why the gold ATM doesn't take credit cards. Even without the May Scale tucked in your wallet, just in case you thought to whip it out and read out the laws of economics to your ATM, this one gives you handy instructions:

April 05, 2011
If data breaches are feared more than hackers, what is the perverse result?
This headline struck my attention:
Data Breaches Feared More than HackersThe majority of compliance professionals feel that their organizations are well or very well prepared to fend off hacker attacks, however, their confidence wanes significantly when assessing other data breach threats. This according to a survey conducted by the Society of Corporate Compliance and Ethics (SCCE) and the Health Care Compliance Association (HCCA).
This mirrored my results in The Market for Silver Bullets, in that the cost of the loss to intangibles and indirects such as reputation and compliance reviews would far outweigh the direct losses to the individuals. Consequently, this would have perverse effects on the treatment of risks.
I didn't really go into what those perverse effects were. Suffice, I thought at the time, to say, security's really screwed up, there is no way you can expect a rational result from this mess. But one thing struck me on reading that heading.
If the indirect effects of the data breach are feared more than the direct effects of the hacker's impacted damages, then there is an easy solution. Simply share the results, and generate a win-win for both. E.g., if the hacker manages to breach, and steal X data sets, he now has two opportunities. He can either exploit the breach set for some gain X*y where y is the average gain per identity, or he can settle with the lead victim.
Because we know that the indirect costs to the victim will far outweigh the direct gain to the attacker, there is an easy settlement. The victim is easily incentivised to pay for the breach to be settled without additional costs. And the attacker gains too as he has less work to do. Negotiation will find a convenient price between the two bounds.
Thus, this state of affairs predicts that the market for silver bullets leads to a market for extortion. Hack citibank, sell them their data back. I have no firm data, but I am comfortable with predicting that the difference is an order of magitude. That is, the costs to the victim are around 10 times the benefit to the attacker. Plenty of room there for a win-win solution.
(For those who are worried about the impact of an illegal contract, it is easy enough to put a silk dress on the pig and sell the breach techniques, with an NDA attached. This of course is the worry behind those breach markets. How close to extortion does it take us? Where do the morals stop and where does the crime start? A topic for another day...)
As a slight footnote, to confirm my prediction of this particular perverse result, I followed the article. Here's the relevant section found on the survey provider's site, two groups called Society of Corporate Compliance and Ethics and Health Care Compliance Association.
Fears of an accidental breach far outweigh fears of an intentional breach. Respondents were asked how likely they felt that data would be released through hacking attacks, intentional breaches by employees and third party vendors, and accidental breaches by employees and vendors. In general the feeling was that accidental breaches were far more likely. Just 8% felt that it was somewhat or very likely a hacker would gain access to the system, When it came to breaches by employees, 61% thought an accidental breach was somewhat or very likely, but just 30% thought the same of an intentional breach. Likewise 41% thought an accidental breach by a third party vendor was somewhat or very likely but only 13% thought an intentional breach was somewhat or very likely.
Unfortunately, no such luck. Right crowd, different story :) Oh well. So markets in extortion won't happen, right?
January 28, 2011
The Zippo Lighter theory of the financial crisis (or, who do we want to blame?)
The Economist summarises who the Financial Crisis Inquiry Commission of USA's Congress would like to blame in three tranches. For the Democrats, it's the financial industry and the de-regulation-mad Republicans:
The main report, endorsed by the Democrats, points to a broad swathe of failures but pins much of the blame on the financial industry, be it greed and sloppy risk management at banks, the predations of mortgage brokers, the spinelessness of ratings agencies or the explosive growth of securitisation and credit-default swaps. To the extent that politicians are to blame, it is for overseeing a quarter-century of deregulation that allowed Wall Street to run riot.
For the Republicans:
A dissenting report written by three of the Republicans could be characterised as the Murder on the Orient Express verdict: they all did it. Politicians, regulators, bankers and homebuyers alike grew too relaxed about leverage, helping to create a perfect financial storm. This version stresses broad economic dynamics, placing less emphasis on Wall Street villainy and deregulation than the main report does.
Finally, one lone dissenter:
A firmer (and, at 43,000 words, longer) rebuttal of the report by the fourth Republican, Peter Wallison, puts the blame squarely on government policies aimed at increasing home ownership among the poor. Mr Wallison argues that the pursuit of affordable-housing goals by government and quasi-government agencies, including Fannie Mae and Freddie Mac, caused a drastic decline in loan-underwriting standards. Over 19m of the 27m subprime and other risky mortgages created in the years leading up to the crisis were bought or guaranteed by these agencies, he reckons. These were "not a cigarette butt being dropped in a tinder-dry forest" but "a gasoline truck exploding" in the middle of one, Mr Wallison says.
 Yessss..... That's getting closer. Not exactly a gasoline truck, as that would have one unfortunate spark. More like several containers, loaded with 19m fully-loaded zippo lighters driven into the forest of housing finance one hot dry summer, and distributed to as many needy dwellers as could be found.
Yessss..... That's getting closer. Not exactly a gasoline truck, as that would have one unfortunate spark. More like several containers, loaded with 19m fully-loaded zippo lighters driven into the forest of housing finance one hot dry summer, and distributed to as many needy dwellers as could be found.
Now, who would have driven that truck, and why? Who would have proposed it to the politicians? Ask these questions, and we're almost there.
December 23, 2010
Ernst & Young called to account -- should Audit firms be investigated for their role in the crisis?
 In a long series of essays on the topic of Audit, I asked the question, why didn't the Audit firms pick up the disasters of the global financial crisis? Not all of those failed firms, as that would be too much to ask, but not even one?
In a long series of essays on the topic of Audit, I asked the question, why didn't the Audit firms pick up the disasters of the global financial crisis? Not all of those failed firms, as that would be too much to ask, but not even one?
As far as I know, no audit firm rang any alarm for any impending disaster for any business that consequently ran into trouble in the GFC. Not a single one!
Which raises the question: not even accidental combinations of misfortunes are being noticed by Auditors? What would it take to get an auditor to ring the alarm bell?
We have a statistically significant sample -- all the world's big firms. By some statistical hypothesis, either some alarm bells should have rung, or, no alarm bells were ever going to ring.
Some might be asking the same thing. Ernst & Young have now been sued by the New York Attorney General, Andrew Cuomo:
NEW YORK (Reuters) – Accounting firm Ernst & Young was sued by New York prosecutors over allegations it helped to hide Lehman Brothers' financial problems, in the first major government legal action stemming from the Wall Street company's 2008 downfall.The civil fraud case contends that Ernst & Young stood by while Lehman used accounting gimmickry to mask its shaky finances. The lawsuit says Lehman ran "a massive accounting fraud," but it did not name as defendants any former top executives at the investment bank whose September 2008 collapse helped spark the global financial crisis.
You can read the indictment here. Now, it's hard to speculate reliably as to where this will go, other than to a quiet settlement. What is more interesting to me at the systemic level is that an audit firm is being brought to account.
People close to Cuomo said one factor in bringing the case was that he knows that the U.S. Securities and Exchange Commission already is investigating former Lehman chief Richard Fuld and other former top Lehman executives.Cuomo "wants to go after the one party he knows isn't being sued," said John Coffee, a professor of corporate law at Columbia University.
Whatever that means. Ernst & Young predictably say they did nothing wrong and all transactions were "by the book." Could well be, and the court will no doubt audit that very statement, as well as the statements of the bankrupcy court:
The lawsuit comes nine months after a court-appointed examiner in the Lehman bankruptcy concluded that Ernst & Young was "professionally negligent" in its audit duties.The report by examiner Anton Valukas also said that Lehman could also have claims against Fuld and former chief financial officers Chris O'Meara, Erin Callan and Ian Lowitt for negligence or breach of fiduciary duty related to the use of Repo 105 transactions.
For me, the big question remains: if we can't expect an audit firm to pick up any signs of trouble, what can we expect of them? Perhaps we could save our money and do our due diligence another way?
The lawsuit seeks more than $150 million in fees that Ernst & Young received from 2001 to 2008 as Lehman's outside auditor -- less than 1 percent of its global annual revenue -- plus other unspecified damages.
However it turns out, the result will be important.
December 12, 2010
Mervyn King calls us to the Old Lady's deathbed?
I've been watching an odd series of posts over in UK's Finanser site with amusement:
All along the lines of,
- the public has lost faith in the banks,
- are looking for any alternative,
- Meanwhile a bunch of social alternatives have popped up,
- so there are alternatives.
Add to that the fact that securitization renders banking a historical inefficiency, and central banking a vestigial cost structure (see the impromptu series on the end of banking, I, II, III).
It's time to change the music, but I've predicted that nobody's going to be the first to say that.
I spoke too soon. Last month, Hasan pointed to Mervyn King again, who's just come out and said:
"One might well say that a financial crisis occurs when the Basel risk weights turn out to be poor estimates of underlying risk. And that is not because investors, banks or regulators are incompetent. It is because the relevant risks are often impossible to assess in terms of fixed probabilities. Events can take place that we could not have envisaged, let alone to which we could attach probabilities. If only banks were playing in a casino then we probably could calculate appropriate risk weights. Unfortunately, the world is more complicated. So the regulatory framework needs to contain elements that are robust with respect to changes in the appropriate risk weights, and that is why the Bank of England advocated a simple leverage ratio as a key backstop to capital requirements."
In short, what the Governor is saying is that Basel III is not the answer. It might be part of the answer, but he's raising some skepticism. Then, he discusses solutions:
"Another avenue of reform is some form of functional separation. The Volcker Rule is one example. Another, more fundamental, example would be to divorce the payment system from risky lending activity - that is to prevent fractional reserve banking (for example, as proposed by Fisher, 1936, Friedman, 1960, Tobin, 1987 and more recently by Kay, 2009).
Blink and you missed it! The end of fractional reserve banking? On the table?
In essence these proposals recognise that if banks undertake risky activities then it is highly dangerous to allow such "gambling" to take place on the same balance sheet as is used to support the payments system, and other crucial parts of the financial infrastructure. And eliminating fractional reserve banking explicitly recognises that the pretence that risk-free deposits can be supported by risky assets is alchemy. If there is a need for genuinely safe deposits the only way they can be provided, while ensuring costs and benefits are fully aligned, is to insist such deposits do not coexist with risky assets.
So there we have the reversion to Glass-Steagall and removal of deposit taking from risk-making, or as he puts it, kicking the payments system out of banks' jurisdiction. My words fail, so back to his:
We certainly cannot rely on being able to expand the scope of regulation without limit to prevent the migration of maturity mismatch. Regulators will never be able to keep up with the pace and scale of financial innovation. Nor should we want to restrict innovation. But it should be undertaken by investors using their own money not by intermediaries who also provide crucial services to the economy, allowing them to reap an implicit public subsidy. It will not be possible to regulate all parts of the financial system as if they were banks. ...
Which in effect is a fall-back to Glass-Steagal, but this time there is a recognition of something called the migration of maturity mismatch. Innovation might be the cassus belli above, but securitization is firmly in Mr King's sites.
But, wait, there's more! Across the pond, Mr King reports that they're talking about redeeming the implied public subsidy of lender of last resort:
As Jeffrey Lacker, President of the Federal Reserve Bank of Richmond, has argued, "merely expanding the scope of regulation to chase those firms that extract implicit guarantees by engaging in maturity transformation would be an interminable journey with yet more financial instability in its wake" (Lacker, 2010).
For "implicit guarantee" read lender of last resort. For "maturity transformation" read securitization, CDOs and the shift from banking to market.
It's happening. Jeffrey Lacker of the Fed has called for a stop to the lender of last resort, and the Governor of the world's first central bank has put it on the table for negotiation. In effect, they're throwing in the towel. In speech celebrating the inventor of the central bank, Mervyn King has called the beginning and the end of an era of financial history.
Central banking is on its last legs, the Old Lady of Threadneedle Street is on her deathbed.
What remains is to give her a decent burial, and preserve our economy in her wake. The shift from Banking to Markets continues, apace.
- What banking is. (Essential for predicting the end of finance as we know it.)
- What caused the financial crisis. (Laying bare the end of banking.)
- A small amount of Evidence. (In which, the end of banking and the rise of markets is suggested.)
- Mervyn King calls us to the Old Lady's deathbed?
- (Introducing the death of the partner and the central bank as turbocharger as 2 new causes)
December 03, 2010
A small amount of Evidence. (In which, the end of banking and the rise of markets is suggested.)
In the last couple of weeks I posted a thesis on what caused the global financial crisis. In technical terms it is the invention and usage of securitization, a.k.a., the market for mortgage-backed securities. In economic and policy terms, it is the shift from banking to markets .
It sounds too simple to be true, but I'll stick to my guns. So, how to show this? Scientifically this is a difficult one to show. Instead, I'll just do this: make observations on big things happening, and interpret them from the theory.
Let's look at the EU who are currently dealing with Ireland. Here's the Economist summary:
The decision by finance ministers in the EURO ZONE to create a European Stabilisation Mechanism as a permanent system for resolving future sovereign-debt difficulties did little to soothe markets, at least at first. The mechanism distinguishes a "solvency" crisis from a "liquidity" one, with bondholders in insolvent countries expected to take the brunt of losses, but does not come into force until 2013. However, markets were encouraged by a hint of more immediate help from the European Central Bank. Jean-Claude Trichet, the ECB's president, advised that people were "tending to underestimate the determination" in Europe to solve the debt crisis. - See article
What does that tell us? Well, the EU went in with a big fat cheque book and acted as lender of last resort, one of the primary functions of central banks. They bailed out Ireland (the country, the banks, the economy, whichever). And the markets weren't impressed.
Europe's policymakers are crying foul. "The speculation on international financial markets can't be explained rationally at all," declared Wolfgang Schäuble, Germany's finance minister.
It's entirely rational: lender of last resort is appropriate to banking, but not appropriate to markets. The markets themselves have figured out the first part, the politicians, not.
(OK, so this skims past the second part, how to deal with markets, and all the pointed questions of what EU should do right now; and how to get themselves out of the mess -- see the article for more on that. I'm simply concentrating on the core, underlying, fundamental systemic cause of failure. Without understanding that, there is no foundation in discussing policy or rescue prescriptions.)
Let's now turn to the USA. There, the highly successful Federal Reserve has now revealed more details about how it managed the crisis:
The numbers are staggering, encompassing more than a dozen emergency programs set up starting in 2007 or 2008. In one program alone the Fed doled out nearly $9 trillion in funds to borrowers such as Morgan Stanley and Merrill Lynch, largely at interest rates below 1 percent. (This program involved overnight loans, so the amount of Fed credit outstanding at any single point in time was much smaller.)Other programs, with longer-term loans also measured in the trillions of dollars.
The Fed actions were just part of a larger array of government bailouts for the financial industry, which were deeply unpopular with most Americans. Rescue programs run outside the Fed included insurance-style backstops for bank debts and the investments from the Treasury's $700 billion TARP (Troubled Asset Relief Program).
In contrast to the EU, the Fed went to town, bought everything ... and is now able to sell it all back:
At the same time, it's possible that the release of details will end up largely vindicating the Fed for the massive financial support that it gave the economy at a time of severe stress. The emergency loans, in the view of many finance experts, helped to avert a much deeper economic slump. And those loans have now been largely paid back without losses to the central bank.
The Fed therefore scores top points as lender of last resort, and the obvious complaint is that the EU isn't spending enough. However, there is a rider or caveat on that:
"My view is that the Fed has done an excellent job since the crisis started, but they didn't do a very good job before the crisis started," says Pete Kyle, a finance expert at the University of Maryland. He says the central bank, as a key financial regulator, should have ensured that US banks had plenty of capital on hand to weather a storm.Some other economists echo that view, arguing that the Fed and other bank regulators should have done much more to safeguard against a surge in high-risk mortgage lending during the years leading up to the crisis, at a time when US home prices were soaring.
Once a crisis is under way, however, the standard view among economists is that a central bank should act as a "lender of last resort," providing credit as freely as possible to prevent widespread bank failures at a time when ordinary investors are in a panic.
When people resort to language like "the standard view" we know something's wrong. The economists are wobbling: they know the standard view, they see the lender of last resort is facing bankrupcy under its own rules, and they're feeling quite bad and conflicted about it.
Whatever is happening to the skepticism of the markets and the economists, this still doesn't tell the ordinary people what went wrong. We're so used to conflicting signals from economists and markets, we'll discount them all without a second thought.
Let's get a little bit more haptic. Let's reach in and touch the problem. Here it is:
Dan Edstrom is a guy who is in the right place at the right time. His profession? He performs securitization audits (Reverse Engineering and Failure Analysis) for a company called DTC-Systems.The typical audit includes numerous [stuff, snipped]. The following flow chart reverse engineers the mortgage on the Ekstrom family residence. It took Dan over one year to take it this far and it clearly demonstrates what happens when there are too many lawyers being manufactured.
Dan went in and documented the mortgage on his house. Think of this as who owns Dan and Teri's house? or from an accountant's pov, who owns the cash flow?
Do you understand it? Of course not. Be not ashamed, the real point is, nobody else understands it either, and that includes the banks.
When the banks found themselves masters of the mortgage-backed securities market, they were holding onto a poisoned chalice. The value that was released in this method was immense: the entire risk premium of banking was delivered into their hands within days, but in exchange for selling off the banking risk, they took on a complexity risk as graphically suggested in that above diagram (or tabulated by ProPublica).
The first premium was large enough to overshadow the second negative premium; can you say appetite for risk? What inevitably occurred was a ponzi-like feeding frenzy on mortgage-backed securities, while complexity created a powder keg with a slow-burn fuse under the castle.
Quite how the spark gradually ate its way along the slow-burn fuse to the powder keg within is a fascinating subject, and one that many will discuss. Many causes and effects within. However, the key issue is this: switching from long term loans to the mortgage-backed securities market, a.k.a. securitization not loans, was the crux.
Now, if we see that, and we recognise there is no turning back, then the big question is, how are the central bankers going to deal with the shift from banking to markets ?
- What banking is. (Essential for predicting the end of finance as we know it.)
- What caused the financial crisis. (Laying bare the end of banking.)
- A small amount of Evidence. (In which, the end of banking and the rise of markets is suggested.)
- Mervyn King calls us to the Old Lady's deathbed?
- (Introducing the death of the partner and the central bank as turbocharger as 2 new causes)
November 27, 2010
What caused the financial crisis. (Laying bare the end of banking.)
Another month, another mini-crisis. Many banks remain in trouble, many countries too, adding weight to the claim that we're not through yet. Say hello, double dip, or depression. Whatever the economists end up calling it, it will be with us for a few years yet.
For what it's worth, I'd suggest this will be a 10 year story. Today's news is about Ireland, yesterday we were in Greece, tomorrow it will be another fun travel destination, where our money will buy more, as long as it's not us.
Each of those countries are looking at scenarios that will be a decade minimum to work through, to pay off their debt.
What does that make a citizen think?
Whatever you think about your national profits for the next decade being expropriated for the sins of your fathers, it seems to make sense to take more than ordinary care, and to sort it out properly this time. This one isn't the localised moral hazard of the S&L crash, it isn't the Asian Financial story of dominos too cozy, it isn't the Russian panic, nor LTCM.
Those were regular, this one's exceptional. This is more like the Japanese experience, on an OECD scale, or the Great Depression. Both things which were at their root central banking crises.
 So what's the cause? It does all seem to be a bit bemusing as theory after damnable theory goes wafting by, and still we don't see the end of the crisis. Theories I've seen and dismissed as mere symptoms:
So what's the cause? It does all seem to be a bit bemusing as theory after damnable theory goes wafting by, and still we don't see the end of the crisis. Theories I've seen and dismissed as mere symptoms:
- derivatives blowup
- sub-prime meltdown
- greed, pure filthy evil greed
- incentives for (greedy, evil) bankers
- cost of wars and other remote adventures
- regulatory intervention
- Sarbanes-Oxley and the death of a thousand cuts
- BIS's capital ratio and how nobody paid attention
- repeal of Glass-Steagall
- the shift away from dollar as reserve supremo
- too big to fail
- moral hazard
- rating agency fraud
- naked short selling
- explosion of public debt...
There is one and only one underlying cause for this crisis. It's the thing that answers everything, and the thing that nobody wants to talk about. It's the massive shift in structural nature of the business that took 30 years to develop, and suddenly everyone's caught by surprise.
It's banking, or more precisely, it's
the end of banking, as we know it
(Which is why I wrote a long post on what banking is.) Banking is no longer essential to society because there is now another method to achieve what banking achieves. That is, we now have two methods to distribute society's savings on the stage of the economy: from small-left to big-right, as it were. Both methods work, but the new method has advantages that will make it dominate over time.
The new method is called:
securitization
It's new, because it was invented in the USA in 1970 (hence the Z). While it is pretty simple to describe, it is (arguably) complex to see:
- take say 1000 vertical loans to people such as housing mortgages,
- aggregate them up into a huge single fund (essentially, a company that handles the cash flow from the loans)
- then slices the fund up horizontally into say 5000 shares
- sell the shares!
- new shareholders are paid the a tiny slice of each mortgage, until term.
I'll leave it as an exercise for the reader to compare how that relates to banking, and just skip to the essence of the shift from the definition of banking: term. The bank can "originate" these loans to the 1000 customers, aggregate them into a fund, slice the fund into shares, and sell the shares.
Here's the clanger: At this point, the bank has sold off the loans to other investors, which means the bank has sold off the risk.
After this point, the bank is no longer in the risk business! What's more, it can do this in 100 days and under. Which means it is no longer in the term business either.
Which means, the bank and those loans are no longer at risk of the economy. Nor a run. In fact, the bank need no longer be in the risk business at all, because it can sell off all its risk. To a market. As the ever-popular Prof Ferguson puts it:
These changes swept away the last vestiges of the business model depicted in It's a Wonderful Life. Once there had been meaningful social ties between mortgage lenders and borrowers. James Stewart's character knew both the depositors and the debtors. By contrast, in a securitized market the interest you paid on your mortgage ultimately went to someone who had no idea you existed. The full implications of this transition for ordinary homeowners would become apparent only 25 years later.
Which means, anyone doing business in securitization is not doing banking.
Now go back to the structure of the banking industry. I showed that the structure, and the regulation, was predicated on the risk inherent in the term structure of banking loans.
As banks are no longer taking on that risk, the structure is no longer required. That is, central banking is no longer useful to the economics of banking, and regulation based on public policy interests and lender of last resort issues is therefore unfounded.
Which further means the regulation is probably (almost certainly) wrong, the incentives are mismatched, the risk analysis is unnecessary, ... on and on it goes. Add in a dash of technology like the Internet, cryptography, and disintermediation (think Zopa or microfinance) and the mix is heady, and unstoppable.
Banks are not doing banking any more, so trying to make them act like they were doing banking is not helpful, it is harmful. In economics terms, there is a fundamental shift:
from banking to markets
But the world is still treating banks as if they do banking. From Basel-3 on down:
But on one point Pandit [Vikram Pandit, CEO of Citigroup] cannot be challenged. Since the promulgation of Hammurabi's Code, in ancient Babylon, no advanced society has survived without banks and bankers. Banks enable people to borrow money, and, today, by operating electronic-transfer systems, they allow commerce to take place without notes and coins changing hands. They also play a critical role in channelling savings into productive investments....
When the banking system behaves the way it is supposed to - as Pandit says Citi is now behaving - it is akin to a power utility, distributing money (power) to where it is needed and keeping an account of how it is used. Just like power utilities, the big banks have a commanding position in the market, which they can use for the benefit of their customers and the economy at large.
So the regulators are making mistakes, a steady series of them. Says TheFinanser's Chris Skinner in evident disgust at the BIS's numberitis:
Hmmm ... HBOS had a higher Tier I Capital Ratio than Lloyds TSB in 2008; Alliance & Leicester and Bradford & Bingley were well above the BIS requirements; RBS is particularly well capitalised; and Northern Rock appeared to have no issue in 2007, as mentioned.And yet, these are all the failed banks of Britain!
This Tier I Capital Ratio measure ain't that good is it?
The rules of the financial world have changed, the structures have not.
In particular, banks are off-the-hook for term failures, but they still make money as if they were on-the-hook. Hence, as banks and other participants discovered that securitization was a licence to print money (because the risk had been sold off to others in the funds markets) what happened?
Everyone dived madly into subprime. Everyone made money! Appetite for risk went sky high, because ... the risk was sold off to the market, and all that was left was the fees! Hence, we had a bubble of risk off-selling in many forms which ultimately led to the global financial crisis.
(You're probably wondering why the banks got so stuck when they had sold off their risk. It may be because <drumroll> they also bought securitized assets from the same markets that they'd sold into! </tara> Outstanding shift from Banking to Speculators, further exercise left for reader, look to the definition of banking again!)
Nobody in the world of banks dares admit it, because the money is too good. But it can't last, and some are wise to the game. Prof. Ferguson pointed to a speech by Mervyn King:
Mervyn King, governor of the Bank of England, called on Tuesday night for banks to be split into separate utility companies and risky ventures, saying it was "a delusion" to think tougher regulation would prevent future financial crises.Mr King's call for a break-up of banks to prevent them becoming "too important to fail" puts him sharply at odds with the direction of domestic and international banking reform.
What's the new world, where banks are no longer needed to do banking? Well, smaller, more purpose-limited ventures is one good start. "Utilities" is a good word. Expect to see more of this sort of proposal.
But, don't expect to see anyone agree that it's the end of banking, as that is still too politically untenable.
- What banking is. (Essential for predicting the end of finance as we know it.)
- What caused the financial crisis. (Laying bare the end of banking.)
- A small amount of Evidence. (In which, the end of banking and the rise of markets is suggested.)
- Mervyn King calls us to the Old Lady's deathbed?
- (Introducing the death of the partner and the central bank as turbocharger as 2 new causes)
November 21, 2010
What banking is. (Essential for predicting the end of finance as we know it.)
To understand what's happening today in the economy, we have to understand what banking is, and by that, I mean really understand how it works.
This time it's personal, right? Let's starts with what Niall Ferguson says about banking:
To understand why we have come so close to a rerun of the 1930s, we need to begin at the beginning, with banks and the money they make. From the Middle Ages until the mid-20th century, most banks made their money by maximizing the difference between the costs of their liabilities (payments to depositors) and the earnings on their assets (interest and commissions on loans). Some banks also made money by financing trade, discounting the commercial bills issued by merchants. Others issued and traded bonds and stocks, or dealt in commodities (especially precious metals). But the core business of banking was simple. It consisted, as the third Lord Rothschild pithily put it, "essentially of facilitating the movement of money from Point A, where it is, to Point B, where it is needed."
As much as the good Prof's comments are good and fruitful, we need more. Here's what banking really is:
Banking is borrowing from the public on demand, and lending those demand deposits to the public at term.
Sounds simple, right? No, it's not. Every one of those words is critically important, and change one or two of them and we've broken it. Let's walk it through:
Banking is borrowing from the public ..., and lending ... to the public.
Both from the public, and to the public. The public at both ends of banking is essential to ensure a diversification effect (A to B), a facilitation effect (bank as intermediary), and ultimately a public policy interest in regulation (the central bank). If one of those conditions aren't met, if one of those parties aren't "the public", then: it's not banking. For example,
- a building society or Savings & Loan is not doing banking, because .. it borrows from *members* who are by normal custom allowed to band together and do what they like with their money.
- a mutual fund is not banking because the lenders are sophisticated individuals, and the borrowers are generally sophisticated as well.
- Likewise, an investment bank does not deal with the public at all. So it's not banking. By this theory, it's really a financial investment house for savvy players (tell that to Deutschebank when it's chasing Goldman-Sachs for a missing billion...).
So now we can see that there is actually a reason why the Central Banks are concerned about banks, but less so about funds, S&Ls, etc. Back to the definition:
Banking is borrowing ... on demand, and lending those demand deposits ... at term.
On demand means you walk into the bank and get your money back. Sounds quite reasonable. At term means you don't. You have to wait until the term expires. Then you get your money back. Hopefully.
The bank has a demand obligation to the public lender, and a (long) term promise from the public borrower. This is quaintly called a maturity mismatch in the trade. What's with that?
The bank is stuck between a rock and a hard place. Let's put more meat on these bones: if the bank borrows today, on demand, and lends that out at term, then in the future, it is totally dependent on the economy being kind to the people owing the money. That's called risk, and for that, banks make money.
This might sound a bit dry, but Mervyn King, the Governor of the Bank of England, also recently took time to say it in even more dry terms (as spotted by Hasan):
3. The theory of bankingWhy are banks so risky? The starting point is that banks make heavy use of short-term debt. Short-term debt holders can always run if they start to have doubts about an institution. Equity holders and long-term debt holders cannot cut and run so easily. Douglas Diamond and Philip Dybvig showed nearly thirty years ago that this can create fragile institutions even in the absence of risk associated with the assets that a bank holds. All that is required is a cost to the liquidation of long-term assets and that banks serve customers on a first-come, first-served basis (Diamond and Dybvig, 1983).
This is not ordinary risk. For various important reasons, banking risk is extraordinary risk, because no bank, no matter where we are talking, can deal with unexpected risks that shift the economy against it. Which risks manifest themselves with an increase in defaults, that is, when the long term money doesn't come back at all.
Another view on this same problem is when the lending public perceive a problem, and decide to get their money out. That's called a run; no bank can deal with unexpected shifts in public perception, and all the lending public know this, so they run to get the money out. Which isn't there, because it is all lent out.
(If this is today, and you're in Ireland, read quietly...)
A third view on this is the legal definition of fraud: making deceptive statements, by entering into contracts that you know you cannot meet, with an intent to make a profit. By this view, a bank enters into a fraudulent contract with the demand depositor, because the bank knows (as does everyone else) that the bank cannot meet the demand contract for everyone, only for around 1-2% of the depositors.
Historically, however, banking was very valuable. Recall Mr Rothschild's goal of "facilitating the movement of money from Point A, where it is, to Point B, where it is needed." It was necessary for society because we simply had no other efficient way of getting small savings from the left to large and small projects on the right. Banking was essential for the rise of modern civilisation, or so suggests Mervyn King, in an earlier speech:
Writing in 1826, under the pseudonym of Malachi Malagrowther, [Sir Walter Scott] observed that:"Not only did the Banks dispersed throughout Scotland afford the means of bringing the country to an unexpected and almost marvellous degree of prosperity, but in no considerable instance, save one [the Ayr Bank], have their own over-speculating undertakings been the means of interrupting that prosperity".
Banking developed for a fairly long period, but as a matter of historical fact, it eventually settled on a structure known as central banking [1]. It's also worth mentioning that this historical development of central banking is the history of the Bank of England, and the Governor is therefore the custodian of that evolution.
Then, the Central Bank was the /lender of last resort/ who would stop the run.
Nevertheless, there are benefits to this maturity transformation - funds can be pooled allowing a greater proportion to be directed to long-term illiquid investments, and less held back to meet individual needs for liquidity. And from Diamond's and Dybvig's insights, flows an intellectual foundation for many of the policy structures that we have today - especially deposit insurance and Bagehot's time-honoured key principle of central banks acting as lender of last resort in a crisis.
Regulation and the structure we know today therefore rest on three columns:
- the function of lender of last resort, which itself is exclusively required by the improbable contract of deposits being lent at term,
- the public responsibility of public lending and public borrowing, and
- the public interest in providing the prosperity for all,
That which we know today as banking is really central banking. Later on, we find refinements such as the BIS and their capital ratio, the concept of big strong banks, national champions, coinage and issuance, interest rate targets, non-banking banking, best practices and stress testing, etc etc. All these followed in due course, often accompanied with a view of bigger, stronger, more diversified.
Which sets half of the scene for how the global financial crisis is slowly pushing us closer to our future. The other half in a future post, but in the meantime, dwell on this: Why is Mervyn King, as the Guv of the Old Lady of Threadneedle Street (a.k.a. Bank of England), spending time teaching us all about banking?
- What banking is. (Essential for predicting the end of finance as we know it.)
- What caused the financial crisis. (Laying bare the end of banking.)
- A small amount of Evidence. (In which, the end of banking and the rise of markets is suggested.)
- Mervyn King calls us to the Old Lady's deathbed?
[1] Slight handwaving dance here as we sidestep past Scotland, and let's head back to England. I'm being slightly innocent with the truth here, and ignoring the pointed reference to Scotland.
November 06, 2010
NSA loses the crown jewels, or, Law of Unintended Consequences meets Flights of Brittleness
Lynn points to a long story in The New Yorker that gives a well-written and strong story by Seymour M. Hersh on the origins of the current Cyber War propaganda push by the US Department of Defence. I and many others of the community called this a budgetary war, not a real threat, and it is good to see that there are many in the USA administration that have called "bull" on the Cyber War claim.
Picking up from page 7:
Why not ignore the privacy community and put cyber security on a war footing? Granting the military more access to private Internet communications, and to the Internet itself, may seem prudent to many in these days of international terrorism and growing American tensions with the Muslim world. But there are always unintended consequences of military activity—some that may take years to unravel.
Of particular note for those who subscribe to the "heavy" approach to secure systems, and poo-poo the doctrine of risk management in favour of absolute security, is an example of the Law of Unintended Consequences, and how complicated it is when you push the envelope at so many levels.
Ironically, the story of the EP-3E aircraft that was downed off the coast of China provides an example. The account, as relayed to me by a fully informed retired American diplomat, begins with the contested Presidential election between Vice-President Al Gore and George W. Bush the previous November. That fall, a routine military review concluded that certain reconnaissance flights off the eastern coast of the former Soviet Union—daily Air Force and Navy sorties flying out of bases in the Aleutian Islands—were redundant, and recommended that they be cut back.“Finally, on the eve of the 2000 election, the flights were released,” the former diplomat related. “But there was nobody around with any authority to make changes, and everyone was looking for a job.” The reality is that no military commander would unilaterally give up any mission. “So the system defaulted to the next target, which was China, and the surveillance flights there went from one every two weeks or so to something like one a day,” the former diplomat continued. By early December, “the Chinese were acting aggressively toward our now increased reconnaissance flights, and we complained to our military about their complaints. But there was no one with political authority in Washington to respond, or explain.” The Chinese would not have been told that the increase in American reconnaissance had little to do with anything other than the fact that inertia was driving day-to-day policy. There was no leadership in the Defense Department, as both Democrats and Republicans waited for the Supreme Court to decide the fate of the Presidency.
The predictable result was an increase in provocative behavior by Chinese fighter pilots who were assigned to monitor and shadow the reconnaissance flights. This evolved into a pattern of harassment in which a Chinese jet would maneuver a few dozen yards in front of the slow, plodding EP-3E, and suddenly blast on its afterburners, soaring away and leaving behind a shock wave that severely rocked the American aircraft. On April 1, 2001, the Chinese pilot miscalculated the distance between his plane and the American aircraft. It was a mistake with consequences for the American debate on cyber security that have yet to be fully reckoned.
For what went wrong after that, read the rest of the story!

October 05, 2010
Cryptographic Numerology - our number is up
Chit-chat around the coffeerooms of crypto-plumbers is disturbed by NIST's campaign to have all the CAs switch up to 2048 bit roots:
On 30/09/10 5:17 PM, Kevin W. Wall wrote:> Thor Lancelot Simon wrote:<...snip...>
> See below, which includes a handy pointer to the Microsoft and Mozilla policy statements "requiring" CAs to cease signing anything shorter than 2048 bits.> These certificates (the end-site ones) have lifetimes of about 3 years maximum. Who here thinks 1280 bit keys will be factored by 2014? *Sigh*.No one that I know of (unless the NSA folks are hiding their quantum computers from us :). But you can blame this one on NIST, not Microsoft or Mozilla. They are pushing the CAs to make this happen and I think 2014 is one of the important cutoff dates, such as the date that the CAs have to stop issuing certs with 1024-bit keys.I can dig up the NIST URL once I get back to work, assuming anyone actually cares.
The world of cryptology has always been plagued by numerology.
Not so much in the tearooms of the pure mathematicians, but all other areas: programming, management, provisioning, etc. It is I think a desperation in the un-endowed to understand something, anything of the topic.
E.g., I might have no clue how RSA works but I can understand that 2048 has to be twice as good as 1024, right? When I hear it is even better than twice, I'm overjoyed!
This desperation to be able to talk about it is partly due to having to be part of the business (write some code, buy a cert, make a security decision, sell a product) and partly a sense of helplessness when faced with apparently expert and confident advice. It's not an unfounded fear; experts use their familiarity with the concepts to also peddle other things which are frequently bogus or hopeful or self-serving, so the ignorance leads to bad choices being made.
Those that aren't in the know are powerless, and shown to be powerless.
When something simple comes along and fills that void people grasp onto them and won't let go. Like numbers. As long as they can compare 1024 to 2048, they have a safety blanket that allows them to ignore all the other words. As long as I can do my due diligence as a manager (ensure that all my keys are 2048) I'm golden. I've done my part, prove me wrong! Now do your part!
This is a very interesting problem [1]. Cryptographic numerology diverts attention from the difficult to the trivial. A similar effect happens with absolute security, which we might call "divine cryptography." Managers become obsessed with perfection in one thing, to the extent that they will ignore flaws in another thing. Also, standards, which we might call "beliefs cryptography" for their ability to construct a paper cathedral within which there is room for us all, and our flock, to pray safely inside.
We know divinity doesn't exist, but people demand it. We know that religions war all the time, and those within a religion will discriminate against others, to the loss of us all. We know all this, but we don't; cognitive dissonance makes us so much happier, it should be a drug.
It was into this desperate aching void that the seminal paper by Lenstra and Verheul stepped in to put a framework on the numbers [2]. On the surface, it solved the problem of cross-domain number comparison, e.g., 512 bit RSA compared to 256 bit AES, which had always confused the managers. And to be fair, this observation was a long time coming in the cryptographic world, too, which makes L&V's paper a milestone.
Cryptographic Numerology's star has been on the ascent ever since that paper: As well as solving the cipher-public-key-hash numeric comparison trap, numerology is now graced with academic respectability.
This made it irresistible to large institutions which are required to keep their facade of advice up. NIST like all the other agencies followed, but NIST has a couple of powerful forces on it. Firstly, NIST is slightly special, in ways that other agencies represented in keylength.com only wish to be special. NIST, as pushed by the NSA, is protecting primarily US government resources:
This document has been developed by the National Institute of Standards and Technology (NIST) in furtherance of its statutory responsibilities under the Federal Information Security Management Act (FISMA) of 2002, Public Law 107-347. NIST is responsible for developing standards and guidelines, including minimum requirements, for providing adequate information security for all agency operations and assets, but such standards and guidelines shall not apply to national security systems.
That's US not us. It's not even protecting USA industry. NIST is explicitly targetted by law to protect the various multitude of government agencies that make up the beast we know as the Government of the United States of America. That gives it unquestionable credibility.
And, as has been noticed a few times, Mars is on the ascendancy: *Cyberwarfare* is the second special force. Whatever one thinks of the mess called cyberwarfare (equity disaster, stuxnet, cryptographic astrology, etc) we can probably agree, if anyone bad is thinking in terms of cracking 1024 bit keys, then they'll be likely another nation-state interested in taking aim against the USG agencies. c.f., stuxnet, which is emerging as a state v. state adventure. USG, or one of USG's opposing states, are probably the leading place on the planet that would face a serious 1024 bit threat if one were to emerge.
Hence, NIST is plausibly right in imposing 2048-bit RSA keys into its security model. And they are not bad in the work they do, for their client [3]. Numerology and astrology are in alignment today, if your client is from Washington DC.
However, real or fantastical, this is a threat model that simply doesn't apply to the rest of the world. The sad sad fact is that NIST's threat model belongs to them, to US, not to us. We all adopting the NIST security model is like a Taurus following the advice in the Aries section of today's paper. It's not right, however wise it sounds. And if applied without thought, it may reduce our security not improve it:
Writes Thor:
> At 1024 bits, it is not. But you are looking
> at a factor of *9* increase in computational
> cost when you go immediately to 2048 bits. At
> that point, the bottleneck for many applications
> shifts, particularly those ...
> Also,...
> ...and suddenly...
>
> This too will hinder the deployment of "SSL everywhere",...
When US industry follows NIST, and when worldwide industry follows US industry, and when open source Internet follows industry, we have a classic text-book case of adopting someone else's threat, security and business models without knowing it.
Keep in mind, our threat model doesn't include crunching 1024s. At all, any time, nobody's ever bothered to crunch 512 in anger, against the commercial or private world. So we're pretty darn safe at 1024. But our threat model does include
*attacks on poor security user interfaces in online banking*
That's a clear and present danger. And one of the key, silent, killer causes of that is the sheer rarity of HTTPS. If we can move the industry to "HTTPS everywhere" then we can make a significant different. To our security.
On the other hand, we can shift to 2048, kill the move to "HTTPS everywhere", and save the US Government from losing sleep over the cyberwarfare it created for itself (c.f., the equity failure).
And that's what's going to happen. Cryptographic Numerology is on a roll, NIST's dice are loaded, our number is up. We have breached the law of unintended consequences, and we are going to be reducing the security of the Internet because of it. Thanks, NIST! Thanks, Mozilla, thanks, Microsoft.
[1] As well as this area, others have looked at how to make the bounty of cryptography more safely available to non-cognicenti. I especially push the aphorisms of Adi Shamir and Kerckhoffs. And, add my own meagre efforts in Hypotheses and Pareto-secure.
[2] For detailed work and references on Lenstra & Verheul's paper, see http://www.keylength.com/ which includes calculators of many of the various efforts. It's a good paper. They can't be criticised for it in the terms in this post, it's the law of unintended consequences again.
[3] Also, other work by NIST to standardise the PRNG (psuedo-random-number-generator) has to be applauded. The subtlety of what they have done is only becoming apparent after much argumentation: they've unravelled the unprovable entropy problem by unplugging it from the equation.
But they've gone a step further than the earlier leading work by Ferguson and Schneier and the various quiet cryptoplumbers, by turning the PRNG into a deterministic algorithm. Indeed, we can now see something special: NIST has turned the PRNG into a reverse-cycle message digest. Entropy is now the MD's document, and the psuedo-randomness is the cryptographically-secure hash that spills out of the algorithm.
Hey Presto! The PRNG is now the black box that provides the one-way expansion of the document. It's not the reverse-cycle air conditioning of the message digest that is exciting here, it's the fact that it is now a new class of algorithms. It can be specified, paramaterised, and most importantly for cryptographic algorithms, given test data to prove the coding is correct.
(I use the term reverse-cycle in the sense of air-conditioning. I should also stress that this work took several generations to get to where it is today; including private efforts by many programmers to make sense of PRNGs and entropy by creating various application designs, and a couple of papers by Ferguson and Schneier. But it is the black-boxification by NIST that took the critical step that I'm lauding today.)
October 04, 2010
62 Million Contracts are now no longer perfectable. Blame me?
In terms of value at risk, this has to be the winner in the monthly "most outrageous post across my desk" competition:
According to attorney Ellen Brown, author of "Web of Debt", a California bankruptcy court has followed what are now being called "landmark cases in other jurisdictions" in ruling that as many as 62 million mortgages may not be foreclosed on.The result could force the biggest banks into bankruptcy because having millions of homeowners get title to their homes with no further mortgage payment would decimate the asset portfolio. As pointed out in a San Francisco Chronicle article in 2007:
"The loans at issue dwarf the capital available at the largest U.S. banks combined, and investor lawsuits would raise stunning liability sufficient to cause even the largest U.S. banks to fail...."
This is an issue that I knew about. We tried to solve it. Blame me. Which makes it much harder to write about.
What's going on here? And why the chicken-little panic? How much truth is in this? Unfortunately, some:
The problem is that at the height of the real estate bubble, mortgages were sliced and diced into investment products -- securities -- that changed hands frequently.
Whoa! Stop right there! This was not a problem constrained to the height of the bubble, but a structural innovation that has dominated the last 30-40 years. Permit me to set the record straight:
The problem is thatat the height of the real estate bubblesince the invention of securitization in the 1970s or so, mortgageswereare sliced and diced into investment products -- securities -- that changedhands frequently.
If you wish to understand anything about the financial crisis, understand this:
securitization was a game-changer.
It was invented in the 1970s or so, and it set the scene for the massive boom we saw in the 2000s, and the massive collapse 2007-2009. Most confusing still, it's a good thing. Moving right along...
As a convenience for the mortgage industry, many of these mortgages were recorded electronically by a system called MERS (Mortgage Electronic Registration System).At issue was when Citibank tried to foreclose on a property in California, the homeowner's defense was that the actual deed was held by MERS and yet since MERS could not offer a homeowner signed documentation to a mortgage agreement, they could not prove ownership and since they couldn't prove ownership, the Deed of Trust could not be transferred and Citibank's note was therefore uncollectible.
Basically, throughout the securitisation process that created the global financial collapse, the issue that was staring us in the face was that the various transactions were not being perfected. That is, the contracts were not being adequately backed up according to the standards of the day. That standard is ultimately measured in court, or not as Citibank has discovered above.
I saw this when I designed my system, and set out to resolve it. The Ricardian Contract form solves the above problem, in part because it is signed, and in other part because it solves a lot of other issues lurking in the mess above. And, when Jim and I filed it into the SEC, they realised that it addressed their concerns, too.
But like this blog post, the problems brought about by securitization's success were put off until tomorrow. And tomorrow's tomorrow. And ... then came 2007. Some singularity somewhere caused systemic ripples throughout the system, which caused all contracts to shake and wobble. But it is important, nay, essential to realise: the fundamental structural feature was securitization. The systemic wobble event was not important. Keep your eye on the securitization ball as it rolls on unchallenged through the USA financial quagmire.
Now they've gone to court, and:
The California bankruptcy court concluded:"Since the claimant, Citibank, has not established that it is the owner of the promissory note secured by the trust deed, Citibank is unable to assert a claim for payment in this case."
So that's what is meant by a contract not being perfected. You can talk about it. You can sell it, slice & dice it, derive it and steal it. Start a boom, pay outrageous bonuses, watch the bubble burst. But you can't get a court to back all these things up. Which matters not one jot if everyone believes the boom will go forever...
Which leads to somewhat of an observation over modern finance... heck, all finance, and probably all business!
Finance is an inverted pyramid that sits on the apex of dispute resolution. Somewhere in a middle layer are contracts. Somewhere up top on the mesa are mortgages and loans and prosperity and the happiness of owning your own home. Down the bottom is dispute resolution.
If the apex collapses, don't be standing nearby with a camera.
September 28, 2010
Feel the dark side of Intellectual Property Rights. You know you want to....
The dark side of Intellectual Property is this: the structure of the market encourages theft, and more so than the more polite in society would predict. It's something that has really annoyed both sides of the debate; those who want to steal grumble about owners making it hard, while owners grumble that they need the help of their government for terrorising the first lot into financial dependency.
Two of the most abject victims of wikinomics are the newspaper and music industries. Since 2000, 72 American newspapers have folded. Circulation has fallen by a quarter since 2007. By some measures the music industry is doing even worse: 95% of all music downloads are illegal and the industry that brought the world Elvis and the Beatles is reviled by the young. Why buy newspapers when you can get up-to-the-minute news on the web? Why buy the latest Eminem CD when you can watch him on YouTube for free? Or, as a teenager might put it: what’s a CD?
Now, if it does that, if IP is structured that way, we can ask a number of searching questions. Was that what we intended? Is this a good thing or a bad thing? Can we improve it?
An interesting case of a company called Zynga (mentioned in last week's story) seems to make the case. First off, theft seems to be part & parcel of intellectual property:
In the latest SF Weekly cover story, multiple former employees of Zynga, speaking on condition that their names not be published so that they could discuss their work experiences candidly, tell us that studying and copying rivals' game concepts was business as usual. One senior employee who has since left the company describes a meeting where Zynga CEO and founder Mark Pincus said, "I don't fucking want innovation. You're not smarter than your competitor. Just copy what they do and do it until you get their numbers."
There's two ways of looking at this. Maybe Pincus has perfected a novel use of the perfect market hypothesis in innovation? Outstanding! In brief, the perfect market hypothesis as applied would say that the market has already acquired all the information, hence there is no point in trying to beat it, hence we should simply acquire the market.
Or maybe he has developed a new theory of creative destruction in innovation, following Schumpeter? It's certainly not my grandmother's definition of innovation, and some would call it by worse names (Guernica springs to mind, if I can bring in an IP link).
 |
| The Creative Destruction Theory of Innovation |
On the other hand, the artists have a different take on the topic:
One of the more common complaints among former Zynga employees is about Pincus' distaste for original game design and indifference to his company's applications, beyond their ability to make money. "The biggest problem I had with him was that he didn't know or care about the games being good -- the bottom line was the only concern," a former game designer says. "While I'm all for games making money, I like to think there's some quality there."
Above, the "former game designer" suggests that his view of "goodness" should override the market's view, as expressed by the bottom line. The clear statement of his boss is the other way around.
Such a disdain for the message of the users is somewhat typical of fields of artistic endeavour where artists create their own shared, internal sense of goodness, and seek to avoid the market's view as insufficiently enlightening or overly opaque (etc). From where I sit, this is a view that artists can hold in a greenfield design where there simply isn't a market, and/or where the artist is also the investor.
But that latter point is troubling. Innovators are like artists, as a whole. One could suggest that innovators won't monetarise, because they'll be focussed on "goodness" and we might well be wasting our time supporting them to the extent of actually listening to them (I speak as an innovator, but prefer you not to mention it today). One could also suggest that they can't monetarise because that trap makes them perpetually too poor to invest.
What then happens if the innovatory process is really stacked in this direction? What happens if most innovators can't monetarise? How do we support a rationale whereby we as society should continue to support innovators with intellectual property rights at all? Why patents, brands, ideas, copyright, etc?
 One answer is so they can recover at least something after it is appropriated:
One answer is so they can recover at least something after it is appropriated:
Another former employee recalls a meeting where Zynga workers discussed a strategy for copying a gangster game, Mob Wars, and creating Zynga's own Mafia Wars application. "I was around meetings where things like that were being discussed, and the ramifications of things like that were being discussed -- the fact that they'd probably be sued by the people who designed the game," he says. "And the thought was, 'Well, that's fine, we'll settle.' Our case wasn't really defensible." (Mob Wars' creator, David Maestri, proprietor of Psycho Monkey, did sue Zynga for copyright infringement. The case was settled for an undisclosed amount.)
So let's stop doing upfront licensing and sales of IPR. The point being that as long as the innovator keeps innovating, and product gets to market, it matters not to everyone else whether he's paid for it before or after its use. Everyone wins.
Just not the way we thought. Not what the brochure said. The goal of intellectual property rights then might not be to save the rights, but to lose them. And, the more you lose, the better, as the the better the theft, the more you can claim back.
(On the search for a good aporism here! Comments welcome.)
If that were so, if we were to assume IP theft as a goal of public policy, we'd be switching our emphasis to making IP easier to prove and recover in litigation. Registrations might deal with the first part (but are arguably too too cumbersome and expensive).
What deals with the second part? How do we improve the rate of recovery in IP litigation? By all accounts, the victim in any litigation is typically the small guy, so the innovator has it stacked against him or her there, too.
September 20, 2010
The Facebook model succeeds. Next steps: copying, responding, losing.
Along the lines of previous reporting, it seems that Facebook has won its spurs. Eliot van Buskirk reports from Wired:
Facebook is making a play to become the dominant player in virtual currency — the funny money you use to everything from digital magazines to Farmville turnips. It’s already a billion-dollar business in which Facebook, the world’s largest social network, will face stiff competition from other behemoths like Apple, Google and PayPal.Facebook already has a big advantage over those companies: a virtual currency, Facebook Credits, that works across different apps rather than being tied to one specific app or another.
...
Sales of virtual goods are projected to reach $1.6 billion this year in the United States alone, according to an Inside Network report. About half of that will be spent on social games, and the majority of that in Facebook games such as Farmville.Facebook claims 30 percent of revenue when people buy these credits — the same cut Apple and Google slice off when users buy virtual goods within their apps — but is already the number one app across all smartphone platforms according to Nielsen.
This means that Facebook will earn its investors the return demanded. Because it has an active market place of many thousands of suppliers, it has gained control of the monetisation within its world, and it takes significant margin of that activity, this means that Facebook has cracked the revenue model in a way that few others have.
However, other big Internet players will notice the success, will revisit their flawed models, and will move to adopt the one that Facebook has worked out for them.
Apple has yet to create a cross-app virtual currency, but offers other virtual goods — iTunes songs, for instance — through pre-paid gift cards. Users may start wondering why they can’t use iTunes credits to purchase goods within iPhone apps like Farmville — and vice versa. And because so much money will be spent in this way, this problem could become a source of annoyance for users and app developers alike.
This is of interest to financial cryptography players as it establishes the basic business rules to play in this market. It's also of interest to regulators and incumbents (read: banks) who want to squash the market:
The U.S. has strict laws against creating new forms of currency, but there’s enough wiggle room for Apple (iTunes), Google (Checkout, Android), Paypal, individual developers, and others to join Facebook in creating virtual currencies that work in apps across their respective platforms, even those beyond games — music, movies, productivity apps, and so on. And that’s when things could get tricky, in the huge and expanding market for virtual goods.
Unfortunately the signs auger badly for them. As frequently commented here in this blog, the European Union tried to beat this one back in the 1990s and succeeded so well it lost. Meanwhile, the USA supported, and partly won with Paypal, but then reversed course and is now set to lose. And, unless the banks wave the get-out-of-jail-free card, they won't be getting as much attention as before. Curiously, their favourite "save me" card might be more justified this time (you know your banking, right?) but it's already been spent, and the results weren't good. Patience should be thin.
Perhaps it is time to roll out Goodhart's law as this blog's aphorism ad nauseum? Meanwhile, bringing the two battles together, this means that while the B-list is moving to copying, the A-list now starts its regulatory response phase.
Good luck on that immense strategic battle! Interesting times ahead.
September 14, 2010
Internet Intellectuals, Media Security Reporting, and other explorations in the market for silver bullets
Evgeny Morozov and a whole lot of other media-savvy people have a silver bullets moment when analysing Haystack, a hopeful attempt at bypassing censorship for citizens in countries like Iran. The software was released, lauded by the press, and got an export licence from the USA government.
By all media-validated expectations, Haystack should have been good to go on and wreak merry havoc against Iranian censorship. Until Jake Appelbaum and his team took a poke at it and discovered it permitted tracking of the dissidents. Then the media flipped and attacked. Familiar story, right?
I want to know why the media was so quick to push this tool. I want answers.
Morozov asks, in various ways, what went wrong? Here's a breakdown of what I think are his essential points, and my answers.
Why didn't the security community come in and comment? That's easy. The security community is mostly a commercially minded group of people who work for food. It includes a small adjunct rabble who make a lot of noise breaking things. Not for money, but for fun & media attention. Allegedly, Appelbaum said:
Haystack is the worst piece of software I have ever had the displeasure of ripping apart. Charlatans exposed. Media inquiries welcome.
If Jake's deep sarcasm isn't slapping you on the forehead, here it is in plain writing: we break the tools because it's cool, because the media write about it, and because it's fun. But the presence of the crowd-pleasing infosoc vigilantes doesn't mean that anyone is going to fix the broken efforts. Or provide good advice. No, that costs money:
UPDATE #1: I just received information that "Haystack has been turned off as of ~19:00 PST, Sept 10/2010", with Austin Heap agreeing that "Haystack will not be run again until there is a solid published threat model, a solid peer reviewed design, and a real security review of the Haystack implementation."
Look at for wider example, the fabled OpenPGP encryption system. In its long history, the major providers emerged as PGP Inc and GnuPG. Both of these groups had substantial funding or business reasons to carry on, to build, at one time or another. Which meant that their programmers could eat. As an alternate case in point, my own efforts in Cryptix OpenPGP went up and down to the tune of money and business need, not to the tune of crackers or bugs or media attention. The hoi polloi took their best shot at these products, and a few cracks were found, but the real story is how the builders built, not how the cracks were found.
So in essence we have in the security community an asymmetric relationship with the world. We are happy to break your product for our fun; but we won't be fixing it. For that, put your money on the table. If you want to change that, get the media to make building secure apps more sexy than breaking them. Simple, but the opposite of how the Haystack story went.
Next. Why did the State Department endorse Haystack with a license to export? The best way of seeing this is a case of "the enemy of my enemy is my friend." It has been evident since the start of the Bush administration (1990?) that the US government has a policy of taunting the Iranians when and how they can. So, of course, the Haystack product fit with the policy.
One could look at the technical merits of the product, and come to some sort of hopeful case. The license is not an endorsement of any strong security, it's actually the reverse. It is an endorsement that the security isn't strong enough to worry the USA. There is one further aspect: the exporting organization has a way to avoid any hard discussions: simply open source the product.
From that perspective, the State department has no benefit from not issuing the license, and every reason to issue it.
What is probably more interesting is to ask: what do we do about a product that puts Iranian lives at risk? The easy answer is to not put lives at risk. Let's not do that, it would seem undeniable to think otherwise, right?
Wrong. It is wrong, at three levels.
Firstly, this is clearly against the policy and practice of the various governments in this space, who routinely put foreign lives at risk in order to pursue local objectives. (We already established some alignment there, above.) According to the count of lives next-door in Iraqi, we're seemingly running at a 100:1 ratio, order of magnitude, of putting their lives at risk, compared to our lives. We might talk about "undeniable value of human life" but the facts make that a difficult assumption.
We could simply say that we the Internet, we the Intellectuals shouldn't adopt the low tactics and cavalier attitude of our governments. We are better than them!
Except, that's unfounded as well. Secondly: Consider the OpenPGP community: this community distributed encrypted software that was frequently used by the same target audience as Haystack. I know because I was part of that community (proudly) and I heard some of the stories.
Stories of success, and stories of failure. People used OpenPGP product and people disappeared and people died.
So why this apparent contradiction? Why is OpenPGP so secure, but people still die, whereas we don't accept Haystack which is insecure and might lead to deaths? The answer is risk.
All security is risk-based. Adi Shamir put it best:
- Absolutely secure systems do not exist.
- To halve your vulnerability, you have to double your expenditure.
- Cryptography is typically bypassed, not penetrated.
Security is relative to everything, and the "black box" called Haystack or OpenPGP is only a part of that context. The security of Haystack may be sufficient in one context, OpenPGP may be hopeless in another context.
And it takes quite a lot of experience, and fairly difficult analysis of the overall context to establish whether the risk of a tool is worth taking. For example, we deep in the security community know that all OpenPGP products can be utterly defeated with equipment worth about five bucks.
Which should make the point: we can't easily say that the use of Haystack will be absolutely safer or less safe. We can only take on risk, or expose others to risk through our efforts, which is why Haystack may well have deserved the Entrepreneur award: the team went where others were too afraid to go, the true spirit of an Entrepreneur.
Finally, thirdly, and to close on risk, we must always consider the null option: we do nothing, therefore we cannot put lives at risk. Right?
No, wrong again. The Null option, do nothing, doesn't work either. If we do not supply OpenPGP secure communications to the Iranian dissidents (or Haystack or whoever, or whatever) then they will use less secure techniques. Because of our actions to limit the availability of secure tools, our actions of denial will increase risk for some others.
That's because we can assume that the dissidents will diss, and we can either help them by providing better tools, or stand idly by while they die for want of better tools. We have to negate the easy implication of "causality & responsibility," there is no simple binary responsibility here; people die if we act, and they die if don't act. Our risk might go down if we do nothing, their's may go up.
What in summary do we have? How to answer the blogsphere angst of "how did this happen to us? Why can't you fix it? The government must do something?"
That's leading to the final question. Why is it that this is so hard, when it seems so easy? Who can we blame for the hype? Why have the expectations of the media been so truly flipped over in the blink of an eye?
The security market is a market in silver bullets.
In other words, in a silver bullets market, there is an absence of well-agreed solid practice & theory. There are lots of producers, and there are lots of products, and lots of theories and lots of practices. But, within the security community, these theories are at war with one-another, and for every apparently sustainable argument, you'll be able to find someone to trash it. And the data to prove it trash-worthy.
In this sense, security is about as well understood as freedom. Just to give a case in point: this article quotes the misnamed and misunderstood Kerckhoffs' Principle:
"Although we sincerely wish we could release Haystack under a free software license, revealing the source code at this time would only aide the authorities in blocking Haystack."That’s a statement in direct conflict with Kerckhoffs' Principle, a cornerstone of security philosophy. The Principle states that the only security worth doing is that which remains secure even if your enemy knows the totality of how it works. Haystack’s refusal to publish the software is an enormous red-flag to security practitioners, suggesting strongly that some aspect of the security it provides somehow hinges on a parlour trick that - once known - becomes useless or potentially hazardous.
This is a reference to Kerckhoffs 6 principles of secure communications which fails for a too-simple reading of one of them. It's a common problem.
Kerckhoffs' second principle states "It must not be required to be secret, and it must be able to fall into the hands of the enemy without inconvenience;" Unfortunately, this is not strictly true. K2 remains a principle and not a law, and yes, when people talk about Kerckhoffs' law, they are wrong.
It's perhaps easier to show this by a hypothetical: if for example Haystack had been built as a Skype plugin, or had used RIM's Blackberry enterprise layer, etc, would we then be able to rely on it? Yes, remembering our risk discussion, because it would be better than the alternate. But these things are secret, breaking K2. Or for more realworld example, if the NSA were to mount Haystack, now with new-improved-secret-crypto!, do you think they would be publishing the source?
Why then does K2 work for us, or as Shannon's maxim, "the enemy knows the system" ? Because revealing the internal design generally makes it much harder to hide behind incompetence. And the silver bullet aspect of the entire security world makes it almost a given that an incompetent result is ensured. In this, Haystack has proved the general incompetence principle of secrecy: that a secret system is likely to hide a great deal of incompetence.
But, that can still be a good risk to take. It all depends. There is no absolute security, so where you draw the line, depends. On everything. Now perhaps we see why Adi's words above, and Kerckhoffs principles, *all of them*, have sustained over time. Knowing the Principles and Hypotheses of security engineering is a given, that's the job of a protocol engineer. That which separates out engineering from art is knowing when to breach a hypothesis.
All this by way of showing that one man's security wisdom might be another man's folly, and in such a world, a silver bullet is a seemingly valuable thing.
Should we support Haystack, knowing all the above? Yes. But maybe we needed hindsight to see the reasons, laid out more clearly. Look at the public lambasting that the participants have had!
Now, imagine you want to do a better job. Feel scared and queasy? Yup, in the climate generated by the media, the security folk and the political agenda, today, there are relatively few incentives to take on this task. Instead, there are much greater incentives to build a social network and really monetarise the potential for massive abuses in privacy than to muck around with democracy and freedom of speech and all that.
Secondly, consider the open security community. We will break it for you, but we won't help you fix it. Like the media, our attention is slanted dramatically against you.
So, in practice, it should be no surprise that groups such as the Haystack team are few and far between. It's almost as if we have the devil's choice: a dodgy system or no system at all. A good security model is not a cheap option, it's not a practical option, nor an economic option. Security will kill your dreams, the structure of the industry makes it so.
If your objective is to help freedom of speech, then delivering crypto systems will help, even ones with known leaks. That's assuming they will do some good, in the balance. There is one final advantage, it is also a lot easier to fix broken tools than to fix absent tools. In contrast to accepted wisdom, writing the solid security model up front, with no customer base, is a fool's errand.
September 01, 2010
Innovation: a word, a dream or a nightmare?
It is fairly normal to hear people talk about innovation, but it doesn't take much experience to realise there is a gulf between the reality and the buzzword. Innovation is not something we can bring to the company just by talking about it. Here's some cold water poured on popular notions by Govindarajan and Trimble (G&T):
The fashion these days is to focus on the supply side of innovation: for example, by encouraging everyone to think big thoughts. 3M, the maker of Post-it notes, ...
Fashion in innovation thinking is an oxymoron if ever I saw one! When did 3M invent Post-it notes? No matter, let's carry on:
...expects its workers to spend 15% of their time on their own projects. Google expects them to spend 20%. This approach is attractively democratic: by giving everyone a chance to innovate, it makes everyone feel special. Or so the theory goes. G&T are ready with the cold water. The let-them-loose approach spreads resources thinly and indiscriminately. Companies dissolve into a thousand small initiatives rather than focusing on a few big problems. It also produces far too many ideas: managers have to spend weeks sorting through the chaff to find a few grains of wheat.
I've seen the 20% idea in operation, and it doesn't work. Calling it democratic is a good approximation, so there is some value to it in a tight bureaucracy seeking to "empower" its people. But innovation-driving it isn't, and doing it in a technology company like google reveals a profound misunderstanding of the techie's human psyche. I'd even suggest that the approach quite possibly hides the sources of true innovation.
G&T say that you need to start by recognising that innovation is unnatural.
Hallelujah! Now, ask your boss whether she'd like something unnatural to happen to her this week ... and we'd be getting close to why that it isn't going to happen.
Established businesses are built for efficiency, which depends on predictability and repeatability—on breaking tasks down into their component parts and holding employees accountable for hitting their targets. But innovation is by definition unpredictable and uncertain. Bosses may sing a pretty song about innovation being the future. But in practice the heads of operational units will favour the known over the unknown.
Right. But it is also not just companies that are obsessed with these things. People are scared, scared for their jobs. Mundane is safe, innovation gets you fired, or if you are lucky the credit will be lost to others. Far safer to talk the buzzwords, only.
So how to to turn big corporations or departments into innovation factories? Well, it's probably unreasonable because we are likely in that statistical impossibility space. Either people will talk about it, and not do it (for fear of their jobs), or people will do it and lose their jobs. So every lesson will be an anti-innovation lesson, and any accidental slippage into innovation will be dismissed as a statistical outlier.
Annecdote: I recall presenting on the fundamentals of why innovation is impossible in banking, to a big british bank's Head of Innovation. Of course, he argued I was wrong. But after he left, two of his employees told me that while he talked the talk very well, he did everything possible to avoid innovation. He was the head of Innovatory Capture & Suppression, and he served the bank well.
The only way to crack the anti-innovatory structure of business is to change the rules.
Many would-be innovators deal with the trade-off between efficiency and innovation by rejecting traditional management entirely. They repeat mantras about “breaking all the rules” and “asking for forgiveness rather than permission”. They set up skunk works (small, autonomous units with a remit to innovate) and mock the boring corporate types who write their pay-cheques. But again this is counter-productive.
However, not the rules written on paper, but the meta-rules of the operation! (People who talk about breaking the rules are generally using this as a cover to get their own way.)
G&T argue that companies need to build dedicated innovation machines. These machines need to be free to recruit people from outside (since big companies tend to attract company men rather than rule-breakers). They also need to be free from some of the measures that prevail in the rest of the company.
Right! But! That gets us back to the same dilemma:
But they must avoid becoming skunk works. They need to be integrated with the rest of the company—they must share some staff, for example, and they must tap into the wider company’s resources as they turn ideas into products. And they must be tightly managed according to customised rather than generic rules. For example, they should be held accountable for their ability to learn from mistakes rather than for their ability to hit their budgets.
We can talk about it but we won't actually do it. Or, what we do will not be it. Or what we do will be captured or dispersed, so not learnt.
Innovation in big corporates, as a turnaround, /has been done/. But the cases are relatively rare, and the conditions are hard to duplicate. Innovation happens in the startup sector, and the word innovation is never used there, it's just business, or survival, or the founder's omniscience. That is, the natural state of the startup is to write the meta-rules, so it is totally natural that the unnatural takes place.
Which perhaps confirms that the only successful strategy for innovation a large company has is to buy out small successful startups ... Sorry about that!
August 20, 2010
Niall Ferguson - Empires on the Edge of Chaos
 Niall Ferguson spoke a few weeks ago at something called the CIS, supposedly a right-wing thinktank in Australia. He's well known for his Ascent of Money series, which is the thing you buy on DVD if you want to tell your Mum about economics and the way the world works. He's also that rarest breed in economics - he's not an economist at all, he's a historian.
Niall Ferguson spoke a few weeks ago at something called the CIS, supposedly a right-wing thinktank in Australia. He's well known for his Ascent of Money series, which is the thing you buy on DVD if you want to tell your Mum about economics and the way the world works. He's also that rarest breed in economics - he's not an economist at all, he's a historian.
His speech is here. It's a very big video download (26Mb), it seems, so I'll post this *after* my download else I'll never see it. Also, see it on vimeo directly which might work better.
Other writings on the same theme can be found in An Empire at Risk and America, the Fragile Empire. But frankly, the words in print don't do justice. It's a great presentation, both in terms of the picture it draws, the evidence assembled, and how well it was presented.
(The introduction of around 8-9 minutes is very skippable...) (Slightly edited to incorporate new links.)
August 13, 2010
memes in infosec III - Perimiter defences against the unknown, invisible, unmeasurable...
Clive Robinson writes in comments, and I can do little more than post it as a special Friday 13th edition. Good luck:
The problem of spend too little, get hurt, spend too much, waste resources unprofitably is older even than money.
It is the basic problem with all defensive behaviour. If you go back to the times of the "hunter-gather" the gathers had an issue (as do all prey): if you put all your resources into gathering then you will not see the predator stalking you. If all gathers spend their time looking for predators, then no gathering will occur and they will starve. Thus there is some trade-off towards an optimum value of lookouts for any given predator, terrain or group size of gathers.
Interestingly the optimum is usually less than four, for all predators and group sizes that fit within a moderate shout range in open terrain. For larger groups, it is usually the number of watchers that will go around the edge of the group and remain within moderate shout range in open terrain. In closed terrain it depends not on shout distance but visual distance. Which is why you get very large groups (antelope, etc) in the open savanna, but much smaller-sized groups (monkeys) in closed areas such as scrub and forest, etc.
Now the important thing to notice is that the number of watchers goes up at a very very small fraction of the number of gathers.
All of which is why traditionally we have looked at perimeter defence. However it has a "physical assumption" underlying it which is "locality" which further assumes "visibility". In a network environment with 0-day attacks, everywhere that is connected is local. Thus perimeter defence only works with visible attack vectors (i.e. those that are known or exhibit behaviour that is sufficiently different from the norm to be detected).
Thus there are three basic classes of attack vector,
- Known (i.e. known knowns).
- Visible (i.e. unknown knowns).
- Unknown (unknown unknowns).
Within reason the Known Class can be correctly defended against with up-to-date Anti-malware, without effecting the day-to-day activities of a host (within the network perimeter). A simple measurand for this class is the number of attacks stopped.
Again within reason, the Visible Class may be mitigated against using various probabilistic techniques. This however may well involve considerable delay (with respect to attack time, not human time) and require "isolation" or "quarantining" hosts within the network perimeter which will usually negatively impact day-to-day activities of a host (within the perimeter). A simple measurand for this class is the number of events detected, a more difficult but more useful measurand is to distinguish between the "positives" (i.e. those that are seen and are proven to be attacks, those that are seen and assumed to be attacks and those that are seen and proven to be false alarms).
At first sight the Unknown Class cannot be defended against because there is "nothing to see" thus detect. Therefore the only perimeter possible is a "perfect air gap" which in current times makes a significant impact on some day to day activities of the hosts on such networks. Because there is "nothing to see" it could be argued that there is no measurand.
Setting the resource line should place it between the Visible and Unknown classes, but in most cases, resource restrictions actually puts it between the Known and Visible classes.
The question then arises, is the Unknown class really unknown?
The answer is probabilistic or a "Qualified No".
If an attack does not copy any host data and does not modify any host or its data and does not impact a hosts day-to-day activities, then its impact inside the perimeter is negligibly small at that point in time (it might for arguments sake use spare CPU cycles and memory to crack password files from another location).
Such activity might be very difficult but not impossible to spot. Currently, with monolithic executable files and current operating systems, it is effectively not possible to spot.
However there is a way that this problem can be resolved but it requires a different computing platform methodology both in hardware and software.
At which point, Clive stopped, leaving us dangling :)
August 11, 2010
Hacking the Apple, when where how... and whether we care why?
 One of the things that has been pretty much standard in infosec is that the risks earnt (costs incurred!) from owning a Mac have been dramatically lower. I do it, and save, and so do a lot of my peers & friends. I don't collect stats, but here's a comment from Dan Geer from 2005:
One of the things that has been pretty much standard in infosec is that the risks earnt (costs incurred!) from owning a Mac have been dramatically lower. I do it, and save, and so do a lot of my peers & friends. I don't collect stats, but here's a comment from Dan Geer from 2005:
Amongst the cognoscenti, you can see this: at security conferences of all sorts you’ll find perhaps 30% of the assembled laptops are Mac OS X, and of the remaining Intel boxes, perhaps 50% (or 35% overall) are Linux variants. In other words, while security conferences are bad places to use a password in the clear monoculture on the back of the envelope over a wireless channel, there is approximately zero chance of cascade failure amongst the participants.
I recommend it on the blog front page as the number 1 security tip of all:
Why this is the case is of course a really interesting question. Is it because Macs are inherently more secure, in themselves? The answer seems to be No, not in themselves. We've seen enough evidence to suggest, at an anecdotal level, that when put into a fair fight, the Macs don't do any better than the competition. (Sometimes they do worse, and the competition ensures those results are broadcast widely :)
However it is still the case that the while the security in the Macs aren't great, the result for the user is better -- the costs resulting from breaches, installs, virus slow-downs, etc, remain lower [1]. Which would imply the threats are lower, recalling the old mantra of:
Business model ⇒ threat model ⇒ security model
Now, why is the threat (model) lower? It isn't because the attackers are fans. They generally want money, and money is neutral.
One theory that might explain it is the notion of monoculture.
This idea was captured a while back by Dan Geer and friends in a paper that claimed that the notion of Microsoft's dominance threated the national security of the USA. It certainly threatened someone, as Dan lost his job the day the paper was released [2].
In brief, monoculture argues that when one platform gains an ascendency to dominate the market, then we enter a situation of particular vulnerability to that platform. It becomes efficient for all economically-motivated attackers to concentrate their efforts on that one dominant platform and ignore the rest.
In a sense, this is an application of the Religion v. Darwin argument to computer security. Darwin argued that diversity was good for the species as a whole, because singular threats would wipe out singular species. The monoculture critique can also be seen as analogous to Capitalism v. Communism, where the former advances through creative destruction, and the latter stagnates through despotic ignorance.
 A lot of us (including me) looked at the monoculture argument and thought it ... simplistic and hopeful. Yet, the idea hangs on ... so the question shifts for us slower skeptics to how to prove it [3]?
A lot of us (including me) looked at the monoculture argument and thought it ... simplistic and hopeful. Yet, the idea hangs on ... so the question shifts for us slower skeptics to how to prove it [3]?
Apple is quietly wrestling with a security conundrum. How the company handles it could dictate the pace at which cybercriminals accelerate attacks on iPhones and iPads.Apple is hustling to issue a patch for a milestone security flaw that makes it possible to remotely hack - or jailbreak - iOS, the operating system for iPhones, iPads and iPod Touch.
Apple's new problem is perhaps early signs of good evidence that the theory is good. Here we have Apple struggling with hacks on its mobile platform (iPads, iPods, iPhones) and facing a threat which it seemingly hasn't faced on the Macs [4].
The differentiating factor -- other than the tech stuff -- is that Apple is leading in the mobile market.
IPhones, in particular, have become a pop culture icon in the U.S., and now the iPad has grabbed the spotlight. "The more popular these devices become, the more likely they are to get the attention of attackers," says Joshua Talbot, intelligence manager at Symantec Security Response.
Not dominating like Microsoft used to enjoy, but presenting enough of a nose above the pulpit to get a shot taken. Meanwhile, Macs remain stubbornly stuck at a reported 5% of market share in the computer field, regardless of the security advice [5]. And nothing much happens to them.
If market leadership continues to accrue to Apple in the iP* mobile sector, as the market expect it does, and if security woes continue as well, I'd count that as good evidence [6].
[1] #1 security tip remains good: buy a Mac, not because of the security but because of the threats. Smart users don't care so much why, they just want to benefit this year, this decade, while they can.
[2] Perhaps because Dan lost his job, he gets fuller attention. The full cite would be like: Daniel Geer, Rebecca Bace, Peter Gutmann, Perry Metzger, Charles P. Pfleeger, John S. Quarterman, Bruce Schneier, "CyberInsecurity: The Cost of Monopoly How the Dominance of Microsoft's Products Poses a Risk to Security." Preserved by the inestimable cryptome.org, a forerunner of the now infamous wikileaks.org.
[3] Proof in the sense of scientific method is not possible, because we can't run the experiment. This is economics, not science, we can't run the experiment like real scientists. What we have to do is perhaps psuedo-scientific-method; we predict, we wait, and we observe.
[4] On the other hand, maybe the party is about to end for Macs. News just in:
Security vendor M86 Security says it's discovered that a U.K.-based bank has suffered almost $900,000 (675,000 Euros) in fraudulent bank-funds transfers due to the ZeuS Trojan malware that has been targeting the institution.Bradley Anstis, vice president of technology strategy at M86 Security, said the security firm uncovered the situation in late July while tracking how one ZeuS botnet had been specifically going after the U.K.-based bank and its customers. The botnet included a few hundred thousand PCs and even about 3,000 Apple Macs, and managed to steal funds from about 3,000 customer accounts through unauthorized transfers equivalent to roughly $892,755.
Ouch!
[4] I don't believe the 5% market share claim ... I harbour a suspicion that this is some very cunning PR trick in under-reporting by Apple, so as to fly below the radar. If so, I think it's well past its sell-by date since Apple reached the same market cap as Microsoft...
[5] What is curious is that I'll bet most of Wall Street, and practically all of government, notwithstanding the "national security" argument, continue to keep clear of Macs. For those of us who know the trick, this is good. It is good for our security nation if the governments do not invest in Macs, and keep the monoculture effect positive. Perverse, but who am I to argue with the wisdom in cyber-security circles?
August 05, 2010
Are we spending too little on security? Or are we spending too much??
Luther Martin asks this open question:
Ian,
I have a quick question for you based on some recent discussions. Here's the background.
The first was with a former co-worker who works for the VC division of a large commercial bank. He tells me that his bank really isn't interested in investing in security companies. Why? Apparently foreach $100 of credit card transactions there's about $4 of loss due to bad debt and about only $0.10 of loss due to fraud. So if you're making investments, it's clear where you should put your money.
Next, I was talking with a guy who runs a large credit card processing business. He was complaining about having to spend an extra $6 million on fraud reduction while his annual losses due to fraud are only about $250K.
Finally, I was also talking to some people from a government agency who were proud of the fact that they had reduced losses due to security incidents in their division by $2 million last year. The only problem is that they actually spent $10 million to do this.
So the question is this: are we not spending enough on security or are we spending too much, but on the wrong things?
Luther
August 01, 2010
memes in infosec I - Eve and Mallory are missing, presumed dead
Things I've seen that are encouraging. Bruce Schneier in Q&A:
Q: We've also seen Secure Sockets Layer (SSL) come under attack, and some experts are saying it is useless. Do you agree?A: I'm not convinced that SSL has a problem. After all, you don't have to use it. If I log-on to Amazon without SSL the company will still take my money. The problem SSL solves is the man-in-the-middle attack with someone eavesdropping on the line. But I'm not convinced that's the most serious problem. If someone wants your financial data they'll hack the server holding it, rather than deal with SSL.
Right. The essence is that SSL solves the "easy" part of the problem, and leaves open the biggest part. Before the proponents of SSL say, "not our problem," remember that AADS did solve it, as did SOX and a whole bunch of other things. It's called end-to-end, and is well known as being the only worthwhile security. Indeed, I'd say it was simply responsible engineering, except for the fact that it isn't widely practiced.
OK, so this is old news, from around March, but it is worth declaring sanity:
Q: But doesn't SSL give consumers confidence to shop online, and thus spur e-commerce?A: Well up to a point, but if you wanted to give consumers confidence you could just put a big red button on the site saying 'You're safe'. SSL doesn't matter. It's all in the database. We've got the threat the wrong way round. It's not someone eavesdropping on Eve that's the problem, it's someone hacking Eve's endpoint.
Which is to say, if you are going to do anything to fix the problem, you have to look at the end-points. The only time you should look at the protocol, and the certificates, is how well they are protecting the end-points. Meanwhile, the SSL field continues to be one for security researchers to make headlines over. It's BlackHat time again:
"The point is that SSL just doesn't do what people think it does," says Hansen, an security researcher with SecTheory who often goes by the name RSnake. Hansen split his dumptruck of Web-browsing bugs into three categories of severity: About half are low-level threats, 10 or so are medium, and two are critical. One example...
Many observers in the security world have known this for a while, and everyone else has felt increasingly frustrated and despondent about the promise:
There has been speculation that an organization with sufficient power would be able to get a valid certificate from one of the 170+ certificate authorities (CAs) that are installed by default in the typical browser and could then avoid this alert ....But how many CAs does the average Internet user actually need? Fourteen! Let me explain. For the past two weeks I have been using Firefox on Windows with a reduced set of CAs. I disabled ALL of them in the browser and re-enabled them one by one as necessary during my normal usage....
On the one hand, SSL is the brand of security. On the other hand, it isn't the delivery of security; it simply isn't deployed in secure browsing to provide the user security that was advertised: you are on the site you think you are on. Only as we moved from a benign world to a fraud world, around 2003-2005, this has this been shown to matter. Bruce goes on:
Q: So is encryption the wrong approach to take?A: This kind of issue isn't an authentication problem, it's a data problem. People are recognising this now, and seeing that encryption may not be the answer. We took a World War II mindset to the internet and it doesn't work that well. We thought encryption would be the answer, but it wasn't. It doesn't solve the problem of someone looking over your shoulder to steal your data.
Indeed. Note that comment about the World War II mindset. It is the case that the entire 1990s generation of security engineers were taught from the military text book. The military assumes its nodes -- its soldiers, its computers -- are safe. And, it so happens, that when armies fight armies, they do real-life active MITMs against each other to gain local advantage. There are cases of this happening, and oddly enough, they'll even do it to civilians if they think they can (ask Greenpeace). And the economics is sane, sensible stuff, if we bothered to think about it: in war, the wire is the threat, the nodes are safe.
However, adopting "the wire" as the weakness and Mallory as the Man-In-The-Middle, and Eve as the Eavesdropper as "the threat" in the Internet was a mistake. Even in the early 1990s, we knew that the node was the problem. Firstly, ever since the PC, nodes in commercial computing are controlled by (dumb) users not professional (soldiers). Who download shit from the net, not operate trusted military assets. Secondly, observation of known threats told us where the problems lay: floppy viruses were very popular, and phone-line attacks were about spoofing and gaining entry to an end-point. Nobody was bothering with "the wire," nobody was talking about snooping and spying and listening [*].
The military model was the precise reverse of the Internet's reality.
To conclude. There is no doubt about this in security circles: the SSL threat model was all wrong, and consequently the product was deployed badly.
Where the doubt lies is how long it will take the software providers to realise that their world is upside down? It can probably only happen when everyone with credibility stands up and says it is so. For this, the posts shown here are very welcome. Let's hear more!
[*] This is not entirely true. There is one celebrated case of an epidemic of eavesdropping over ethernets, which was passwords being exchanged over telnet and rsh connections. A case-study in appropriate use of security models follows...
July 29, 2010
The difference between 0 breaches and 0+delta breaches
Seen on the net, by Dan Geer:
The design goal for any security system is that the number of failures is small but non-zero, i.e., N>0. If the number of failures is zero, there is no way to disambiguate good luck from spending too much. Calibration requires differing outcomes.
I've been trying for years to figure out a nice way to describe the difference between 0 failures, and some small number N>0 like 1 or 2 or 10 in a population of a million.
Dan might have said it above: If the number of failures is zero, there is no way to disambiguate good luck from spending too much.
Has he nailed it? It's certainly a lot tighter than my long efforts ... Once we get that key piece of information down, we can move on. As he does:
Regulatory compliance, on the other hand, stipulates N==0 failures and is thus neither calibratable nor cost effective. Whether the cure is worse than the disease is an exercise for the reader.
An insight! For regulatory compliance, I'd substitute public compliance, which includes all the media attention and reputation attacks.
May 28, 2010
questioning infosec -- don't buy into professionalism, certifications, and other silver bullets
Gunnar posts on the continuing sad saga of infosec:
There's been a lot of threads recently about infosec certification, education and training. I believe in training for infosec, I have trained several thousand people myself. Greater knowledge, professionalism and skills definitely help, but are not enough by themselves.We saw in the case of the Great Recession and in Enron where the skilled, certified accounting and rating professions totally sold out and blessed bogus accounting practices and non-existent earning.
Right. And this is an area where the predictions of economics are spot on. In Akerlof's seminal paper "the Market for Lemons," he predicts that the asymmetry of information can be helped by institutions. In the economics sense, institutions are non-trading, non-2-party market contractual arrangements of long standing to get stuff happening. Professionalism, training, certifications, etc all are slap-bang in the recommendations.
So why don't they help? There's a simple answer: we aren't in the market for lemons! There's one key flaw: Lemons postulates that the seller knows and the buyer doesn't, and that simply doesn't apply to infosec. (Criteria #1) In the market for security, the seller knows about his tool, but he doesn't know whether it is fit for the buyer. In contrast, the salesman in Akerlof's market assumed correctly that a car was good for the buyer, so the problem really was sharing the secret information from the seller to the buyer. Used car warranties did that, by forcing the seller to reveal his real pricing.
The buyer doesn't really know what he wants, and the seller has no better clue. Indeed, it may be that the buyer has more of a clue, and at least sometimes. So professionalism, certification, training and warranties isn't going to be the answer.
Another way of looking at this is that in infosec, in common with all security markets (think defence, crime) there is a third party: the attacker. This is the party that really knows, so knowledge-based solutions without clear incorporation of the aggressor's knowledge aren't going to work. This is why buying the next generation stealth fighter is not really helpful when your attacker is a freedom fighter in an Asian hell-hole with an IED. But it's a lot more exciting to talk about.
Which leads me to one controversial claim. If we can't get useful information from the seller, then the answer is, you've got to find it by yourself. It's your job, do it. And that's really what we mean by professionalism -- knowing when you can outsource something, and knowing when you can't.
That's controversial because legions of infosec product suppliers will think they're out of a job, but that's not quite true. It just requires a shift in thinking, and a willingness to think about the buyer's welfare, not just his wallet. How do we improve the ability of the client to do their job? Which leads right back to education: it is possible to teach better security practices. It's also possible to teach better risk practices. And, it can be done on an organisation-wide basis. Indeed, this is one of the processes that Microsoft took in trying to escape their security nightmare: get rid of the security architecture silos and turn the security groups into education groups [1].
So from this claim, why the flip into a conundrum. Why aren't certifications the answer? It's because certifications /are an institution/ and institutions are captured by one party or another. Usually, the sellers. Again a well-known prediction from economics: institutions to protect the buyer are generally captured by the seller in time (if not in the creation). I think this was by Stiglitz or Stigler, pointing to finance market regulation, again.
A supplier of certifications needs friends in industry, which means they need to also sell the product of industry. It's hard to make friends selling contrarian advice, it is far more profitable selling middle-of-the-road advice about your partners [2]. "Let's start with SSL + firewalls ..." Nobody's going to say boo, just pass go, just collect the fees. In contrast:
In short, the biggest problem in infosec is integration. Education around security engineering for integration would be most welcome.
That's tough, from an institutional point of view.
[1] Of course, even for Microsoft, bettering their internal capabilities was no silver bullet. They did get better, and it is viewed now that their latest products are more secure. FWIW. But, they still lost pole position last week, as Apple pipped Microsoft to become the world's biggest tech organisation, by market cap. Security played its part in that, and it is something of a rather stellar prediction that it still remains better /for your security/ to work with a Mac, because apparent Mac market shares are still low enough to earn a monoculture bounty for Apple users. Microsoft, keep trying, some are noticing, but no cigar as yet :)
[2] E.g., I came across a certification and professional code of conduct that required you to sign up as promoting /best practices/. Yet, best practices are lowest-common-denominator, they are the set of uncontroversial products. We're automatically on the back foot, because we're encouraging an organisation to lower its own standards to best practices, and comply with whatever list someone finds off the net, and stop right there. Hopeless!
March 24, 2010
Why the browsers must change their old SSL security (?) model
In a paper Certified Lies: Detecting and Defeating Government Interception Attacks Against SSL_, by Christopher Soghoian and Sid Stammby, there is a reasonably good layout of the problem that browsers face in delivering their "one-model-suits-all" security model. It is more or less what we've understood all these years, in that by accepting an entire root list of 100s of CAs, there is no barrier to any one of them going a little rogue.
Of course, it is easy to raise the hypothetical of the rogue CA, and even to show compelling evidence of business models (they cover much the same claims with a CA that also works in the lawful intercept business that was covered here in FC many years ago). Beyond theoretical or probable evidence, it seems the authors have stumbled on some evidence that it is happening:
The company’s CEO, Victor Oppelman confirmed, in a conversation with the author at the company’s booth, the claims made in their marketing materials: That government customers have compelled CAs into issuing certificates for use in surveillance operations. While Mr Oppelman would not reveal which governments have purchased the 5-series device, he did confirm that it has been sold both domestically and to foreign customers.
(my emphasis.) This has been a lurking problem underlying all CAs since the beginning. The flip side of the trusted-third-party concept ("TTP") is the centralised-vulnerability-party or "CVP". That is, you may have been told you "trust" your TTP, but in reality, you are totally vulnerable to it. E.g., from the famous Blackberry "official spyware" case:
Nevertheless, hundreds of millions of people around the world, most of whom have never heard of Etisalat, unknowingly depend upon a company that has intentionally delivered spyware to its own paying customers, to protect their own communications security.
Which becomes worse when the browsers insist, not without good reason, that the root list is hidden from the consumer. The problem that occurs here is that the compelled CA problem multiplies to the square of the number of roots: if a CA in (say) Ecuador is compelled to deliver a rogue cert, then that can be used against a CA in Korea, and indeed all the other CAs. A brief examination of the ways in which CAs work, and browsers interact with CAs, leads one to the unfortunate conclusion that nobody in the CAs, and nobody in the browsers, can do a darn thing about it.
So it then falls to a question of statistics: at what point do we believe that there are so many CAs in there, that the chance of getting away with a little interception is too enticing? Square law says that the chances are say 100 CAs squared, or 10,000 times the chance of any one intercept. As we've reached that number, this indicates that the temptation to resist intercept is good for all except 0.01% of circumstances. OK, pretty scratchy maths, but it does indicate that the temptation is a small but not infinitesimal number. A risk exists, in words, and in numbers.
One CA can hide amongst the crowd, but there is a little bit of a fix to open up that crowd. This fix is to simply show the user the CA brand, to put faces on the crowd. Think of the above, and while it doesn't solve the underlying weakness of the CVP, it does mean that the mathematics of squared vulnerability collapses. Once a user sees their CA has changed, or has a chance of seeing it, hiding amongst the crowd of CAs is no longer as easy.
Why then do browsers resist this fix? There is one good reason, which is that consumers really don't care and don't want to care. In more particular terms, they do not want to be bothered by security models, and the security displays in the past have never worked out. Gerv puts it this way in comments:
Security UI comes at a cost - a cost in complexity of UI and of message, and in potential user confusion. We should only present users with UI which enables them to make meaningful decisions based on information they have.
They love Skype, which gives them everything they need without asking them anything. Which therefore should be reasonable enough motive to follow those lessons, but the context is different. Skype is in the chat & voice market, and the security model it has chosen is well-excessive to needs there. Browsing on the other hand is in the credit-card shopping and Internet online banking market, and the security model imposed by the mid 1990s evolution of uncontrollable forces has now broken before the onslaught of phishing & friends.
In other words, for browsing, the writing is on the wall. Why then don't they move? In a perceptive footnote, the authors also ponder this conundrum:
3. The browser vendors wield considerable theoretical power over each CA. Any CA no longer trusted by the major browsers will have an impossible time attracting or retaining clients, as visitors to those clients’ websites will be greeted by a scary browser warning each time they attempt to establish a secure connection. Nevertheless, the browser vendors appear loathe to actually drop CAs that engage in inappropriate be- havior — a rather lengthy list of bad CA practices that have not resulted in the CAs being dropped by one browser vendor can be seen in [6].
I have observed this for a long time now, predicting phishing until it became the flood of fraud. The answer is, to my mind, a complicated one which I can only paraphrase.
For Mozilla, the reason is simple lack of security capability at the *architectural* and *governance* levels. Indeed, it should be noticed that this lack of capability is their policy, as they deliberately and explicitly outsource big security questions to others (known as the "standards groups" such as IETF's RFC committees). As they have little of the capability, they aren't in a good position to use the power, no matter whether they would want to or not. So, it only needs a mildly argumentative approach on the behalf of the others, and Mozilla is restrained from its apparent power.
What then of Microsoft? Well, they certainly have the capability, but they have other fish to fry. They aren't fussed about the power because it doesn't bring them anything of use to them. As a corporation, they are strictly interested in shareholders' profits (by law and by custom), and as nobody can show them a bottom line improvement from CA & cert business, no interest is generated. And without that interest, it is practically impossible to get the various many groups within Microsoft to move.
Unlike Mozilla, my view of Microsoft is much more "external", based on many observations that have never been confirmed internally. However it seems to fit; all of their security work has been directed to market interests. Hence for example their work in identity & authentication (.net, infocard, etc) was all directed at creating the platform for capturing the future market.
What is odd is that all CAs agree that they want their logo on their browser real estate. Big and small. So one would think that there was a unified approach to this, and it would eventually win the day; the browser wins for advancing security, the CAs win because their brand investments now make sense. The consumer wins for both reasons. Indeed, early recommendations from the CABForum, a closed group of CAs and browsers, had these fixes in there.
But these ideas keep running up against resistance, and none of the resistance makes any sense. And that is probably the best way to think of it: the browsers don't have a logical model for where to go for security, so anything leaps the bar when the level is set to zero.
Which all leads to a new group of people trying to solve the problem. The authors present their model as this:
The Firefox browser already retains history data for all visited websites. We have simply modified the browser to cause it to retain slightly more information. Thus, for each new SSL protected website that the user visits, a Certlock enabled browser also caches the following additional certificate information:
A hash of the certificate.
The country of the issuing CA.
The name of the CA.
The country of the website.
The name of the website.
The entire chain of trust up to the root CA.When a user re-visits a SSL protected website, Certlock first calculates the hash of the site’s certificate and compares it to the stored hash from previous visits. If it hasn’t changed, the page is loaded without warning. If the certificate has changed, the CAs that issued the old and new certificates are compared. If the CAs are the same, or from the same country, the page is loaded without any warning. If, on the other hand, the CAs’ countries differ, then the user will see a warning (See Figure 3).
This isn't new. The authors credit recent work, but no further back than a year or two. Which I find sad because the important work done by TrustBar and Petnames is pretty much forgotten.
But it is encouraging that the security models are battling it out, because it gets people thinking, and challenging their assumptions. Only actual produced code, and garnered market share is likely to change the security benefits of the users. So while we can criticise the country approach (it assumes a sort of magical touch of law within the countries concerned that is already assumed not to exist, by dint of us being here in the first place), the country "proxy" is much better than nothing, and it gets us closer to the real information: the CA.
From a market for security pov, it is an interesting period. The first attempts around 2004-2006 in this area failed. This time, the resurgence seems to have a little more steam, and possibly now is a better time. In 2004-2006 the threat was seen as more or less theoretical by the hoi polloi. Now however we've got governments interested, consumers sick of it, and the entire military-industrial complex obsessed with it (both in participating and fighting). So perhaps the newcomers can ride this wave of FUD in, where previous attempts drowned far from the shore.
February 22, 2010
US officials move to infect Populace with 5T00P.1D virus -- google, bombs, Mozilla, oil & barrels of stupidity
A wave of stupidity is flooding through the USA mediawaves. Here's an example:
A cyberattack disabled US cell phone networks, slowed Internet traffic to a crawl and crippled America's power grid Tuesday -- all in the interest of beefing up US security. Dubbed "Cyber ShockWave" and organized by the Bipartisan Policy Center (BPC), the event was held at a Washington hotel room transformed for the day into the White House Situation Room, where the president and his advisers typically meet to address national emergencies.In the simulation, former top US officials debated how to respond as the power grid in the eastern United States was virtually shut down by a stealth cyberattack and a pair of bombings, cutting electricity to tens of millions of homes.
This is an "exercise" conducted by something called the Bipartisan Policy Group. The confusion between officialdom and lobbying could be forgiven, because it was intentional. Consider this list of Washington DC rock stars:
- Fran Townsend, former president George W. Bush's one-time Homeland Security advisor
- Charles Wald, a retired general and the former deputy commander of US European Command
- Michael Hayden, a former CIA director, ex-Homeland Security chief Michael Chertoff
- former Director of National Intelligence John Negroponte, former deputy CIA director John McLaughlin
- Joe Lockhart, former president Bill Clinton's press secretary ...
Then we have the amazing spectacle of Google complaining about being attacked by China!? Is there -- can there be -- any credence to this story? To me, it doesn't pass the laugh test, it is clearly a propaganda story with a hidden message. A little clicking and we find this:
Second, we have evidence to suggest that a primary goal of the attackers was accessing the Gmail accounts of Chinese human rights activists. Based on our investigation to date we believe their attack did not achieve that objective. Only two Gmail accounts appear to have been accessed, and that activity was limited to account information (such as the date the account was created) and subject line, rather than the content of emails themselves.
Oh. 2 activists... that's two, the number between one and three ... gmail accounts of alleged activists. Not hacked but probed. This is below underwhelming, this is quintessence of underwhelming, the very quantum of underwhelming!
One glance and it's gone. If you read more, the contradictions just keep rolling in. Apparently it is related to copyright theft, or, no it's not. Related to a concerted attack on 30 big companies, or not. It's caused by a horrifying new technique called "man-in-the-mailbox" or it's caused by phishing, or a virus, not. It's China, or it's Taiwan! It's a school, or it's the Red Army?
What's going on? What is curious is why a group so historically sensible and focussed as Google fell to such a stupidity as announcing this in a blather of hype. Well, read a bit further:
These attacks and the surveillance they have uncovered--combined with the attempts over the past year to further limit free speech on the web--have led us to conclude that we should review the feasibility of our business operations in China. We have decided we are no longer willing to continue censoring our results on Google.cn, and so over the next few weeks we will be discussing with the Chinese government the basis on which we could operate an unfiltered search engine within the law, if at all. We recognize that this may well mean having to shut down Google.cn, and potentially our offices in China.
Ah. So, google are under pressure from the Chinese government. This is *nothing* to do with cyber-hacks, activist, freedom of speech, intellectual property, APTs, and everything to do with the access to the Chinese market. On terms appropriate to Google. They needed a casus belli to convince someone (shareholders? own employees?) of the need to rattle sabres, and a hack is a great catch-all. But, in the process of feeding the media craving for new heights in gullibility, google might have drunk a little too deeply of the kool-aid, because they then negotiated with the NSA to cut a secret deal; if there is ever a sign that it's all over for independence, that's the one!
Google approached the NSA shortly after the attacks, sources said, but the deal is taking weeks to hammer out, reflecting the sensitivity of the partnership. Any agreement would mark the first time that Google has entered a formal information-sharing relationship with the NSA, sources said. In 2008, the firm stated that it had not cooperated with the NSA in its Terrorist Surveillance Program.Sources familiar with the new initiative said the focus is not figuring out who was behind the recent cyberattacks -- doing so is a nearly impossible task after the fact -- but building a better defense of Google's networks, or what its technicians call "information assurance."
Getting out of China, to maintain independence, then signing up with the NSA, doesn't present a consistent message. I love the quote about how they don't want to break any laws on spying on Americans...
Back to China. The rhetoric has spread further than expected. Over in Mozilla's groups, the anti-China faction has stirred up another little hate campaign over a Chinese CA called CNNIC.
With this background in mind, let's unpack the Mozilla debate. What set off the debate was the addition of the China Internet Network Information Center (CNNIC) as a trusted CA in Firefox. CNNIC is not part of the Chinese government but many people assert that it would be willing to act in concert with the Chinese government.To see why this is worrisome, let's suppose, just for the sake of argument, that CNNIC were a puppet of the Chinese government. Then CNNIC's status as a trusted CA would give it the technical power to let the Chinese government spy on its citizens' "secure" web connections. If a Chinese citizen tried to make a secure connection to Gmail, their connection could be directed to an impostor Gmail site run by the Chinese government, and CNNIC could give the impostor a cert saying that the government impostor was the real Gmail site. The Chinese citizen would be fooled by the fake Gmail site (having no reason to suspect anything was wrong) and would happily enter his Gmail password into the impostor site, giving the Chinese government free run of the citizen's email archive.
Which offends them mightily, because CNNIC is likely to follow the Chinese government's rules on ... well, everything, as did a veritable stampede of popular western companies (Microsoft, Sun, Cisco, Skype spring to mind, and don't forget google who did, and don't and won't and might stop and want to take their bat and ball and go home). The problem for Mozilla is, CNNIC seems to offend them in more or less legal ways, in more or less policy ways, and in more or less the ways of every other view we can objectively apply.
The crime, after all the evidence is assembled (not a single credible fact that I have seen), is pretty thin, and as thin as the accusations levelled against every other CA from time to time.
But, this matters not at all if the real objective is popular manipulation (propaganda, by some). Note the clear linkage above from google to gmail to Mozilla... What might be called governance and protection of 250 million users in Mozilla technical circles might also politely be called nationalism by others.
But. Silly as it is, the message meshes in nicely with the current global geopolitical aspirations of some in Washington, at top. Back to the silk-dress appeal for pork-barrel funds by the "BPG":
An operation dubbed "Cyber ShockWave" has spanked the U.S.'s cyberdefenses -- hypothetically. Under the scenario organizers dreamed up, virus-infected smartphones spread malware to their owners' PCs. From there, the attackers DDoSed telecommunications networks into submission, brought down electrical grids and bombed a gas pipeline. The verdict: America's cyberdefenses are wanting.
What's the connection between the Mozilla skirmish, the Google retreat, and the unaffiliated-affiliated NGO above?
These are all the same war, the war on China. And, the battleground isn't anywhere near China (indeed they are probably as bemused as anyone else), it's happening in the American media. Although Mozilla do not think they are political and although Google would like not to be political, both of these agents are being dragged into an anti-China rhetoric by a much more media-savvy player, anciently called the military-industrial complex, at times called "the hawks," more recently called the Neocons, and now wielding the pathetic title of Bipartisan Policy Group:
"You're going to see planes being grounded now. You're going to see trains not moving," said Fran Townsend, former president George W. Bush's one-time Homeland Security advisor, who was promoted to Homeland Security secretary for the simulation.The "cabinet members" debated how to respond to the situation and what advice to give the president, with suggestions ranging from calling out the National Guard, nationalizing the power companies and retaliating once the attackers' identities were known.
"If this is an attack on the United States the president, as commander-in-chief, has the authority to use the full powers at his disposal," said former deputy attorney general Jamie Gorelick, playing the role of the US attorney general.
"We're in good shape from a command and control standpoint," said "Secretary of Defense" Charles Wald, a retired general and the former deputy commander of US European Command. "We can take action offensively if we know where to go," Wald said. "Problematically, we don't know where that is."
That crowd doesn't know the difference between a bit and a bomb, but they don't need to because the warfront is the media front, and they certainly know a thing or two about using the media to prepare you for their next big adventure. You might thing this is a small thing, but the propaganda just keeps on rolling. The British version of the NSA, called GCHQ, is also infected:
"A successful cyber attack against public services would have a catastrophic impact on public confidence in the government, even if the actual damage caused by the attack were minimal," [Cheltenham spy agency's new Cyber Security Operations Centre (CSOC) says].The warning forms part of a preliminary "horizon scanning" report produced by the new unit, which is scheduled to begin operations next month. Its job will be to continually monitor internet security, producing intelligence on botnets, denial of service attacks and other digital threats to national security.
Such a level of FUD has rarely been seen outside the information security industry and wartime. This is awful news for just about everyone. What most of these players want is to shake China down. Google wants "in" on comfortable USA competition rules, where it gets the preferential treatment that allows its business model to shine. No bad thing for the Google shareholder, but the Chinese government wants to reserve that market for a local player (for obvious & easy reasons):
In the last two decades, China's economic reform programs and its citizens' entrepreneurial flair have lifted hundreds of millions of Chinese people out of poverty. Indeed, this great nation is at the heart of much economic progress and development in the world today.
Google wants a piece of that action, plain and simple. Mozilla wants "in" on far more vague grounds that can't really be tied down, but they probably feel an interest in preserving the ability of activists in China to browse securely. Given my crypto history, it should be no surprise that I'm sympathetic to that argument as are many readers, but China isn't. If we think of it in legal terms, this puts Mozilla squarely against the current anti-democratic, anti-freedom-of-speech laws of one quarter of the planet. As google said:
We have taken the unusual step of sharing information about these attacks with a broad audience not just because of the security and human rights implications of what we have unearthed, but also because this information goes to the heart of a much bigger global debate about freedom of speech.
Meanwhile, the last-war-generals in Washington DC want "in" to China on a geophysical control basis, whereas the Chinese government wants to reserve the supply of commodities to itself. That is, China has a long term strategic mission of securing the supply of commodities to its industries. Washington DC disagrees. Hence, we find a lot of strange bedfellows all agreeing on the same objective, but for wildly different reasons.
At this point, most readers will think I'm short a few marbles. All can I say in my defence is this: the rise of China in the thought-processes of the Washington DC set is pretty easy to see, if you look. It's been there for at least a decade to my knowledge; it pops up in any serious scandal from Middle East, looking eastwards to some watery point well west of Japan. You'll have to take it on faith that when you're in a tussle with China, suddenly you'll find an 800lb gorilla in the room as your ally. Slashdot knows it, from many examples here's just one:
While I don't disagree that we could do more in the area of computer security, one needs to look closely at the affiliations of the people running this "exercise."They're both loyal Neocon insiders. John Negroponte [wikipedia.org] is the former Bush Director of National Intelligence. Michael Chertoff [wikipedia.org] is the former Director of Homeland Security, and co-author of the Patriot Act. And both of these positions were just the last in a string of appointments by Bush/Cheney.
And as career neoconservatives, they've been at the forefront of fearmongering and prevarication in order to lead the US to war and erode civil liberties. These are not opinions, these are well-documented facts [google.com].
The neocons are a one trick circus; this is just their newest pony. If you've been paying attention the past nine years, how can you possibly doubt that this is anything else?
A gorilla you really don't want in your living room, because the cost of the alliance is probably a house re-build. The danger lurking within is this: the hawks' theory is that China will take over the USA militarily sometime in the next few decades. Whatever you think about geopolitics (last 20 years of small proxy wars, etc) this has led a not-insignificant group within the Beltway into wanting a war of some form with China. Their theory is that they have to do it now or soon, or else it will be too late.
And this may explain the flush of rhetoric out of Washington DC: the hawks are scared they are running out of time for a war, and for that, the next step is simple: they have to swing the American public behind them, into a bellicose, anti-China mood (recall how they did this with Iraq 2).
Which brings us back to the cyber-war nonsense. This is the perfect cassus belli because there is no embarrassing evidence to show they are lying; indeed we can't even get it right or clear or agreed in the open market because the electrons won't sit still after the attack. As cassus bellis go, it's got more mileage than historical ones such as Iraqi nukes or Saddam's mate Osama or the North Vietnamese torpedoe boats in the Gulf of Tonkin, because in the end, the physical evidence spoke up.
From now on in, cyber-war will be a central plank of the war on China. The only problem is, it's a lie, a casus belli, and it's more or less unprovably false and unprovably true and very very scary, all at the same time. The American Public are being set up, again. Same as it ever was, but this time the entire Internet, security, communications and interactions world is being dragged in.
That effects every one of us. This time it's personal.
(As an aside, the hawks' strategy is doomed to failure. It worked in Iraq 1 & 2 because of many factors that were easily predictable. Arguably, it failed or worked in Talibans 1, 2. It failed in Iran, but there's still hope. Unlike Iraq & Iran, who supply lots of *commodity* oil, and Afghanistan which supplies commodity opium, China supplies manufactured goods to USA. If oil or drugs slow down, the price goes up, and the market adjusts. The traders love that, it's called volatility.
On the other hand, if Walmart is emptied, we've got bigger problems, nobody benefits from that. But this easily predictable failure of strategy won't stop the hawks, possibly because their experience in economics is limited to slopping at the pork-barrel trough. As far as policy goes, this is the same stupid crowd that chose to hollow out its nearest and dearest southern neighbour in the so-called _war on drugs_. The stupidity virus has gone deep.)
January 28, 2010
the most magical question of all -- why are so many bright people fooling themselves about the science in information security?
It has been clear for a long time that information security was more about perception than any other factor than was good for it, a concept I tried to turn into a theory in the market for silver bullets, based on some solid thinking by others on the economics of insufficient information. Here are some random snippets that seem to anecdotally support that security is dominated by perception.
Gunnar reports on Google who were apparently subject to a cyber-attack by China. I didn't notice, probably because it doesn't pass the laugh test, but he collects all this security-blog-o-sphere stuff into a nice package:
Of course cyberattacks and the other issues raised by Google as rationale have been around for a long time, so why did they choose now as the time to threaten to pull out? ... First, we know that Google has been getting its butt kicked by Baidu.com. Baidu's search market share in 3Q09 was 77%. ... Google was in need of some positive PR to correct its worsening image (especially in Europe, where concerns about privacy are mounting on a daily basis). Google.cn is the goat that would be sacrificed ... It's no surprise than NSA is getting interested in the story. One doesn't need to know much about US politics to realize that framing this as a national security issue is going to make Google's case for US government's pressure on China much stronger ... No wonder Google has been hiring all those smart policy types with government experience ...
While Google is bandying around the phrase "national security" as a commercial weapon, Bruce Schneier is earning lots of airmiles by talking not about security but about what he calls *magical thinking*: TSA rules to make you safer from the last attack:
Of course not, the attacks are designed to get through whatever we're doing. The liquid bombers used liquid so now we screen liquids. This is a powder bomber using powders. They will look at what we do and do something different. There's sort of a bit of magical thinking about the last hour, its not a more dangerous hour, its the hour this guy happened to choose. I am not sure why the next guy can't choose the first hour or a different material or maybe even not an airplane. Focusing on the tactic might make us feel a little better but its not going to make us any safer.
Or, what military types refer to as fighting the last war, or, building the Maginot Line. Which would support the notion that the real enemy that TSA is fighting is the home front, and perception is the weapon of choice.
Adam has a nice collection of the latest TSA madness, including this quote:
'It became necessary to destroy the town to save it,' a TSA major said today. He was talking about the decision by allied commanders to shock and awe the public regardless of civilian casualties, to rout al Qaeda.
Which I can't tell if it is a spoof or not, but it seems to be on point. Here is more evidence of the perceptional nature of security: news that Microsoft's browser had a flaw in it has finally caused governments to sit up and do the unthinkable: warn people not to use a Microsoft product.
Nobody would ever notice if a government said "we don't use Linux because of security issues" or "we don't permit Apple because of ..." Microsoft's browbeating of the press and governments has been so successful that for 2 decades, nobody dare say "don't use Microsoft." Remember "Nobody every got fired for buying IBM?"
Which unfortunately has been a great loss to Microsoft (as it was to IBM) because it hid the danger from them, too, until 1992. Now they are facing the long-term decline, shackled with their chains of past insecurity. Perception-wise, they will probably never be able to shake off the the real public opinion, now that it's shifted, even with the great work listed at bottom.
 Too late for their future shareholders, but maybe their past shareholders had the right idea? Markus Kuhn reports on a placebo bomb detector for the BBC, and discovered it is testably indistinguishable with any other random appliance purchased at the local Dixon's (consumer electronics store):
Too late for their future shareholders, but maybe their past shareholders had the right idea? Markus Kuhn reports on a placebo bomb detector for the BBC, and discovered it is testably indistinguishable with any other random appliance purchased at the local Dixon's (consumer electronics store):
There is no way in which this device could be programmed to distinguish the many different substances that the ADE651 manufacturer claimed it could, not to mention that any useful interaction with such an LC circuit would require a transmitter antenna, a power source, and lots of other components that the ADE651 appears to lack.
These things sell for around 40,000 sterling each, in quantity, and the Iraqi government swears by them. OK, whatever. Compelling proof ... that the power of the placebo is essential to unlock the minds of the (human) bomb detectors that do the real job? You be the judge. What has not as yet been answered to me is why the TSA has not purchased them -- if they are America's department for magical thinking, why not purchase such things?
The devices contain no power source (”powered by the user’s static electricity”, no battery), resemble very much a dowsing rod, and generally leave much to be desired regarding a plausible operating principle or performance in repeatable double-blind trials. There are several such military dowsing rods on the market.
And they won't contribute to global warming! So real security (where "real" means, we have evidence that this is how people think, act and purchase) is as much about placebo devices as anything else. Here's the most magical question of all: why is an entire generation of crypto/security/geeks fixated on the technical workings of a device? Insisting that it operate to lab specs? When all the evidence from the field indicates that it doesn't matter much if at all?
Here's another outstanding example: Last month there was a series of crypto break news in GSM phones. Here's a summary from emergentchaos's Mordaxus.
Orr Dunkelman, Nathan Keller, and Adi Shamir have released a paper showing that they've broken KASUMI, the cipher used in encrypting 3G GSM communications. KASUMI is also known as A5/3, which is confusing because it's only been a week since breaks on A5/1, a completely different cipher, were publicized. So if you're wondering if this is last week's news, it isn't. It's next week's news.
(Except it's last month's news.) OK, joking aside, so what? GSM phones use encryption to stop the papparazzi recording your love-chat, stop neighbours hearing your shopping list, and spoofers stealing GSM minutes. As long as they do that, why aren't we happy with a 40 bit crypto response to the 20 bit crypto threat?
(In 1994 numbers, etc, just add water for 16 years of crypto-flation.)
It will be interesting to see the response from the GSM Association. They have the opportunity to show leadership. If they recognize that this is a real problem, reassure us that it's not a catastrophe, and show that they're taking it seriously, then this can be an all-around good thing for them and us.We're all adults (well, okay, most of us are adults and act like adults some of the time), and if we know that there will be an upgrade in a few years, then that's great. We lived through the WEP issues. We are living through the SSL evil proxy issues. This is less acute than either of those. But we need to have some assurance that in a few years, we'll just get wireless devices with a safety net.
I don't mean to pick on mordaxus here, but this typifies an entire security industry: absolute obsession with an apparent security rating (measured in bits of crypto strength) and an almost willful blindness to the environment of choice. Let's list how safe we are because of GSM's fine security design:
- All phones provide the complete and perfect location and relationship tracking device for all citizens [one, two, three, four], and we told on great authority that we should be worried when they aren't so good at tracking, according to Kuhn's colleague Richard Clayton,
- the conversation is only encrypted over the airwaves to the nearest base station (which has minimal security in it, if those "buy your own base-station" adverts are correct),
- Phones are probably programmable over the air via various techniques (undocumented, elusive, insert your conspiracy theory here about advice to take out your battery when attending a secret meeting, etc etc), and
- The entire infrastructure doesn't really have a lot of security, and that's purposeful.
What is the "real problem" that Mordaxus expects them to spot? What catastrophe? It's not as if we need to speculate here, we actually have real evidence: We know that when they were broken 12 years ago by Lucky Green ... nothing happened. It didn't change our security situation one iota.
Their challenge is to have a response before this news metastasizes into a common perception that 3G crypto is worthless.
Right. If we have no security argument, we also are left arguing on perception.
There are some out there that think they can use psychology to assess our current security thinking. Perhaps they can answer the most magical question of all: why are the world's top security sellers so quick to damn a crypto algorithm that has lost of few bits, like MD5, when the world's top security buyers are happily purchasing Placebo devices with 5km ratings? Or Cell-phones with 40 bit crypto? And, apparently happy with their choice?
Let's face it. Security thought as a science is failed, it is all marketing, all perception, all religion. The good news is that this meme seems to be finally getting some traction in the scientific community: "So Long, and no thanks for the Externalities: The Rational Rejection of Security Advice by Users" by Cormac Herley, who works for, of all people, Microsoft Research. Finally, we have the paper that says what we all knew:
It is often suggested that users are hopelessly lazy and unmotivated on security questions. They chose weak passwords, ignore security warnings, and are oblivious to certificates errors. We argue that users’ rejection of the security advice they receive is entirely rational from an economic perspective. The advice offers to shield them from the direct costs of attacks, but burdens them with far greater indirect costs in the form of effort. Looking at various examples of security advice we find that the advice is complex and growing, but the benefit is largely speculative or moot. For example, much of the advice concerning passwords is outdated and does little to address actual threats, and fully 100% of certificate error warnings appear to be false positives.
Read that if you think there is a place for science in information security. On the other hand, if you think information security is something else, better off to go read something on creative journalism, public relations, politics, marketing, ...
December 09, 2009
Bowles case is more evidence: Britain takes another step to a hollowed-out state
In the very sad story of the Justice System as we know it, a British courts has ruled the beginning of the end.
He went to jail this week, protesting his innocence. Speaking to The Times, he said: "There are no missing millions, there's no villa in the Virgin Islands, there has been no fraud. I am not allowed to earn any money, my assets were restrained so I couldn't use them to defend myself - it's a relentless, never-ending, vicious, cruel and wicked system.
Of course, all mobsters say that. So what was the crime?
Bowles was convicted by a jury in June of cheating the Revenue of £1.2 million in VAT but sentencing had been adjourned on three previous occasions. He had been found guilty of failing to pay VAT on a BIG land sale and diverting money due to the taxman to prop up Airfreight Express, his ailing air-freight company.
Now we have come full circle, and the evidence is presented: the Anti-money-laundering project of the OECD (known as the Financial Action Task Force, a Paris-based body) is basically and fundamentally inspired by the desire to raise tax. Hence, we will see a steady progression of government-revenue cases, occasionally interspersed with Mr Big cases. This is exactly what the OECD wanted. Not the mobsters, murderers, drug barons and terrorists pick up, but:
Bowles is a divorced, middle-aged company director from Maidenhead who has been transformed from successful entrepreneur to convicted fraudster.
A businessman, from the very heartland of English countryside. Not a dangerous criminal at all, but someone doing business. Not "them" but us. POCA or Proceeds of Crime Act is now an important revenue-raising tool:
It was not suggested that Bowles, who has no criminal record, had used the money to fund a luxury lifestyle. Nevertheless, when the Revenue began a criminal investigation into his affairs in 2006 all his assets were frozen under the powers of the Proceeds of Crime Act.Bowles was required to live on an allowance and rely on legal aid for his defence rather than pay out of his own resources. Defence lawyers claimed that preparation of Bowles's defence case was hampered further because his companies' financial records were in the hands of administrators.
The accounts were not disclosed until a court hearing in February this year, at which point Bowles sought permission to have a forensic accountant examine them to determine the VAT position. He was refused a relaxation of the restraint order to pay for a forensic accountants' report. The Legal Services Commission also declined to fund such a report from legal aid.
After the court was told that the records "could be considered by counsel with a calculator" the trial went ahead. Bowles was cleared of two charges but found guilty of a third.
It works this way. First the money is identified. Then, the crime is constructed, the assets are frozen, legal-aid is denied, and the businessman goes to jail. By the time he gets out of that, he probably cannot mount a defence anyway, and rights are just so much confetti. This stripping of rights is a well-known technique in law, as only 1 in 100 can then mount a recovery of rights action, it is often done when the job of the prosecutor is more important than rights.
Let's be realistic here and assume that Bowles was guilty of tax fraud. His local paper certainly thinks he was guilty:
A tax cheat from Maidenhead who dodged paying £1.3m in VAT has been jailed for three-and-a-half years. ... The court heard between October 2001 and July 2006 Bowles failed to submit VAT returns to HM Customs and Excise (HMCE) and then HM Revenue & Customs (HMRC). The VAT related to the sale of land for commercial development in Cardiff worth £7.5m.Following an HMRC criminal investigation Bowles, from Sandisplatt Road, was charged on three counts of 'cheating the revenue'. Peter Avery, assistant director, HMRC Criminal Investigations, said: "This sentence will serve as a deterrent to anyone who thinks that tax fraud is a risk worth taking."
Firstly, this is quite common, and secondly, tax is the most complicated thing in existence, so complicated that most ordinary lawyers don't recognise it as law by principle. It's the tax code, it's special. It's actually very hard not to be guilty of it, when you have a fair-sized business (whoever heard of a value-added-tax on a land sale?)
But even assuming that the guy was guilty, there was rather stunning evidence to the contrary, which underscores the point that this was revenue raising, not the bringing down of a Mr Big:
A financial report has since been prepared, free of charge, by a firm of chartered accountants. A draft copy was presented to the judge two months ago and a full version handed to him this week. Its analysis concludes that rather than owing tax, Bowles's companies had actually overpaid their taxes.The report stated: "In our opinion, none of the evidence points to Philip Bowles fraudulently evading or concealing VAT due to HMRC ... It would have been reasonable to conclude that no fraud has taken place."
Lawyers for Bowles claimed in court that matters were compounded by a failure to explain VAT law properly. They alleged the jury were wrongly informed that companies in the same group could not assign tax liabilities and credits between each other.
When a firm of *chartered accountants* utters _an opinion_ over finances, this is a legally imposing evidence. It is given a special status in court, in that the court may rely on it, and so might all others; this special status is awarded for the purposes of public companies that need to impress others such as creditors and shareholders that the company is sound. This form of reliance is not available outside the accounting profession, and only available in an accounting context (e.g., when a firm of accountants audits a certification authority, we do not get a special right to rely on it without further ado).
When a firm of chartered accountants does this for free, this is beyond surprising, this is a shock. The natural order of things is now upset. When the accountants are working for free, this might mean that the professions are mounting a last-ditch effort to preserve the Justice System in Britain, as I predicted:
It took 20 years to hollow out Mexico, we have a bit longer in other countries, because the institutions are staffed by stiffer, better educated people.
Those stiffer, better educated institutions realise that we all are poorer when the justice system is used to raise revenue. Or perhaps they realise their turn is next?
November 26, 2009
Breaches not as disclosed as much as we had hoped
One of the brief positive spots in the last decade was the California bill to make breaches of data disclosed to effected customers. It took a while, but in 2005 the flood gates opened. Now reports the FBI:
"Of the thousands of cases that we've investigated, the public knows about a handful," said Shawn Henry, assistant director for the Federal Bureau of Investigation's Cyber Division. "There are million-dollar cases that nobody knows about."
That seems to point at a super-iceberg. To some extent this is expected, because companies will search out new methods to bypass the intent of the disclosure laws. And also there is the underlying economics. As has been pointed out by many (or perhaps not many but at least me) the reputation damage probably dwarfs the actual or measurable direct losses to the company and its customers.
Companies that are victims of cybercrime are reluctant to come forward out of fear the publicity will hurt their reputations, scare away customers and hurt profits. Sometimes they don't report the crimes to the FBI at all. In other cases they wait so long that it is tough to track down evidence.
So, avoidance of disclosure is the strategy for all properly managed companies, because they are required to manage the assets of their shareholders to the best interests of the shareholders. If you want a more dedicated treatment leading to this conclusion, have a look at "the market for silver bullets" paper.
 Meanwhile, the FBI reports that the big companies have improved their security somewhat, so the attackers direct at smaller companies. And:
Meanwhile, the FBI reports that the big companies have improved their security somewhat, so the attackers direct at smaller companies. And:
They also target corporate executives and other wealthy public figures who it is relatively easy to pursue using public records. The FBI pursues such cases, though they are rarely made public.
Huh. And this outstanding coordinated attack:
A similar approach was used in a scheme that defrauded the Royal Bank of Scotland's (RBS.L: Quote, Profile, Research, Stock Buzz) RBS WorldPay of more than $9 million. A group, which included people from Estonia, Russia and Moldova, has been indicted for compromising the data encryption used by RBS WorldPay, one of the leading payment processing businesses globally.The ring was accused of hacking data for payroll debit cards, which enable employees to withdraw their salaries from automated teller machines. More than $9 million was withdrawn in less than 12 hours from more than 2,100 ATMs around the world, the Justice Department has said.
2,100 ATMs! worldwide! That leaves that USA gang looking somewhat kindergarten, with only 50 ATMs cities. No doubt about it, we're now talking serious networked crime, and I'm not referring to the Internet but the network of collaborating, economic agents.
Compromising the data encryption, even. Anyone know the specs? These are important numbers. Did I miss this story, or does it prove the FBI's point?
November 23, 2009
Google and Finance 2.0? Nope, sorry. They lack the competency of demythicalisation.
One of the interesting things about the financial system we built back in the late 1990s is that the design was pretty much spot on, and that keeps getting confirmed. I recently found out that the PKI infrastructure used the design in a CA-to-CA protocol, so they do know how to do it :)
Slowly, the knowledge inches its way up to the level needed to appreciate and duplicate the work of the early pioneers (insert long list of names here...). Over on the Harvard Business blog, Umair Haque muses on what "finance 2.0" would be like and looks at google.
Every day, you handle more searches than the NYSE handles trades — and that difference, I'm guessing, is about to hit an order of magnitude more. Every day, you connect people, businesses, and communities in deeper and tighter ways than besuited beancounters do. From my tiny perspective, it seems that you just might be in the best position of any organization in the world to take on Finance 2.0.
It's an inspirational question; and we know where the inspiration came from. But it is not exactly spot on. Google is a good fit for the market data side and search ("market"), as seen above. But not for the trade side, or more particularly the settlement side. If you know the difference, you're half way there. They *could be* a good fit because that side is just a matter of acquiring the right skills, the right mentality. But it takes a job of work and some tearing down of assumptions, because those things aren't easy to look up on wikipedia. Been there, spent the money, and only by luck and hard work did I figure it out. Not, I assure you, because "I'm smarter."
After money, the first great financial innovation was bills of exchange. What's interesting about bills of exchange is that they're just, well, information. Their example makes the point: money, debt, derivatives — all are just information.
Oh, big mistake, and this makes the point. Finance isn't "just information," it's information built on a foundation of transactions, which is built on a foundation of contracts, which is built on ... well, you get the point. And these many floors, each a foundation for the next, are widely and deeply misunderstood even, or especially in the building known as finance.
In my experience, when I talk to deep industry experts, they almost universally focus on the elevator ride and consequently bumble around with great authority in a 2 x 4m box within a huge edifice. I guess this point shouldn't be controversial, as we've now seen this great financial crisis, so we know that the industry is competitive with Hollywood when it comes to the mythology and starstruckedness.
Google Finance is nice. I like using it a lot. But if it created thick value — by really slashing search costs in finance — it would have prevented people, communities, and society from investing in toxic CDOs in the first place. It didn't. It's a pair of reading glasses, when what the world needs (to begin with) is the financial equivalent of an electron microscope.What would a Googlier finance industry resemble? What would a more Googly set of capital markets look like? That's the $12 trillion dollar question. After all, markets are just search engines — remember?
See how people are getting closer? So much hope, still far from the solution, but getting closer. Given the amount of desire for solutions right now, there is an outside chance that the creativity needed could take off around 2015, where it didn't in 1995.
Let's get serious. Markets are just search engines, but only at one level of abstraction. This is where google fits, where information is searchable. At other abstractions they are exchanges of information, and this widely-studied topic is full of nuance, full of deception. Google doesn't fit here at all, and many have broken themselves on it.
What does it look like? It looks like financial cryptography; finance with a delicate touch of cryptography, but also larger doses of software, rights, accounting, governance stuffed in between. If you want to know what it looks like in more detail than a windmilling blog post, study Digicash for inspiration, AADS for the complications, Systemics for the transactions, the gold issuance business for the governance.
But beware; it's not about awesome, nor is it about marketing blah blah, nor is it about huge data capabilities. If anything, the core skill you need is demythologisation; the stripping away of fairy tales, until you can see the core.
What company is best for that? I have my views, but it ain't google.
November 13, 2009
FC: better than freedom?
Better than freedom?Nov 12th 2009 | BAGHDAD
From The Economist print edition
Why Iraqis cherish their mobile phonesASKED to name the single biggest benefit of America’s invasion, many Iraqis fail to mention freedom or democracy but instead praise the advent of mobile phones, which were banned under Saddam Hussein. Many Iraqis seem to feel more liberated by them than by the prospect of elected resident government.
In the five years since the first network started up, the number of subscribers has soared to 20m (in a population of around 27m), while the electricity supply is hardly better than in Mr Hussein’s day....
Good news for them! It gets better:
During recent years of civil strife, when many stayed indoors, mobile phones were the lifeline. They also became a tool of commerce. Reluctant to risk their lives by visiting a bank, many subscribers transferred money to each other by passing on the serial numbers of scratch cards charged with credit, like gift vouchers. Recipients simply add the credit to their account or sell it on to shops that sell the numbers at a slight discount from the original. This impromptu market has turned mobile-phone credit into a quasi-currency, undermining the traditional informal hawala banking system.
Practically every financial cryptographer I know has made this observation. Phones can be used to ship money. Mobile minutes are a fantastic demand base for money. They've been traded at face value for a long time. And, visiting banks is dangerous in some contexts, something we rich fat&happy westerners often forget.
This is pure financial cryptography: the turning of a simple technical architecture based on some security (some crypto) into a network capable of moving value for people. If there is any doubt left...
The market’s growing size is making some bankers wonder if phone credit should be traded on a public exchange. This may not be practical, but more regulation would be welcome. ... Prostitutes get regular customers to send monthly retainers to their phones, earning them the nickname “scratch-card concubines”, while corrupt government officials ask citizens for $50 in phone credit to perform minor tasks.
 We got it all: markets to trade phone credit, crime, so we've crossed that GP thing, and booming trade where the worry-worts in government would normally blush and ban.
We got it all: markets to trade phone credit, crime, so we've crossed that GP thing, and booming trade where the worry-worts in government would normally blush and ban.
Of course, those same people will rant on about how this is promoting crime, and it must be banned.
Criminal rings are among the parallel currency’s busiest users. Kidnap gangs ask for ransom to be paid by text messages listing a hundred or more numbers of high-value phone cards. ... Viewed as cash substitutes, scratch cards have also drawn the attention of armed robbers. In one case, a gang emptied out the card storage of Iraq’s biggest mobile operator, Zain, which is based in neighbouring Kuwait.
Serious architects of money systems know that *all* such electronic systems also work to seriously track the crook (even the much-hyped DigiCash was not exactly as it seems). The notion that you can send a ransom over a phone is just press-headlines and FUD. Remember, the cell towers can track the phone bearer to 10m or so, so if you do that, it's because the police aren't doing their job.
Still, it remains popular political policy to shoot the messenger, as was done in Europe in the 1990s, and now is popular in other countries. But we've also learnt that when a need is big enough, even the normal worries are swept away:
Not to be left out of the bonanza, Iraq’s cash-strapped government now says it will sell a fourth mobile-operating licence, after raising $1.25 billion from each of the last three. That is less than its vast oil reserves promise to put into the state’s coffers but a lot easier to negotiate. And Baghdad is not the only place where mobile-phone commerce thrives. The UN says it has plans to deliver aid to Iraqi refugees in Syria in the same way.
Is the mobile phone better than freedom? Only when free enough to allow freedom to develop. In this case, financial cryptography is the general rubik, but economists would recognise the real linkage here: Free trade is freedom; the ability of Iraqis to avoid "going to the bank" when there's shooting outside is a life saver.
Literally, phone money saved their lives. In our fat&content western society, freed up payments won't save anyone's life, we're not in Mexico yet. But financial cryptography can shave a percentage point or two off of the price of *everything* because payments cost money and FC delivers those same things for a fraction of the costs.
And that you can take to the bank, or more importantly, back to the economy. Got a problem with growth? Install an FC plugin into your economy, and watch.
November 07, 2009
The War on Drugs moves to endgame: the War on US Americans
The decision to conduct a war on drugs was inevitably a decision to hollow-out Mexico. The notion of hollowing-out states is a time-honoured tradition in the Great Game, the way you control remote and wild places. The essential strategy is that you remove the institutions that keep places strong and stable, and bring them to a chaos which then keeps the countries fighting each other.
While they fight each other they are easier to control and extract value from. This is the favourite conspiracy theory behind the middle east and the famous Kissinger Deal: The Sheiks are propped up and given control of weak states as long as they trade their oil in dollars, and use the money to buy American goods. Of course we only speculate these details, and sometimes things look a little loose.
There are weaknesses in the strategy. Obviously, we are playing with fire when hollowing out a state ... so this is quite a lot of danger to the nearby states. (Which of course leads to the next part of the strategy, to play fire against fire and undermine an entire region.)
Which brings us to the War on Drugs and the decision to place Mexico into the role of hollowed-out state. John Robb points to this article:
Beheadings and amputations. Iraqi-style brutality, bribery, extortion, kidnapping, and murder. More than 7,200 dead-almost double last year's tally-in shoot-outs between federales and often better-armed drug cartels. This is modern Mexico, whose president, Felipe Calderón, has been struggling since 2006 to wrest his country from the grip of four powerful cartels and their estimated 100,000 foot soldiers.
 So, quite obviously if one understands the strategy, don't do this nearby. Do it far away. Reagan's famous decision to do this must have been taken on one his less memorable days ... no matter how the decision was taken on Mexico, now Reagan's chickens have cross the border to roost in mainland USA:
So, quite obviously if one understands the strategy, don't do this nearby. Do it far away. Reagan's famous decision to do this must have been taken on one his less memorable days ... no matter how the decision was taken on Mexico, now Reagan's chickens have cross the border to roost in mainland USA:
But chillingly, there are signs that one of the worst features of Mexico's war on drugs - law enforcement officials on the take from drug lords - is becoming an American problem as well. Most press accounts focus on the drug-related violence that has migrated north into the United States. Far less widely reported is the infiltration and corruption of American law enforcement, according to Robert Killebrew, a retired U.S. Army colonel and senior fellow at the Washington-based Center for a New American Security. "This is a national security problem that does not yet have a name," he wrote last fall in The National Strategy Forum Review. The drug lords, he tells me, are seeking to "hollow out our institutions, just as they have in Mexico."
Quite what is going on in these people's minds is unclear to me. The notion that it "has no name" is weird: it's the standard strategy with the standard caveat. They overdid the prescription, now the disease bounces back stronger, more immune, with a vengeance! Further, I don't actually think it is possible to ascribe this as a deliberate plot by the Mexican drug lords, because it is already present in the USA:
Experts disagree about how deep this rot runs. Some try to downplay the phenomenon, dismissing the law enforcement officials who have succumbed to bribes or intimidation from the drug cartels as a few bad apples. Peter Nuñez, a former U.S. attorney who lectures at the University of San Diego, says he does not believe that there has been a noticeable surge of cartel-related corruption along the border, partly because the FBI, which has been historically less corrupt than its state and local counterparts, has significantly ratcheted up its presence there. "It's harder to be as corrupt today as locals were in the 1970s, when there wasn't a federal agent around for hundreds of miles," he says.But Jason Ackleson, an associate professor of government at New Mexico State University, disagrees. "U.S. Customs and Border Protection is very alert to the problem," he tells me. "Their internal investigations caseload is going up, and there are other cases that are not being publicized." While corruption is not widespread, "if you increase the overall number of law enforcement officers as dramatically as we have| - from 9,000 border agents and inspectors prior to 9/11 to a planned 20,000 by the end of 2009 - "you increase the possibility of corruption due to the larger number of people exposed to it and tempted by it." Note, too, that Drug Enforcement Agency data suggest that Mexican cartels are operating in at least 230 American cities.
By that I mean, the drug situation has already corrupted large parts of the USA governance structure. I've personally heard of corruption stories in banks, politics, police and as far up the pecking order as FINCEN, intel agencies and other powerful agencies. As an outside observer it looks to me like they've made their peace with the drugs a long time ago, heaven knows what it looks like to a real insider.
So I see a certain sense of hubris in these writings. This feels to me that the professional journalist did not want to talk about the corruption that has always been there (e.g., how else did the stuff get distributed before?). What seems to be happening is that now that Mexico is labelled in the serious press (*) as hollowed-out, it has become easier to talk about the problem in mainstreet USA because we can cognitively blame the Mexicans. Indeed, the title of the piece is The Mexicanization of American Law Enforcement:
And David Shirk, director of the San Diego-based Trans-Border Institute and a political scientist at the University of San Diego, says that recent years have seen an "alarming" increase in the number of Department of Homeland Security personnel being investigated for possible corruption. "The number of cases filed against DHS agents in recent years is in the hundreds," says Shirk. "And that, obviously, is a potentially huge problem." An August 2009 investigation by the Associated Press supports his assessment. Based on records obtained under the Freedom of Information Act, court records, and interviews with sentenced agents, the AP concluded that more than 80 federal, state, and local border-control officials had been convicted of corruption-related crimes since 2007, soon after President Calderón launched his war on the cartels. Over the previous ten months, the AP data showed, 20 Customs and Border Protection agents alone had been charged with a corruption-related crime. If that pace continued, the reporters concluded, "the organization will set a new record for in-house corruption."
Well, whatever it takes. If the US-Americans have to blame the Mexican-Americans in order to focus on the real problems, that might be the cost of getting to the real solution: the end of Prohibition. Last word to Hayden, no stranger to hubris:
Michael Hayden, director of the Central Intelligence Agency under President George W. Bush, called the prospect of a narco-state in Mexico one of the gravest threats to American national security, second only to al-Qaida and on par with a nuclear-armed Iran. But the threat to American law enforcement is still often underestimated, say Christesen and other law enforcement officials.
* Mind you, I do not see how they are going to blame the Mexicans for the hollowing-out of the mainstream press. Perhaps the Canadians?
November 01, 2009
Gold bullion market set to implode?
I don't normally follow the gold talk because on the one hand it is the goldbugs saying "gold is set to explode" and on the other is a bunch of bankers that insult the noble metal, while on the backside buying & selling it short, naked and happy as fast as they can. That is, the story never changes.
Which in some senses is good. There has always been an expectation that gold would survive. So far nothing has changed to keep that expectation solid, with gold at $1000 an ounce, up from around $250 8 or 9 years ago.
But there is another aspect beyond the price: the market itself. As it happens, this is founded on a thing called "good delivery" bars run by LBMA (London Bullion Market Association), London being the center of the physical gold trading world. This is a good efficient and simple system which works like this: once your gold is "in" the LBMA good delivery programme, you can reliably ship it to any one of the vaults that are in, and sell it within. Deliver it out of LBMA-territory, and your gold loses its status. To put it in, it has to be tested, at some cost.
So, most of the physical retail gold that is traded (in bars) is inside the LBMA system. It's just easier to buy and sell when someone guarantees it. Which brings me to the point: Obviously, the guarantee can be wrong.
About 10 years ago the debate of unreliable LBMA bars erupted in the digital gold community, and we discovered at that time that the gold is not routinely checked in any way once it is in the system (not this). At all! I predicted then that this would mean the gold would slowly lose its integrity, as insiders raided it sliver-by-sliver, over the many many decades of its operation. It looks like I was right, from this post that JPM sent:
C) In an Asian depository, they've found "Good Delivery" bricks that had been gutted and filled with tungsten.
And predictably, the writer goes on to report "B) A number of large interests have demanded audits of gold stored in London."
 If you hold gold in the LBMA system, be worried. If you are an issuer of digital gold be very worried. Why? Because it looks like the gold markets are about to be tested. Not in price terms but in delivery terms. To summarise the long anti-markets rant by "marketskeptics" (a.k.a. Eric deCarbonnel):
If you hold gold in the LBMA system, be worried. If you are an issuer of digital gold be very worried. Why? Because it looks like the gold markets are about to be tested. Not in price terms but in delivery terms. To summarise the long anti-markets rant by "marketskeptics" (a.k.a. Eric deCarbonnel):
- Indians are shifting from buying gold jewellry to gold coins.
- China now actively promotes selling and holding of physical gold. That's the government, and every bank!
- Hong Kong and Dubai are pulling their physical gold out of London. German and Swiss investors and funds, likewise, and also demanding delivery out of the USA.
- There is now an overall trend to take physical delivery from metals facilities (vaults, exchanges, etc).
- Which has resulted in a rash of complaints ... which quickly become fingers pointed at possible collapse: delays, "complications", wrong bars, wrong weights, "restrictions", costs blossoming, etc.
- New York and Tokyo commodity exchanges are now permitting their gold futures contracts to be settled not in real metal but in shares of gold exchange-traded funds (ETFs)... NYSE-Liffe arbitrarily switched delivery of 1kg bars to ... notes on 1/3 interests in 100 ounce bars. If you can get three notes, you can take a 100 ounce!
- irregularities in bar amounts have surfaced at different places (e.g., Canadian Mint)
- Deutsche Bank may have recently closed out a gold shortage by buying it from the ECB and delivering it. Apparently, to the tune of 35.5 tons of gold, in one day! 12 days earlier someone shorted the same amount...
- gold banks (those big in the trade) are offering 25% over spot to settle in anything but physical gold.
 Have we got the message that physical gold now counts? If so, then one could wonder why open interest in gold trading on COMEX has since exploded? From August this year, it's jumped from a stable 1000-1100 tons band to around 1450. That's 40% up in a virtually traded commodity that is increasingly being demanded to convert to physical delivery! And, according to their reserves, it cannot be delivered: COMEX only holds 250t.
Have we got the message that physical gold now counts? If so, then one could wonder why open interest in gold trading on COMEX has since exploded? From August this year, it's jumped from a stable 1000-1100 tons band to around 1450. That's 40% up in a virtually traded commodity that is increasingly being demanded to convert to physical delivery! And, according to their reserves, it cannot be delivered: COMEX only holds 250t.
I wouldn't rule out a run on COMEX, and if so, it will likely collapse. That's because its reserves are a fraction of the open interest, so it looks highly vulnerable to being squeezed by the open traders (the "shorts") on one hand and the retail demands for physical delivery. Why won't the former deliver? Because for the most part they haven't got it; a short sale is generally a promise to acquire it when needed. In trading parlance, a lot more of the shorts are "naked shorts" which means they rely on a falling market (it's supposed to be illegal to be naked in a public trading, but a lot of markets look more like a nudist convention than a church meeting).
And we have a rising demand for physical, and a rising price in gold. So the squeeze happens this way: first the COMEX warehouse gets cleaned out. Then COMEX puts the squeeze on the short sellers to deliver their promise. Gold, physical, now. Which shorts then suddenly fold their cards, reveal their nakedness and declare mea culpa, I'm a nudist, so chase me. At some point, when enough of this goes on and is reported, the whole pyramid of cards collapses.
 What's the likelihood of this happening? I feel it is being tested at the moment. It will probably take a rash of more bad financial news to make it happen, faster than we can react. E.g., a couple of months of CITs or European unemployment figures. But it is possible, because the gold markets have not been divorced from the decades of corruption that brought down the other markets. More likely we will see a gradual shift out of COMEX, out of London and across to other gold exchanges; preferably ones outside the western/toxic asset belt, and ones that can more easily prove their reserves. Meanwhile, those who hang on will lose value. Someone has to pay for the frauds of the past.
What's the likelihood of this happening? I feel it is being tested at the moment. It will probably take a rash of more bad financial news to make it happen, faster than we can react. E.g., a couple of months of CITs or European unemployment figures. But it is possible, because the gold markets have not been divorced from the decades of corruption that brought down the other markets. More likely we will see a gradual shift out of COMEX, out of London and across to other gold exchanges; preferably ones outside the western/toxic asset belt, and ones that can more easily prove their reserves. Meanwhile, those who hang on will lose value. Someone has to pay for the frauds of the past.
It's definitely not easy to predict when something will happen. But it is possible to point to fundamental and powerful contradictory forces. And that's the situation right now with the markets in gold, if that post is reliable (it might not be, it's from a goldbug, after all!). I would suggest that if people want to speculate in the gold of any form right now, hold physical only. The rest is ... too uncertain in value. That's beyond speculation, that's gambling, only do that if you really enjoy the thrill of losing bar-worths of value.
(Note: one thing I loosely follow is goldmoney's blogs and posts from founder James Turk. He's just announced that Turk's long-running newsletter is now migrated online only, and for free.)
October 28, 2009
Councils engaged in "War on Rubbish Days" to thank the FATF for new seizure powers..
How the war on drugs has become the war on you is an ongoing topic. However, ordinary people would generally dismiss this as more ranting blogs and kooksterising. Until it happens, in which case we simply present the evidence and hope we don't get caught in the cross-fire. From Britain, spotted by Charon QC and noosphere:
Councils get ‘Al Capone’ power to seize assets over minor offencesDraconian police powers designed to deprive crime barons of luxury lifestyles are being extended to councils, quangos and agencies to use against the public, The Times has learnt. The right to search homes, seize cash, freeze bank accounts and confiscate property will be given to town hall officials and civilian investigators employed by organisations as diverse as Royal Mail, the Rural Payments Agency and Transport for London.
The measure, being pushed through by Alan Johnson, the Home Secretary, comes into force next week and will deploy some of the most powerful tools available to detectives against fare dodgers, families in arrears with council tax and other minor offenders. The radical extension of the Proceeds of Crime Act, through a Statutory Instrument which is not debated by parliament, has been condemned by the chairman of the Police Federation. ...
My reading of the article is that this is a done deal. In a new rendition of that old Chinese curse, be careful what you wish for, it seems that the police (Federation) are now opposed to the ill-thought-out extensions of seizure powers.
Paul McKeever said that he was shocked to learn that the decision to hand over “intrusive powers” to people who were not police was made without consultation or debate.“The Proceeds of Crime Act is a very powerful tool in the hands of police and police-related agencies and it shouldn’t be treated lightly,” Mr McKeever said. “There is a behind the scenes creep of powers occurring here and I think the public will be very surprised. They would want such very intrusive powers to be kept in the hands of warranted officers and other law enforcement bodies which are vetted to a very high standard rather than given to local councils.”
His concerns are shared by leading legal figures, who believe that there is a risk of local authorities abusing the powers to search people’s homes, seize their money, freeze their accounts and confiscate their property. They also see parallels with the spread of counter-terrorist surveillance powers to monitor refuse collections and school catchment areas.
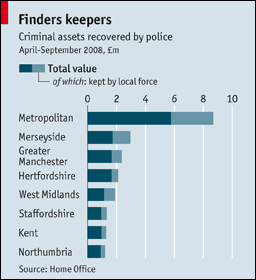 They're shocked now, but wait until the councils ask them for advice on how to meet new and rising Home Office profitability targets. Wait, I know! A new role for the FATF: business development for County Police, Local Councils and other stationary Princes.
They're shocked now, but wait until the councils ask them for advice on how to meet new and rising Home Office profitability targets. Wait, I know! A new role for the FATF: business development for County Police, Local Councils and other stationary Princes.
Wideranging confiscation powers were given to police and law enforcement bodies in 2003 to seize the cash and property from drug dealers, people-traffickers and money launderers. They were viewed as “Al Capone powers” — a means of getting at the Mr Bigs of organised crime by seizing wealth accrued from criminality. David Blunkett, then Home Secretary, said law enforcement was targeting “the homes, yachts, mansions and luxury cars of the crime barons”.The expansion of seizure powers is part of a Home Office plan to “embed” financial seizure across the criminal justice system. Ministers set a target to recover £250 million in criminal assets by 2010, rising to £1 billion per year soon after.
Three weeks ago I wrote where this was heading: Mexico. I gave it 20 years, and now it's 20 days later.
Put yourself in the shoes the Mr Bigs that this targets; do you think they are trembling in their evil boots at the thought of the rubbish police coming after them? Or, are they seeing new opportunities for corporate expansion? Or, are they worried they need to move fast to stake out the territory before the Mr Not-So-Big from across town gets a jump on them?
October 23, 2009
Microsoft: the new IBM?
 Microsoft has peaked and is on the way down. For those who watched the rise in the 1980s, and the domination in the 1990s, this is good news. It was a long wait.
Microsoft has peaked and is on the way down. For those who watched the rise in the 1980s, and the domination in the 1990s, this is good news. It was a long wait.
In the aftermath of the failure of Vista, there is of course a lot of hand-wringing. Some talk about security, notably following CEO Steve Ballmer's admission:
Mr Ballmer said: "We got some uneven reception when [Vista] first launched in large part because we made some design decisions to improve security at the expense of compatibility. I don't think from a word-of-mouth perspective we ever recovered from that."
Let's go back to the basics. As I described in previous posts, the problem is that Microsoft is sitting on a 20 year legacy of insecurity (e.g., 1). Bill Gates recognised that the pre-Internet design assumption was heading into stormy weather, and to his credit tried to turn it around.
But, it turns out that it is easier to turn around a Blackbird than a supertanker, and even Ballmer's legendary energy didn't substantially challenge the Newtonian physics. I have to hand it to them, at least they tried!
The point isn't whether Vista was sunk by security issues (Schneier), or whether it was sunk by marketing & direction failures (as suggested by Mordaxus). This is backwards thinking. The strategic picture is that security issues had to succeed in order to save Microsoft's dominant position.
The fact now clear is that Vista failed, and this has consequences for Microsoft. Firstly the security problem is still there; so they will still have to figure that one out. But secondly, it still means that anyone concerned with security over the last decade has now had a long time to discover the solution. For the most part it is a mixture of (a) stick with old/simpler Microsoft systems, (b) switch to Mac as highlighted on this blog, or (c) switch to other more reliable (==secure) technologies like web-based, cloud,, smart-phone etc. Thirdly, while Microsoft was grappling with the problem, the PC-to-Internet equation of the 1990s has shifted. It is now a much different place.
Ultimately, it means the end of dominance for Microsoft. Like the year 1989 for IBM, the emergence of the credible alternates is no longer just hopeful talk, it is concrete. And a big correction is needed, and as seen in the chart on market caps, the market has done that over the last decade.
But unlike IBM in 1989, Microsoft does seem to know its fate. Bill Gates is the King, and he sealed his legacy by signalling this pain in a really big way back in 2002. So instead of a mass riot, a run for the bank, a complete collapse of confidence as we saw in 1989, it looks like we are now heading to a more regularised market in IT. The big players are now all within striking distance of each other. They all have some particularly strong territory, they all can defend their territory, and they can all look a the new stuff and wonder if they can get in for some of it. The IT market is now interesting again.
Welcome to the next decade!
October 18, 2009
The new coin of the NSA is also the new coin of the economy
RAH sends around a review of a new book on the NSA. Just to underscore Chris's the energy thesis mentioned a few days ago, there is this enticing conclusion:
The issue is critical because at the NSA, electrical power is political power. In its top-secret world, the coin of the realm is the kilowatt. More electrical power ensures bigger data centers. Bigger data centers, in turn, generate a need for more access to phone calls and e-mail and, conversely, less privacy. The more data that comes in, the more reports flow out. And the more reports that flow out, the more political power for the agency.
And it isn't just the NSA. The Economist points out that the cash that 3 big players have to go to war with will be spent on data centers (and what you do in them, called Cloud computing in the current buzzword):
Full war chestsThis means that all three will have ample resources to spend in the main areas of the fight: data centres, cloud services and the periphery. In data centres, Google is ahead, but Microsoft is catching up in size and sophistication. Apple has most to learn, but this, too, seems only a question of time and money. Just as much of hardware has become a commodity, knowing how to build huge data centres may not be a big competitive advantage for long. And data centres can get only so big before scale ceases to be an advantage.
So you need lots of them, like google's three dozen. Where to build? You build them where the tech people are (because you want lots of technical employees who can drive in and press reset buttons on google's 2 million servers...) and you build them where energy is cheap. E.g., the cutely-named Apple-Google Power Corridor is located in North Carolina's "Research Triangle", a tech-university area located at twin cities of Raleigh/Durham. So they've got the personnel base, and:
“We’ve been working together with pofficials [sic?] from Caldwell County to market this idea for several years,” said Millar. “Duke Energy serves both sites, and is competitive with its pricing,” which is typically between 4 and 5 cents a kilowatt hour for industrial customers.“One of the things that’s driving the competitiveness of our area is the power capacity built for manufacturers in the past 50 years,” said Millar. “Having that capacity and those redundancies has helped the region. We’ve got other sites and other buildings ready to go as well.”
They've got the energy! Power, of the energy form, underpins the new economy. Energy economics might not be a new idea: it supports China's booming economy (see chart at bottom). So whatever one thinks about the USA's politics of dabbling around from the Middle East to China, playing the Great Game in the energy belt, there are correlations of importance there.
The negotiations are part of a longstanding effort by the West to try to halt Iran’s nuclear program, which many in the West say is geared toward producing weapons. Iran says the program is designed to generate energy.
Geographically, politically and economically, a new currency based on the kWh is not an outlandish idea.
October 16, 2009
The Elliot Wave has arrived at stage 5, so it's all over for the dollar!
I just had to write about this one:
The greenback is heading for the trough of a super-cycle that started in August 1971, Uno said, referring to the Elliot Wave theory, which holds that market swings follow a predictable five-stage pattern of three steps forward, two steps back.The dollar is now at wave five of the 40-year cycle, Uno said. It dropped to 92 yen during wave one that ended in March 1973. The dollar will target 50 yen during the current wave, based on multiplying 92 with 0.764, a number in the Fibonacci sequence, and subtracting from the 123.17 yen level seen in the second quarter of 2007, according to Uno.
The Elliot Wave was developed by accountant Ralph Nelson Elliott during the Great Depression. Wave sizes are often related by a series of numbers known as the Fibonacci sequence, pioneered by 13th century mathematician Leonardo Pisano, who discerned them from proportions found in nature.
! Well, I'll bet all the technical traders are packing up their books and retiring, now that they've heard this news.
More seriously, the problem with fundamental analysis (like the above) is that although it can be very right, it can also be very hard to time. Point in fact, I predicted the shift in the dollar (and so did a lot of others). But I predicted it around 2001, and it just didn't happen according to any schedule I could see. So this information is interesting but relatively worthless on a daily basis.
On the other hand, the technical trader works to patterns. To scientists this seems more like voodoo or interpreting the future from chicken entrails, and to all objective metrics it is like that. But the technical traders swear by it, and they promise it makes them money.
What's the truth? I think it is clear that complexity is such that fundamentals can't be time-predicted so easily. Which means that day-to-day is unpredictable, being the random walk. But something has to happen (never forget the Stiglitz observation), and it happens in the minds of the traders. Ideas for patterns emerge: cat droppings & bouncings, peaks & troughs, decision points. The ideas that are consistent over time are probably decided by the efficiency of meme-spreading more than anything else, which then leads to the patterns becoming self-confirming.
So where are we heading? Well, the dollar is no longer the undisputed champion. But it will still retain leadership for some time, a steady decline into a more dispersed market. People talk about alternates:
Uno said after the dollar loses its reserve currency status, the U.S., Europe and Asia will form separate economic blocs. The International Monetary Fund’s special drawing rights may be used as a temporary measure, and global currency trading will shrink in the long run, he said.
But that doesn't make sense; as Chris says:
As a bear of little economic brain but with market experience approaching 25 years, I prefer to deal with the practical, rather than the theoretical. I observe that the transaction currency is relatively unimportant, because the foreign exchange market allows an alternative currency to be used in a microsecond. What matters is, for a consumer, the capability to make future payments in the transaction currency; and for a producer, where and in what currency and asset class the proceeds of sale may be invested.
Right.
I propose an entirely different approach, and that is to distinguish between the value standard we use, and the currencies we exchange by reference to the standard.Firstly, a fixed amount of energy - for instance the energy value of a liter of gasoline, or its equivalent in kilowatt hours - would be intuitively obvious as a pricing reference. Most people could relate to that, and whether the unit is called a petro, electro, or an energy dollar is irrelevant.
Secondly, there is the need for nationally and globally acceptable units of currency as a store of value. A unit redeemable in land rental value could perhaps be a nationally acceptable currency, but for international acceptance or "fungibility" the obvious candidates are electricity, which is pure energy, and carbon-based fuels, such as natural gas, gasoline, kerosene, heating oil and fuel oil.
If a new force is to emerge, it won't be a political unit like the IMF's accounting thing, nor will it be a historical thing like gold, but will be backed by something substantial. Energy is one universal, and if anything it is going up in value and demand, not down (so it doesn't equate to Moore's law or technology reductions, nor to natural commodity pricing).
But also, we should be very important not to attach the dollar's pain to the American Economy. Although it will suffer one hell of a hangover, bear in mind this observation from the Economist:
Only one thing seems sure about the future of the digital skies: the company or companies that dominate it will be American. European or Asian firms have yet to make much of an appearance in cloud computing. Nokia, the world’s biggest handset-maker, is trying to form a cloud with its set of online services called Ovi, but its efforts are still in their infancy. Governments outside America may harbour ambitious plans for state-funded clouds. They would do better simply to let their citizens make the most of the competition among the American colossi.
Practically all new value is created in North America. They may have sacrificed their dollar over the irrational exuberance, but the attitudes in creating new value run deep; Europe can't do it, and most all other new countries copy the essential model of post WWII Japan: copy and out-perform.
(So much for a quick post!)
October 13, 2009
Hard(er) data on the big shift for the dollar
Following last week's post on the "sneak attack on the dollar," here is some harder news from today's Lynn'o'gram. From Forbes:
Steven Englander, chief U.S. currency strategist at Barclays ( BCS - news - people ) Capital says it is the culmination of what currency traders have feared for some time now. In the second quarter central banks put just 37% of assets into dollars. Typically, banks invest 70% of their assets in the greenback."No one wants to be caught holding too many dollars," Englander said, "and this rising reluctance is increasing pressure on the U.S. dollar." Englander noted that the second quarter was the only time that central banks have accumulated more than $100 billion of reserves in the quarter, and the dollar's share of this accumulate has been less than 40%.
He also noted that this period was also the only time the euro has accounted for more than 50% of the accumulation when central banks, in aggregate, have accumulated more than $80 billion. Furthermore, the yen's share of the increase in reserves was 12%, by far the highest incremental share since 2005. "The drop in aggregate reserves in the fourth quarter of 2008 and the first quarter of 2009 was almost all U.S. dollar, but the recovery has been primarily in non-U.S. dollar reserves," Englander said.
 From Bloomberg and the "picture is worth a 1000 words" school:
From Bloomberg and the "picture is worth a 1000 words" school:
The CHART OF THE DAY shows the percentage of allocated world currency reserves in dollars has fallen as holdings in euros increased in the past decade, according to quarterly data compiled by the International Monetary Fund.
But you have to click and go there ... for the chart. It shows that euro reserve has risen from 18% to 29% over the last decade, meaning that dollar reserve has shrunk from 70% to 60%. Very approx, eyeball method. Elsewhere it says that chart covers 63% of the total reserves of central banks, as some reserves such as China's aren't reported.
In summary, it seems that most of the shift occurred around 2002 to 2003, but now there is a sudden leap in this last quarter.
“Global central banks are getting more serious about diversification, whereas in the past they used to just talk about it,” said Steven Englander,
Well, not quite all. The Europeans are still just talking:
The economies of both Japan and Europe depend on exports that get more expensive whenever the greenback slumps. European Central Bank President Jean-Claude Trichet said in Venice on Oct. 8 that U.S. policy makers’ preference for a strong dollar is “extremely important in the present circumstances.”
Here's an idea: why don't Japan and Europe trade with each other, and avoid the problem? Gosh.... Finally, to remind us that sentiment is an issue:
“People didn’t like the dollar in 1995,” said Taylor, whose firm has $9 billion under management. “That was very stupid and turned out to be wrong. Now, we are getting to the point that people’s attitude toward the dollar becomes ridiculously negative.”
To live contrarian, buy the dollar. Postscript from FC in 2006 for some old predictions of what this means:
Let's do the maths, so as to explain why this is significant. If we take the shift as from 60% to 50%, allowing euros to rise from 30% to 40%, then we see a relative shift in USD demand of say 20%. Call it over 2 years, and we can guess at a shift of 10% per year in the total international currency use of USD.If all countries are doing this - and there are good game theory, trade and geopolitical reasons to suspect this - then we see a massive washing around the world of some 10% of the USD during the space of a year. This will go on until we reach a new stability, a level which is anyone's guess at the moment
Just in case you're sacking your fundamentals analysts at the moment and need help...
October 12, 2009
How the FATF brought down modern civilisation and sent us all to retire in Mexico
 Nobody likes criminals. Even criminals don't like criminals; they are unfair competition.
Nobody likes criminals. Even criminals don't like criminals; they are unfair competition.
So it is with some satisfaction that our civilisation has worked for a 1000 years to suppress the criminal within; going back to the Magna Carta where the institution of the monarch was first separated from the money making classes, and the criminal classes, both. Over time, this genesis was developed to create the rights of the people to hold assets, and the government as firmly oriented to defending those rights.
One of those hallowed principles was that of consolidated revenue. This boring, dusty old thing was a foundation for honest government because it stopped any particular agency from becoming a profitable affair. That is, no longer government for the people, but one of the money making or money stealing classes mentioned above.
Consolidated Revenue is really simple: all monies collected go to the Treasury and are from there distributed according to the budget process. Hence, all monies collected, for whatever purpose, are done so on a policy basis, and are checked by the entire organisation. If you have Budget Day in your country, that means the entire electorate. Which latter, if unhappy, throws the whole sorry group out on the streets every electoral cycle, and puts an entirely new group in to manage the people's money.
This simple rule separates the government from the profit-making classes and the criminal classes. Break it at your peril.
Which brings us to the FATF, the rot within modern civilisation. This Paris-based body with the soft and safe title of "Financial Action Task Force" deals with something called money laundering. Technically, money laundering exists and there is little dispute about this; criminals need a way to turn their ill-gotten gains into profit. When criminals get big, they need to turn a lot of bad money into good money. So part of the game for the big boys was to set up large businesses that could wash a lot of money. It is called laundering, and washing because the first large-scale money-cleansing businesses were launderies or launderettes: shops with coin-operated washing machines, which took lots and lots of cash, in a more or less invisible fashion. Etc etc, this is all well known, undisputed, a history full of colour.
What is much more disputable is how to deal with it. And this is where the FATF took us on the rather short path to a long stay in hell. Their prescription was simple: seize the money, and keep it. It is indeed as simple as the law of Consolidated Revenue. Which they then proceeded to break, as well, in their innocence and goodliness.
The Economist reports on how far Britain, a leader in this race to disaster, has come in 30 short years it has taken to unravel centuries of governance:

The public sale of criminals' property, usually through auction houses or salvage merchants, has been big business for a long time. The goods are those that crooks have acquired legitimately but with dirty money, as opposed to actual stolen property, which the police must try to reunite with its rightful owners. Half the proceeds go to the Home Office, and the rest to the police, prosecutors and courts. The bigger police forces cream off millions of pounds a year in this way (see chart).
So if a crook steals goods, the police work for the victim. But if a crook makes money by any other means, the police no longer works for the victim, but for itself. We now have the Home Office, the prosecutors, the courts, and the humble British Bobby well incentivised to promote money laundering in all its guises. Note that the profit margin in this business is *well in excess of standard business rates of return* and we will then have no surprise at all that the business of legal money laundering is booming:
Powers to confiscate criminals' ill-gotten gains have grown steadily. A drugs case in 1978, in which the courts were unable to strip the traffickers of £750,000 of profits, caused Parliament to pass asset-seizure laws that applied first to drug dealers, and then more widely. The 2002 Proceeds of Crime Act expanded these powers greatly, allowing courts to seize more or less anything owned by a convict deemed to have a "criminal lifestyle", and introducing a power of civil recovery, whereby assets may be confiscated through the civil courts even if their owner has not been convicted of a crime.
Everyone's happy with that of course! (Read the last two paragraphs for a good, honest middle-class belly laugh.) Of course, the normal argument is that the police are the good guys, and they do the right thing. And if you oppose them, you must be a criminal! Or, you like criminals or benefit from criminals or in some way, you are dirty like a criminal.
And such it is. This is the sort of thought level that characterizes the discussion, and is frequently brought up by supporters of the money laundering programmes. It's also remarkably similar to the rhetoric leading up to most bad wars (who said "you're either with us or against us?"), pogroms and other crimes against civilisation.
Serious students of economics and society can do better. Let's follow the money:
Since then, police cupboards have filled up fast. Confiscations of criminal proceeds in 2001-02 amounted to just £25m; in 2007-08 they were £136m, and the Home Office has set a goal of £250m for the current financial year. To meet this, new powers are planned: a bill before parliament would allow property to be seized from people who have been arrested but not yet charged, though it would still not be sold until conviction. This, police hope, will prevent criminals from disposing of their assets during the trial.
This is the standard evolution of a new product cycle in profitable business. First, mine the easy gold that is right there in front of you. Next, develop variations to increase revenues. Third, institute good management techniques to reduce wastage. The Home Office is setting planning targets for profit raising, and searching for more revenue. The government has burst its chains of public service and is now muckraking with the rest of the dirty money-grubbing corporates, and is now in a deadly embrace of profitability with the dirty criminal classes.
 All because the legislature forgot the fundamental laws of governance!
All because the legislature forgot the fundamental laws of governance!
Can the British electorate possibly reel in this insatiable tiger, now they've incentivised it to chase and seize profit? Probably not. But, "surely that doesn't matter," cry the middle-class masses, safe in their suburban homes? Surely the police would never cross the NEXT line and become the criminals, seizing money and assets that was not ill-gotten?
Don't be so sure. There is enough anecdotal evidence in the USA (1) that this is routine and regular. And unchallenged. It will happen in Britain, and if it goes unchallenged, the next step will become institutionalised: deliberate targetting of quasi-criminal behaviour for revenue raising purposes. Perhaps you've already seen it: are speeding fines collected on wide open motorways, or in danger spots?
The FATF have broken the laws of civilisation, and now we are at the point where the evidence of the profit-making police-not-yet-gang is before us. The Economist's article is nearly sarcastic .. uncomfortable with this immoral behaviour, but not yet daring to name the wash within Whitehall. Reading between the lines of that article, it is both admiring of the management potential of the Home Office (should we advise them to get an MBA?), and deeply disgusted. As only an economist can be, when it sees the road to hell.
Britain stands at the cusp. What do we see when we look down?
We see Mexico, the country that Ronald Reagan hollowed out. That late great President of the USA had one massive black mark on his career, which is a cross for us all to bear, now that he's skipped off to heaven.
 Ronald Reagan created the War on Drugs, which was America's part in the FATF alliance. It was called "War" for marketing reasons: nobody criticises the patriotic warriors, nobody dare challenge their excesses. This was another stupidity, another breach of the natural laws of civilisation (separation of powers, or in USA, this might be better known as the destruction of the Posse Comitatus Act). This process took the "War" down south of the border, and turned the Mexican political parties, judiciary, police force and other powerful institutions into victims of Ronald Reagan's "War". From a police perspective, Mexico was already hollowed out last decade; what we are seeing in the current decade is the hollowing out of the Army. The carving up of battalions and divisions into the various gangs that control the flow of hot-demand items to from the poor south to the rich north of the Americas.
Ronald Reagan created the War on Drugs, which was America's part in the FATF alliance. It was called "War" for marketing reasons: nobody criticises the patriotic warriors, nobody dare challenge their excesses. This was another stupidity, another breach of the natural laws of civilisation (separation of powers, or in USA, this might be better known as the destruction of the Posse Comitatus Act). This process took the "War" down south of the border, and turned the Mexican political parties, judiciary, police force and other powerful institutions into victims of Ronald Reagan's "War". From a police perspective, Mexico was already hollowed out last decade; what we are seeing in the current decade is the hollowing out of the Army. The carving up of battalions and divisions into the various gangs that control the flow of hot-demand items to from the poor south to the rich north of the Americas.
When considering these issues, and our Future in Mexico, there are several choices.
The really sensible one would be to shut down the FATF and its entire disastrous experiment. Tar&feather anyone involved with them, run them out of town backwards on a donkey, preferably to a remote spot in the Pacific, with or without speck of land. The FATF are irreparable, convinced that they are the good guys, and can do no wrong. But politically, this is unlikely, because it would damn the politicians of a generation for adopting childish logic while on duty before the public. And the FATF's influence is deep within the regulatory and financial structure, everyone will be reminded that "you backed us then, you don't want people to think you're wrong..." Nobody will admit the failure, nobody will say «¡Discuplanos!» to the Mexican pueblo for depriving them of honest policing and a civilised life.
 The simple choice is to go back to our civilised roots and impose the principle of Consolidated Revenue back into law. In this model, the Home Office should have its business permit taken away from it, and budget control be restored. The Leicestershire Constabulary should be raided by Treasury and have its eBay and Paypal accounts seized, like any other financial misfits. This is the Al Capone solution, which nobody is comfortable with, because it admits we can't deal with the problem properly. But it does seem to be the only practical solution of a very bad lot.
The simple choice is to go back to our civilised roots and impose the principle of Consolidated Revenue back into law. In this model, the Home Office should have its business permit taken away from it, and budget control be restored. The Leicestershire Constabulary should be raided by Treasury and have its eBay and Paypal accounts seized, like any other financial misfits. This is the Al Capone solution, which nobody is comfortable with, because it admits we can't deal with the problem properly. But it does seem to be the only practical solution of a very bad lot.
Or we choose to go to Mexico. Step by step, slowly but in our lifetimes. It took 20 years to hollow out Mexico, we have a bit longer in other countries, because the institutions are staffed by stiffer, better educated people.
But not that long. That is the thing about the natural laws: breach them, and the policing power of the economy will come down on you eventually. The margins on the business of sharing out ill-gotten gains are way stronger than any principled approach to policing or governance can deal with. I'd give it another 20 years for Britain to get to where Mexico is now.
October 09, 2009
Washington DC discovers new economic force: the World
Compelling evidence that FinancialCryptography.com is not deeply read in Washington DC arrived with this fascinating article:
It’s the biggest mystery in global finance right now: Who conducted a sneak attack on the U.S. dollar this week?It began with a thinly sourced but highly explosive report Monday in a British newspaper: Arab oil sheiks are conspiring with the Russians and Chinese to quit using the dollar to set the value of oil trades — a direct threat to the global supremacy of the greenback.
Is it true? Everyone from the head of the Saudi central bank to U.S. officials scrambled to undercut the story, but no matter.
Wakeup America? The collapse of the dollar was first heralded around 2001. The clue was the weaker-than-deserved crash after the dotcom era. Then, as evidence continued to pile in that the Fed was managing the US crises and economy too nicely, and the President was spending too many of the toys chasing towelheads and oil in Asia, the idea of a shift from dollar hegemony to multiple leading units went from theory to inevitability.
War Against the Dollar, the Pillar of United States PowerWhatever happens, Washington can no longer backtrack. In fact, the survival of the U.S. is menaced - not by an external enemy, but by internal economic weakness and tensions running between its communities. Many are becoming conscious of the fact that U.S. power is based upon a mirage, the dollar. These are only pieces of paper, printed when more are needed, while the rest of the world feels obliged to use them.
For the past three years, Jacques Chirac and Gerhard Schroder have engaged France and Germany in a pitiless war against the United States. They have sent emissaries world wide to convince other States to convert their monetary reserves to euros. The first to accept were Iran, Iraq and North Korea. Precisely the countries described by George W. Bush as those of the "axis of evil".
Meanwhile, Vladimir Putin has begun restoring the economic independence of the Russian Federation. He has reimbursed - ahead of time - the debts that Yeltsin had contracted with the International Monetary Fund and will also make an early repayment, before the end of the year, of the remaining debts to the Club of Paris.
That was 2003. It was reported here, not because we like poking fun at the Yanks, but because a monetary shift of this proportion is HUGE. Such a shift passes as news, except in Washington DC of course, where it's a sneak attack! The evidence in monetary terms was compelling enough to make it not only hypothesis but a clear progression; this blog reported it at least a dozen times back to 2003 (when the blog started. E.g.: 2008, x, x, x, x, The Coming Collapse of the Dollar, x, x, x, x, x, 2004).
Meanwhile, back in Washington DC, where the brightest and best are analysing this surprising development:
For American officials, the possibility of the dollar losing its long-term dominance in global commerce is a nightmare scenario because it would likely mean sharply higher interest rates at home and a declining ability to finance the U.S. debt. No one believes it could really happen right now, but stories like the British report this week make it seem incrementally more likely.
Reading the article, I get the feeling that because the report is British, it isn't credible. And Fisk, the author, is apparently a radical who consorts with Osama bin Laden. That's good news for us here in financialcryptography. That means it is not personal, the people in Washington DC don't read anything from outside their borders....
And so the USA seals its fate. With analysis like that, American policy is apparently immune from forces beyond the board, even when triggered from within.

In other news, President Obama was awarded the Nobel Peace Prize, which comes with a gold medal. Going up in value every day...
If he can save the dollar, he could be in line for another gold coin. He's probably too late this year as the Prize in Economics, in memorium of Alfred Nobel, will be awarded this Monday. But there's always next year.
September 25, 2009
Where does anyone (young) want to go, today?
I got some good criticism on the post about accounting as a profession. Clive said this which I thought I'd share:
As an engineer who's father was an accountant I will give you three guesses as to what he told me not to do when I grew up... Oddly it is the same for engineers, we tend to tell our children to do other things. As I've said before if you want to get on in life you should learn to speak the language that the man who cuts your cheque at the end of the month does, or more correctly his boss ;)So even if you are just a humble team leader get yourself three courses,
- MBA,
- Vocal training,
- Psychology or Method acting.
And no I'm not joking about 3.
He's talking about what we do when we get to 30 and beyond, e.g., most readers of this blog. For us older folks looking back, it is depressing that the world looks so sucky; but this is a time-honoured thing. The myths have been stripped away, the rot revealed.
But the youth of today is perpetually optimistic, and the question they ask is eternal and (Spence-like) opinionated: what to study, first?
What then do we recommend for a first degree for someone near 20? It seems that nobody promotes the accountancy field, including the incumbents. Accountants don't practice accountancy, if they are any good. The only accountant I ever knew well committed suicide.
An MBA doesn't work, this is something that should be done after around 5-10 years of experience. Hence, I'm not convinced a straight business degree ("Bachelors in Business Studies" ?) makes sense either, because all that additional stuff doesn't add value until experience is there to help it click into place.
I wouldn't suggest economics. It is like law and accounting, in that it helps to provide a very valuable perspective throughout higher business planes. But it doesn't get you jobs, and it is too divorced from practical life, too hard to apply in detail. Engineering seems far too specialised these days, and a lot of it is hard to work in and subject to outsourcing. Science is like engineering but without the focus.
To my mind, the leading contenders as a first degree are (in no particular order):
⇒ law,
⇒ computer science,
⇒ biotech, and
⇒ marketing.
Firstly, they seem to get you jobs; secondly, law, compsci and marketing are easy to apply generally and broadly, and pay dividends throughout life. I'm not quiet sure about Biotech in the "broad" sense, but it is the next big thing, it is the wave to ride in.
Comp sci was the wave of the 1980s and 1990s. Now it is routine. Any technical degree these days tends to include a lot of comp sci, so if there is a tech you enjoy, do that degree and turn it into a comp sci degree on the inside.
 Law is in my list because it is the ultimate defensive strategy. Headline Law tends to offend with its aggressively self-serving guild behaviour ("a man who represents himself has a fool for a client and a fool for a lawyer") and as a direct practice (courts) the field seems made for crooks. More technically, all disputes are win-lose by definition, and therefore litigation is destructive by definition, not productive. This is offensive to most of humanity.
Law is in my list because it is the ultimate defensive strategy. Headline Law tends to offend with its aggressively self-serving guild behaviour ("a man who represents himself has a fool for a client and a fool for a lawyer") and as a direct practice (courts) the field seems made for crooks. More technically, all disputes are win-lose by definition, and therefore litigation is destructive by definition, not productive. This is offensive to most of humanity.
But litigation is only the headline, there are other areas. You can apply the practical aspects of law in any job or business, and you can much more easily defend yourself and your business against your future fall, if you have a good understanding of the weapons of mutual destruction (a.k.a. lawsuits). About half of the business failures I've seen have occurred because there was no good legal advisor on the team; this is especially true of financial cryptography which is why I've had to pick up some of it; what one person I know calls "bush lawyering."
The downside to studying law is that you can lose your soul. But actually the mythology in law is not so bad because it is grounded in fundamental rights, so keep those in mind, and don't practice afterwards. It's nowhere near as bad as the computing scene (no grounding at all, e.g., open source) or the marketing blah blah (your mission is to unground other's perceptions!).
Marketing is there because every successful business needs it, and you can only be successful with it. MBAs are full of marketing, which reflects its centrality (and also gives a good option for picking it up later). But marketing is also dangerous because it gives you the tools to fool yourself and all around you, and once you've become accustomed to the elixir, your own grounding is at risk.
I don't advise any of the arts (including Clive's points 2,3) as a primary degree for youth, because businesses hire on substance, so it is important to have some to offer. E.g., people who study psychology tend to end up doing HR ("human resources"), badly, perhaps because they lack the marketing sense to make HR the most important part of the business.
Likewise, avoid anything that is popular, soft, fun, nice and that all your touchy-feely friends want to do. When there are too many people and too little substance, the competition suppresses everyone and makes you all poor. That's the best result because at least it is honest; a very few dishonest ones become rich because they figure out the game. The notion that you can study acting, media, history, photography or any of the finer arts, and then make a living, doesn't bear talking about. It is literally gambling with lives, and has no place in advice to young people.
September 18, 2009
Where does the accounting profession want to go, today?
 So, if they are not doing audits and accounting, where does the accounting profession want to go? Perhaps unwittingly, TOdd provided the answer with that reference to the book Accounting Education: Charting the Course through a Perilous Future by W. Steve Albrecht and Robert J. Sack.
So, if they are not doing audits and accounting, where does the accounting profession want to go? Perhaps unwittingly, TOdd provided the answer with that reference to the book Accounting Education: Charting the Course through a Perilous Future by W. Steve Albrecht and Robert J. Sack.
It seems that Messrs Albrecht and Sack, the authors of that book, took the question of the future of Accounting seriously:
Sales experts long ago concluded that "word of mouth" and "personal testimonials" are the best types of advertising. The Taylor Group1 found this to be true when they asked high school and college students what they intended to study in college. Their study found that students were more likely to major in accounting if they knew someone, such as a friend or relative, who was an accountant.
So they tested it by asking a slightly more revealing question of the accounting professionals:
When asked "If you could prepare for your professional career by starting college over again today, which of the following would you be most likely to do?" the responses were as follows:
Type of Degree % of Educators Who Would % of Practitioners Who Would Who Would Earn a bachelor's degree in something other than accounting and then stop 0.0 7.8 Earn a bachelor's degree in accounting, then stop 4.3 6.4 Earn a Master's of Business Administration (M.B.A.) degree 37.7 36.4 Earn a Master's of Accountancy degree 31.5 5.9 Earn a Master's of Information Systems degree 17.9 21.3 Earn a master's degree in something else 5.4 6.4 Earn a Ph.D. 1.6 4.4 Earn a J.D. (law degree) 1.6 11.4 These results are frightening,...
Well indeed! As they say:
It is telling that six times as many practicing accountants would get an M.B.A. as would an M.Acc., over three times as many practitioners would get a Master's of Information Systems degree as would get an M.Acc., and nearly twice as many practitioners would get a law degree instead of an M.Acc. Together, only 12.3 percent (6.4% + 5.9%) of practitioners would get either an undergraduate or graduate degree in accounting.2 This decrease in the perceived value of accounting degrees by practitioners is captured in the following quotes:We asked a financial executive what advice he would give to a student who wanted to emulate his career. We asked him if he would recommend a M.Acc. degree. He said, "No, I think it had better be broad. Students should be studying other courses and not just taking as many accounting courses as possible. ...My job right now is no longer putting numbers together. I do more analysis. My finance skills and my M.B.A. come into play a lot more than my CPA skills.
.... we are creating a new course of study that will combine accounting and
information technology into one unique major.......I want to learn about information systems.
(Of course I'm snipping out the relevant parts for speed, you should read the whole lot.) Now, we could of course be skeptical because we know computing is the big thing, it's the first addition to the old list of Reading, Arithmetic and Writing since the dark ages. Saying that Computing is core is cliche these days. But the above message goes further, it's almost saying that Accountants are better off not doing accounting!
The Accounting profession of course can be relied upon to market their profession. Or can they? Todd was on point when he mentioned the value chain, the image in yesterday's post. Let's look at the wider context of the pretty picture:
Robert Elliott, KPMG partner and current chairman of the AICPA, speaks often about the value that accountants can and should provide. He identifies five stages of the "value chain" of information. The first stage is recording business events. The second stage is summarizing recorded events into usable data. The third stage is manipulating the data to provide useful information. The fourth stage is converting the information to knowledge that is helpful to decision makers. The fifth and final stage is using the knowledge to make value-added decisions. He uses the following diagram to illustrate this value chain:This five-stage breakdown is a helpful analysis of the information process. However, the frightening part of Mr. Elliott's analysis is his judgment as to what the segments of the value chain are worth in today's world. Because of the impact of technology, he believes that:
- Stage 1 activity is now worth no more than $10 per hour
- Stage 2 activity is now worth no more than $30 per hour
- Stage 3 activity is now worth $100 per hour
- Stage 4 activity is now worth $300 per hour
- Stage 5 activity is now worth $1,000 per hour
In discussing this value chain, Mr. Elliott urges the practice community to focus on upper-end services, and he urges us to prepare our students so they aim toward that goal as well. Historically, accounting education has prepared students to perform stage 1- and stage 2-type work.
Boom! This is compelling evidence. It might not mean that the profession has abandoned accounting completely. But it does mean that whatever they do, they simply don't care about it. Accounting, and its cousin Audits are loss-leaders for the other stuff, and eyes are firmly fixed on other, higher things. We might call the other stuff Consulting, and we might wonder at the correlation: consulting activities have consumed the major audit firms. There are no major audit firms any more, there are major consulting firms, some of which seem to sport a vestigial audit capability.
Robert Elliot's message is, more or less, that the audit's fundamental purpose in life is to urge accountancy firms into higher stages. It therefore matters not what the quality (high?) is, nor what the original purpose is (delivering a report for reliance by the external stakeholder?). We might argue for example whether audit is Stage 2 or Stage 3. But we know that the auditor doesn't express his opinion to the company, directly, and knowledge is the essence of the value chain. By the rules, he maintains independence, his opinion is reserved for outsiders. So audit is limited to Stages 3 and below, by its definition.
Can you see a "stage 4,5 sales opportunity" here?
Or perhaps more on point, can you avoid it?
It is now very clear where the auditors are. They're not "on audit" but somewhere higher. Consulting. MBA territory. Stage 5, please! The question is not where the accounting profession wants to go today, because they already got there, yesterday. The financial crisis thesis is confirmed. Audits are very much part of our problem, even if they are the accounting profession's solution.
What is less clear is where are we, the business world? The clients, the users, the reliers of audit product? And perhaps the question for us really is, what are we going to do about it?
July 15, 2009
trouble in PKI land
The CA and PKI business is busy this week. CAcert, a community Certification Authority, has a special general meeting to resolve the trauma of the collapse of their audit process. Depending on who you ask, my resignation as auditor was either the symptom or the cause.
In my opinion, the process wasn't working, so now I'm switching to the other side of the tracks. I'll work to get the audit done from the inside. Whether it will be faster or easier this way is difficult to say, we only get to run the experiment once.
Meanwhile, Mike Zusman and Alex Sotirov are claiming to have breached the EV green bar thing used by some higher end websites. No details available yet, it's the normal tease before a BlabHat style presentation by academics. Rumour has it that they've exploited weaknesses in the browsers. Some details emerging:
With control of the DNS for the access point, the attackers can establish their machines as men-in-the-middle, monitoring what victims logged into the access point are up to. They can let victims connect to EV SSL sites - turning the address bars green. Subsequently, they can redirect the connection to a DV SSL sessions under a certificates they have gotten illicitly, but the browser will still show the green bar.
Ah that old chestnut: if you slice your site down the middle and do security on the left and no or lesser security on the right, guess where the attacker comes in? Not the left or the right, but up the middle, between the two. He exploits the gap. Which is why elsewhere, we say "there is only one mode and it is secure."
Aside from that, this is an interesting data point. It might be considered that this is proof that the process is working (following the GP theory), or it might be proof that the process is broken (following the sleeping-dogs-lie model of security).
Although EV represents a good documentation of what the USA/Canada region (not Europe) would subscribe as "best practices," it fails in some disappointing ways. And in some ways it has made matters worse. Here's one: because the closed proprietary group CA/B Forum didn't really agree to fix the real problems, those real problems are still there. As Extended Validation has held itself up as a sort of gold standard, this means that attackers now have something fun to focus on. We all knew that SSL was sort of facade-ware in the real security game, and didn't bother to mention it. But now that the bigger CAs have bought into the marketing campaign, they'll get a steady stream of attention from academics and press.
I would guess less so from real attackers, because there are easier pickings elsewhere, but maybe I'm wrong:
"From May to June 2009 the total number of fraudulent website URLs using VeriSign SSL certificates represented 26% of all SSL certificate attacks, while the previous six months presented only a single occurrence," Raza wrote on the Symantec Security blogs.... MarkMonitor found more than 7,300 domains exploited four top U.S. and international bank brands with 16% of them registered since September 2008.
.... But in the latest spate of phishing attempts, the SSL certificates were legitimate because "they matched the URL of the fake pages that were mimicking the target brands," Raza wrote.VeriSign Inc., which sells SSL certificates, points out that SSL certificate fraud currently represents a tiny percentage of overall phishing attacks. Only two domains, and two VeriSign certificates were compromised in the attacks identified by Symantec, which targeted seven different brands.
"This activity falls well within the normal variability you would see on a very infrequent occurrence," said Tim Callan, a product marketing executive for VeriSign's SSL business unit. "If these were the results of a coin flip, with heads yielding 1 and tails yielding 0, we wouldn't be surprised to see this sequence at all, and certainly wouldn't conclude that there's any upward trend towards heads coming up on the coin."
Well, we hope that nobody's head is flipped in an unsurprising fashion....
It remains to be seen whether this makes any difference. I must admit, I check the green bar on my browser when online-banking, but annoyingly it makes me click to see who signed it. For real users, Firefox says that it is the website, and this is wrong and annoying, but Mozilla has not shown itself adept at understanding the legal and business side of security. I've heard Safari has been fixed up so probably time to try that again and report sometime.
Then, over to Germany, where a snafu with a HSM ("high security module") caused a root key to be lost (also in German). Over in the crypto lists, there are PKI opponents pointing out how this means it doesn't work, and there are PKI proponents pointing out how they should have employed better consultants. Both sides are right of course, so what to conclude?
Test runs with Germany's first-generation electronic health cards and doctors' "health professional cards" have suffered a serious setback. After the failure of a hardware security module (HSM) holding the private keys for the root Certificate Authority (root CA) for the first-generation cards, it emerged that the data had not been backed up. Consequently, if additional new cards are required for field testing, all of the cards previously produced for the tests will have to be replaced, because a new root CA will have to be generated. ... Besides its use in authentication, the root CA is also important for card withdrawal (the revocation service).
The first thing to realise was that this was a test rollout and not the real thing. So the test discovered a major weakness; in that sense it is successful, albeit highly embarrassing because it reached the press.
The second thing is the HSM issue. As we know, PKI is constructed as a hierarchy, or a tree. At the root of the tree is the root key of course. If this breaks, everything else collapses.
Hence there is a terrible fear of the root breaking. This feeds into the wishes of suppliers of high security modules, who make hardware that protect the root from being stolen. But, in this case, the HSM broke, and there was no backup. So a protection for one fear -- theft -- resulted in a vulnerability to another fear -- data loss.
A moment's thought and we realise that the HSM has to have a backup. Which has to be at least as good as the HSM. Which means we then have some rather cute conundrums, based on the Alice in Wonderland concept of having one single root except we need multiple single roots... In practice, how do we create the root inside the HSM (for security protection) and get it to another HSM (for recovery protection)?
Serious engineers and architects will be reaching for one word: BRITTLE! And so it is. Yes, it is possible to do this, but only by breaking the hierarchical principle of PKI itself. It is hard to break fundamental principles, and the result is that PKI will always be brittle, the implementations will always have contradictions that are swept under the carpet by the managers, auditors and salesmen. The PKI design is simply not real world engineering, and the only thing that keeps it going is the institutional deadly embrace of governments, standards committees, developers and security companies.
Not the market demand. But, not all has been bad in the PKI world. Actually, since the bottoming out of the dotcom collapse, certs have been on the uptake, and market demand is present albeit not anything beyond compliance-driven. Here comes a minor item of success:
VeriSign, Inc. [SNIP] today reported it has topped the 1 billion mark for daily Online Certificate Status Protocol (OCSP) checks.[SNIP] A key link in the online security chain, OCSP offers the most timely and efficient way for Web browsers to determine whether a Secure Sockets Layer (SSL) or user certificate is still valid or has been revoked. Generally, when a browser initiates an SSL session, OCSP servers receive a query to check to see if the certificate in use is valid. Likewise, when a user initiates actions such as smartcard logon, VPN access or Web authentication, OCSP servers check the validity of the user certificate that is presented. OSCP servers are operated by Certificate Authorities, and VeriSign is the world's leading Certificate Authority.
[SNIP] VeriSign is the EV SSL Certificate provider of choice for more than 10,000 Internet domain names, representing 74 percent of the entire EV SSL Certificate market worldwide.
(In the above, I've snipped the self-serving marketing and one blatant misrepresentation.)
Certificates are static statements. They can be revoked, but the old design of downloading complete lists of all revocations was not really workable (some CAs ship megabyte-sized lists). We now have a new thing whereby if you are in possession of a certificate, you can do an online check of its status, called OCSP.
The fundamental problem with this, and the reason why it took the industry so long to get around to making revocation a real-time thing, is that once you have that architecture in place, you no longer need certificates. If you know the website, you simply go to a trusted provider and get the public key. The problem with this approach is that it doesn't allow the CA business to sell certificates to web site owners. As it lacks any business model for CAs, the CAs will fight it tooth & nail.
Just another conundrum from the office of security Kafkaism.
Here's another one, this time from the world of code signing. The idea is that updates and plugins can be sent to you with a digital signature. This means variously that the code is good and won't hurt you, or someone knows who the attacker is, and you can't hurt him. Whatever it means, developers put great store in the apparent ability of the digital signature to protect themselves from something or other.
But it doesn't work with Blackberry users. Allegedly, a Blackberry provider sent a signed code update to all users in United Arab Emirates:
Yesterday it was reported by various media outlets that a recent BlackBerry software update from Etisalat (a UAE-based carrier) contained spyware that would intercept emails and text messages and send copies to a central Etisalat server. We decided to take a look to find out more....
Whenever a message is received on the device, the Recv class first inspects it to determine if it contains an embedded command — more on this later. If not, it UTF-8 encodes the message, GZIPs it, AES encrypts it using a static key (”EtisalatIsAProviderForBlackBerry”), and Base64 encodes the result. It then adds this bundle to a transmit queue. The main app polls this queue every five seconds using a Timer, and when there are items in the queue to transmit, it calls this function to forward the message to a hardcoded server via HTTP (see below). The call to http.sendData() simply constructs the POST request and sends it over the wire with the proper headers.
Oops! A signed spyware from the provider that copies all your private email and sends it to a server. Sounds simple, but there's a gotcha...
The most alarming part about this whole situation is that people only noticed the malware because it was draining their batteries. The server receiving the initial registration packets (i.e. “Here I am, software is installed!”) got overloaded. Devices kept trying to connect every five seconds to empty the outbound message queue, thereby causing a battery drain. Some people were reporting on official BlackBerry forums that their batteries were being depleted from full charge in as little as half an hour.
So, even though the spyware provider had a way to turn it on and off:
It doesn’t seem to execute arbitrary commands, just packages up device information such as IMEI, IMSI, phone number, etc. and sends it back to the central server, the same way it does for received messages. It also provides a way to remotely enable/disable the spyware itself using the commands “start” and “stop”.
There was something wrong with the design, and everyone's blackberry went mad. Two points: if you want to spy on your own customers, be careful, and test it. Get quality engineers on to that part, because you are perverting a brittle design, and that is tricky stuff.
Second point. If you want to control a large portion of the population who has these devices, the centralised hierarchy of PKI and its one root to bind them all principle would seem to be perfectly designed. Nobody can control it except the center, which puts you in charge. In this case, the center can use its powerful code-signing abilities to deliver whatever you trust to it. (You trust what it tells you to trust, of course.)
Which has led some wits to label the CAs as centralised vulnerability partners. Which is odd, because some organisations that should know better than to outsource the keys to their security continue to do so.
But who cares, as long as the work flows for the consultants, the committees, the HSM providers and the CAs?
July 09, 2009
Webmoney's start in the 1998 crisis
In comments, Igor Drokov asked for data points on my claim that Webmoney single-handedly saved the Russian people from their crisis. The problem with Webmoney has always been that the documentation is in Russian, so the story spread slowly and was wildly exaggerated in the telling. I asked Dani Nagy, who is fluent in Russian, for the truth, and here's what he said:
Here is a summary of the official history of WebMoney, as told in 2005 (in Russian) and an interview:
The first financial transaction in WebMoney happened on November 20, 1998, when the shock of the financial meltdown was still raw in Russia. They started their operations with a "Marshall-plan", spending a few tens of thousands of dollars as follows: the first 1000 registered users got 30 WMZ (WM denominated in USD) on their accounts, the first few vendors that signed up for accepting WM got 100 WMZ and invitations were rewarded by 3 WMZ each, if successful.
For about a month, they announced each signed-up vendor as a separate news item on their main page. By December 1998 they switched to batch announcements, as the service was growing in popularity, albeit mostly confined to Moscow due to the (almost negligibly) low residential internet penetration elsewhere in Russia.
The growth was quite rapid. By the end of 1999, businesses operating mostly online, such as ISPs, banner exchanges, hosting providers and web design studios, adopted Webmoney almost universally. It was in 1999 when exchange agents started popping up in major Russian cities. They also got into the remittance business, mostly for Russians working in America's dot com boom.
By 2000, WebMoney was already very popular across Russia. That same year, Oleg Bunas started a branch in Minsk, Belarus. See this (also in Russian).
Of course, in those years, WebMoney was severely constrained by the low Internet penetration in Russia. But among internet users it was a runaway success from the very beginning, as there was no comparable fast and cheap means of payment. The banking sector certainly failed to meet the demand for such.
My (Dany's) comment:
Giving cash to conductors on railroads has been and still remains a popular means of money transfer, but when it's -20C outside (with a raging blizzard to complete the picture), the benefits of being able to wire money from the comfort of one's home or office are difficult to overstate. :-)
The effect of the present financial crisis on WebMoney is thankfully measured by Google.
July 06, 2009
alternative monies for peace?
When the Nobel Prize for Peace was awarded a few years back for alternative finance (in this case, microlending bank Grameen and inventor Mohammad Yunus), this caught people by surprise. Economics maybe, but why peace? There is an alternative payment system called M-PESA in Kenya that has made the case (spotted here by Philipp):
M-PESA flows reversed during Kenya’s political crisis, with rural users sending money to urban contacts.As I noted in a previous post - “Why has M-PESA become so popular in Kenya?” M-PESA was used predominantly for the transfer of remittances in the two research sites. Usually these flowed from urban centres like Kibera to rural villages like Bukura. However, there was a reversal in such flows during the post-election crises in Kenya. Urban migrants were receiving money and airtime from their rural relatives.
During this period, money and airtime cards could not be physically transported across the country. Many of the roads were blocked by rioting youth, and the railway was dismantled. This was problematic for many of the urban migrants. They needed money to escape the threat of ethnic violence, and airtime to communicate about their situation.
Some of the migrants received such support from friends and relatives in the village, who transferred both money and airtime via M-PESA. Others withdrew cash from M-PESA if they had a balance in their account. Most banks remained closed during the violence, which further made it difficult to access money. Some agents located in urban areas, which were affected by the violence, confirmed this finding. They asserted that the demand for services was high during this period. They further explained that the nature of transaction had changed—urban customers were making withdrawals rather than deposits.
In times of trouble, the standard mechanisms are attacked. Rioters target merchants and especially banks. So what works? Well, alternative methods spring up.
It doesn't so matter what the alternative methods are, as long as they are alternatives. In this sense, the world's banking strategy of cartelising the payments mechanisms is a recipe for collapse, because we are enforcing a legal monoculture. When the monoculture hits a virus, all transactions catch the cold and the economy goes to bed.
The same thing happened in 1998 or so when the Russian financial crisis happened. The Russian banking sector met its Battle of Kursk and collapsed, taking their payments abilities with them. A rough upstart called Webmoney was luckily up and going, and was able to transmit sorely needed payments across Russia and further. At the end of the crisis, it was the last man left standing, because it wasn't one of them.
So when you see regulation and cartelisation against alternative finance systems, ask for a guarantee of stability from the those supporting the anti-competitive activity. Of course no such is worth the paper it is printed on, but somehow we have to get the message through that lightweight alternative finance is good for us all, and monoculture is bad for us, unless you happen to be the predominant organism that is taking over the organ of economy.
April 03, 2009
The Exquisite Torture of Best Practices
Best practices has always seemed to be a flaky idea, and it took me a long time to unravel why, at least in my view. It is that, if you adopt best practices, you are accepting, and proving, that you yourself are not competent in this area. In effect, you have no better strategy than to adopt whatever other people say.
The "competences" theory would have it that you adopt best practices in security if you are an online gardening shop, because your competences lie in the field of delivering gardening tools, plants and green thumbs advice. Not in security, and gosh, if someone steals a thousand plants then perhaps we should also throw in the shovel and some carbon credits to ease them into a productive life...
On the other hand, if you are dealing with, say, money, best practices in security is not good enough. You have entered a security field, not through fault of your own but because crooks really do always want to steal it. So your ability in defending against that must be elevated, above and beyond the level of "best practices," above and beyond the ordinary.
In the language of core competences, you must develop a competence in security. Now, Adam comes along and offers an alternate perspective:
Best practices are ideas which make intuitive sense: don't write down your passwords. Make backups. Educate your users. Shoot the guy in the kneecap and he'll tell you what you need to know.
I guess it is true that best practices do make some form of intuitive sense, as otherwise they are too hard to propogate. More importantly:
The trouble is that none of these are subjected to testing. No one bothers to design experiments to see if users who write down their passwords get broken into more than those who don't. No one tests to see if user education works. (I did, once, and stopped advocating user education. Unfortunately, the tests were done under NDA.)The other trouble is that once people get the idea that some idea is a best practice, they stop thinking about it critically. It might be because of the authority instinct that Milgram showed, or because they've invested effort and prestige in their solution, or because they believe the idea should work.
What Adam suggests is that best practices survive far longer than is useful, because they have no feedback loop. Best practices are not tested, so they are a belief, not a practice. Once a belief takes hold, we are into a downward spiral (as described in the Silver Bullets paper, which itself simply applies the full _asymmetric literature_ to security) which at its core is due to the lack of a confirming test in the system that nudges the belief to keep pace with the times; if there is nothing that nudges the idea towards relevancy, it meanders by itself away from relevancy and eventually to wrongness.
But it is still a belief, so we still do it and smile wisely when others repeat it. For example, best practices has it that you don't write your passwords down. But, in the security field, we all agree now that this is wrong. "Best" is now bad, you are strongly encouraged to write your passwords down. Why do we call the bad idea, "best practices" ? Because there is nothing in the system of best practices that changes it to cope with the way we work today.
The next time someone suggests something because it's a best practice, ask yourself: is this going to work? Will it be worth the cost?
I would say -- using my reading of asymmetric goods and with a nod to the systems theory of feedback loops, as espoused by Boyd -- that the next time someone suggests that you use it because it is a best practice, you should ask yourself:
Do I need to be competent in this field?
If you sell seeds and shovels, don't be competent in online security. Outsource that, and instead think about soil acidity, worms, viruses and other natural phenomena. If you are in online banking, be competent in security. Don't outsource that, and don't lower yourself to the level of best practices.
Understand the practices, and test them. Modify them and be ready to junk them. Don't rest on belief, and dismiss others attempts to have you conform to belief they themselves hold, but cannot explain.
(Then, because you are competent in the field, your very next question is easy. What exactly was the genesis of the "don't write passwords down" belief? Back in the dim dark mainframe days, we had one account and the threat was someone reading the post-it note on the side of the monitor. Now, we each have hundreds of accounts and passwords, and the desire to avoid dictionary attacks forces each password to be unmemorable. For those with the competence, again to use the language of core competences, the rest follows. "Write your passwords down, dear user.")
February 04, 2009
The un-internalised cost of your data breach
 Adam points to a report by Ponemon Institute and old friends PGP Inc on data breaches.
Adam points to a report by Ponemon Institute and old friends PGP Inc on data breaches.
data breach incidents cost U.S. companies $202 per compromised customer record in 2008, compared to $197 in 2007. Within that number, the largest cost increase in 2008 concerns lost business created by abnormal churn, meaning turnover of customers. Since the study’s inception in 2005, this cost component has grown by more than $64 on a per victim basis, nearly a 40% increase.
Frequent readers of this blog will recall that I often post numbers of the average end-user cost of events like phishing. The number is about $1000.
Ignoring the obviously simplistic scientific process here, or better yet, leaving it to someone more scientific ... there is a huge difference between $200 and $1000.
We can take several views on this:
- a "caveat emptor view" has the user taking all the costs, because in libertarian economies, the user takes the responsibility for their choices. The responsible libertarian purchases PGP, of course.
- a "switching view" would have it that the only kick-back to the company is when a smaller proportion of the users switch to other providers, thus causing lessons of pain. This "churn view" is where the Ponemon report suggests the market is.
- the "risk sharing view" would have it that the user pays a smaller but still painful part. Call it 20%, or the opposite of what we see above. This should put the user firmly in the security protocol, and address any risks that the user is lax, but puts the onus on the business to provide the right tools.
- the "insurance view" is that the user pays the first $50 such as happens in credit card purchases. This more or less fixes the user's part in the protocol to little things like "don't lose the card" and passes the rest across to the company.
- "efficient view" would have it that the cost to the users should be close to $0 and the cost to the business should be closer to $1200. This is because the business is better able to manage all of the risk, knowing the business, as it does.
| 1200 | 1100 | 1000 | 900 | 800 | 700 | 600 | 500 | 400 | 300 | 200 | 100 | 000 | User Pays | |
| Caveat emptor | user buys PGP | |||||||||||||
| Switching | "churn" | |||||||||||||
| risk sharing | small but painful | |||||||||||||
| insurance | "don't lose that card" | |||||||||||||
| Efficient | know the business! | |||||||||||||
| Business pays | 000 | 100 | 200 | 300 | 400 | 500 | 600 | 700 | 800 | 900 | 1000 | 1100 | 1200 |
Markets tend to mature towards either the efficient view or the insurance view. The market in your identity is not mature. The reasons for that might be widely debated, but I'll have a quick stab here: we never really wanted to buy and sell our identities. We don't want that market in the first place, so damned if we're going to let it mature.
February 02, 2009
Risk is business: why mathematical models will not analyse security
Risk analysis, like every other measurement undertaking, reaches some point of diminishing return. In fact, I think we could offer that risk analysis that has to do with "econ" reaches that point more quickly than many other disciplines due to the uncertainties in the measurement factors.
Which is one of the central problems with the use of models: it won't work if we plug in bad numbers, something known poetically as garbage-in-garbage-out or GIGO.
What we do know in security is that we lack the metrics to deliver the inputs, to any good extent. That is well understood, and there is a conference called Metricon which looks at this very question, how to turn our terrible collection of bad data into a set of metrics that can actually deliver some conclusions.
But it gets worse! To show this I need to link across to something called net-present-value ("NPV") or capital-asset-pricing-model ("CAPM"). The task of these financial models is to generate a number (approximately called a "value") for each project, to allow comparison between projects. It doesn't tell you how much each project is worth, because we recognise that the model is trying to predict the future, and so mistakes and absences in our current information will not give us that. However, by using it to compare the different projects, we filter out all the mistakes that are in common across projects.
It is therefore the best known tool for comparison of projects. Which makes it ideal for security risk management, because that is all we want to do: analyse many competing ideas, create a "value" for them, and compare those values against each other. We then select the ones with the highest "value".
Which leads us to Alex's other comment:
NPV necessitates some concept of cash flow: Rt/(1+i)^t where Rt is cash flow in.
No, not at all. NPV requires a value. It just happens to use a "cashflow" or dollar value at a time point. It happens to require that the "cashflows" are all calculated the same way, so as to filter out errors and biases for the later comparison phase. It happens to require that all projects be turned into a cashflow view. But it does not require a flow of income to the project.
So where do these "values" come from? Well, the same place as always, by using our experience, some finger-in-the-air guesses, and a pocket calculator.
Risk Analysis, in InfoSec/Engineering at least, is currently based on the Dutch model: probable frequency of loss and probable magnitude of loss (note that ALE is a number of limited value, as risk is a derived number like km/hr).
Right. Financial projects do exactly the same. They take probable frequency of revenues, probable sizes of revenues, multiply them out (or integrate them), reduce them backwards to current time, then sum them all with probable costs treated in the same way. It's called net-present-value, and probable frequency of loss together with probable magnitude of loss is a cashflow to NPV.
So if the point is, risk analysis in security work has failed to incorporated the last phase, then OK, yes, that is understood. Security people also talk about ROI, without understanding why it has been junked already in finance. The sum of it is that current approaches to risk analysis in InfoSec/Engineering are just CAPM done incompletely and badly. So I make the claim that risk analysis in the "econ" sense is CAPM, or should be CAPM.
The problem however is more deep seated than that. Although the analysis of why CAPM works applies fully to security work, to the extent that CAPM dominates ALE, there are some gotchas. And these are in assumptions that only the finance geeks are really going to be able to surface.
- CAPM assumes independence of projects. This assumption is not easily acceptable to security work, because we have an active attack scenario. That is, although the attacker doesn't care one way or another, the more we lean on the assumption of independence, the more the attacker will care, and this assumption will turn brittle.
- CAPM assumes a market. Not only does it generate its results in a market context (in short, the goal is to achieve the envelope of market risk-reward), it separates out risks and hands some risks to the market, keeping some risks for itself. C.f., diversification. In security world, we don't generally assume a market, nor can we deal with the way CAPM slices and dices those risks.
This is no mild criticism. If we take away those assumptions, CAPM is dead. Totally dead, dead as a dodo, finance has to go back to the 1950s and start again, and Markowitz has to give back his Nobel prize.
So my claim here is that whatever risk analysis and management ends up being in the security field, if it is a mathematical thing, then:
- risk management is CAPM, albeit badly and incompletely.
- These techniques rely on assumptions that security work does not have.
If we then add the first argument that everyone else is familiar with:
- we don't have decent metrics to feed into the models,
we can see why I draw my aggressive conclusion: risk management is dead. At least, if we define risk management as a mathematical model for analysing costs and benefits of different security projects. On the other hand, if we define it like Alex does:
risk management has as much to do with understanding capability as it does with arriving at a state of knowledge. Without that capability component, you'll never achieve a state of wisdom.
Or like the article that Arthur pointed to:
StanCorp manages all those risks in a host of ways, Chadee says, including "sound product design and underwriting; effective claims management; disciplined pricing; distribution expertise; broad diversification of risk by customer geography, industry, size, and occupation; maintenance of a strong financial position; maintenance of reinsurance and risk-pool arrangements...." You get the idea.
Then I've got a better word for it: business. Or, as Gunnar puts it, assets. Or, as Clive puts it, quality. So sure, it's a book about reliability from Daniels Geer & Conway, or marketing:
So security needs to be sold to the consumer business in the same way as quality. That is as a method of improving efficiency by increasing productivity of the work force and reducing cost.However to do this the "ICT security staff" need to be able to make a business case to the organisational managment using the language that business managment use.
Or an MBA. In short, it's business.
January 26, 2009
WoW crosses GP: get rich quick in World of Warcraft

SecretSquirrel writes:
it's a "get rich quick" guide for sale ... but actually for the virtual money inside the WoW game
Around a year or two ago I penned a series of rants called "GP" which predicted that the primary success signal of a new money was ... crime! The short summary is that in the battle for mindspace between issuers, users, critics & regulators, the press (who?) the offended and the otherwise religious ... there is no way for the external observer to figure out whether this is worthwhile or not.
But wait, there is one way: if a criminal is willing to put his time, his investment, indeed his very freedom on the line for something, it's got to be worth something! GP is undeniably crossed, I theorise, when criminals steal the value, and therefore provide a most valuable signal to the world that this stuff is worth something.
(it's not a parody!)it's exactly following the format to the line, of any of the famous get-rich-quick newsletters.
(eg, http://www.landingpagecashmachine.com or hundreds of others) ... even the famous "three-line centered upper-lower case headline"
Call me cynical, but I have seen hundreds of digital cash systems live and die without meriting a second thought. There have been thousands I haven't seen! In my decade++ of time in this field, I've only seen one external signal that is reliable. Even this:
You know they say WoW is over $150 million per month in player fees now!
Is ... well, ya know, could be a fake. Did we see that Satyam, a huge audited IT outsourcing firm in India added some 13,000 jobs ... and nobody noticed?
If I am right, I'll also be blamed for the upsurge in fake crimes :)
January 24, 2009
We may have risk, but _banking is risk_
Some felt my claim of banking and insurance was too brave:
The only business that does risk management as a core or essence is banking and insurance (and, banking is debatable these days). For all others, risk management is just an ancilliary aspect, a nice-to-have, something that others say is critical to you, but you ignore because you've got too much to do.
From this I separated out into those that do risk management because because they are risk management, from those who have risk management because it is useful. If you are familiar with object oriented thinking, this is the difference between isARiskManagement and haveARiskManagement.
Banking is risk management because of the term mismatch. Simply put, banks take in deposits, which are payable on demand, and lend it out at term, which means the banks can't get it back. By ordinary business rules, banks are bankrupt, because they cannot pay back what they owe. Anytime you can get a large bunch of depositors together, you can prove this, by starting a "run" on a bank.
This not only makes banking different from all other businesses, it also makes banking, all of banking, at is very core an exercise in managing the risk of those term loans (and those deposits, but there are some easy answers to that side). Insurance is the same, although different in some ways. As Alex has it:
Most security folks (and many in the financial industry) believe that risk analysis is something to *engineer* future state, rather than a tool used in understanding our ability to meet qualitative objectives. As such, when the state of nature changes (as it inevitably does) or when it's determined that the analyst screwed up in accounting for uncertainty or variable measurement - the whole process is demonized.
If banks did that, they would die. When banks muck up their risk management, they fail because that's what they are, they are risk. When the entire sector, banking as an industry, mucks up its risk management, then it fails, as a sector. Finance goes down the tube.
On the other hand, other businesses have risk management. It's an option, it's a nice-to-have, or a told-to-have. As Alex says of public companies:
First, allow me to point you to future earnings guidance statements made by public companies.
Or, as Don wrote in comments over at EC, "Risk management as the basis for information security planning is alive and well in healthcare (required by HIPAA) and for federal systems (required by FISMA)." Some companies are told to do it, but that alone doesn't make it right, nor useful.
What does this is-versus-have differentiation allow us to say? Well, in banking, if you don't do risk management, you are dead. You are expert in this, and maybe nothing else. It is your core competence, it your very being, your essence.
In other businesses, not so. It all depends. Maybe you have a competence in risk management, or maybe you have a department that does this, or maybe your security guys think it's hot stuff. Or maybe not. The point being, risk management is optional, and some firms will be good at it and some not. Or, as Alex puts it:
Chemical and Aerospace engineering, Food Service, and many other industries I'm skipping over do perform rigorous risk analysis, it's just that the system they operate in has much less uncertainty.
Which leads to the rather contrary conclusion that, unless it delivers results, then ... it might not be worth the money, however it is arrived at, whatever you are cooking. And by obvious conclusion, there are options: you can either apply risk management as it is mathematically inspired, or you can choose to eliminate these risks, as was the old 1990s security dogma, or you can choose to manage these risks from a business perspective, incorporating other knowledge.
The point of the first half of that post was to open up the options. Only banks have to do risk management, and cannot choose. Others can choose. Which sets it up for the rest of the post, which suggests that actually, risk management as it is stressed by the "economic" school may not be worthwhile.
January 23, 2009
the Business of Risk Management in Security -- a Response
Alex writes in comments a response to my "Business" post. As it is comprehensive and detailed, I'll re-post it here for reasons I can't exactly explain. Here goes, rest of words from Alex:
I find that most people with InfoSec backgrounds confuse the purpose of using probability theory in risk analysis (1).
Most security folks (and many in the financial industry) believe that risk analysis is something to *engineer* future state, rather than a tool used in understanding our ability to meet qualitative objectives. As such, when the state of nature changes (as it inevitably does) or when it's determined that the analyst screwed up in accounting for uncertainty or variable measurement - the whole process is demonized.
In reality, a good model for risk analysis can only help rational actors arrive at rational conclusions. It cannot and will not foresee a precise future state, but it rather serves to help remove bias and provide structure to what would otherwise be an ad-hoc decision making process. It is with this in mind, that I often ask the authors of these sorts of articles - "well, how then shall we live?" The best answer I get is "suggested practices"(2). The problem with this concept is that it is, in and of itself, a risk analysis model, just one done as a faith-based initiative rather than one done with any real rigor ("trust me, I'm the auditor, you need these controls").
W/regards to other points:
"The only business that does risk management as a core or essence is banking and insurance"
False on two accounts. First, allow me to point you to future earnings guidance statements made by public companies.
Second, I'd say that FinServ is just a market segment that applies analytical rigor to a product line that has a significant degree of uncertainty. Chemical and Aerospace engineering, Food Service, and many other industries I'm skipping over do perform rigorous risk analysis, it's just that the system they operate in has much less uncertainty.
"risk management is... something...you ignore because you've got too much to do."
Nope, at worst it's just something you don't apply significant rigor to because it's not perceived as necessary. When you walk across the street, decide to hire or not to hire, just about any decision that has the potential for negative consequence, you're creating a belief statement that is "go" or "no go". This is very much a risk analysis, as in a Bayesian sense you're creating a belief statement about what is the most probable wise action.
"ROI in infosec is GIGO"
I think you're confusing the concept of the quality of inputs into a model with a statement about the quality of the model.
With regards to ROI in infosec, I find those who simply state that it "can't be done" categorically to be boorish purveyors of hyperbole. They seem to be obsessed with confidentiality and forget that availability is a significant aspect of the charter for most security departments. ROI for keeping production systems available most certainly can be calculated with some degree of suitability.
Now that said, I don't believe that ROI is applicable when we're concerned with and/or including the probability of losses due to breaches in confidentiality and integrity, as these concepts are not easily tied to incoming cash flow in a direct and obvious manner.
"Risk management is just another word for NPV, so risk management doesn't work."
False premise, false conclusion. NPV necessitates some concept of cash flow: Rt/(1+i)^t where Rt is cash flow in. Risk Analysis, in InfoSec/Engineering at least, is currently based on the Dutch model: probable frequency of loss and probable magnitude of loss (note that ALE is a number of limited value, as risk is a derived number like km/hr). Two totally different concepts.
"a priori, risk management suffers GIGO"
Um, what? If you mean that using deductive reasoning, models about the world require useful inputs to develop useful outputs, OK then. All perceptions of reality have that same limitation. But I see no deduction on your part to achieve a statement of "a priori".
"Consider the famous case of the car-lock. Car locks used to be notoriously weak. Why? Because a car stolen was a car sold. So, no matter what numbers were applied in the above risk management calculation, it always gave the wrong result; better locks made the position worse!"
You seem to be assuming an objective ethical position here and inferring that all actors would desire to achieve it. Rather, the car company most certainly did an analysis and came to the conclusion that it's interests were different than the consumer. It's a great example not because it "proves" risk analysis to be silly in some Popperist sense (3) but rather it highlights the most interesting problem in Risk Management - the problem of multiple perspectives (an example would be where the risk manager's individual compensation is inconsistent with executive risk tolerance).
Finally, in response to your summary, I think you over-complicate the value the CISO/CSO/CRO has to the company. Their value boils down to only two things; Align risk exposure to the tolerance of management or create operational efficiencies. All this other talk of "aligning to business and strategy" is, in my opinion, pure bunk.
(1): note that the concept of risk management isn't necessarily what you're referring to here - risk management has as much to do with understanding capability as it does with arriving at a state of knowledge. Without that capability component, you'll never achieve a state of wisdom.
(2): ironically using the term "best/good practices" implies some sort of analysis and measurement.
(3): In fact, I'd say that the state has changed to the point where the opposite is true, cars probably have too much lock security built in. I wonder what the locksmithing industry would have to say about the 70's vs. now and their ability to retrieve our keys for us.
January 20, 2009
Selgin on the subtle competition between "official" and "alternative" currencies
Argentina has run out of coins it seems, something that happens when your government thinks it knows how to run an economy better than the people, and it falls for the old commodity-coinage-price-inversion trick. (Last I heard, the same had happened in the USA, so don't laugh so hard....)
Why the shortage? Argentina's central bank blames it on "speculators," meaning everyone from ordinary citizens, who stockpile coins, to Maco, the private cash-transport company (think of Brinks) that repackages change gathered from bus companies to resell at an 8% premium. But those explanations ring false. "Black marketeering" would not exist if coins were easy to get in the first place. After all, Argentines could just as easily hoard razor blades or matchbooks. Yet there's no shortage of those. What's so special about coins?The answer is that coins are supplied by the government alone. "Put the federal government in charge of the Sahara desert," Milton Friedman said, "and in five years there'd be a sand shortage." If Argentina wants to end the coin shortage, it ought to give up its monopoly.
Crazy? Not if history is the guide. Over two centuries ago, Great Britain faced a coin shortage more severe than Argentina's -- so severe that it threatened to stop British industrialization in its tracks. People struggled to get coins for everyday use. The average worker was lucky to make 10 shillings a week, while the smallest banknotes were for 10 times as much. So the coin shortage even prevented factories from paying wages.
Like Argentina's government today, the British government wasn't able to end the shortage. Yet the shortage did end -- thanks to private-sector action. Fed up with the government's inaction, British firms started minting their own coins. Within a decade a score of private mints struck more coins than the Royal Mint had issued in half a century -- and better ones: heavier, more beautiful, and a lot harder to fake. Yet they were also less expensive, since private coiners sold their products at cost plus a modest markup, like other competitive firms, instead of charging the coins' face value, as governments like to do. Finally, when those who had accepted the private coins for payment went back to the issuer to redeem them, issuers offered to exchange their coins for central bank notes at no cost.
The blindingly obvious way to deal with this, for economists who've done any reading of the free banking literature, is to allow alternative currencies. The problem then arises that the Central Banks will resist this because of the threat to control. I was asked this question yesterday, and while I gave an answer, Prof. George Selgin's description is better. He outlines the path to "controlling" competing currencies in this WSJ post. It is subtle, and takes some getting used to.
If Argentina wants to end the shortage, it ought, not only to tolerate private coinage, but to sanction it. It can do so, while eliminating any risk that such coinage would be abused, through very simple legislation. It should allow any private firm to issue distinctly marked coins, perhaps subject to some minimal capital requirements, while making it clear that no one need ever accept any privately issued coins , even as change for purchases.Such a law may be all that's needed to solve the coin shortage, while also preventing anyone from forcing people to accept money they didn't trust. Anyone, that is, except the Central Bank of Argentina.
The subtle essence I highlight above is to create a range of slight benefits for the official currency, over freely competing alternatives. If ones goal for monetary policy is inflation control and a sound official unit of currency, then it isn't necessary to totally ban the alternatives, instead it is sufficient to make yours more attractive.
This can be done by having a few rules. One is the legal tender rule, which says ONLY that a debt that is offered for payment (proferred?) in the legal tender is considered to be paid. So, if I offer you $$$ and if you don't accept my $$$, and prefer the debt paid in bananas instead, the debt is legally acceptable as paid, in court.
This amounts to a very subtle and relatively small subsidy in favour of the official currency. It is enough to make it the favoured one. It is cheating, of course, because the Central Bank is not competing on a level playing field. Which is why it is important to ground this in monetary policy goals.
If your goal is to control the economy, then you won't permit this to happen at all, and your economy will suck, because of the Misean calculation problem. Indeed, banning private monies amounts to evidence that your goal is to control the economy, and as we know this is impossible, it is evidence of the government's ignorance of economics.
So the issue with alternative currencies is:
First, recognise that your monetary policy goal is your own sound currency, not control of the economy. Second, loosen the controls to open up the way for alternatives. Third, leave the official one on the pedestal for sufficient "official" purposes, using tricks like legal tender law.... Fourth, encourage the alternatives to reach places yours does not.
This way, the alternatives cannot knock it off the pedestal for the time being, but the alternatives fill the niches in the economy that the official unit cannot reach. This is true monetary policy; for the benefit of the people, not against them.
January 19, 2009
Microsoft: Phishing losses greatly over-estimated
09 Jan 2009 14:21Phishers make much less from their scams than analysts have estimated, according to research from the software maker. The financial losses experienced by victims of phishing scams may be up to 50 times less than estimated by analysts, according to a Microsoft study. Previous studies by organisations such as Gartner, which in 2007 estimated US phishing losses at $3.2bn (£2bn), "crumble upon inspection", Microsoft researchers said in their report, published on Tuesday.
Nevertheless, stories of easy money may be encouraging a phishing "gold rush" effect, where large numbers of newcomers enter the phishing business expecting huge returns, only to be preyed upon by more experienced phishers, according to A Profitless Endeavor: Phishing as Tragedy of the Commons.
The study, undertaken by Microsoft researchers Cormac Herley and Dinei Florencio, also suggests there is less profit than thought in phishing because there is only a limited number of people who will be fooled by the scams, and that pool gets smaller as the scams claim victims.
"Phishing is a classic example of tragedy of the commons, where there is open access to a resource that has limited ability to regenerate," the authors say in their report. "Since each phisher independently seeks to maximise his return, the resource is over-grazed and [on average] yields far less than it is capable of." Instead of getting a maximum return for a minimum effort, the majority of phishers make a weekly wage of hundreds, rather than thousands, of dollars, the researchers said.
....
No comment from here, because I haven't read the source as yet.
January 17, 2009
Getting the business into security, or is it...
Ian says in comments to the post on "Business":
Your emphasis - exactly. I read Frank's 'paper' yesterday and I read it very differently. You've missed emphasising "security is essentially risk management" in the first sentence. i.e. Frank IS saying that economic risk is the turning point of the whole thing.
yes, clearly risk management is how they link their security model approach to the business. My point however was that this was a "nod" and not necessarily enough.
Let's make this polemic. Risk management is a dead duck. Here's some reasons why:
The only business that does risk management as a core or essence is banking and insurance (and, banking is debatable these days). For all others, risk management is just an ancilliary aspect, a nice-to-have, something that others say is critical to you, but you ignore because you've got too much to do. So we have a choice: is security like finance, or is it like "the rest of business?"
I would say it is not like finance. So risk management is not the core.
The question then might be whether risk management as an ancillary adds anything that helps? That depends, a lot. It turns out there is a fatal flaw in this approach.
What is the risk management approach? Well, at the detailed level, it generally turns out to be something like two calculations:
risk = (percentage chance of event) * (damage/costs of when it happens.)
defence = (percentage chance of mitigation) * (money saved)
result = comparison_function (set of all risks, set of all defences, costs).
We really don't need to cite a lot of papers (security academics take note) nor get hung up on what the real meaning of the words or variables are here, because this is a well known finance technique. It's called ROI, or more properly NPV. Let's just borrow from the finance people, because they have done this work, won their Nobel prizes and covered the territory.
Frequently, it is pointed out that the financing of security projects should be done on this basis. This is true because we don't have any other cross-business comparison tools, and your CFO demands it.
However, regardless of this truth, it doesn't really satisfy with security projects. The reason NPV doesn't work is that we don't have good numbers to plug in, like those that we have in finance. ROI in infosec is GIGO, whereas for other business areas, all of them, we can actually find those numbers. (There are good reasons why this is the case, and the hint here may be that security is like defence, and they don't do good ROI either.)
So, NPV doesn't work in Security, even though we need it. Risk management is just another word for NPV, so risk management doesn't work. Although the theory is pretty cool, actually, we don't know what those numbers are (a priori, risk management suffers GIGO), and afterwards, as long as we are making profits, we don't care (a posteriori, profits are more important than risks).
What's left? In both cases, the discussion is swamped by business issues, and those issues don't give a hoot for either number. What's left is business. If we haven't seen security as a business problem, first and foremost, no amount of Markovitzian mathematics is going to save us.
Consider the famous case of the car-lock. Car locks used to be notoriously weak. Why? Because a car stolen was a car sold. So, no matter what numbers were applied in the above risk management calculation, it always gave the wrong result; better locks made the position worse!
The simple view of this is "What's your business model?" If you want to put it in a more academic strain of thought, then yes, it is economics, but we have to include liability dumping as a technique, and that is not something that is mathematically pliable. Better to skip the econ approach, and just call it for what it is: business.
November 25, 2008
Who would judge a contest for voting machines?
In a previous entry I suggested creating an AES-style competition for automated voting systems. The idea is to throw the design open to the world's expertise on complex systems, including universities, foundations and corporates, and manage the process in an open fashion to bring out the best result.
Several people said "Who would judge a contest for voting machines?" I thought at first blush that this wasn't an issue, but others do. Why is that? I wonder if the AES experience surfaced more good stuff than superficially apparent?
If you look at the AES competition, NIST/NSA decided who would be the winner. James points out in comments that the NSA is indeed competent to do this, but we also know that they are biased by their mission. So why did we trust them to judge honestly?
In this case, what happened is that NIST decided to start off with an open round which attracted around 30 contributions, and then whittled that down to 5 in a second round. Those 5 then went forward and battled it out under increased scrutiny. Then, on the basis of the open scrutiny, and some other not-so-open scrutiny, the NSA chose Rijndael to be the future AES standard.
Let's hypothesize that the NSA team had a solid incentive to choose the worst algorithm, and were minded to do that. What stopped them doing it?
Several things. Firstly, there were two rounds, and all the weaker algorithms were cleaned out in the first round. All of the five algorithms in the second round were more or less "good enough," so the NSA didn't have any easy material to work with. Secondly, they were up against the open scrutiny of the community. So any tricky choice was likely to cause muttering, which could spread mistrust in the future, and standards are susceptible to mistrust. Thirdly, by running a first round, and fairly whittling the algorithms done on quality, and then leading into the second round, NIST created an expectation. Positively, this encouraged everyone to get involved, including those who would normally dismiss the experiment as just another government fraud, waiting to reveal itself. At a more aggressive extreme, it created a precedent, and this exposed the competition to legal attack later on.
These mechanisms worked hand in hand. Probably, either alone was not sufficient to push the NSA into our camp, but together they locked down the choices. Once that was done, the NSA saw its natural incentives to cheat neutered by future costs and open scrutiny. As it no longer could justify the risk of cheating, its best strategy was to do the best job, in return for reputation.
The mechanism design of the competition created the incentives for the judge to vote how we wanted -- for the best algorithm -- even if he didn't want to.
So, we can turn the original question around. Instead of asking who would judge such a competition, design a mechanism such that we don't care who would judge it. Make it like the AES competition, where even if they had wanted to, the NSA's best strategy was to choose the best. Set yourself a challenge: we get the right result even when it is our worst enemy.
November 20, 2008
Unwinding secrecy -- busting the covert attack
Have a read of this. Quick summary: Altimo thinks Telenor may be using espionage tactics to cause problems.
Altimo alleges the interception of emails and tapping of telephone calls, surveillance of executives and shareholders, and payments to journalists to write damaging articles.
So instead of getting its knickers in a knot (court case or whatever) Altimo simply writes to Telenor and suggests that this is going on, and asks for confirmation that they know nothing about it, do not endorse it, etc.
 |
| Who ya bluffin? |
...Andrei Kosogov, Altimo's chairman, wrote an open letter to Telenor's chairman, Harald Norvik, asking him to explain what Telenor's role has been and "what activity your agents have directed at Altimo". He said that he was "reluctant to believe" that Mr Norvik or his colleagues would have sanctioned any of the activities complained of..... Mr Kosogov said he first wrote to Telenor in October asking if the company knew of the alleged campaign, but received no reply. In yesterday's letter to Mr Norvik, Mr Kosogov writes: "We would welcome your reassurance that Telenor's future dealings with Altimo will be conducted within a legal and ethical framework."
Think about it: This open disclosure locks down Telenor completely. It draws a firm line in time, as also, gives Telenor a face-saving way to back out of any "exuberance" it might have previously "endorsed." If indeed Telenor does not take this chance to stop the activity, it would be negligent. If it is later found out that Telenor's board of directors knew, then it becomes a slam-dunk in court. And, if Telenor is indeed innocent of any action, it engages them in the fight to also chase the perpetrator. The bluff is called, as it were.
This is good use of game theory. Note also that the Advisory Board of Altimo includes some high-powered people:
Evidence of an alleged campaign was contained in documents sent to each member of Altimo's advisory board some time before October. The board is chaired by ex-GCHQ director Sir Francis Richards, and includes Lord Hurd, a former UK Foreign Secretary, and Sir Julian Horn-Smith, a founder of Vodafone.
We could speculate that those players -- the spooks and mandarins -- know how powerful open disclosure is in locking down the options of nefarious players. A salutory lesson!
September 25, 2008
another quiet week in finance
 This curious article bears out some of the predictions made previously:
This curious article bears out some of the predictions made previously:
In fact, most Wall Street computer models radically underestimated the risk of the complex mortgage securities, they said. That is partly because the level of financial distress is “the equivalent of the 100-year flood,” in the words of Leslie Rahl, the president of Capital Market Risk Advisors, a consulting firm.But she and others say there is more to it: The people who ran the financial firms chose to program their risk-management systems with overly optimistic assumptions and to feed them oversimplified data. This kept them from sounding the alarm early enough.
Top bankers couldn’t simply ignore the computer models, because after the last round of big financial losses, regulators now require them to monitor their risk positions. Indeed, if the models say a firm’s risk has increased, the firm must either reduce its bets or set aside more capital as a cushion in case things go wrong.
In other words, the computer is supposed to monitor the temperature of the party and drain the punch bowl as things get hot. And just as drunken revelers may want to put the thermostat in the freezer, Wall Street executives had lots of incentives to make sure their risk systems didn’t see much risk.
“There was a willful designing of the systems to measure the risks in a certain way that would not necessarily pick up all the right risks,” said Gregg Berman, the co-head of the risk-management group at RiskMetrics, a software company spun out of JPMorgan. “They wanted to keep their capital base as stable as possible so that the limits they imposed on their trading desks and portfolio managers would be stable.”
One way they did this, Mr. Berman said, was to make sure the computer models looked at several years of trading history instead of just the last few months. The most important models calculate a measure known as Value at Risk — the amount of money you might lose in the worst plausible situation. They try to figure out what that worst case is by looking at how volatile markets have been in the past.
So, what's going on here? It's a simple cycle.
- Something goes wrong.
- Someone creates a fix.
- Something goes wrong.
- We discover that those that fixed it were ok, and those that didn't failed.
At this point, the bureaucrats and worry-worts leap into action and demand that the fix be regulated. But then what happens is this:
- Something goes wrong, and some fail as above.
- The fix is mandated.
- The fix is implemented.
- Someone bypasses the fix, creatively, because it reduces profits.
- Something goes much wronger because the system is now more complex.
- Those who bypassed the fix demand a bailout.
Why is this? Managers took their eye off the ball of risk in 4 above. But, they followed the rules! Perversely, then, they can credibly go back and insist they did all that was asked of them. Therefore, the bailout is necessary, because the responsibility for risk is now passed from the risk takers to the rule makers.
In time this pervades the market, so we end up with this:
- For everything that goes wrong, a new fix is mandated by the rule makers.
- For every mandated fix that is implemented, those that reduce profits are bypassed, creatively.
- The system is now much more complex.
- The complexity exceeds the ability of the rule makers, because while they understand the rules, they do not understand the bypasses.
- The complexity exceeds the ability of the risk takers, as they understand the bypasses, but have lost sight of the reasons for the fixes.
- We enter the territory known as "fragility to Black Swans".
- Black Swan arrives.
None of this is any surprise to engineers. Complexity makes things really collapse in big and complex ways. The other solution is somewhat simpler:
- Something goes wrong.
- Those that covered the issue, survive. Those that didn't, die.
- The strong survive.
Think of it as a plane with more than one engine... But this is really only possible when regulators and the public alike realise that these are complex systems, and are not amenable to the notions of total reliability. This is the territory where redundancy is king, and failure is encouraged.
Bankrupcy is healthy to the eco-system. If you try and avoid it, watch out for a bigger failure later on. Another salutory lesson comes from the auditors. They were supposed to protect the public investor from the managers in the firm; when Arthur Andersen was caught out for allegedly protecting the managers from the investors ... it collapsed. When KPMG found itself on the wrong side of someone's stake holder list, it almost folded but wise regulators said we can't lose another one.
The message here is very clear: It's a cycle thing again:
- Become very friendly with those who can save you.
- Make lots of money.
- Call in the favours when it goes wrong.
 To close, another perspective on all this is from the Black Swan of Nassim Nicholas Taleb. Here's an introductory article on Black Swans, pointed out by Twan, around 20 pages, describing the statistical anomaly that causes complex systems to fail spectacularly. This is no source of mystery to engineers, but for finance people, worth reading.
To close, another perspective on all this is from the Black Swan of Nassim Nicholas Taleb. Here's an introductory article on Black Swans, pointed out by Twan, around 20 pages, describing the statistical anomaly that causes complex systems to fail spectacularly. This is no source of mystery to engineers, but for finance people, worth reading.
September 11, 2008
US passports in 36 lots?
People on the crypto list were asking whether prices of street sales of insecurity could tell us stuff, like the drugs czars get from the price of street drugs. Dan Geer reports that the current cost of US passports is: $18k for 36, or $500 per unit. I'm not sure what the "lot of 36" entails.
He also reports a bunch of other things available for sale on the net black markets. Here's a selection of prices that would interest this audience:
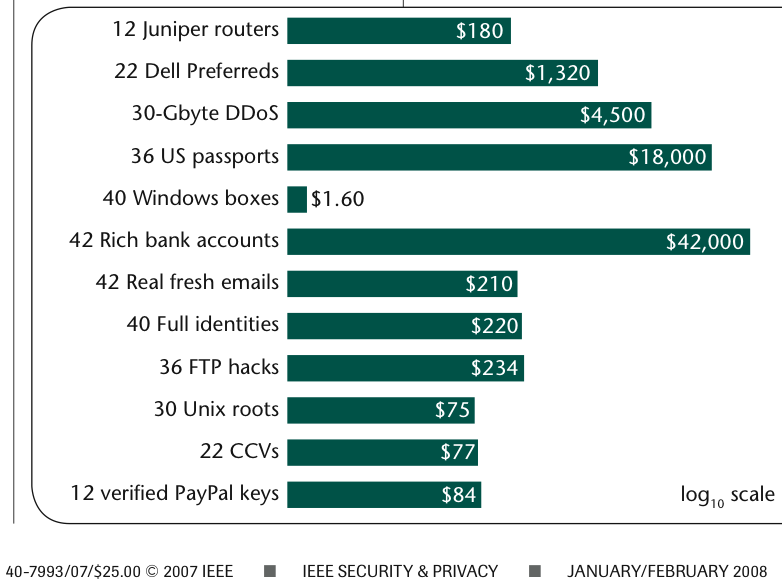 40 compromised windows boxes: $1.60
40 compromised windows boxes: $1.60
42 rich bank accounts: $42,000
42 real fresh emails: $210
40 Full identities: $220
30 Unix roots: $75
etc etc.
There is one really big lesson that these prices can tell you: their persistence and their apparent attention to the laws of supply and demand mean that these are goods that have value, and will probably always have value.
Using legislative tools to squat the goods of value falls foul of Goodhart's law. You can use the tool, but it just pops up somewhere else. Legislation then is like any other drug, every hit gives you less and shorter pleasure, so you need more of it each time. You see where this is going? Think prohibition, etc, and look for other solutions.
If we agree on that, and then ignore the laws of economics, as a society (which is the case with the drugs czars), then all other observations feel rather specious. However, we can glean some insights of the marketplace from the above.
Firstly, those rich bank accounts must be reliable end-to-end, to be worth $1000 each. That is, money laundering at the scale needed is functioning very well, notwithstanding 2 decades' effort to address it. Like the drugs people, the anti-money laundering people would be well advised to study some economics before making their next move.
Secondly, security hasn't improved any, over time, and if anything it has been bedded into a status quo. OK, we knew that, but it is good to have some evidence of it.
Thirdly, the ratios of utility + security remain between Linux boxes and Windows boxes. This is a complex issue, though: on the one hand, Linux boxes are used to run core tasks from high-end ISPs, so their value is much higher. On the other hand, there are some views that Windows might have got more secure, and Linux might still be being compromised in large numbers. We just can't see that possibility from these numbers, because they reflect two things (being the relative utilities and the relative securities).
It would be very useful to show compromise numbers between the various brands. Nothing much else gets people to stop bickering and fluffing up their security feathers, and gets them back to work. If anything, the emergence of universal skepticism of Microsoft's security in the early 2000s was what caused Bill Gates to write his famous memo and attempt a turn-around. The same thing seems to be true of other organisations; the don't burst their own bubble of security hubris, others have to.
My dream metric for someone to produce would be this: Which brand of browser were you using when you were last phished, or otherwise had your bank account stolen? Which email client? And which operating system?
I suspect that only then will the posturing stop and developers start to really work on solutions. The reward is oh-so-much clearer: get those numbers down.
August 05, 2008
Monetary affairs on free reign, but the horse has Boulton'd
 The Fed roared into action mid July to rescue IndyMac, one of the USA's biggest banks. It's the normal story: toxic loans, payouts by the government, all accompanied by the USG moving to make matters worse. Chart of the week award goes to James Turk of Goldmoney:
The Fed roared into action mid July to rescue IndyMac, one of the USA's biggest banks. It's the normal story: toxic loans, payouts by the government, all accompanied by the USG moving to make matters worse. Chart of the week award goes to James Turk of Goldmoney:
One of the basic functions of a central bank is to act as the 'lender of last resort'. This facility is used to keep banks liquid during a period of distress.For example, if a bank is experiencing a run on deposits, it will borrow from the central bank instead of trying to liquidate some of its assets to raise the cash it needs to meet its obligations. In other words, the central bank offers a 'helping hand' by providing liquidity to the bank in need.
The following chart is from the Economic Research Department of the St. Louis Federal Reserve Bank. Here is the link: http://research.stlouisfed.org/fred2/series/BORROW. This long-term chart illustrates the amount of money banks have borrowed from the Federal Reserve from 1910 to the present.
This chart proves there is truth to the adage that a picture is worth a thousand words. It's one thing to say that the present financial crisis is unprecedented, but it is something all together different to provide a picture putting real meaning to the word 'unprecedented'.
It is an understatement to say that the U.S. banking system is in uncharted territory. The Federal Reserve is providing more than just a 'helping hand'.
Also check the original so you can see the source!
The problem with the "basic function" of the poetically-named 'lender of last resort' is that it is more a theory than a working practice. Such a thing has to be proven in action before we can rely on it. Unlike insurance, the lending of last resort function rarely gets proven, so it languishes until found to be broken in our very hour of need. Sadly, that is happening now in Switerland. Over at the Economist they also surveyed the Fed's recent attempts to prove their credibility in the same game. FM & FM were bailed out, and gave the dollar holder a salutory lesson. The mortgage backers were supposed to be private:
The belief in the implicit government guarantee allowed the pair to borrow cheaply. This made their model work. They could earn more on the mortgages they bought than they paid to raise money in the markets. Had Fannie and Freddie been hedge funds, this strategy would have been known as a “carry trade”.It also allowed Fannie and Freddie to operate with tiny amounts of capital. The two groups had core capital (as defined by their regulator) of $83.2 billion at the end of 2007 (see chart 2); this supported around $5.2 trillion of debt and guarantees, a gearing ratio of 65 to one. According to CreditSights, a research group, Fannie and Freddie were counterparties in $2.3 trillion-worth of derivative transactions, related to their hedging activities.
There is no way a private bank would be allowed to have such a highly geared balance sheet, nor would it qualify for the highest AAA credit rating. In a speech to Congress in 2004, Alan Greenspan, then the chairman of the Fed, said: “Without the expectation of government support in a crisis, such leverage would not be possible without a significantly higher cost of debt.” The likelihood of “extraordinary support” from the government is cited by Standard & Poor’s (S&P), a rating agency, in explaining its rating of the firms’ debt.
Now, we learn that FM & FM are government-sponsored enterprises, and the US is just another tottering socialist empire. OK, so the Central Bank, Treasury and Congress of the United States of America lied about the status of their subsidised housing economy. Now what? We probably would be wise to treat all other pronouncements with the skepticism due to a fundamentally flawed and now failing central monetary policy.
The illusion investors fell for was the idea that American house prices would not fall across the country. This bolstered the twins’ creditworthiness. Although the two organisations have suffered from regional busts in the past, house prices have not fallen nationally on an annual basis since Fannie was founded in 1938.... Of course, this strategy only raises another question. Why does America need government-sponsored bodies to back the type of mortgages that were most likely to be repaid? It looks as if their core business is a solution to a non-existent problem.
Although there is an obvious benefit in paying for good times, there is an obvious downside: you have to pay it back one day, and you pay it back double big in the down times, likely with liberal doses of salt in your gaping wounds. Welcome, Angst!
We keep coming back to the same old problem in the financial field as with, say, security, which is frequently written about in this blog. So many policies eventually founder on one flawed assumption: that we believe we know how to do it right.
However, Fannie and Freddie did not stick to their knitting. In the late 1990s they moved heavily into another area: buying mortgage-backed securities issued by others (see chart 3). Again, this was a version of the carry trade: they used their cheap financing to buy higher-yielding assets.
Why did they drift from the original mission?
Because they could. Because they were paid on results. Because it was fun. Because, they could be players, they could get some of that esteemed Wall Street respect.
 A thousand likely reasons, none of which are important, because the general truth here is that a subsidy will always turn around and hurt the very people who it intends to help. Washington DC's original intention of providing some nice polite subsidy would and must be warped to come around and bite them. Some day, some way.
A thousand likely reasons, none of which are important, because the general truth here is that a subsidy will always turn around and hurt the very people who it intends to help. Washington DC's original intention of providing some nice polite subsidy would and must be warped to come around and bite them. Some day, some way.
Sometimes the mortgage companies were buying each other’s debt: turtles propping each other up. Although this boosted short-term profits, it did not seem to be part of the duo’s original mission. As Mr Greenspan remarked, these purchases “do not appear needed to supply mortgage market liquidity or to enhance capital markets in the United States”.
References to the comments of Mr Greenspan are generally to be taken as insider financial code for the real story. Apparently also of Mervyn King, yet, evidently, neither is a wizard who can repair the dam before it breaches, merely farseers who can talk about the spreading cracks.
Now, the USA housing market gets what it deserves for its hubris. The problems for the rest of us are twofold: it drags everything else in the world down as well, and it is not as if those in the Central Banks, the Congresses, the Administrations or the Peoples of the world will learn the slightest bit of wisdom over this affair. Plan on this happening again in another few decades.
If you think I jest, you might like to invest in a new book by George Selgin entitled Good Money. Birmingham Button Makers, the Royal Mint, and the Beginnings of Modern Coinage, 1775-1821
Although it has long been maintained that governments alone are fit to coin money, the story of coining during Great Britain’s Industrial Revolution disproves this conventional belief. In fact, far from proving itself capable of meeting the monetary needs of an industrializing economy, the Royal Mint presided over a cash shortage so severe that it threatened to stunt British economic growth. For several decades beginning in 1775, the Royal Mint did not strike a single copper coin. Nor did it coin much silver, thanks to official policies that undervalued that metal.
To our great and enduring depression, the lesson of currency shortage was not learnt until after well after the events of the 1930s. The story of Matthew Boulton is salutory:
Late in 1797 Matthew Boulton finally managed to land his long-hoped-for regal coining contract, a story told in chapter five, “The Boulton Copper.” Once Boulton gained his contract, other private coiners withdrew from the business, fearing that the government was now likely to suppress their coins. Although the official copper coins Boulton produced were better than the old regal copper coinage had been, and were produced in large numbers, in many respects they proved less effective at addressing the coin shortage than commercial coins had been.
Eventually Boulton took part in the reform of the Royal Mint, equipping a brand new mint building with his steam-powered coining equipment. By doing so, Boulton unwittingly contributed to his own mint’s demise, because contrary to his expectations the government reneged on its promise to let him go on supplying British copper coin.
Then, policy was a charade and promises were not to be believed. Are we any better off now?
July 17, 2008
SEC starts to investigate Bear Stearns. Or does it?
If you read the last few days' posts on the crisis market sometimes but erroneously known as Banking (and you should check up on Lynn's comments on CDOs to see more detail) then you might be forgiven for thinking that the job of the regulators is to ride into town and clean up all the dirty games: subprime, CDOs and toxic mortgages. It could be that way, but the truth is more complicated.
The Bear Stearns affair is illustrative of the dilemmas. At one level, it's just another dirty chip in a card game where seedy reputations are being made, and dirty cards are being played, to mangle the metaphors. At another level, it is indicative that the problem is far more systemic than just another failed bank to be rescued.
In short, this story was about a major bank in the US that very nearly folded its cards. At the time, Bear Stearns went through its "Barings moment" when the bad news of its impending bankrupcy turned up late Friday. By next Monday, however, instead of collapsing, a white knight rescuer in the form of Goldman Sachs JP Morgan, a top-tier investment bank, turned up to offer a charitable price of $2 per share.
Bear-Stearns itself was major because it handled the biggest chunk of securities settlement. That is, the boring back-office task of swapping money for shares, or owners for owners, depending on how you look at it. Which brings to mind that if the major back-end settlement bank failed, this could clog the markets. Can you say systemic risk ?
Alan Greenspan can say that with authority, and this was what prompted his fabled rescue of another major player, LTCM (for Long Term Capital Management) back in the late 1990s. When LTCM was rescued from its too-big-to-comprehend positions, the financial world sucked much breath between collective teeth. Weren't we supposed to be passed the notion of rescuing failed financial players? Wasn't the Barings failure a wake-up call that we should take our risks and carry them too?
Was LTCM really that big?
In the event, Alan Greenspan proved to be the supreme player of poker: The Fed didn't spend any money on the deal, and instead fingered the banks who were to share the risk. A strong implication was that the big financial players (such as Morgan and Goldman) were in deep for the profits, and they should pay up for the losses. History suggests that he more or less got it right, or right enough, even to the extent of a few rebels who short-sold him and had to be punished later on.
For LTCM, the collective breath was slowly let out as the news and rumours trickled in as to how deep it was.
Because of its core role in settlements, Bear Stearns may have been the same, or maybe not. The financial brethren collectively drew breach in, but early fears of systemic risk were quickly replaced by cries of "rip-off!" Just exactly how did Goldman Sachs JPMorgan manage to engineer a bargain-basement price for a key player and competitor? After some huffing and puffing, the price went up to $10, which tells us something about the real value here.
Just maybe, the regulators have now moved to ask those questions:
BOSTON, July 16 (Reuters) - Dozens of hedge funds and broker dealers are scrambling to send reams of e-mails and trading records to U.S. regulators probing suspected stock price manipulation, several sources at hedge funds said.The U.S. Securities and Exchange Commission recently sent subpoenas to more than 50 firms concerning trading in investment banks Bear Stearns, which was rescued in March, and Lehman Brothers Holdings Inc (LEH.N: Quote, Profile, Research), whose shares have been hurt badly by rumors about its financial health, said four sources, who have seen the documents but were not authorized to speak about them publicly.
Among those receiving subpoenas was investment bank Goldman Sachs Group Inc (GS.N: Quote, Profile, Research) and prominent hedge fund firms SAC Capital Advisors LLC and Citadel Investment Group. All three were named in a recent article about the Bear collapse in Vanity Fair.
Is this good news? On the surface, it sounds like hard dealing. Finally, the regulators are riding into town. Hip hip hooray!
But a few things are disquieting, and cheers may be premature. Firstly, the regulators were already in on the deal, so they were already in-the-know. If they are now investigating a game they were in on, this looks no good: Either they were duped, or they were players.
Secondly, the SEC has no particularly good reputation for these sorts of investigations (remember Lazio, mutual funds, etc?). It is an agency that is thought to be understaffed, under-missioned, under-enforced and generally turns up to the party after the barn has burnt to the ground. Indeed, perhaps minded by the SEC's record as a political hired-gun, Congress is musing on the possibilities of a UK-style super-regulator, and/or handing that power to the Federal Reserve.
Thirdly, subpoenas are a two-edged sword. Although they might feed information to the issuer of the subpoena, they also shut down the information for anyone else. It's as simple as the players saying to everyone and anyone "we have no comment on running cases;" they've been handed a get-out-of-jail card at least as far as investigative reporting goes. Likewise, the subpoena is a club that can just as easily be wielded within an investment bank or hedge fund as against any outsider; it's a licence to martyr any whistleblower who might accidentally have a momentary attack of morals. Not only that, the information is now likely to be locked down within the SEC's investigation department, which would typically protect it fiercely for several years in a real investigation, and as long as it takes for the heat to die down in a political paid-favour.
Fourthly, of the investigations I have seen, the good ones are done quietly, with surgical strikes for information. A subpoena is sent only after other tools have been exhausted because it raises the stakes in the game so high. To send 50 out at once is about as surgical as carpet-bombing.
The overall sense then remains. The Bear Stearns affair smells, and rumour has it that the Brothers Lehman were seen washing at the same laundry. Who else? IndyMac? It might be a coincidence, but there is no end to the bad news for the USA Federal investigative and regulatory arms in recent years.
Which brings us to the point of the article, and the lesson as to why financial cryptographers read and understand the financial markets. The financial regulators promote a model of independent and fair regulation, but this is simply not the case. Briefly, sometimes, we experience periods in history where regulators do strive to stand apart and to regulate lightly and fairly. For the benefit of more than the incumbents. But more often than not, the regulators are the best heeled but least well-equipped players in a rigged game, always on the back foot, and operating to a steady series of political favours which will generally make matters worse.
With the retirement of Greenspan, and the political assassination of Spitzer, the USA markets are now normalising towards a stability of chaos. For financial cryptographers, then, it is important to understand that the structure of the market is dominating, and the regulators are players in that structure, not fair policemen, or designers of that structure. Enter that game at your peril, and if you do, understand it better than they do.
Addendum: of course, not getting the names right doesn't help understanding at all... JP Morgan bought Bear Stearns, not Goldman Sachs.
Mystified by subprime? ask the Telegraph...
Mystified by how 'sub-prime' debt engulfed Wall Street's smartest and now threatens the wider global economy? BigMac points to the Telegraph's comic strip, which might help explain how the story started:
 |
The credit crisis explained in black and white. |
Click to The Telegraph for partial comic strip |
Or to here for the fuller adult version... |
Or to here for the original slide show... |
... to which a comment on BoingBoing says: |
| "I have it on good sources that this was actually made at Countrywide Financial" |
| which explains why no-one wants their name on it! |
Also see The Economist on Freddie and Fannie: it's turtles all the way down!
July 16, 2008
Why do Banks lend poorly in the sub-prime market? Because they are not in Banking!
In a response to yesterday's post on the fall of the US dollar, Gunnar points out that incentives being out of alignment is no stranger to the banking world:
Interestingly enough Charlie Munger identified much the same themes (not all the particulars) way back in Wesco Financial's 1990 letter:Granting the presence of perverse incentives, what are the operating mechanics that cause widespread bad loans (where the higher interest rates do not adequately cover increased risk of loss) under our present system? After all, the bad lending, while it has a surface plausibility to bankers under cost pressure, is, by definition, not rational, at least for the lending banks and the wider civilization. How then does bad lending occur so often?It occurs (partly) because there are predictable irrationalities among people as social animals. It is now pretty clear (in experimental social psychology) that people on the horns of a dilemma, which is where our system has placed our bankers, are extra likely to react unwisely to the example of other peoples' conduct, now widely called "social proof". So, once some banker has apparently (but not really) solved his cost-pressure problem by unwise lending, a considerable amount of imitative "crowd folly", relying on the "social proof", is the natural consequence. Additional massive irrational lending is caused by "reinforcement" of foolish behavior, caused by unwise accounting convention in a manner discussed later in this letter. It is hard to be wise when the messages which drive you are wrong messages provided by a mal-designed system.
In order to understand what is going on in the market for banks, I think there is something that is extremely important to bear in mind. And this is:
banks are no longer in banking
In other words, it is more or less a myth these days that banks engage in banking, so whatever we think about banking, we shouldn't apply it to banks. How can this be? Well, let's get the theory straight: The concept of banking is this:
A market in which intermediaries borrow from the public on demand and lend to the public at term.
So, these intermediaries take on a risk between "demand deposits" and "term loans" that is captured in the interest rates and is protected by security. Etc etc. "Term" here means a long time, long enough such that there is no easy way to predict the economic future. This is a highly significant risk, and what causes banking to be different.
However, with the invention of securitization in the 1970s or so, while the intermediaries (sometimes known as banks) still borrowed from the public on demand, and created loans at term, they then went on to sell those term loans to the public. Banks are no longer lending at term, or more precisely are no longer exposed to the ramifications of term, themselves. They therefore enter into these term loans at little risk to themselves. Hence, although they are still styled as banks, and are regulated as "in banking", they are not actually engaging in the trade of banking. To be doing banking, you must engage in both sides of the equation; that special risk by being on both sides is the reason for the special subsidy and regulation of banking. Securitization removes that risk.
Hence, banks are now encouraged to do as many loans as possible, without worrying about the term risks. That is someone else's problem. Do I hear subprime ?
So while Charlie Menger's comment that there is a herd effect and a sociological effect that drives bad lending, the answer is much simpler. There is no dilemma, as banks don't need to lend wisely, they simply aren't at risk.
Having said that, it is going to take another decade or so for regulators and the public to wake up to this state of affairs. The banking subsidy is a licence to make money, and no bank wants to lose such a franchise, especially now that they've got out of the risky business of banking. It'd be a crime to let the easy money go!
Mystified by how 'sub-prime' debt engulfed Wall Street's smartest and now threatens the wider global economy? The Telegraph's comic strip may help explain how the story started.
July 15, 2008
The sorry tale of the US Dollar's long downwards spiral -- how did this happen?
Oil, geopolitics, those pesky Russians, irrational Bay Area exuberance, the drums of war, Sir Alan's folly, the cheeky Chinese, the conceit of monetarism, or, that inept circus known as the Bush Administration? We all know the dollar is collapsing, but what we don't know is (a) why, and (b) where to? JPM sent news last month of the latest RBS brief that says, in brief, to hell in a handbasket:
The Royal Bank of Scotland has advised clients to brace for a full-fledged crash in global stock and credit markets over the next three months as inflation paralyses the major central banks."A very nasty period is soon to be upon us - be prepared," said Bob Janjuah, the bank's credit strategist.
A report by the bank's research team warns that the S&P 500 index of Wall Street equities is likely to fall by more than 300 points to around 1050 by September as "all the chickens come home to roost" from the excesses of the global boom, with contagion spreading across Europe and emerging markets.
Heady stuff! The essential problem is that the US economy, and/or the government, and/or the Americans, has overspent.
The old story is the inflation one: too many dollars washing around causes too much investment, and then a little inflation, and a little more and a little more and a lot more ... until the government decides to put the brakes on because the lenders want more than can be returned. But the brakes take a few years to change the pace, and a few more years of pain and a few more years of rebuilding. By the time all the damage is repaired, we have forgotten where it came from, so nobody really believes this stuff anyway, and we're ready to live the good times again! It's our turn! Hysteresis being a wonderful thing, we enter what is quaintly called the Austrian Business Cycle, and the economy bounces around like a yoyo from generation to generation.
Except: supposedly with the death of Keynes and the rise of the Austrians and the new enlightened central banking age, we were supposed to be passed all that. What went wrong? That is what is flumoxing the fundamentalists amongst us. What we know is that we've never been here before, and like other complicated stories, there are *many factors*. Here's my attempt at listing the forces:
1. The 1990s Internet/tech boom caused a massive jolt to business, in effect a "productivity shock" albeit upwards. Productivity was kicked upwards in those areas effected. This released additional value into other areas, which had the effect of releasing additional investment into other areas. In a sense, the overall effect was inflationary, because the existing money stock was being used more effectively.
2. Because of the climb in productivity, the economy grew rapidly. This meant an increased demand for money, which central banks were happy to accomodate. However, because of the release of value, this also had the effect of increasing the supply of money. More inflation.
3. Around 2000, when most households in the USA had acquired their obligatory new-age accessory, the PC, the wheels came off the Internet boom. Which should have been expected to put an end to the general boom in the economy. Predictably, Alan Greenspan boosted up money creation to soften the blow.
4. In comes Bush: "Cry Havoc! and let slip the dogs of war!" Which unleashed the wildcats of spending. Well, maybe..., opinions might be divided on what the causes where, but the fact remains that this President has doubled the national debt of USA from 2001 to now, and that's one big achievement that we can all be proud of.
5. Which, as war talk inevitably does, leads to the observation that certain countries were targetted, and nobody has any clue what the metric was. If you know, please write in, with evidence if possible. Which, more importantly, resulted in an explosion of that old disease: Fear, Uncertainty and Doubt. In this case, monetary FUD meant that those who *might* be targetted worried about their over-dependency on that ultimate class of financial oil: the dollar.
 |
| Gold went up . . . . |
5.b Sometime around 2002-2003, countries started shifting out of the dollar. Slowly. Gently. Pretending not to. Refer to cartel and game theory to understand the theatre here. Either way, the shine was off, especially for those at the nexus of confusion: Islamic, oil-exporting, non-USA trade partners such as Libya, Iran, Iraq.
6. Which was extraordinarily lucky for Europe, as just around the right time, the Euro burst into life, giving a currency of impeccable (Bundesbank) anti-inflation credentials. The Bundesbank was located in Frankfurt. The ECB is located in Frankfurt, too. This is no accident. So, countries found it relatively easy to justify shifting a large part of their reserves to Euros. Slowly, Gently, Pretending Everything But.
7. Which meant all this dollar surplus went washing back to the US, at around the same time as the Bush administration was borrowing more, spending more, warring more. It may never be officially confirmed, but the Fed was on the case by 2003, and managing the process of absorbing a more than normal homeward bound flow of dollars. Not a happy picture. Monetarily speaking, although the tech boom was over, the money boom carried on, and there wasn't a darn thing the Fed could do about it, because those darn foreigners insisted on buying real assets in paper dollars. Hello, housing boom.
8. The dollar went down. Consistently, from around 2001. Which would have been fine, all things being equal, as this just means we buy less Airbuses, more Boeings, etc, until it all balances out.
9. However, as the dollar was the trading currency of the world, things were decidedly not equal. By fiat of Bretton Woods, as it were. Monetary policy has never really considered wholesale redemptions by the world's customers, so it was an open question as to what would happen. In this case, those wiley Europeans, those cunning Chinese, those devilish Japanese, and even the happy go lucky Aussies ... all decided to *help the Fed*. And, help in this case, turned out to be letting their currencies go down as well. Which means, they issued more money, and inflated under the umbrella, while the Fed was swallowing more, while the Bush administration was borrowing more. In essence, this meant the real corrections were delayed and hidden, because the currency markets were more or less in balance.
10. Not so real assets: Gold went up. Housing boomed. Dollars went down, and the other nationals went downish, enjoying the chance, because they won profit by their favour to the Fed. And, what happens when everyone inflates at the same time?
11. Commodities first, but then foodstuffs, and finally ordinary stuff went up in price. Tech stuff still continued going down because the tech machine was still rolling, if not booming. Stuff that was made in the new wunderfabrik of China went down in price, as that vast empire of cheap labour opened up. In sum, nobody noticed that the central banks, all of them, were stealing the bounty of the lowering dollar, the tech productivity shock, and the China export trade. So much for the vaunted anti-inflation reputations.
 12. Hence, in short summary, the military expenditures took over from the tech bubble. The dogs-of-war chased dollar-holders who went scurrying across to the Euro, creating a dollar bubble which underwrote the housing bubble. All hard assets boomed around the western world. Everything boomed in the US, except fiscal balance.
12. Hence, in short summary, the military expenditures took over from the tech bubble. The dogs-of-war chased dollar-holders who went scurrying across to the Euro, creating a dollar bubble which underwrote the housing bubble. All hard assets boomed around the western world. Everything boomed in the US, except fiscal balance.
13. Which all came to a close when the oil shock hit. The shock was triggered by the boys-own adventures of Bush and his chums in the great game (a euphemism for interference and manipulation in the Middle East). However, be careful: we have to factor in around 50 years of manipulation of the oil supply industry, which caused an imbalance waiting to collapse. This supply-side manipulation can be seen in new oil fields like Alaska, there is so much oil washing around there that some say that if it were fed to the US market, the prices would drop to around zero and Kissinger's fabled contracts with the sheikhs would collapse. Which would collapse the dollar. Apparently, if there's anything that Washington fears more than an open market in Middle Eastern democracy, it is an open market in oil.
14. Never minding the source of the shock, it was the straw that broke the camel's back: Cash that was previously washing around from other sources was sucked up by the new demands on oil (which feeds into practically every other sector of the physical goods economy) and this caused the investment, housing and other booms to break. Then, the fundamentalists (those traders who believe in long term trends and numbers) started to take a good hard look at the real numbers, and people got scared. "Withdraw from everything!" ...
Fundamentalists knew the USA economy was out of balance in around 2000, when the tech bubble burst ... something should have happened then, but to our surprise, nothing much happened (unless you had a tech job, that was pretty dire). What caught us out is how many other factors were involved, how deep the USA trap was, and how long it took for these huge, massive imbalances to come home to roost. If it is any comfort, this is going to be as well studied as the Great Recession, for the same reasons: the monetary authorities and the governments got it all wrong.
Here we are, staring at recession. It's hard to recommend what to do, but it should be to reduce dependency on the US dollar, anyway you can. Whatever you have in mind, do it quickly.
The sorry tale of the US Dollar's long downwards spiral -- how did this happen?
Oil, geopolitics, those pesky Russians, irrational Bay Area exuberance, the drums of war, Sir Alan's folly, the cheeky Chinese, the conceit of monetarism, or, that inept circus known as the Bush Administration? We all know the dollar is collapsing, but what we don't know is (a) why, and (b) where to? JPM sent news last month of the latest RBS brief that says, in brief, to hell in a handbasket:
The Royal Bank of Scotland has advised clients to brace for a full-fledged crash in global stock and credit markets over the next three months as inflation paralyses the major central banks."A very nasty period is soon to be upon us - be prepared," said Bob Janjuah, the bank's credit strategist.
A report by the bank's research team warns that the S&P 500 index of Wall Street equities is likely to fall by more than 300 points to around 1050 by September as "all the chickens come home to roost" from the excesses of the global boom, with contagion spreading across Europe and emerging markets.
Heady stuff! The essential problem is that the US economy, and/or the government, and/or the Americans, has overspent.
The old story is the inflation one: too many dollars washing around causes too much investment, and then a little inflation, and a little more and a little more and a lot more ... until the government decides to put the brakes on because the lenders want more than can be returned. But the brakes take a few years to change the pace, and a few more years of pain and a few more years of rebuilding. By the time all the damage is repaired, we have forgotten where it came from, so nobody really believes this stuff anyway, and we're ready to live the good times again! It's our turn! Hysteresis being a wonderful thing, we enter what is quaintly called the Austrian Business Cycle, and the economy bounces around like a yoyo from generation to generation.
Except: supposedly with the death of Keynes and the rise of the Austrians and the new enlightened central banking age, we were supposed to be passed all that. What went wrong? That is what is flumoxing the fundamentalists amongst us. What we know is that we've never been here before, and like other complicated stories, there are *many factors*. Here's my attempt at listing the forces:
1. The 1990s Internet/tech boom caused a massive jolt to business, in effect a "productivity shock" albeit upwards. Productivity was kicked upwards in those areas effected. This released additional value into other areas, which had the effect of releasing additional investment into other areas. In a sense, the overall effect was inflationary, because the existing money stock was being used more effectively.
2. Because of the climb in productivity, the economy grew rapidly. This meant an increased demand for money, which central banks were happy to accomodate. However, because of the release of value, this also had the effect of increasing the supply of money. More inflation.
3. Around 2000, when most households in the USA had acquired their obligatory new-age accessory, the PC, the wheels came off the Internet boom. Which should have been expected to put an end to the general boom in the economy. Predictably, Alan Greenspan boosted up money creation to soften the blow.
4. In comes Bush: "Cry Havoc! and let slip the dogs of war!" Which unleashed the wildcats of spending. Well, maybe..., opinions might be divided on what the causes where, but the fact remains that this President has doubled the national debt of USA from 2001 to now, and that's one big achievement that we can all be proud of.
5. Which, as war talk inevitably does, leads to the observation that certain countries were targetted, and nobody has any clue what the metric was. If you know, please write in, with evidence if possible. Which, more importantly, resulted in an explosion of that old disease: Fear, Uncertainty and Doubt. In this case, monetary FUD meant that those who *might* be targetted worried about their over-dependency on that ultimate class of financial oil: the dollar.
 |
| Gold went up . . . . |
5.b Sometime around 2002-2003, countries started shifting out of the dollar. Slowly. Gently. Pretending not to. Refer to cartel and game theory to understand the theatre here. Either way, the shine was off, especially for those at the nexus of confusion: Islamic, oil-exporting, non-USA trade partners such as Libya, Iran, Iraq.
6. Which was extraordinarily lucky for Europe, as just around the right time, the Euro burst into life, giving a currency of impeccable (Bundesbank) anti-inflation credentials. The Bundesbank was located in Frankfurt. The ECB is located in Frankfurt, too. This is no accident. So, countries found it relatively easy to justify shifting a large part of their reserves to Euros. Slowly, Gently, Pretending Everything But.
7. Which meant all this dollar surplus went washing back to the US, at around the same time as the Bush administration was borrowing more, spending more, warring more. It may never be officially confirmed, but the Fed was on the case by 2003, and managing the process of absorbing a more than normal homeward bound flow of dollars. Not a happy picture. Monetarily speaking, although the tech boom was over, the money boom carried on, and there wasn't a darn thing the Fed could do about it, because those darn foreigners insisted on buying real assets in paper dollars. Hello, housing boom.
8. The dollar went down. Consistently, from around 2001. Which would have been fine, all things being equal, as this just means we buy less Airbuses, more Boeings, etc, until it all balances out.
9. However, as the dollar was the trading currency of the world, things were decidedly not equal. By fiat of Bretton Woods, as it were. Monetary policy has never really considered wholesale redemptions by the world's customers, so it was an open question as to what would happen. In this case, those wiley Europeans, those cunning Chinese, those devilish Japanese, and even the happy go lucky Aussies ... all decided to *help the Fed*. And, help in this case, turned out to be letting their currencies go down as well. Which means, they issued more money, and inflated under the umbrella, while the Fed was swallowing more, while the Bush administration was borrowing more. In essence, this meant the real corrections were delayed and hidden, because the currency markets were more or less in balance.
10. Not so real assets: Gold went up. Housing boomed. Dollars went down, and the other nationals went downish, enjoying the chance, because they won profit by their favour to the Fed. And, what happens when everyone inflates at the same time?
11. Commodities first, but then foodstuffs, and finally ordinary stuff went up in price. Tech stuff still continued going down because the tech machine was still rolling, if not booming. Stuff that was made in the new wunderfabrik of China went down in price, as that vast empire of cheap labour opened up. In sum, nobody noticed that the central banks, all of them, were stealing the bounty of the lowering dollar, the tech productivity shock, and the China export trade. So much for the vaunted anti-inflation reputations.
 12. Hence, in short summary, the military expenditures took over from the tech bubble. The dogs-of-war chased dollar-holders who went scurrying across to the Euro, creating a dollar bubble which underwrote the housing bubble. All hard assets boomed around the western world. Everything boomed in the US, except fiscal balance.
12. Hence, in short summary, the military expenditures took over from the tech bubble. The dogs-of-war chased dollar-holders who went scurrying across to the Euro, creating a dollar bubble which underwrote the housing bubble. All hard assets boomed around the western world. Everything boomed in the US, except fiscal balance.
13. Which all came to a close when the oil shock hit. The shock was triggered by the boys-own adventures of Bush and his chums in the great game (a euphemism for interference and manipulation in the Middle East). However, be careful: we have to factor in around 50 years of manipulation of the oil supply industry, which caused an imbalance waiting to collapse. This supply-side manipulation can be seen in new oil fields like Alaska, there is so much oil washing around there that some say that if it were fed to the US market, the prices would drop to around zero and Kissinger's fabled contracts with the sheikhs would collapse. Which would collapse the dollar. Apparently, if there's anything that Washington fears more than an open market in Middle Eastern democracy, it is an open market in oil.
14. Never minding the source of the shock, it was the straw that broke the camel's back: Cash that was previously washing around from other sources was sucked up by the new demands on oil (which feeds into practically every other sector of the physical goods economy) and this caused the investment, housing and other booms to break. Then, the fundamentalists (those traders who believe in long term trends and numbers) started to take a good hard look at the real numbers, and people got scared. "Withdraw from everything!" ...
Fundamentalists knew the USA economy was out of balance in around 2000, when the tech bubble burst ... something should have happened then, but to our surprise, nothing much happened (unless you had a tech job, that was pretty dire). What caught us out is how many other factors were involved, how deep the USA trap was, and how long it took for these huge, massive imbalances to come home to roost. If it is any comfort, this is going to be as well studied as the Great Recession, for the same reasons: the monetary authorities and the governments got it all wrong.
Here we are, staring at recession. It's hard to recommend what to do, but it should be to reduce dependency on the US dollar, anyway you can. Whatever you have in mind, do it quickly.
July 11, 2008
wheretofore Vista? Microsoft moves to deal with the end of the Windows franchise
Since the famous Bill Gates Memo, around the same time as phishing and related frauds went institutional, Microsoft has switched around to deal with the devil within: security. In so doing, it has done what others should have done, and done it well. However, there was always going to be a problem with turning the super-tanker called Windows into a battleship.
I predicted a while back that (a) Vista would probably fail to make a difference, and (b) the next step was to start thinking of a new operating system. This wasn't the normal pique, but the cold-hearted analysis of the size of the task. If you work for 20 years making your OS easy but insecure, you don't have much chance of fixing that, even with the resources of Microsoft.
The Economist brings an update on both points. Firstly, on Vista's record after 18 months in the market:
To date, some 140m copies of Vista have been shipped compared with the 750m or more copies of XP in daily use. But the bulk of the Vista sales have been OEM copies that came pre-installed on computers when they were bought. Anyone wanting a PC without Vista had to order it specially.Meanwhile, few corporate customers have bought upgrade licences they would need to convert their existing PCs to Vista. Overwhelmingly, Windows users have stuck with XP.
Even Microsoft now seems to accept that Vista is never going to be a blockbuster like XP, and is hurrying out a slimmed-down tweak of Vista known internally as Windows 7. This Vista lite is now expected late next year instead of 2010 or 2011.
It's not as though Vista is a dud. Compared with XP, its kernel—the core component that handles all the communication between the memory, processor and input and output devices—is far better protected from malware and misuse. And, in principle, Vista has better tools for networking. All told, its design is a definite improvement—albeit an incremental one—over XP.
Microsoft tried and failed to turn it around, security+market-wise. We might now be looking at the end of the franchise known as Windows. To be clear, while we are past the peak, any ending is a long way off in the distant future.
Classical strategy thinking says that there are two possible paths here: invest in a new franchise, or go "cash-cow". The latter means that you squeeze the revenues from the old franchise as long as possible, and delay the termination of the franchise as long as possible. The longer you delay the end, the more revenues you get. The reason for doing this is simple: there is no investment strategy that makes money, so you should return the money to the shareholders. There is a simple example here: the music majors are decidedly in cash-cow, today, because they have no better strategy than delaying their death by a thousand file-shares.
Certainly, with Bill Gates easing out, it would be possible to go cash-cow, but of course, we on the outside can only cast our augeries and wonder at the signs. The Economist suggests that they may have taken the investment route:
Judging from recent rumours, that's what it is preparing to do. Even though it won't be in Windows 7, Microsoft is happy to talk about “MinWin”—a slimmed down version of the Windows core. It’s even willing to discus its “Singularity” project—a microkernel-based operating system written strictly for research purposes. But ask about a project code-named “Midori” and everyone clams up.By all accounts, Midori (Japanese for “green” and, by inference, “go”) capitalises on research done for Singularity. The interesting thing about this hush-hush operating system is that it’s not a research project in the normal sense. It's been moved out of the lab and into incubation, and is being managed by some of the most experienced software gurus in the company.
With only 18 months before Vista is to be replaced, there's no way Midori—which promises nothing less than a total rethink of the whole Windows metaphor—could be ready in time to take its place. But four or five years down the road, Microsoft might just confound its critics and pleasantly surprise the rest of us.
Comment? Even though I predicted Microsoft would go for a new OS, I think this is a tall order. There are two installed bases in the world today, being Unix and Windows. It's been that way for a long time, and efforts to change those two bases have generally failed. Even Apple gave up and went Unix. (The same economics works against the repeated attempts to upgrade the CPU instruction set.)
The flip-side of this is that the two bases are incredibly old and out-of-date. Unix's security model is "ok" but decidedly pre-PC, much of what it does is simply irrelevant to the modern world. For example, all the user-to-user protection is pointless on a one-user-one-PC environment, and the major protection barrier has accidentally become a hack known as TCP/IP, legendary for its inelegant grafting onto Unix. Windows has its own issues.
So we know two things: a redesign is decades over-due. And it won't budge the incumbents; both are likely to live another decade without appreciable change to the markets. We would need a miracle, or better, a killer-app to budge the installed base.
Hence the cold-hearted analysis of cash-cow wins out.
But wait! The warm-blooded humanists won't let that happen for one and only one reason: it is simply too boring to contemplate. Microsoft has so many honest, caring, devoted techies within that if a decision were made to go cash-cow, there would be a mass-defection. So the question then arises, what sort of a hybrid will be acceptable to shareholders and workers? Taking a leaf from recent politics, which is going through a peak-energy-masquerade of its own these days, some form of "green platform" has appeal to both sides of the voting electorate.
June 30, 2008
Cross-border Notarisations and Digital Signatures
My notes of a presentation by Dr Ugo Bechini at the Int. Conf. on Digital Evidence, London. As it touches on many chords, I've typed it up for the blog:
The European or Civil Law Notary is a powerful agent in commerce in the civil law countries, providing a trusted control of a high value transaction. Often, this check is in the form of an Apostille which is (loosely) a stamp by the Notary on an official document that asserts that the document is indeed official. Although it sounds simple, and similar to common law Notaries Public, behind the simple signature is a weighty process that may be used for real estate, wills, etc.
It works, and as Eliana Morandi puts it, writing in the 2007 edition of the Digital Evidence and Electronic Signature Law Review:
Clear evidence of these risks can be seen in the very rapid escalation, in common law countries, of criminal phenomena that are almost unheard of in civil law countries, at least in the sectors where notaries are involved. The phenomena related to mortgage fraud is particularly important, which the Mortgage Bankers Association estimates to have caused the American system losses of 2.5 trillion dollars in 2005.
OK, so that latter number came from Choicepoint's "research" (referenced somewhere here) but we can probably agree that the grains of truth sum to many billions.
Back to the Notaries. The task that they see ahead of them is to digitise the Apostille, which to some simplification is seen as a small text with a (dig)sig, which they have tried and tested. One lament common in all European tech adventures is that the Notaries, split along national lines, use many different systems: 7 formats indicating at at least 7 softwares, frequent upgrades, and of course, ultimately, incompatibility across the Eurozone.
To make notary documents interchangeable, there are (posits Dr Bechini) two solutions:
- a single homogenous solution for digsigs; he calls this the "GSM" solution, whereas I thought of it as a potential new "directive failure".
- a translation platform; one-stop shop for all formats
A commercial alternative was notably absent. Either way, IVTF (or CNUE) has adopted and built the second solution: a website where documents can be uploaded and checked for digsigs; the system checks the signature, the certificate and the authority and translates the results into 4 metrics:
- Signed - whether the digsig is mathematically sound
- Unrevoked - whether the certificate has been reported compromised
- Unexpired - whether the certificate is out of date
- Is a notary - the signer is part of a recognised network of TTPs
In the IVTF circle, a notary can take full responsibility for a document from another notary when there are 4 green boxes above, meaning that all 4 things check out.
This seems to be working: Notaries are now big users of digsigs, 3 million this year. This is balanced by some downsides: although they cover 4 countries (Deustchland, España, France, Italy), every additional country creates additional complexity.
Question is (and I asked), what happens when the expired or revoked certificate causes a yellow or red warning?
The answer was surprising: the certificates are replaced 6 months before expiry, and the messages themselves are sent on the basis of a few hours. So, instead of the document being archived with digsig and then shared, a relying Notary goes back to the originating Notary to request a new copy. The originating Notary goes to his national repository, picks up his *original* which was registered when the document was created, adds a fresh new digsig, and forwards it. The relying notary checks the fresh signature and moves on to her other tasks.
You can probably see where we are going here. This isn't digital signing of documents, as it was envisaged by the champions of same, it is more like real-time authentication. On the other hand, it does speak to that hypothesis of secure protocol design that suggests you have to get into the soul of your application: Notaries already have a secure way to archive the documents, what they need is a secure way to transmit that confidence on request, to another Notary. There is no problem with short term throw-away signatures, and once we get used to the idea, we can see that it works.
One closing thought I had was the sensitivity of the national registry. I started this post by commenting on the powerful position that notaries hold in European commerce, the presenter closed by saying "and we want to maintain that position." It doesn't require a PhD to spot the disintermediation problem here, so it will be interesting to see how far this goes.
A second closing thought is that Morandi cites
... the work of economist Hernando de Soto, who has pointed out that a major obstacle to growth in many developing countries is the absence of efficient financial markets that allow people to transform property, first and foremost real estate, into financial capital. The problem, according to de Soto, lies not in the inadequacy of resources (which de Soto estimates at approximately 9.34 trillion dollars) but rather in the absence of a formal, public system for registering property rights that are guaranteed by the state in some way, and which allows owners to use property as collateral to obtain access to the financial captal associated with ownership.
But, Latin America, where de Soto did much of his work, follows the Civil Notary system! There is an unanswered question here. It didn't work for them, so either the European Notaries are wrong about their assertation that this is the reason for no fraud in this area, or de Soto is wrong about his assertation as above. Or?
June 15, 2008
Selling Security using Prospect Theory. Or not.
Bruce Schneier writes a good essay on Prospect Theory and how this effects selling of security. The basic story is that people accept a risk-free smaller gain, but gamble with a risky larger loss; our decisions are not symmetric, and do not follow "utility" or "expected value" lines. Given that we gamble big with losses, he closes the essay with:
How does Prospect Theory explain the difficulty of selling the prevention of a security breach? It's a choice between a small sure loss -- the cost of the security product -- and a large risky loss: for example, the results of an attack on one's network. Of course there's a lot more to the sale. The buyer has to be convinced that the product works, and he has to understand the threats against him and the risk that something bad will happen. But all things being equal, buyers would rather take the chance that the attack won't happen than suffer the sure loss that comes from purchasing the security product.Security sellers know this, even if they don't understand why, and are continually trying to frame their products in positive results. That's why you see slogans with the basic message, "We take care of security so you can focus on your business," or carefully crafted ROI models that demonstrate how profitable a security purchase can be. But these never seem to work. Security is fundamentally a negative sell.
One solution is to stoke fear. Fear is a primal emotion, far older than our ability to calculate trade-offs. And when people are truly scared, they're willing to do almost anything to make that feeling go away; lots of other psychological research supports that. Any burglar alarm salesman will tell you that people buy only after they've been robbed, or after one of their neighbors has been robbed. And the fears stoked by 9/11, and the politics surrounding 9/11, have fueled an entire industry devoted to counterterrorism. When emotion takes over like that, people are much less likely to think rationally.
Though effective, fear mongering is not very ethical. The better solution is not to sell security directly, but to include it as part of a more general product or service. Your car comes with safety and security features built in; they're not sold separately. Same with your house. And it should be the same with computers and networks. Vendors need to build security into the products and services that customers actually want. CIOs should include security as an integral part of everything they budget for. Security shouldn't be a separate policy for employees to follow but part of overall IT policy.
Security is inherently about avoiding a negative, so you can never ignore the cognitive bias embedded so deeply in the human brain. But if you understand it, you have a better chance of overcoming it.
Using Prospect Theory here is interesting, and finance theory also has something similar to say: companies close to big losses are encouraged to gamble more.
It is also more evidence that the sellers of security do not have an advantage in selling security: buyers do not believe the messages, and only buy due to external issues. Establishing that will knock-down the 'lemons' thesis that security is a market with a seller's advantage, and suggest that it is a market in silver bullets, with no advantage.
It is also more evidence in a trend I noticed a while back but have not adequately formalised (ftr, Bruce Schneier may have spotted it first from Counterpane's recent history). What happens when the security industry collapses and is no longer an industry in its own right? Who then does security? The rest of industry, that's who: security moves back from being a specialisation captured by the enlightened few to a general skill that all need. It's your job, do it.
But, there be dragons. As is well known for a long time: if buyers do not value the security, then general purpose suppliers do not supply it. Supplying something not wanted doesn't help sales, of course, and this is what Microsoft did throughout the 80s and 90s, until the famous memo a handful of years back. So even though the security pendulum is swinging away from the dysfunctional specialist priesthood back to the generalist skilled area, we already know that we have a problem with the demand side of the equation, and that side is also dysfunctional.
Much food for thought.
June 07, 2008
Negroponte's judo flip on the PC industry
Sometimes we get to watch a structural change unfold before our eyes. The Intel 64bit mistake that let AMD in was one such; the Napster story another, and now, we are seeing the endings of another. Again against Intel, the OLPC, the so-called $100 laptop, has succeeded in creating a new segment. The Economist writes:
But in one respect the XO Laptop has undoubtedly made an impact: by helping to spawn a new market for low-cost laptops. Hardly any models costing $500 or less were available when the XO burst onto the scene, but now there is a wide selection of such machines, from familiar makers such as HP and Intel, and from relative newcomers such as Asus and Pioneer Computers. By raising the very possibility of a $100 laptop, the XO presented the industry with a challenge. Wayan Vota, founder of OLPCNews.com, an independent website that follows the project, calls the XO a “harbinger of an entirely new class of computers”.
Structure matters. In the market for PCs, there is a basic difference between the desktop and the laptop. Students of economics will realise that this distinction can act to discriminate between those who want to spend more and those who want to spend less. And so it is: in computer sales, the desktops inhabit the bottom end, and personal computing for the well-heeled is dominated by laptops.
In simple terms, if you can afford a laptop, you get a laptop. If not, you get a desktop. Again in economics-speak, this discrimination captures more of the consumer surplus (your spare cash), provides improved Hayekian information to manufacturers (what you really want), and ultimately leads to better and cheaper products for all.
This had the rather odd effect that although computers kept on getting better and better, laptops were not getting cheaper, only better. Indeed, those older models which were clearly suitable once and therefore would be adequate now, and cheaper, were instead being consistently stripped from the market. By common agreement, the bottom end laptop was scrubbed out.
This apparently breaks Moore's law, which implies that the same thing should get cheaper over time. Where's the cheaper laptop? Negroponte must have asked this very question, and known that given everything else we know about the computing industry, there should have been a cheaper laptop.
As described above, we know the reason there is none, but that stability is by consensus with the consumers and makers. There is nothing wrong with actually building one, and breaking the stability. And this is what Negroponte did: build something that was possible, but the market had avoided because of price discrimination reasons.
There are strong emotions about the OLPC. No matter what you think about the design, the OS, the choices, the sales or the cute green ears, one thing is clear: Negroponte succeeded in doing a judo flip on Intel, Asus and the other manufacturers, and creating the new segment. Once he had succeeded to the extent that he could sell them, other laws of competition kicked in, and the manufacturers were forced to follow.
Although the Classmate may have stolen some of the XO’s thunder in the developing world, another low-cost laptop has been a runaway success in the developed world. The tiny Asus Eee PC, little bigger than a paperback book and weighing less than a kilogram, sold more than 300,000 units in 2007 alone. It is now available in several versions: the most basic model, with a seven-inch screen, costs $299, and a new high-end model with a nine-inch screen costs $549. HP, the world’s biggest PC-maker, entered this new market in April with the “Mini-Note”, a small laptop weighing just over a kilogram. It too will cost under $500.All of these new machines are being aimed at consumers in the rich world, who like the idea of a computer that can be taken anywhere, as well as being sold for educational use in poor countries. The $100 laptop has been a success—just not, so far, in the way its makers intended.
In the end, the fate of the OLPC is less interesting, and discussions about whether the OLPC succeeded or not miss the point. The real point is that the segment is now created. Thanks to Nicholas Negroponte, students of business now have a new case study in market structure and price discrimination, and everyone else now has a cheap laptop.
May 10, 2008
What makes a Security Project?
Why is it that when you come across a good new thought, it is harder to deal with than an old, rehashed thought? I struggle with this all the time: E.g., blogs. my favourite ones are the writers that do original and new thinking. These guys nibble and munch at problems until they find answers. Then they bake solutions. These posts are so full of good stuff that I don't know where or how to respond. On the other hand, my unfavourite blogs are the ones that stick very clearly in the middle ground, express mildly polemic thoughts that a majority agree with and a minority already said, and seem to spend more time collecting and building popular support than anything useful.
Lots of good posts these days over at Gunnar's area, and I can't easily respond to them.
I see no evidence that [Sun] understand the need for writing secure code more so than Microsoft. In fact I see every evidence that Sun is several years behind Microsoft on software security. Let's do the list - Howard/Leblanc's work, threat modeling, software security patterns and practices, SDL, SecPal, BlueHat, OWASP guidance work and that is all before we get to identity stuff.
You won't see such an ... *opinion* from the popular fence sitters! Why is this? I think it is for several reasons. To say such a thing means you court disfavour with large companies, including the one you named, but also other companies who might realise you are likely to bark with more bite than other tame consultants.
Further, one has to think of the evidence to back up the opinion, and that's not always easy. I know because I tried to clarify this three years ago, while dealing with the question. When I sat and thought about why I thought some organisations weren't up to scratch, I had no easy answers. So I wrote down everything I could think of ... and then judged every organisation I knew on my list of metrics.
For once, then, I can respond to Gunnar, and in full wide-screen TV mode:
| Points -> | Source | Disclosure | Goal of Security | Security Czar | Audit Project | Risks & Threats | Crypto | Total Points | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Projects | read | open | compete | patches | weak- nesses | mistakes | espoused | formal- ised | intern- alised | appointed | has power | and uses it... | started | mile- stones | cycled | aligned | active | stats | rebels | full | |
| OpenBSD |  |  |  |  | ??? | ??? |  |  |  |  |  |  |  |  | ??? |  |  |  |  |  | 16 |
| FreeBSD |  |  |  |  | ??? | ??? |  | ??? |  |  |  |  |  |  | ??? |  |  |  |  |  | 15 |
| OpenSSH |  |  | ??? |  |  |  |  | ??? |  |  |  |  |  | ??? | ??? |  |  |  |  |  | 14 |
| PGP Inc |  |  |  |  |  |  |  |  |  |  |  | ??? | ??? | ??? | ??? |  |  |  |  |  | 12 |
| GnuPG |  |  |  |  |  | ??? |  |  |  | ??? | ??? | ??? | ??? | ??? | ??? |  |  |  |  |  | 11 |
| ZSentry |  |  |  | ??? | ??? | ??? |  | ??? |  |  |  | ??? |  |  |  |  |  |  |  |  | 9 |
| Mozilla |  |  |  |  |  |  |  |  |  |  |  |  |  | ??? | ??? |  |  |  |  |  | 7 |
| OpenSSL |  |  |  |  | ??? |  | ??? | ??? | ??? |  |  |  | ??? | ??? | ??? |  |  |  |  |  | 7 |
| Linux |  |  |  |  | ??? | ??? |  |  |  |  |  |  | ??? | ??? | ??? |  |  |  |  |  | 7 |
| Hushmail |  |  |  | ??? | ??? | ??? | ??? | ??? | ??? | ??? | ??? | ??? | ??? | ??? | ??? |  |  |  |  |  | 7 |
| Microsoft |  |  |  |  |  |  |  |  |  | ??? | ??? | ??? |  |  | ??? |  |  |  |  |  | 6 |
| Java |  |  |  |  |  |  |  |  |  |  |  |  |  |  | ??? |  |  |  |  |  | 6 |
| Ciphire |  |  |  | ??? |  | ??? | ??? | ??? | ??? | ??? | ??? | ??? |  |  | ??? |  |  |  |  |  | 6 |
| Skype |  |  |  |  |  |  |  |  |  | ??? | ??? | ??? | ??? | ??? | ??? |  |  |  |  |  | 4 |
| Ricardo |  |  |  |  |  | ??? |  |  |  |  |  |  |  |  |  |  |  |  |  |  | 10 |
To make sense of that, you will have to check out the fuller essay. Even then, note that it was never finished, and the opinions are already 3 years old. As to whether Gunnar is right, check the table metrics, calculate your view and decide for yourself!
The Italian Job: highlights the gap between indirect and direct damage
If you've been following the story of the Internet and Information Security, by now you will have worked out that there are two common classes of damage that are done when data is breached: The direct damage to the individual victims and the scandal damage to the organisation victim when the media get hold of it. From the Economist:
Illustration by Peter Schrank ... Italians had learnt, to their varying dismay, amusement and fascination, that—without warning or consultation with the data-protection authority—the tax authorities had put all 38.5m tax returns for 2005 up on the internet. The site was promptly jammed by the volume of hits. Before being blacked out at the insistence of data protectors, vast amounts of data were downloaded, posted to other sites or, as eBay found, burned on to disks.
The uproar in families and workplaces caused by the revelation of people's incomes (or, rather, declared incomes) can only be guessed at. A society aristocrat, returning from St Tropez, found himself explaining to the media how he financed a gilded lifestyle on earnings of just €32,043 ($47,423). He said he had generous friends.
...Vincenzo Visco, who was responsible for stamping out tax dodging, said it promoted “transparency and democracy”. Since the 1970s, tax returns have been sent to town halls where they can be seen by the public (which is how incomes of public figures reach the media). Officials say blandly that they were merely following government guidelines to encourage the use of the internet as a means of communication.
The data-protection authority disagreed. On May 6th it ruled that releasing tax returns into cyberspace was “illicit”, and qualitatively different from making them available in paper form. It could lead to the preparation of lists containing falsified data and meant the information would remain available for longer than the 12 months fixed by law.
The affair may not end there. A prosecutor is investigating if the law has been broken. And a consumer association is seeking damages. It suggests €520 per taxpayer would be appropriate compensation for the unsolicited exposure.
An insight of the 'silver bullets' approach to the market is that these damages should be considered separately, not lumped together. The one that is the biggest cost will dominate the solution, and if the two damages suggest opposing solutions, the result may be at the expense of the weaker side.
What makes Information Security so difficult is that the public scandal part of the damage (the indirect component) is generally the greater damage. Hence, breaches have been classically hushed up, and the direct damages to the consumers are untreated. In this market, then, the driving force is avoiding the scandal, which not only means that direct damage to the consumer is ignored, it is likely made worse.
We then see more evidence of the (rare) wisdom of breach disclosure laws, even if, in this case, the breach was a disclosure by intention. The legal action mentioned above puts a number on the direct damage to the consumer victim. We may not agree with €520, but it's a number and a starting position that is only possible because the breach is fully out in the open.
Those then that oppose stronger breach laws, or wish to insert various weasel words such as "you're cool to keep it hush-hush if you encrypted the data with ROT13" should ask themselves this: is it reasonable to reduce the indirect damage of adverse publicity at the expense of making direct damages to the consumer even worse?
Lots of discussion, etc etc blah blah. My thought is this: we need to get ourselves to a point, as a society, where we do not turn the organisation into more of a secondary victim that it already is through its breach. We need to not make matters worse; we should work to remove the incentives to secrecy, rather than counterbalancing them with opposing and negative incentives such as heavy handed data protection regulators. If there is any vestige of professionalism in the industry, then this is one way to show it: let's close down the paparazzi school of infosec and encourage and reward companies for sharing their breaches in the open.
April 21, 2008
VCs have a self-destruction gene, let's tweak it
Adam asks why there aren't more Paul Grahams, who asks why there aren't more Googles. When I actually read the post, I was somewhat confused, because he provided the evidence for Adam's question. The guy is rich, doesn't that make him wise? He's definitely thrown the holy handgrenade of confusion amongst the faithful knights, this time.
The headline question is, why aren't their more Googles:
Google's founders were willing to sell early on. They just wanted more than acquirers were willing to pay. It was the same with Facebook. They would have sold, but Yahoo blew it by offering too little.
OK, that statement is fine, true, a non-controversial statement (albeit, it doesn't actually address the headline question one iota). Now put your coffee mug down, take a deep breath and read this:
Tip for acquirers: when a startup turns you down, consider raising your offer, because there's a good chance the outrageous price they want will later seem a bargain.
Is this a test? Is Paul Graham hoping that people will read this and say, ha ha, I spotted your little joke? Or does he seriously believe that the current crop of acquirers are so stupid as to allow their self-destruction gene to run rampant and clean out the field a little?
On the off-chance that the above is not completely transparent, let's work it through. (As this is a blog that is read by few people, we run little risk of spoiling his fun.) The first thing to realise is that startup founders are always totally convinced that their offer is worth more. That's part of their makeup. As Paul Graham points out, this uncanny, reality-defying total belief is essential to getting the startup to where it is now.
So, it is a given that when you go to a startup, they will believe that they are worth more than you offer. If they don't believe that, then you possibly should take that as a sign, as perhaps Paul Graham suggests. However, when it comes to takeovers, this will quickly become a self-fulfilling rejection, so you need to somehow inject some pragmatics into the equation. If there are no pragmatics, there is no sale, period, and we aren't having this conversation. There's a lot of that going around these days....
So, somehow, pragmatics is inserted into the brain of the founder to fight the self-fulfilling fantasy gene of demi-god status. How this is done is totally random of course, by simple game theory; if we knew how this was done, we'd use it against him, and his demi-god capabilities would immediately destroy our tactics, so it can't be possible, before the fact, to know how. Capice?! As this is impossible to predict (is there a smart financier behind the founder? A mother? Is he actually ready for a takeover? Is he in fact smart and the bravo is a facade?) it is not really plausible to derive much info from any offer he rejects or accepts.
Given that, let's then turn to the advice: offer more money. OK, that's fine if this is a one round game. But what happens in round two? Well, clearly, all the startups hear about all the VCs who have followed the advice of the sage, and they all reject the first offers.
By induction over the basic model we can quickly determine that (a) we started from no useful information, and (b) each successive round takes us further from no information, and (c) each round that concludes with a successful "higher price" sale sucks more money out of the VCs, so (d) this strategy is guaranteed to kill more VCs and fund less startups than any government subsidy could possible do.
Round n+1: everyone goes broke.
In fact, this is simply how trade works, and economists and greengrocers alike learn it at an early age. In the trade it is called haggling, and the advice to haggle is no more useful than advice like "listen to your mother when she's right."
To repeat the comment I made on Adam's blog: VCs are about hard work. Just like the rest of life, there is no easy money. And circus tricks like the above are fine for the marketing and webpage ... "we know when to double our offer" ... but they won't give you any insight into how the VC world really works.
The rest of the post asks some good questions:
The most surprising thing I've learned is how conservative they are. VC firms present an image of boldly encouraging innovation. Only a handful actually do, and even they are more conservative in reality than you'd guess from reading their sites.I used to think of VCs as piratical: bold but unscrupulous. On closer acquaintance they turn out to be more like bureaucrats. They're more upstanding than I used to think (the good ones, at least), but less bold.
Right. VCs are very very conventional. Very very bureaucratic. But the facade is outrageous, daring, all flash and bang. Why is this? Why can't a VC have an image that looks conservative?
I met some guys who do exactly that. Conservative. Not only do they pick a strong investment strategy that targets particular groups, they clearly explain their investment strategy on their site. And they do OK. I wish I could have done a deal with them, but their strategy and mine weren't aligned.
So, why do VCs believe they need this false front? Is it because you cannot attract a steady series of crazy offers across the desk without appearing to be crazy? You can't date a teenager without ... dressing like one? You can't be a VC without pretending to have a nose ring?
Plus most of them are money guys rather than technical guys, so they don't understand what the startups they're investing in do.
Ain't that the truth! The biggest problem I've seen with VCs is that they have next to no technical ability. So they have no ability to sort the technically sound from the technical fantasy. And this rhymes with my comments on CSOs from a while back: Strong technical people get that way by studying lots of tech. Strong money people get that way by studying lots of money. A rare bird indeed is one who naturally finds themselves in both camps.
Top tip: look for a strong technical player who has an MBA. This guarantees that, even if they aren't good at the money, they at least have the language and the culture injection enough to be able to understand and communicate.
(insert routine self-important blah blah disclosure here!)
Finally, he asks:
I've tried to explain this to VC firms. Instead of making one $2 million investment, make five $400k investments.
OK, sure, this is the phenomena that appeared in the mid 90s with several incubator investors and the Spring Street market. Basically, investment became technically a whole lot cheaper and more opportunities sprung up, creating a hole, a new opportunity in the market.
The failing is that the due diligence doesn't get any cheaper. The trick is to find a way to reduce the cost of the due diligence. There are ways to do it, but you aren't going to find them in VC firms, which is why angels exist.
( Hint: pay me like a VC and I'll tell you how to do it. 2nd Hint: if you pay me like a VC, it will be just as expensive. 3rd Hint: obviously, the trick is to not pay me like a VC. 4th and 5th hints will cost real VC money ... are you getting it yet? )
(As I recall, I analysed Spring Street and realised that they understood the flaw in the idea, and instead simply used the exposure to bootstrap up from the little boys' idea to the big boys' market.)
April 20, 2008
The Medium is the Message: what is the message of security today?
Who said that? Was it Andy Warhol or Marshal McLuhan or Maurice Saatchi?
A few days ago, we reflected on the medium of the RSA conference, and how the message has lost its shine. One question is how to put the shine back on it, but another question is, why do we want shine on the conference? As Ping mused on, what is the message in the first place?
The medium is the message. Here's an example that I stumbled across today: Neighbours. If you don't know what that is, have a look at wikipedia. Take a few moments to skim through the long entry there ...
If you didn't know what it was before, do you know now? Wikipedia tells us about the popularity, the participants, the ratings, the revamps, the locations, the history of the success, the theme tune, and the awards. Other than these brief lines at the beginning:
Neighbours is a long-running Australian soap opera. The series follows the daily lives of several families who live in the six houses at the end of Ramsay Street, a quiet cul-de-sac in the fictional middle-class suburb of Erinsborough. Storylines explore the romances, family problems, domestic squabbles, and other key life events affecting the various residents.
Wikipedia does not tell the reader what Neighbours is. There are 5998 words in the article, and 55 words in that message above. If we were being academic, we could call them message type I and type II and note that there is a ratio of 100 to 1 between them!
At a superficial, user-based level, the 55 words above is the important message. To me and you, that is. But, to whoever wrote that article, the other 99% is clearly the most important. Their words are about the medium, not what we outsiders would have called the message, and it is here that the medium has become the message.
Some of that stuff *is* important. If we drag through the entire article we find that the TV show does one million daily audience in Australia, peaked at 18 million in the UK, and other countries had their times too. That you can take to the bank, advertisers will line up out on the street to buy that.
We can also accurately measure the cost and therefore benefit to consumers: 30 minutes each working day. So we know, objectively, that this entertainment is worth 30 minutes of prime time for the viewers. (The concept of a soap opera guarantees repeat business, so you know you are also targetting a consistent set of people, consistently.)
We can then conclude that, on the buy side and the sell side of this product, we have some sort of objective meeting of the minds. And, we can compress this mind meeting into a single number called ratings. Based on that one number alone, we can trade.
That number, patient reader, is a metric. A metric is something that is objectively important to both buyer and seller. It's Okay that we don't know what "it" is, as long as we have the metric of it. In television, the medium is the message, and that's cool.
Now, if we turn back to the RSA channel .. er .. conference, we can find similar numbers: In 2007, 17,000 attendees and 340 exhibitors. Which is bankable, you can definitely get funding for that, so that conference is in good shape. On the sell side, all is grand.
However, as the recent blog thread pointed out, on the buy side, there is a worrying shortage of greatness: the message was, variously, buyers can't understand the products, buyers think the products are crap, buyers don't know why they're there, and buyers aren't buying.
In short, buyers aren't, anymore. And this separates Neighbours from RSA in a way that is extremely subtle. When I watch an episode of Neighbours, my presence is significant in and of itself because the advertising works on a presence & repeat basis. I'm either entertained and come back tomorrow, or I stop watching, so entertainment is sufficient to make the trade work.
However, if I go to the RSA conference, the issue of my *presence* isn't the key. Straight advertising isn't the point here, so something other than my presence is needed.
What is important is that the exhibitors sell something. Marketing cannot count on presence alone because the buyer is not given that opportunity statistically (1 buyer, 340 exhibitors, zero chance of seeing all the adverts) so something else has to serve as the critical measurement of success.
Recent blog postings suggest it is sales. Whatever it is, we haven't got that measurement. What we do have is exhibitors and participants, but because these numbers fail to have relevance to both sides of the buy-sell divide then these numbers fail to be metrics.
Which places RSA in a different space to Neighbours. Readers will recognise the frequent theme of security being in the market for silver bullets, and that the numbers of exhibitors and participants are therefore signals, not metrics.
And, in this space, when the medium becomes the message, that's very uncool, because we are now looking at a number that doesn't speak to sales. When Marshal McLuhan coined his phrase, he was speaking generally positively about electronic media such as TV, but we can interpret this in security more as a warning: In a market based on signals not metrics, when the signals become the system, when the medium becomes the message, it is inevitable that the system will collapse, because it is no longer founded on objective needs.
Signals do not by definition capture enough of the perfect quality that is needed, they only proxy it in some uncertain and unreliable sense. Which is fine, if we all understand this. To extend Spence's example, if we know that a degree in Computer Science is not a guarantee that the guy can program a computer, that's cool.
Or, to put it another way: there are no good signals, only less bad ones. The signal is less bad than the alternate, which is nothing. Which leads us to the hypothesis that the market will derail when we act as if the the signal is a metric, as if the Bachelor's in CompSci is a certification of programming skill, as if booth size is the quality of security.
Have another look at Neighbours. It's still going on after 22 years or so. It is around one million, because of some revamp. That metric is still being taken to to the bank. The viewer is entertained, the advertiser markets. Buyer and seller are comfortable, the message and the medium therefore are in happy coincidence, they can happily live together because the medium lives on solid metrics. All of this, and we still don't know what it is. That's TV.
Whereas with the world of security, we know that the signal of the RSA conference is as strong as ever, but we also know that, in this very sector that the conference has become the iconic symbol for, the wheels are coming off. And, what's even more disturbing, we know that the RSA conference will go from strength to strength, even as the wheels are spinning out of view, and we the users are sliding closer to the proverbial cliff.
I know the patient reader is desperate to find out what Neighbours really is, so here goes. Read the following with an Aussie sense of humour:
About 10 years back I and a partner flew to Prague and then caught a train to a a Czech town near the Polish border, in a then-devastated coal belt. We were to consult to a privatised company that was once the Ministry of Mines. Recalling communist times, the Ministry had shrunk from many hundreds of thousands of miners down to around 20,000 at that time.Of which, only 2 people spoke English. These two English speakers, both of them, picked us up at the train station. As we drove off, the girl of the pair started talking to us, and her accent immediately jolted us out of our 24 hours travel stupor: Australian! Which was kind of unexpected in such a remote place, off the beaten track, as they say down under.
I looked slowly at my friend, who was Scandinavian. He looked at me, slowly. Okay, so there's a story here, we thought... Then, searching for the cautious approach, we tried to figure it out:
"How long have you lived here?" I asked.
She looked back at me, with worry in her face. "All ma life. Ah'm Czech." In pure, honest dinkum Strine, if you know what that means.
"No, you're not, you're Aussie!"
"I'm Czech! I kid you not!"
"Okay...." I asked slowly, "then why do you have an Australian accent."
Nothing, except more worry on her face. "Where did you learn English?"
This she answered: "London. I did a couple of year's Uni there."
"But you don't have an English accent. Where did you pick up an Australian accent?"
"Promise you won't laugh?" We both duly promised her we would not laugh, which was easy, as we were both too tired to find anything funny any more.
"Well," she went on, "I was s'posed to do English at Uni but I didn't." That is, she did not attend the University's language classes.
"Instead, I stayed at home and watched Neighbours every lunchtime!"
Of course, we both cracked up and laughed until she was almost in tears.
That's what Neighbours is -- a cultural phenomena that swept through Britain by presenting an idyllic image of a sunny, happy place in a country far far away. Lots of fun people, lots of sunshine, lots of colour, lots of simple dramas, albeit all in that funny Aussie drawl. A phenomena strong enough that, in an unfair competition of 22 minutes, squeezed between daily life on the streets of the most cosmopolitan city in the world, it was able to imprint itself on the student visitor, and totally dominate the maturing of her language. The result was perfect English, yet with no trace of the society in which she lived.
But you won't read that in Wikipedia, because, for the world of TV, the medium is the message, and they have a metric. They only care that she watched, not what it did to her. And, in the converse, the language student got what she wanted, and didn't care what they thought about that.
April 19, 2008
The illusion of Urban Legends - the Dutch Revolving Bicycle Cycle
Chandler spots a post by Michael on those pervasively two-wheeled Dutch, who all share one standard beaten-up old bike model, apparently mass-produced in a beaten-up old bike factory.
The Dutch are also prosperous, and they have a strong engineering and technology culture, so I was surprised on two visits in the last few years to see that their bikes are all junkers: poorly maintained, old, heavy, three-speeds. The word I used was all. ...I asked about this and everyone immediately said "if you had a good bike it would be immediately stolen." On reflection, I'm not satisfied with the answer, for a couple of reasons. First, the Dutch are about as law-abiding as Americans, perhaps more. Second, the serious lock that has kept my pretty good bikes secure on sketchy streets in two US cities for decades is available for purchase all over the world.
Third, and most important, I don't see how this belief could be justified by real data, because there were absolutely no bikes worth stealing anywhere I looked. ...
Right. So here's an interesting case of an apparently irreconcilable conundrum. Why does all the evidence suggest that bike insecurity is an improbability, yet we all believe it to be pervasive? Let's tear this down, because there are striking parallels between Micheal's topic and the current debate on security. (Disclosure: like half of all good FCers, I've spent some time on Amsterdam wheels, but it is a decade or so back.)
At least, back then, I can confirm that bicycle theft was an endemic problem. I can't swear to any figures, but I recall this: average lifespan of a new bike was around 3 months (then it becomes someone else's old bike). I do recall frequent discussions about a German friend who lost her bike, stolen, several times, and had to go down to the known areas where she could buy another standard beat-up bike from some shady character. Two or three times per year, and I was even press-ganged into riding shotgun once, so I have some first-hand evidence that she wasn't secretly building a bike out of spare parts she had in her handbag. Back then, the going price was around 25-50 guilders (hazy memory) which would be 10-30 euros. Anyone know the price at the moment?
For the most part, I used inline skates. However when I did some small job somewhere (for an FC connection), I was faced with the issue. Get a bike, lose it! As a non-native, I lacked the bicycle-loss-anti-angst-gene, so I was emotionally constrained from buying the black rattler. I faced and defeated the demon with a secret weapon, the Brompton!
The Dutch being law-abiding: well, this is just plain wrong. The Dutch are very up-right, but that doesn't mean they aren't human. Law-abiding is an economic issue, not an absolute. IMO, there is no such thing as a region where everyone abides by the law, there are just regions where they share peculiarities in their attitudes about the law. For tourists, there are stereotypes, but the wise FCer gnaws at the illusion until the darker side of economic reality and humanity is revealed. It's fun, because without getting into the character of the people, you can't design FC systems for them!
As it turns out, there is even a casual political term for this duality: the Dutch Compromise describes their famous ability to pass a law to appease one group of people, and then ignore it totally to appease another. A rather well-known counterexample: it is technically illegal to trade in drugs and prostitution. E.g., for the latter, you are allowed to display your own wares in your own window. For an example, look around for a concentration of red lights in the window.
Final trick: when they buy a new bike (as new stock has to be inserted into the population of rotating wheels), the wise Dutch commuter will spend a few hours making it look old and tatty. Disguise is a skill, which may explain the superficial observation that no bicycle is worth stealing.
What I don't know: why the trade persists. One factor that may explain this is that enough of the Dutch will buy a stolen bike to make it work. I also asked about this, and recall discussions where very up-right, very "law-abiding" citizens did indeed admit to buying stolen wheels. So the mental picture here is of a rental or loaning system, and as a society, they haven't got it together to escape their cyclical prisoner's dilemma.
Also: are bike locks totally secure? About as secure as crypto, I'd say. Secure when it works, a broken bucket of worthless bits when it doesn't. But let's hear from others?
Addendum: citybikes are another curiosity. Adam reportst that they are now being tried in the US.
April 14, 2008
Signs of Liability: 'Zero Day Threat' blames IT and Security industry
I painfully predicted a few years back that phishing and related identity theft would result in class action suits. I lost my bet as it didn't happen fast enough, but a significant step has been taken (reported by Lynn) with the publication of a book that apparently blames the banks and the software manufacturers for identity theft. Here's a review from USA today (also Yahoo):
Surprisingly, the real villains in Zero Day Threat are not the identity thieves themselves, despite their unsavory lives of crime. Rather, the villains are supposed pillars of communities: bankers, credit-bureau managers and computer makers who enable the burglars, and who could ameliorate the identify-theft crisis but, instead, look away in the name of larger corporate profit.Acohido and Swartz did not expect to write a book about villainous bankers, credit-bureau managers and computer makers when they began research five years ago. They began by writing reports for this newspaper on PC viruses and spam, which at first seemed like mutually exclusive topics. The more they reported on their disparate stories, the more Acohido and Swartz realized that spammers and virus writers were more than amateur disrupters in cyberspace. In fact, many of them had become cybercrooks, capitalizing on the vulnerabilities of the Internet.
"We found that there were much more complex contagions eroding the security and privacy of sensitive data" than mere spammers and virus writers, Acohido and Swartz comment, "and those corrupters had more to do with business practices and marketing strategies of the financial services and technology industries."
The authors promise "astounding revelations," and they deliver. In keeping with the complexity of identity theft, Acohido and Swartz organize the book in a complex, even daring, manner. Each chapter has three recurring sections - Exploiters, Enablers and Expediters.
The Exploiters consist of the lawbreakers, some of them addicts needing money for narcotics, some of them stone-cold-sober career criminals operating identity-theft syndicates across national borders. The Enablers consist of the banks, credit bureaus, credit card companies and data brokers seemingly blind, deaf and dumb to the need for privacy protection. The Expediters consist of the technologists who write computer programs with good intentions (at places like Microsoft), and their evil twins who write programs as recreation to disrupt networks.
I'm not recommending the book, as I haven't got it nor read it. The point isn't to buy it, but to watch how much traction the book and the message gets in the public mind: If middle class America (the heartland of victims) groks that the banks and the software suppliers are responsible, then, things might happen.

Legislation might get written, as is suggested in the article. However, in general, we know that legislation is generally bad because the lawmakers don't know enough; more law will haunt us more than it helps us. It is no more than childish dreams to hope that the SB1386 miracle is repeated.
For this reason, the class action suit might result in a better result. If it goes wrong, only one manufacturer gets hurt. If it goes right, it establishes a precedent in law and a message in the minds of the otherwise security-shy manufacturers. N.B., another step closer was taken when class-action lawsuits were filed for the Hannaford breach.
A footnote based on some econ theory: One of the observations that is often made is that it is all to do with incentives. This comes from the agency theory branch of economics, and it identifies how actors act according to the monetary incentives in front of them.
The specific problem is that, other than a few anti-virus suppliers and other exceptions, nobody much ever made money from security in the world of IT. That's because of an unfortunate truth: the user bears the entire cost of a failure of security. Now, obviously, if there was a way to pass that liability and cost back to the manufacturers, then, so the theory goes , security will get better.
This hits a roadblock when we look at the structure of the industry: it is far more based on open standards and innovation than we might care to believe. E.g., the IBM PC line, the Unix OS, the 'C' language, the open email protocol, have all inspired massive standardisation, extension, and copying. This is great because the innovation diffuses across society in an extremely cost-effective way. But it has a downside, which is that we can't easily hold the "manufacturer" liable because it is unclear who is the manufacturer of these innovations.
E.g., if we decide that Linux security is flaky, do we sue Linus or Dennis or Redhat or ...?
The end result of all this bounty is that consumers have to take one for the team, because to make manufacturers liable will stop the innovation and diffusion, conceivably double the cost of their product, stop the IT revolution, and take us back to the time of national telco champions. Nobody wants that.
For that reason, blanket legislation is a bad idea. But as the problem remains, the class action suit might be the safety valve that corrects some of the worst excesses of the pathologically neutered security industry.
March 24, 2008
S/MIME: we don't need more reasons why it failed...
Reading up on econ and sec for something that won't be mentioned in this post, I stumbled across this passage by Ozment and Schechter in "Bootstrapping the Adoption of Internet Security Protocols":
If Alice has adopted authentication, she signs all of her email. She thus expects Bob to reject unsigned messages that purport to be from her but cannot be authenticated. If Alice has not adopted authentication, she does not sign her messages. She thus expects Bob to accept messages from her even though they are not signed. To know whether to accept an unsigned message purportedly from Alice, Bob must know whether Alice has adopted authentication.
That's as eloquent a comment as I've come across of what we might call the S/MIME signing problem (with some hints to other systems like OpenPGP or SSL).
The authors then spend another 12 or so pages addressing the issue, and I've yet to read that, but it does seem that we can shortcut their analysis and say: this market won't work! Here's more:
Solving this problem requires a secure mechanism through which Bob can determine if Alice has adopted authentication. For example, if Bob already knows Alice he might consider it safe to call and ask if she signs her messages. Unfortunately, the Internet has lacked a general mechanism with which to securely determine whether a system or its users has adopted an authentication technology.
Students of tautology will find that interesting. What to do? From my podium, I say this:
There is only one mode, and it is secure.
The 3rd hypothesis has the legs to walk this journey, and it would carry S/MIME into securing much more email, if only those legs were set free to walk your secure talk. Now to read the rest of their paper...
Liability for breaches: do we need new laws?
It is frequently pointed out by economists that incentives are the key to a lot of behaviour. They argue that, if incentives are aligned, positive results happen, and if misaligned, damage is done. This tradition goes a long way back in economics tradition, and has been recently highlighted to the Internet security community by Prof. Ross Anderson and others, who point out that the incentives are not aligned in information security.
The point in Information Technology is that a supplier provides the service, but disclaims the liability. The nature of this service might range from Microsoft's Windows operating system to banks' online interfaces, to Mozilla's browser to the vast behemoth known as the credit system. In each case, there are security ramifications to the service which are all passed on to the user. However, as the user is generally in no position to fix or even understand the security ramifications, we have an incentives clash.
The classical (liberal?) cry is that we need new laws to shift the liability back to supplier. The economic argument against that is simple: firstly, we have no clear picture of the efficient way to deal with the liability, and secondly, passing a law is almost always going to make matters less clear. So it will probably be wrong.
Now switch across to the breaches debate. Breaches in the US roll on, and sometimes even jump through the immigration barrier to the UK and other places. That's old news, but what is not is that the legal fraternity are now in on the act, and ready to file class action suits:
In a likely precursor of what's to come, a Philadelphia law firm and an attorney in Maine have filed class-action lawsuits against Hannaford Bros. Co., the Scarborough, Maine-based supermarket chain that this week disclosed a data security breach involving the potential compromise of 4.2 million credit and debit cards.Philadelphia-based Berger & Montague PC filed its lawsuit yesterday in U.S. District Court in Maine. A similar suit was filed Tuesday by Bangor, Maine-based attorney Samuel Lanham Jr. on behalf of Hannaford customers in all of the states where the grocer does business.
In a class action suit, one suit is filed and all victims join it on one side. The judgement is then awarded and shared out (with a hefty percentage going to the attorneys). You could criticise the concept on several ground: the lawyers always win, the payouts are often small to each individual, the cases take a long time, the smaller company is blown away by them, there are easy ways to game the payout... etc etc, but from an economics perspective it is also evident that the class action suit achieves a switch in incentives.
Before now, the supplier of online banking, or merchant retailing, or Internet software was untouchable in any big sense for security issues. This was the point of the incentives commentators, in that there was no incentives alignment. (I went even further in the market for silver bullets by showing how incentives are negatively aligned. Because of the silver bullets effect, the big player is incentivized to deliberately avoid the much bigger extraordinary costs -- fingerpointing -- while absorbing all small, direct losses without noticing. This means that the big player was incentivized to avoid dealing with security, and thus was generally incentivized to make matters worse for the individual.)
Now, some large lump of incentives for security has switched across to the supplier. Now, at a minimum, there is the threat of a class action suit. Indeed, it is now a validated threat, as we can see the clarity, the presence and the danger (for retailers at least). At the maximum, there may be an actual judgement at the end of actual filed suit, something that is less likely and more tangible than a threat. Hence, it is now possible to calculate the expected value (loss) from the class action activity.
If, then, the silver bullet economics are shifted to the point where these direct security costs are now more important than the indirect fingerpointing costs, we might also hope that incentives have shifted sufficiently to bring security costs to the user back onto the agenda for the supplier. If we achieve that, then we'll have achieved a good thing.
Which also brings us to another conclusion about the market for security: we don't need any new laws, as the class action system may be sufficient. Well, that's not entirely true. What we do need is this:
1. a breach disclosure law (as SB1386 has been credited with opening the floodgates of breach information), and2. a mechanism to shift the newly-surfaced incentives, such as the class action system.
It cannot be stressed enough that SB1386 was *necessary* to change the balance. It wasn't however sufficient, for that we still need to allocate the liability more directly. In the presence of class action threats, no more may be needed, and especially, new liability laws will be damaging because they will not only be too limiting in their understanding, they are likely to damage the (free market) emergence of the class action mechanism.
When do we find out if class action is enough? I first predicted this path many years back with respect to phishing, and eventually gave up waiting. So it is also fair to say that we need one more component:
3. Time. Patience.
Not something I (nor politicians nor blog writers nor security sellers) are well-endowed with, apparently, but it seems the market has sufficient endowments of it.
March 07, 2008
Is "National Security" a market for silver bullets?
John Robb poses a puzzler:
The US national security budget is nearly $700 billion a year (much more if the total costs of Iraq/Afghanistan are thrown in), more than the rest of the world combined. Unfortunately, within that entire budget there isn't a single research organization or think tank that is seriously studying, analyzing or synthesizing the future of warfare and terrorism. Fatally, most of the big thinkers working on the future of warfare do their critical work in their spare time, usually while working other jobs to put food on the table for their families. ... Here's why. The need for relevancy became apparent on 9/11, when a small group of attackers hit the US without regard, or even a passing thought, to the trillions the US had previously invested in national security. The public's response, this first time, was to pour more trillions to correct that failure. When another unanticipated situation occurs again (and it will, likely in a increasingly rapid succession as small group warfare climbs an exponential ramp of productivity improvements), the public will not be as generous
This has an echo like silver bullets.
We have a market where lots of money is being thrown into various warfighting events and capabilities. Each seller knows their tools, but unless it is a commodity product like rifles, the seller does not know that well how their weapons fit in to the big picture. We might happily get sellers of robots knowing what their robot does, but the are very reliant on the buyer to know whether to deploy them as minesweepers or mesh-network extenders.
Then, we've got the specter of the aggressive attacker. One half-million dollar attack "defeated" the defences, and things might not be any better now
In short, the next black swan is likely to do the opposite of what the national security bureaucracy thinks. Rather than be the driver of massive rounds of new funding, it could turn it into a husk of its former self. Given that simply remaining relevant will become the key to future public funding of our national security system...
Add in the recent history of Iraq, Afghanistan, and now Pakistan, and it seems that either the buyer of product doesn't know what he's doing, or whoever does know isn't telling the rest of them. Either way, same thing; the buyer of product may know how to do classical open country tank warfare, but not closed guerilla warfare.
Is national security a market for silver bullets? We seem to have a rough match of the base conditions. In the paper I ask that question because it is a natural extension of IT security (and I, like John Robb, would like a few million for my thinktank) but it is not really clear that we have enough data to answer the question.
What do you think? Do the buyer and seller in the market for national security have the information they need for efficient trading of product?
And, if they don't, if we find national security in the dismal square of Spencian inefficiency, what would you do about it? I'm not sure I agree with everything that John Robb rights, but this one is worth repeating:
Competition from below. New, grass roots efforts at the state and local levels will compete favorably against national programs. As in: if the federal bureaucracy can't protect us, we will do the job ourselves locally (New York City has already paved that pathway with its own counter-terrorism center). Expect a fight between local and federal, a fight where the local wins.
Because that is evidence from ground zero: New York. The arisal of local security would be seen by the feds as a failure, but according to this model, the failure would be part of the market, not the their own failings.
March 06, 2008
Economics not repealed, just slow: Paypal blames Browsers for Phishing
Well, it had to happen one day. A major player has finally broken the code of silence and blamed the browsers. In this case, it is PayPal, and Safari.
Infoworld last week quoted Michael Barrett, PayPal’s CIO, saying the following:“Apple, unfortunately, is lagging behind what they need to do, to protect their customers. Our recommendation at this point, to our customers, is use Internet Explorer 7 or 8 when it comes out, or Firefox 2 or Firefox 3, or indeed Opera.”
The browser is the user's security tool. The browser is the only thing between you and the phisher. The browser is the point of all attack attention. The browser is it. That's why it had SSL built in -- to correctly identify the website as the one you wanted to go to.
So above, Paypal blames Safari for not doing enough about phishing. It's true, Safari does nothing (as I found out recently and had to switch back to Firefox). It likely had to be Paypal because the regulated banks won't say boo without permission, and Paypal might be supposed to be net-savvy. It had to be Safari because (a) there is that popular alternate now, and (b) Apple is still small enough not to be offended, and (c) others have done something in the phishing area.
A take-away then is not the names involved, but the fact that a large player has finally lost patience and is pointing fingers at those who are not addressing phishing:
At issue is the fact that Safari lacks a built-in phishing filter to warn users about shady Web sites. Safari also doesn’t support so-called Extended Validation certificates, which turn the address bar green if a site is legit. Extended Validation certificates aren’t the complete answer but are a help.
OK, so those are some ideas, and Safari could do something. However there may be more to this than meets the eye:
An emerging technology, EV certificates are already supported in Internet Explorer 7, and they've been used on PayPal's Web site for more than a year now. When IE 7 visits PayPal, the browser's address bar turns green -- a sign to users that the site is legitimate. Upcoming versions of Firefox and Opera are expected to support the technology.
Aha! It's not a general complaint to Apple at all. It is a complaint that EV has not been implemented in Safari. It's a very specific complaint!
( Long term readers know that EV implements the basic steps necessary to complete the SSL security model: By naming the CA that makes the claim, it clearly encapsulates the statement. By making it more clear what was going on to the user the final step was made to the risk-bearing party. )
Paypal has purchased a green certificate. And now they want it to work. It works on IE, but not on others. (Firefox and Opera say "soon" and so are given a pass. For now.) Apple rarely comments on its plans, so it has been named and shamed for not adopting the agreed solution. More for not playing the game than anything.
The sad thing about the EV is that it is (approximately) what the browsers should have done years ago, when phishing became apparent.
But nothing could be done. I know, I tried. If there is any more elegant proof of the market for silver bullets, I'm hard pressed to find it. To break the equilibrium around SSL+cert-user-CA (that reads SSL plus cert minus user minus CA), EV had to be packaged as an industry consortium agreeing on an expensive product. Once so packaged, it was then sold to Microsoft and to some major websites. Once in the major places, influence is then brought to bear to get the rest to come into line.
The problem with this, as I lay out in silver bullets, is that shifting from one equilibrium to another is a strictly weaker strategy. Firstly, we are not that confident in our choice of equilibrium. That's by definition; we wouldn't play this game if we knew how to play the game. Secondly, and to spin a leaf from John Boyd, the attacker can turn inside our OODA loop. Which is to say, he can create and modify his attacks faster than we can change equilibrium. Or, he is better at playing his game than we are.
You can read a much more extended argument in the essay (new, improved with extra added focus!). But for now, what I find interesting is the questions we don't yet have answers to.
What would be the attacker's best strategy, knowing all we do about the market and our claim that this is equilibrium shifting? Would the attacker destroy EV? Would he protect EV? Would he milk it?
Another question is, what is Apple's best strategy? It is currently outside the consortium, but has been attacked. Should it join and implement EV? Go it alone? Ignore? Invent an own strategy?
January 20, 2008
How to improve the Standards Process: the Prisoner's Dilemma
As you know, this blog does not like the over-deification of standards that many encourage. So when Mitchell asks:
The goal of is the discussion is to think about whether we can improve the setting. It's because this is so important that I want to focus on it.For example, can we encourage more openness and transparency in the creation of web standards? We've proved that openness and transparency work well for code: they encourage discussions to focus on technical merit; they allow everyone who is interested to understand the details; they encourage participation. Why not do this with the creation of web standards?
you can expect some less than positive responses. Still, much as we don't like it, it's a fair question, because whichever way you look at it, Mozo is stuck in the standards game.
Why is Standards so hard? We are up against many things here, but one view is that it is a battle of the worst of the small against the worst of the large.
Firstly, the small. Human nature is to operate in closed groups. Even in so-called open groups, most work gets done in private, and people are adept at creating motives, processes, and excuses to push things more to the closed end of the scale.
For example, many Internet security projects claim to run an open security process, but operate a closed process. They do this by various tricks: invite-only policy, closed archives, hidden names, no communications. In practice such a process reduces to a closed group, and the result of such dissonance is stagnation and mistrust, often needlessly because the people working in these groups are trying their damnest to get the job done.
What are the human processes here? People all want to be with the winning side, and for the last 10 years, "open" is the winning side. So the "open" is essential, and security groups are not immune to that.
But, when push comes to shove, being open is such a complete change for the psyche that most people can't deal with it. One minor example: how does the security director can say "I don't know" on a public list when breaches are in the air and the press is looking for blood? It's hard enough to be uncertain before your own team, not to mention that it is hard to sort things out when too many people are able to speak at once.
The business of security has more than its fair share and historical wisdom, excuses and complexities, so, human nature being what it is, we end up with a facade of openness, and real work gets done in closed session. Even in the open groups...
In between the large and the small is the economics. These might be considered to the rules of warfare in Standards. The top three influences in Standards Setting are economics, economics and economics. In that order.
Luckily, the economics is well known! By agreeing to a common standard, we achieve a benefit in common. We each individually face a higher cost. However, some of us don't have to pay the individual higher cost, and may still win from the others, because the benefit is in common.
If this sounds familiar, it is because it is a widely studied thing called The Prisoner's Dilemma.
What's the big thing about the Prisoner's Dilemma? Cheating: everyone has the incentive to cheat, but hold the other guys to honesty. If I cheat, and you all do the right thing, I win. Unfortunately if we all cheat, we all lose, which is why it is called a dilemma.
Now we get to the large: if we then add competitive pressures to this mix, we have an explosive combination that is called "cartels" in economic terms (c.f., Gary Hamel and C. K. Prahalad, who studied the economics of standards, joint ventures and industry associations). Harken back to the old Netscape days, and consider how Microsoft and others fought over the "web standard". Blackbird, W3C etc. As there's real money involved here, the end result is that people take cheating seriously, and deception is the rule, not the exception.
In such a circumstance, the Standards Business is best modelled as a battle between large corporations under Prisoner's Dilemma economics. (Other things might sound nicer, but remember that deception is the rule...) If you want to get anywhere in that battlefield, the only way is to break the economics of the Prisoner's Dilemma, and that means ... to change the reward structure. But because the Standards group is supposed to be unpaid, it has to be done with non-monetary payoffs.
Which leaves one thing: reputation.
To put the other guy's reputation on the line, you have to show that he is breaking the rules. Which means: we need rules, tough ones, and the fiercer rules the better. Here's some ideas:
- All archives should be public.
- All decisions should be made in the public list.
- Rough consensus should rule.
- The group can be joined by anyone.
- All conflicts of interest should be declared.
For yourself,
- become an adept at negotiation, as that is the practice of how to deal with the theory of PD.
- Always remember that before anything, standards setting is an economics process, not a political or moral process.
- Always be ready to withdraw.
Knowing all this doesn't mean we can avoid the Prisoner's Dilemma, as some dilemmas can't be saved. But it does put you in a better position to realise when the process is stalled through deadlock, and to spot who is really unable to contribute because deception is the only way they know. As it is an economic process, withdrawal is the ultimate defence, as your time is better spent elsewhere.
December 30, 2007
Why Security Modelling doesn't work -- the OODA loop of today's battle
Editor's note: now with a Chinese translation
I've been watching a security modelling project for a while now, and aside from the internal trials & tribulations that any such project goes through, it occurs to me that there are explanations of why there should be doubts. Frequent readers of FC will know that we frequently challenge the old wisdom. E.g., a year ago I penned an explanation of why, for simple money reasons, you cannot build security into the business from the early days.
Another way of expressing this doubt surrounding Security Modelling is by reference to Col. Boyd's OODA loop. That stands for Observe, Orient, Decide, Act and it expresses Boyd's view of fighter combat. His thesis was that this was a loop of continuous cycles that characterised the fighter pilot's essential tactics.
Two things made it more sexy: firstly, as a loop, he was able to suggest that the pilot with the tighter OODA loop would turn inside the other. This was a powerful metaphor because turning inside the enemy in fighter combat is as basic as it gets; every schoolboy knew how Spitfires could turn inside Messerschmitt 109s, and thus was won the Battle of Britain.
Obviously things aren't quite so simple, but this made it easy to understand what Boyd was getting at. The second thing that made the concept sexy was that he then went on to show it applied to just about every form of combat. And, that's true: I recall from early soldiering lessons on soviet army doctrine, that the russkies could turn their defence into a counter-attack faster than our own army could turn our attack into a defence. At all unit sizes, the instructors pointed out.
Taking a leaf from Sun Tzu's Art of War, the OODA loop concept may also be applied to other quasi-combat scenarios such as security and business. If we were to translate it to security modelling, we can break the process simply into four phases:
- threat modelling
- security modelling
- architecture
- implementation & deployment
To do it properly, each of these phases is important. You can't skip them, says the classical wisdom. We can agree with that, at a simple level. Which leaves us a problem: each of those phases costs time and effort.
A proper threat model for a medium sized project should take a month or so. A proper security model, I'd suggest 3 months and up. The other two phases are also 3 months and climbing, with overruns. So, for anything serious, we are talking a year, in total, for the project.
Now consider the attacker. Today's aggressor appears very fast. So-called 0-day viruses, month-long migration cycles, etc. A couple of days ago, there was this report that talked about the ability of Storm and Son-of-Storm's ability to migrate dynamically: "what emerges is a picture of a group of skilled, professional software developers learning from their mistakes, improving their code on a weekly basis and making a lot of money in the process."

Which means that the enemy is turning in his OODA loop in less than a month, sometimes as quickly as a day. Either way, the enemy today is turning faster than any security model-driven project is capable of doing.
What to do? Adolf Galland apocryphally told Reichsmarschall Göring that he could win the Battle of Britain with a squadron of Spitfires, but he was only behind by a few percentage points. In security terms we are looking at an order of magnitude, at least, which seems to lead to two possible conclusions: either your security model results in perfect security, there are no weaknesses, and it matters not how fast the enemy spins on his own dime. Or, classical security modelling is simply and utterly too slow to help in today's battle.
We need a new model. Now, this isn't to say "stop all security modelling." Even in the worst case, if the technique is completely outdated, it will remain a tremendously useful pedagogical discipline.
Instead, what I am suggesting is that the conventional wisdom doesn't hold scrutiny; something has to break. Whatever it is, security modelling is likely to have to change its practices and wisdoms, if it is to survive as the wisdom of the future.
Quite dramatically, indeed, as it possibly needs to achieve a 10-100 fold increase in its OODA loop performance in order to match the current enemy. In other words, a revolution in security thinking.

Editor's note: now with a Chinese translation
December 04, 2007
CFP -- WEIS -- papers by 1st March 2008
Alessandro writes:
WEIS 2008 - Workshop on the Economics of Information Security
June 25-27, 2008 in Hanover, New Hampshire
CALL FOR PAPERS
Information security requires not only technology, but a clear understanding of risks, decision-making behaviors and metrics for evaluating business and policy options. How much should we spend on security? What incentives really drive privacy decisions? What are the trade-offs that individuals, firms, and governments face when allocating resources to protect data assets? Are there good ways to distribute risks and align goals when securing information systems?
While organizations and individuals face new and evolving technical challenges, we know that security and privacy threats rarely have purely technical causes. Economic, behavioral, and legal factors often contribute as much as technology to the dependability of information and information systems. The application of economic analysis to these problems has proven to be an exciting and fruitful area of research.
The 2008 Workshop on the Economics of Information Security invites original research papers focused on the economics of information security and the economics of privacy. We encourage economists, computer scientists, business school researchers, law scholars, security and privacy specialists, as well as industry experts to submit their research and attend the Workshop. Suggested topics include (but are not limited to) empirical and theoretical economic studies of:
- Optimal investment in information security
- Privacy, confidentiality and anonymity
- Cybertrust and reputation systems
- Intellectual property protection
- Information access and provisioning
- Risk management and cyberinsurance
- Security standards and regulation
- Behavioral security and privacy
- Cyberterrorism policy
- Organizational security and metrics
- Psychology of risk and security
- Phishing, spam, and cybercrime
- Vulnerability discovery, disclosure, and patching
Important dates
Submissions due: March 1, 2008
Notification of acceptance: April 10, 2008
Workshop: June 25-27, 2008
August 30, 2007
Why are analyses of cash v. debit card so fundamentally flawed?
Several weeks back, Dave Birch commented in depth about Leo van Hove's article. (Unfortunately not free to read.) Dave does the job of bringing the paper to the public, hopefully faithfully.
What follows is a somewhat critical response to Leo's article (as viewed through Dave's spectacles). In summary, I would suggest that the analysis is flawed, because it fails to consider the costs of subsidies. Fundamental questions in the analysis, which for sake of polemic thought I'll claim as being answered in the negative, are raised below.
The cash v. everything else debate hinges on the costs to banks of the various instruments. Occasionally, when convenient, the costs to the merchants are brought in as well. If the analysis is stretching out to be fair, it also includes the costs to the users. This is rarer, but Leo talks about this.
What is never brought in is the opportunity costs to those without these tools. The central banks hint at this issue when they talk about societal costs (and who's to know how they calculate this) but what they fundamentally fail to recognise is the cost of a credit card transaction for someone without a credit card. Or, likewise, without a bank account.
By way of example, how much does it cost to hire a car without a credit card? In many countries, you simply cannot do it. The cost of something you can't do is so high it breaks the model; ignoring that cost, while popular, is not the appropriate response for policy or science. Dave and Leo hint at this:
One of the most obvious implications stemming from this observation is that there is a low price elasticity: the consumer demand for goods and services does not depend greatly on the cost of the payment instruments.
The large group of society who can't pay the cost are sometimes called the unbanked, in the banking world. That's part honest recognition, and part marketing: Banks and sometimes central banks say, we must "bank" everyone, and the unbanked are are future growth area.
Sounds simple, and perhaps it is. Why then haven't they done this? Why do most countries exhibit large (double-digit) portions of the population outside the bank net? Part of the answer, if not all of it, is the risk, and banks are, if nothing else, very careful in the risk business.
And now we get closer to the nub of the efficient payments problem. Payment systems are not banking. Payment systems are more technical systems, almost turn-key devices, that can be built for standard levels of risk (and in this context, I mean, the risk that all businesses except banks take on).
That is, by normal principles, payment systems should be outside banking. If payment systems were outside banking, then the "unbanked problem" wouldn't exist, because the risk would be properly allocated to those people doing transactions.
However, payment systems are not outside banking, for one very good reason, and that is this: Banks need a way to borrow consumer's money. They need the hard cash to build reserves which allows them to make loans ... back to the same public. (That's what banking is, BTW.) And, it turns out that if you offer a payment system alongside a deposit account, this makes for a ready source of those demand deposits. The synergies are very high, as the MBAs would say. The need to control competition is very high, central bankers would say, because a strong, non-leaky bank sector is in society's interests.
We must keep firmly in mind, however, that payment systems is not the same business as banking (remember, always, payment systems are not risky, unless you make them so), and therefore, the tying of payment systems to banking is a cross-subsidisation. So that means that the entire analysis of the costs of cash are wrong unless they start with the assumption that we deliberately run a cross-subsidisation system by definition, and we have to eat that cost as a society.
This is seems an appropriate time to bring in Leo / Daves version of the story:
We've agreed that the market for payment instruments is very different from other markets. So different, in fact, that "market" is probably an inappropriate description. This issue is a basic structural problem: central banks are charged with improving the efficiency of the payment system while being responsible for the most inefficient mechanism. Inefficient here means, just to be clear, "has highest social cost".
So we are all agreed that payment systems are not open, even if we disagree on how to discuss the foundation. I'm pretty sure that the entire unbanked world would vote for my thesis, and a large proportion of the banked would do so too, once properly appraised of the costs of the subsidy (Paypal charges what percentage per transaction?).
And, that's the punchline: without including the costs of that cross-subsidisation system, all other analyses are not only flawed, but meaningless. It matters not whether cash, debit cards and credit cards compete, because we have chosen by policy to run cross-subsidies. Only if we are to drop all the subsidies are we likely to come close to a meaningful competition, and only if we measure the costs of subsidies are we close to comparison or policy.
And this finally gets us to the real core of the argument: Nobody's talking about opening up the payments market. Not in Europe, at least. And, since 9/11, the US has taken great strides to close it up, aligning the majority of the rich world.
Nobody's talking about competition as a driver for efficiency in payment systems. Therefore, we can claim, the assumption that the central banks are accepting the responsibility for the efficiency of the payment systems is, on the face of it, wrong. What then is Leo's article about?
Leo focuses on the apparent tension between a central bank's duty to ensure efficient payments systems and its operational activities in providing the least efficient payment system of all.
Why is this? Why so much contradiction? Once we've accepted the above logic, we can predict what this debate is really about.
Central banks are caught between their customers (banks) and their regulators (parliaments, the public, those nasty bloggers, etc). Banks understand one thing: control of market. Europeans (by this I mean the peculiar policy ones in or near Brussels) understand one other thing: everything should be the same price across Europe. And one price that hasn't fallen to Brussels is the cross-border payment.
The central banks then find themselves at the poker table with the banks, trading chips with labels like SEPA, CASH and FRANCHISE. SEPA is "Single European Payments Area" and means one price across Europe for all retail payments, more or less. The game works like this:
"Who'll take SEPA off my hands in exchange for CASH?"
Which, if you follow the highly unspoken cross-subsidisation of payment systems above, is why the debate seems so surreal.
Whoever plays with SEPA and CASH is playing for high stakes poker. The problem is, we have already seen the cards in the hands of other players, and they've got TRAINWRECK written all over them.
July 20, 2007
ROI: security people counting with fingers?
A curious debate erupted over whether there is ROI on security investments. Normally sane Chris Walsh points to normally sensible Richard Bejtlich seems to think that because a security product saves money and cannot make money on its own, therefore it is not an investment, and therefore there cannot be ROI.
The problem the "return on security investment" (ROSI) crowd has is they equate savings with return. The key principle to understand is that wealth preservation (saving) is not the same as wealth creation (return).
If you use your fingers to count, you will have problems. The issue here is a simple one of negative numbers and the distinctions between absolute and relative calculations.
Here's how it works. Invent Widget. Widget generates X in revenue, per unit, which includes some small delta x in shrinkage or loss. Call it 10% of $100 so we are at an X of $90 of revenues.
Now, imagine a security tool that reduces the shrinkage by half. X' improves by $5. As X' of $95 is an improvement in your basic position of X at $90, this can then be calculated as an ROI (however that is done).
What then is the fallacy? One way to put it is like this (edited from original):
The "savings" you get back are what you already own, and you only need to claw them back.
No such, you don't have it, so it isn't yours to calculate, and resting on some moral or legal position is nonsense. The thief laughs at you, even if the blog evidence is that nobody else notices the joke, including economists who should know better! The thing that Richard is talking about is not "savings" in economic terms but "sunk costs."
In business terms, too, all numbers and formulas are just models. As the fundamental requirement is here to compare different investments then as long as we treat "savings" or "shrinkage" or "sunk costs" or whatever the same way in each instance of the model, the result is comparable. Mathematics simply treats minus numbers as backwards of positive numbers, it doesn't refuse to do it. A "savings" is just a negative number taken from another positive number that might be called "ideal maximum".
Having said all that, Richard's other points are spot on:
- Calculating ROI is wrong, it should be NPV. If you are not using NPV then you're out of court, because so much of security investment is future-oriented.
- Predicting the "savings" from a security investment is hard. There are few metrics, and they are next to useless. No security seller will give them to you. So you are left predicting from no base of information.
- Hence excessively hopeful interest in metrics conferences and breach reports. But, I like Richard treat that skeptically. Yes, it will help. No, it won't make the NPV calculations anywhere near useful enough to be accurate.
- NPV is therefore not going to help that much because they are wildly unfounded in their predictions. NPV therefore suffers from GIGO -- garbage-in-garbage-out! (more)
- You need something else.
In closing, it still remains the case that security people say their managers don't understand security. And, as above, managers are safe in assuming that security people don't understand business. Another point that is starting to become more widely accepted, thank heavens, again spotted recently from sensibly sane Arthur ( Chris Walsh :).
April 19, 2007
We pluck the lemons; you get the plums: the Lemon Maligned, in Wikipedia as in the security literature
 Several people (thanks Twan, Lynn) have pointed to Bruce Schneier's recent article on Security as Lemons. I'll not comment about it directly, as frequent readers here know my counter-claim that security is not about lemons, and reference to Akerlof will lead you down the garden path. Instead, it points to Wikipedia's entry on Akerlof's "The Market for Lemons." This article kindly points to a nice theory about the entry of Lemons into the language, as hopelessly-flawed new cars, so bad they have to be replaced entirely.
Several people (thanks Twan, Lynn) have pointed to Bruce Schneier's recent article on Security as Lemons. I'll not comment about it directly, as frequent readers here know my counter-claim that security is not about lemons, and reference to Akerlof will lead you down the garden path. Instead, it points to Wikipedia's entry on Akerlof's "The Market for Lemons." This article kindly points to a nice theory about the entry of Lemons into the language, as hopelessly-flawed new cars, so bad they have to be replaced entirely.
(ed: original article seen at right, and the text is at bottom.) The advert is great, but if the wikipedia article is anything to go by (**), it is not the last word on the Lemon.
Reading Wikipedia is good for getting a taste, but teachers and professors in the academic world have long warned that as it is user-written, it is no substitute for doing the real research.
This wikipedia article is no exception, indeed to use its own terminology, it's a lemon (**). And, it's not the difference between new cars and used cars (a switch that Akerlof himself used, for what I applaud as obvious and fair literary licence). The article is poor on the very economics it is trying to describe, albeit, ones that are not trivial.
By way of showing how hard it is to get this economics right, here are some of the difficulties with Wikipedia's maligning of the Lemon:
"Examples include the market for used cars, the dearth of formal credit markets in developing countries and the unavailability of health insurance for the elderly (that is, in the absence of government programs such as Medicare)."
Although the first is Akerlof's market for lemons, the other two are not. Instead, they are better found in the space described by Stiglitz & Rothschild, and others.
The distinction is around who knows (more): Buyer or Seller? Large party or small?
Does the distinction matter? Not if trade is like a mirror, as all are fair by definition. But the point of the asymmetrical information literature was that not all is symmetrical; the mirror is broken, and the shards cut both sides.
Where it becomes clearer is that Akerlof proposed one solution set for the ignorant buyer, and Stiglitz & Rothschild proposed another solution set for the ignorant seller, and they are very different. You can get a taste, only, here on the Nobel Prize page. As an aside, these solutions are prevalent and confirmed in the market place, confirming the existence of two contrasting spaces. Which leads us to:
Ironically, there is no reciprocal danger of a market for a good product collapsing in this manner when the asymmetry is in favour of the buyer, that is to say, when the buyers can assess more accurately the quality of the products than the sellers.
Which is exactly what Stiglitz and Rothschild were looking at: the reverse, and they showed markets where we can find collapse: tax and insurance (e.g., health insurance for the elderly).
Another one is to compare to Gresham's law:
The result is that a market in which there is asymmetrical information with respect to quality shows characteristics similar to those described by Gresham's Law: the bad drives out the good.
The danger of the comparison is only eclipsed by the popularity of the mistake: the structural underlying forces are simply different. In Gresham's Law on currency, there was a mandated currency based on a variable quality product -- cows! These circumstances are not even remotely similar to the unmandated product of equal quality like VWs; the conclusion rhymes, but no more than a VW sounds like a cow.
Criteria for a lemon market1. Asymmetry of information
2. An incentive exists for the seller to pass off a low quality product as a higher quality oneno buyers can accurately assess the value of a product through examination before sale is made
all sellers can more accurately assess the value of a product prior to sale
3. Sellers have no credible disclosure technology (sellers with a great car have no way to credibly disclose this to buyers)
4. Deficiency of *effective* public quality assurances (by reputation or regulation)
5. Deficiency of *effective* guarantees / warranties
Skipping the too-hard biases in the above, look at the last parts, 3, 4 and 5. These are not the Lemons of Akerlof. Indeed,
Akerlof argues that many market institutions may be regarded as emerging from attempts to resolve problems due to asymmetric information. One such example is guarantees from car dealers; others include brands, chain stores, franchising and different types of contracts.
He argues that the arisal of institutions such as franchises, assurances and warranties will solve the lemons problem; Wikipedia suggests that their impossibility is the problem, not the solution. The article seems to have got it wrong with the examples as well. I agree the example on Indian milk delivery looks good, but the used computer market is less a match. What is a complete failure of a match is this:
Online dating clubs.... the limited description of an individual in an online dating advertisement is "...likely to be a careful selection of qualities and possibly false," [4] which leads to a situation of asymmetrical information; the person "selling" themselves as a potential dating partner knows far more about their qualities and defects than the recipient of the notification.
This is only true if we consider a date to be akin to slavery, i.e., the market where women buy men. It takes two to tango: dating generally involves a symmetrical exchange at practically all levels, the more so since equality reared her ugly head. Unless your date wears citric lipstick, he won't taste of lemon!

Which brings us to one final mistake, and this time it is not Wikipedia's fault, but the Nobel prize committee's and probably most of the economic world. Recall that these guys mentioned above won the Nobel Prize in Economics for their creation of an entire new sub-field:
For more than two decades, the theory of markets with asymmetric information has been a vital and lively field of economic research. Today, models with imperfect information are indispensable instruments in the researcher's toolbox. Countless applications extend from traditional agricultural markets in developing countries to modern financial markets in developed economies. The foundations for this theory were established in the 1970s by three researchers: George Akerlof, Michael Spence and Joseph Stiglitz. They receive the Bank of Sweden Prize in Economic Sciences in Memory of Alfred Nobel, 2001, "for their analyses of markets with asymmetric information".
So, where are the sour grapes? Above, I contrasted Akerlof as against Stiglitz & Rothschild, as they looked at the alternate sides of the asymmetry. That is, Akerlof looked the ignorant small buyer against the all-knowing big seller, and Stiglitz & Rothschild looked at how the ignorant seller operates against the all-knowing small buyer!
What a fascinating contrast! But, as any economist worth his salt knows, all economics reduces to a simple 2 x 2 chart. The market in asymmetric information is no exception:
| The Market for Goods, as described by Information and by Party | Buyer Knows | Buyer Lacks |
|---|---|---|
| Seller Knows | Efficient Goods | Lemons (used cars) |
| Seller Lacks | Limes (Tax, Insurance) | Silver Bullets (Security) |
Indeed, the market in asymmetric information isn't asymmetric! It's better described as insufficient or imperfect, and only half of it is asymmetric. There are "perfectly symmetric" markets, upper left, and there are "symmetrically flawed" markets of insufficient information, lower right.
This latter is the domain of Michael Spence, an unsung hero of economic thought. You and your date belong here, too, although whether his writings will help you to get along is an open question.
So the Nobel Prize committee got the penultimate word wrong, and this may be why people commonly make two mistakes in understanding this market:
#1 "it's all about Akerlov's market for lemons."#2 " 'signals' are what you need to solve the market for lemons."
Both Wrong: Firstly, there are three difficult spaces, Spence and S&R being equally well-ignored. Secondly, the solutions from each are mishmashed from one space to the other, and hence misapplied. C.f., signalling lemons doesn't help, as signals come from Spence, not Akerlof.
As I say, Wikipedia did not make these mistakes. Instead, the article on Spence says it well:
(Hmmmm..... I am forced to say..... having read that, I now realise I have been making a mistake in my understanding Spence, in that I ignored the cost argument..... more thought required!)
We continue to make these mistakes, starting with the Nobel Prize committee, through other august names, and ending with myself included. Which brings us to (my) closing comment, and the point: unless you read the original source material, you may well end up writing a lemon, or to similar taste, perpetuating someone else's lemon.
So let's really close with VW's original source material, kindly written in clear by University of Iowa's adclass, at the bottom of the advertisement above:
The Volkswagen missed the boat.The chrome strip on the glove compartment is blemished and must be replaced. Chances are you wouldn't have noticed it; Inspector Kurt Kroner did.
There are 3,389 men of our Wolfsburg factory with only one job; to inspect Volkswagens at each stage of production. (3,00 Volkswagens are produced daily; there are more inspectors than cars.)
Every shock absorber is tested (spot checking won't do), every windshield is scanned. VWs have been rejected for surface scratches barely visible to the eye.
Final inspection is really something! VW inspectors run each car off the line onto the Funktionsprüfstand (car test stand), tote up 189 check points, gun ahead to the automatic brake stand and say "no" to one VW out of fifty.
This preoccupation with detail means the VW lasts longer and requires less maintenance, by and large, than other cars. (It also means a used VW depreciates less than any other car.)
We pluck the lemons; you get the plums.
Ad copy: Volkswagen of America. (A) Doyle Dane Bernback, New York. (Ad) Helmut Krone. (P) Wingate Paine. circa 1960s.
(** Editor's note: The wikipedia article is now improved and may be a better rendition of the Akerlof paper. However, it only gives an idea, and an insufficient base for reliance. It behoves to read the original paper in depth before commenting.)
February 28, 2007
U.S. Dollar Drops Against Counterfeit U.S. Dollar
In the wake of yesterday's dramatic drop in many world stock markets:
U.S. Dollar Drops Against Counterfeit U.S. Dollar
February 25, 2007NEW YORK-At the close of trading Monday, the U.S. dollar dipped to a record low of $.60 against the counterfeit U.S. dollar, which also outpaced the dollar against the euro and the yen.
"We don't even accept regular U.S. dollars anymore," said Union, NJ 7-Eleven manager Rick Grove, echoing the sentiments of merchants nationwide. "We've gotten stung a few times taking in the real ones. I always tell my cashiers, if it feels fake to the touch, and you can't see both sides when you hold it up to the light, it's fine."
Concerned about further devalutation of standard U.S. currency, Federal Reserve Chairman Ben Bernanke has suggested that Congress outlaw counterfeit bills entirely.
© Copyright 2007 Onion Inc. All rights reserved.
The onion's satire aside, the way the US dollar and its counterfeits compete ... and cooperate ... around the world is fascinating stuff, and is food for thought for us FCers seeking to protect our system. We will meet our enemy, and...
November 22, 2006
CFP: 6W on the Economics of Information Security (WEIS 2007)
The Heinz School, Carnegie Mellon University Pittsburgh (PA), USA
June 7-8, 2007
http://weis2007.econinfosec.org/
C A L L F O R P A P E R S
Submissions due: March 1, 2007
How much should we spend on security? What incentives really drive privacy decisions? What are the trade-offs that individuals, firms, and governments face when allocating resources to protect data assets? Are there good ways to distribute risks and align goals when securing information systems?
The 2007 Workshop on the Economics of Information Security builds on the success of the previous five Workshops and invites original research papers on topics related to the economics of information security and the economics of privacy. Security and privacy threats rarely have purely technical causes. Economic, behavioral, and legal factors often contribute as much as technology to the dependability of information and information systems. Until recently, research in security and dependability focused almost exclusively on technical factors, rather than incentives. The application of economic analysis to these problems has now become an exciting and fruitful area of research.
We encourage economists, computer scientists, business school researchers, law scholars, security and privacy specialists, as well as industry experts to submit their research and attend the Workshop. Suggested topics include (but are not limited to) empirical and theoretical economic studies of:
- Optimal security investment
- Software and system dependability
- Privacy, confidentiality, and anonymity
- Vulnerabilities, patching, and disclosure
- DRM and trusted computing
- Trust and reputation systems
- Security models and metrics
- Behavioral security and privacy
- Information systems liability and insurance
- Information threat modeling and risk management
- Phishing and spam
**Important dates**
- Submissions due: March 1, 2007
- Notification of acceptance: April 10, 2007
- Workshop: June 7-8, 2007
For more information visit http://weis2007.econinfosec.org/.
October 10, 2006
NZ on Identity
It is almost but not quite a truism that if you make identity valuable, then you make identity theft economic, amongst other things. Here's New Zealand's take on the issue, at the end of a long article on government reform:
Let me share with you one last story: The Department of Transportation came to us one day and said they needed to increase the fees for driver's licenses. When we asked why, they said that the cost of relicensing wasn't being fully recovered at the current fee levels. Then we asked why we should be doing this sort of thing at all. The transportation people clearly thought that was a very stupid question: Everybody needs a driver's license, they said. I then pointed out that I received mine when I was fifteen and asked them: "What is it about relicensing that in any way tests driver competency?" We gave them ten days to think this over. At one point they suggested to us that the police need driver's licenses for identification purposes. We responded that this was the purpose of an identity card, not a driver's license. Finally they admitted that they could think of no good reason for what they were doing - so we abolished the whole process! Now a driver's license is good until a person is 74 years old, after which he must get an annual medical test to ensure he is still competent to drive. So not only did we not need new fees, we abolished a whole department. That's what I mean by thinking differently.
The rest of the article is very well worth reading, for a summary of NZ's economics successes.
July 22, 2006
More Brittle Security -- Agriculture
And we thought Thunderbird's security was slow and brittle -- consider Nick's comments on agriculture:
The crucial role of security for the history of farming may also shed light on the birth of agricultural in the first place. Hunter-gatherers were very knowledgeable about plants and animals, far more than the typical modern. It would not have taken a genius -- and there were many, as their brains were as large as ours -- to figure out that you can plant a seed into the ground and it will grow. There must have been, rather, some severe institutional constraints that prevented agriculture from arising in the first place. The basic problem is that somebody has to protect that seedling for several months from enemies, and then has to harvest it before the enemy (or simply a envious neighbor) does. Security and allocation of property rights between providers of security and providers of farm labor were the intractable problems that took vast amounts of trial and error as well as genius to solve in order for agriculture to take root.
Nick's referring to the arisal of property rights:
There were at least eight centers of secondary innovations (e.g. crop and livestock domestications and agricultural tools) that look independent: the Middle East, China, India, sub-Saharan Africa, Peru, central America, eastern North America, and New Guinea. But they all occured within a few thousand years of each other, after at least 100,000 years of anatomically modern humans.
(My emphasis.) He refers to it as a cultural revolution, perhaps in deference to its title, but what it really is is the arisal of patterns of cooperation, in this case through the particular mechanism of property rights.
I've postulated in the past that property rights needs two essential elements: 1. the claim, a.k.a. the declaration of a title in property, and 2. the defence, a.k.a., the big man with the pointy stick. I'll stick to that hypothesis as the two essential elements of property, although running the experiment seems longer than worthwhile.
(See recent posts on negotiation for another form of cooperation.)
June 28, 2006
on Leadership - negotiating the RTFM into the realm of forgotten schoolyard jokes
Yesterday, I claimed that leadership in tech teams is more or less down to one thing -- communication. That is the one huge gaping hole in our skills. Now, there are certainly other holes, and deep students of leadership (have you read the Kotter articles yet?) will point them out. My claim here is that the comms hole is so big in tech teams that if you fill that you'll be a happy little vegemite; if you fill any other hole, you'll be justing sucking on salt.
Bang for buck, it is communication that will give you the biggest return on investment. You can see some efforts over at Mozo where Mitchell posts on 8 sessions with staff seeking some understanding at mission. Why? She is seeking to reduce the surface area of the discussions at hand. To do that, she has to get everyone on board; first with the things that Mozilla must do, and then on the things that Mozilla thinks it should do. Bit by bit.
Communication in tech teams however goes way way beyond corporate mission statements.
In essence we as leaders have to unwind the RTFM factor. A leader has to know how to deal with the deep-seated needs of tech people and how to acquire and transmit the information needed for all the people to contribute. The way to deal with this is a little known skill and science called negotiation.
So let's talk about that. First, definition. What is negotiation?
Negotiation is the reaching of agreement, where before there was none, by means of dialogue and communication.
How often do you negotiate? Much more than you think. In fact, almost all difficult discussion falls under the rubic of negotiation. Negotiation occurs whenever there is an issue of contention. It happens when you buy a house, marry, discipline a child, choose a school, pick a restaraunt, ask your boss for help, as well as buying an orange at a fruit market.

Do you disagree? Then we must negotiate. If we do agree on this point, it was an easy negotiation, and maybe you can save yourself the bother of reading further.
Most people think of negotiation as something that happens rarely, when buying something with an uncertain price tag, or trying to get a raise in your job. That is a mistake; negotiation is the process that occurs whenever there is some form of dispute or disagreement that is resolved by discussion.
Most people don't ever get a chance to learn it properly, and pick it up as they go along. For this reason, most people make terrible negotiators. There are a very few naturals, but for the most part, only learning some home truths will set you on the path to real negotiation. There is only one large group in society that has negotiation beaten into them, and they are *not* represented well in the techie field.
So I will ignore them for now, and thrust on. Let's talk negotiation. Let's negotiate some serious talk.

Negotiation divides into two halves: win-win and win-lose. Win-win sits in contrast with win-lose. The two do not go together, and much of ones basic skill is in knowing when each is appropriate, how to move between the two, and stick with the appropriate one. Today's post is really about win-win -- explaining the much over-hyped and misunderstood term of win-win.
The basic principle behind the separation of negotiation into these two components is known as The Prisoners' Dilemma. In this simple problem, two people have to cooperate, but the problem is such that if one of them cheats, that cheater earns a larger payoff.
| Who wins? | I lose | I win |
|---|---|---|
| You lose | (failure) | win-lose |
| You Win | win-lose | win-win |
The Prisoner's Dilemma is a game from economics. Do not be scared by this, it is a very simple game, with some wonderful and thought provoking results that explain many complexities in your day to day life. Understanding this game will payoff in many ways -- the first of which is why Frank's suggestion of Reciprocity works!
This problem is a dilemma, because the total payout if we cooperate is higher, but the individual payout if one can successfully cheat is higher for the cheater. Do we cooperate or do we cheat? (These tables will be better on the HTML - click the link). But if we both cheat, we both lose big time.
| Payouts: yours / mine | I cheat | I cooperate |
|---|---|---|
| You cheat | -10 / -10 | 10 / -20 |
| You cooperate | -20 / 10 | 5 / 5 |
In the above table, see how if only one of us cheats, the payout for the cheater is high, but the cooperator is punished badly! If we both cooperate, we get less each, but we are both in the positive.
Now add the numbers together - the sum for both of us cooperating is 10, and all of the others squares are summed to much less. So, as a group, we are better off cooperating, and individually, we are better off cheating, but making sure the other does not cheat. Are we saying that we need to cheat, but stop the other person cheating?

Sounds like real life, right?
Classically, we talk about two accused crooks brought in for questioning by the police -- they are the two prisoners in the dilemma. If both of them keep quiet, then both walk, as there is no real evidence of the crime. If one of them blabs, then the other goes to jail for a long time because he also lied, while the blabber gets off lightly for turning evidence. The question is, for you as a crook, how do you stop the other guy blabbing?
What can we do to try and reach the best payoff? How can our two crooks stay out of jail? These are the central questions of negotiation - once answered, they allow a selection of tactics and process that helps achieve the best payoff.
Before we can achieve the best payoff, we must know in which square of the Prisoner's Dilemma we find ourselves. Let's imagine we have decided to go for a group benefit -- the common good. How do two crooks ensure that neither blabs?
Several ways! They could work together and establish trust, by doing lots of heists, one after the other. Alternatively, the two crooks could employ revenge - if Joe blabs and Fred goes to jail, Joe will find the mob chasing him later on. This expands the basic game into a more complex form of game involving external payoffs. Another way is to establish trust via bonds. Maybe marry each other's sister, or owe each other a bounty?

The key then is to create an external context and to add something else to the game. In the first suggestion above, the two crooks expect to do many jobs in the future. So, their combined payoff in the future depends on doing many jobs together, and they can only do that if they keep together as a team. In the second suggestion, they add a future punishment, so that the rules of the game, and the consequent payoffs, are modified to ensure the cheater loses his incentive (see Stag hunt). Finally, they create Family - which is an extended, powerful relationship. Just like a company, or a tribe, or a football team, our two crooks can bond together in a group that carries them past today's challenges.
In simple terms, they can change the payoffs. The more complex solution is to make the game a repeating game. That is, to make each dilemma one of many, so that each cheating payoff has to balance the loss of potential future shared benefits.
And, that is the key to understanding whether one is in a win-win scenario or a win-lose scenario:
Is this the only time we negotiate? Is this the end of the game? Is there another round?

If there is more to come, then you are, basically, in a win-win negotiation session. If there is no more to come, then you are in win-lose.
That's the first and most basic lesson of negotiation.
Am I in win-win or win-lose?
You must ask yourself this question so frequently it becomes second nature. And, this question is often the same as asking
Is this the only time we negotiate, or do we have a future?
As much second nature is your assessment as to whether you, or your negotiating partner, is considering the future or not.
From here, the world forks. You go to either the relationship process of win-win or, you go to the best payoff of win-lose.
Which are you in? If it is not obvious, you will find out if I post again.
June 25, 2006
FC++3 - The Market for Silver Bullets
In this paper I dip into the esoteric theory of insufficient markets, as pioneered by Nobel Laureate Michael Spence, to discover why security is so difficult. The results are worse than expected - I label the market as one of silver bullets. Yes, there are things that can be done, but they aren't the things that people have been suggesting.
This paper is a bit tough - it is for the serious student of econ & security. Far from being the pragmatic "fix this now" demands of Philipp Gühring and the "rewrite it all" diagnosis of Mark Miller, it offers a framework of why we need this information out there in the public sphere.
What is security?As an economic `good' security is now recognised as being one for which our knowledge is poor. As with safety goods, events of utility tend to be destructive, yet unlike safety goods, the performance of the good is very hard to test. The roles of participants are complicated by the inclusion of agressive attackers, and buyers and sellers that interchange.
We hypothesize that security is a good with insufficient information, and reject the assumption that security fits in the market for goods with asymmetric information. Security can be viewed as in a market where neither buyer nor seller has sufficient information to be able to make a rational buying decision. These characteristics lead to the arisal of a market in silver bullets as participants herd in search of best practices, a common set of goods that arises more to reduce the costs of externalities rather than achieve benefits in security itself.
Does it really show that the security market is one of silver bullets, and best practices are bad, not good? You be the judge! That's what we do in FC++, put you in the peer-review critic's seat.
June 23, 2006
The Fed knows - more evidence that the Fed is managing the washback
I proposed a hypothesis on US debt levels few weeks back: "US debt has dramatically expanded not (only) because of Bush administration but (also) because of the buyback of US currency as it shifts its status from 'absolute reserve' to 'leading reserve' ."
I asked around and didn't get any confirmation on the hypothesis of the managed washing of the US currency! Here's an indication that others are also spotting it. Anne Streiber writes:
There is evidence that the US is attempting to manage the decline by purchasing its own debt. As Asian purchasing of US paper declined last month, the slack was taken up by Caribbean and UK banks that would not normally have the liquidity to make such purchases. Therefore, they are acting for a third party, and the only party that would buy dollars when a loss in value is inevitable is the US Treasury.
Curiously, we've known about the USD washback to the US for years, in the sense of an expectation. And we've known that US debt levels have been soaring for a long time. But it took the confirmatory evidence from central banks around the world, post facto, before we were confident enough in our understanding to take the next step - join the two as causal.
Which means, the Fed does know a lot more than we think. We are years behind.
June 11, 2006
USD shift in reserve currency status confirmed - call it 10% per year
Below are some figures below about how the USD is now losing some of its power as world currency. Note that this has been expected for many years now, but obviously if you are one of the CBs that wants to shift reserves, you want to do it without stating it. So we've had to sit here on the prediction for some time, biting our fingernails.
On Thursday, June 8, Russia became the latest in the list of countries that shifted a part of its Central Bank reserves from the dollar. Sergei Ignatyev, chairman of the Central Bank, said that only 50 percent of its reserves are now held in dollars, with 40 percent in euros and the rest in pounds sterling. Earlier it was believed that just 25-30 percent of Russia's reserves were held in euros, with virtually all the rest held in dollars.
Let's do the maths, so as to explain why this is significant. If we take the shift as from 60% to 50%, allowing euros to rise from 30% to 40%, then we see a relative shift in USD demand of say 20%. Call it over 2 years, and we can guess at a shift of 10% per year in the total international currency use of USD.
If all countries are doing this - and there are good game theory, trade and geopolitical reasons to suspect this - then we see a massive washing around the world of some 10% of the USD during the space of a year. This will go on until we reach a new stability, a level which is anyone's guess at the moment.
What then happens to the "value?" Obviously, the music stops at some point. Now, my macroecon is a bit rusty, but here's what I think happens. Most of the money bounces around the world and demand then exceeds supply, so the prices starts dropping. As there is a clear need to totally get rid of a substantial lump of it, this goes on until that is "got rid of." But how do we get rid of currency? Who takes it back these days?
The mechanism for this apparent paradox is US assets. As the USD price goes down, US assets start to look cheaper and cheaper. So more and more of the value finds itself coming out of the international washing machine and into the US markets. Stocks (shares, companies) and real estate. IP catalogues. Money market investment. Anything available that will be for sale in USD will be purchased.
Now, the sellers of these things will either be foreigners (in which case nothing changes, the music is still playing) or they will be US persons, in which case, they are happy to hold dollars. Demand for dollars is always firm in the US, by definition.
So the music stops when that above value lands in the US. The foreign dollars are exchanged for US assets. A great sell-off, in other words.
But wait - what happens to the dollars then? Well, there are now too many of them in the US. Now we see why the US economy is continuing to boom. The dollars are coming back home, and *effective inflation* is running at the amount calculated above.
(Well, it's a bit worse than that. 2/3 of the dollar is outside the US. So a 10% shift from outside to inside means a doubling effect on local dollars. Yup, there is in these assumptions a 20% increase in the number of dollars washing back to the US every year, but bear in mind these are napkin numbers.)
What does this mean? Likely that the housing bubble will not burst, or not burst so aggressively. Likely that businesses will find plenty of cash for loans, so they'll be running on infinite credit. The stock market is still pointed up! But prices will be shifting against companies and individuals in a fairly significant jolt of inflation, and what's more, the Fed won't be able to curtail it as it normally does.
To stop it, the Fed would have to soak up that liquidity. How's it going to do that? Issue more bonds? Hmmm, there's a thought. Is the massive debt increase over the last 6 years really nothing to do with the administration, but it is all the flip side of soaking up the wash back? Any real macroeconomists in the house? Can we do some napkin numbers on how much additional debt has been issued and how much currency is washing in? (Ed: Confirmation?)
Full article:
Russia Shifts Part of Its Forex Reserves from Dollars to EurosCreated: 09.06.2006 11:02 MSK (GMT +3), Updated: 16:06 MSK MosNews
On Thursday, June 8, Russia became the latest in the list of countries that shifted a part of its Central Bank reserves from the dollar. Sergei Ignatyev, chairman of the Central Bank, said that only 50 percent of its reserves are now held in dollars, with 40 percent in euros and the rest in pounds sterling. Earlier it was believed that just 25-30 percent of Russia's reserves were held in euros, with virtually all the rest held in dollars.
Russia's gold and foreign currency reserves have grown rapidly over the last few years in tandem with high oil and gas prices. As MosNews has reported earlier, Russia currently has the world's fourth-largest reserves, after China, Japan and Taiwan, and it looks to overcome Taiwan by the end of the year, with reserves growing by $5-6 billion monthly.
The Russian Central Bank's move ties in with increasing signs that Middle Eastern oil exporters are also looking to diversify their reserves out of the dollar. "This is a bearish development for the dollar," Chris Turner, head of currency research at ING Financial Markets, told the British Financial Times. "It reminds us that global surpluses are accumulating to the oil exporters, and Russia is telling us that an increasingly lower proportion of these reserves will be held in dollars. This suggests there is a trend shift away from the dollar."
Clyde Wardle, senior Emerging Market Currency strategist at HSBC, told the paper: "We have heard talk that Middle Eastern countries are doing a similar thing and even some Asian countries have indicated their desire to do so."
Moscow's move was unsurprising. Russia's $71.5billion Stabilization fund, which accumulates windfall oil revenues, is due to be converted from rubles to 45 percent dollars, 45 percent euros and 10 percent sterling. The day-to-day movements of the ruble are monitored against a basket of 0.6 dollars and 0.4 euros. About 39 percent of Russia's goods imports came from the eurozone in 2005, against just 4 percent from the US.
The statement plays into a perception that central banks, which together hold $4.25 trillion of reserves, are increasingly channeling fresh reserves away from the dollar to reduce potential losses if the dollar was to fall sharply.
Copyright ¿ 2004 MOSNEWS.COM
http://www.mosnews.com/money/2006/06/09/dollarshift.shtml
May 26, 2006
How much is all my email worth?
I have a research question. How much is all my email worth? As a risk / threat / management question.
Of course, that's a difficult thing to price. Normally we would price a thing by checking the market for the thing. So what market deals with such things?
We could look at the various black markets but they are more focussed on specific things not massive data. Sorry, bad guys, not your day.
Alternatively, let's look at the US data brokers market. There, lots and lots of data is shared without necessarily concentrating on tiny pickings like credit theft identifiers. (Some of it you might know about, and you may even be rewarded for some of it. Much is just plain stolen out of sight. But that's not today's question.) So how much would one of those data broker's pay for *full* access to my mailbox?

Let's assume I'm a standard boring rich country middle class worker bee.
Another way to look at this is to look at google. It makes most of the money in advertising, and it does this on the tiny hook of your search query. It is also experimenting with "catalogue your hard drive" products (as with Apple's spotlight and no doubt Microsoft and Yahoo are hyperventilating over this already). So it must have a view as to the value of *everything*.
So, what would it be worth to those companies to *sell* the entire monitoring contents of my email, etc, for a year to Yahoo, Google, Microsoft, or Apple? Imagine a market where instead of credit card offers to my dog clogging up mailbox, I get data sharing agreements from the big friendly net media conglomerates.
www.google.com/headspecials
Failing to nail your hammer? Your marketing seems like all thumbs?
Try Google's get-in-his-head program.
Today's only, Iang's emails, buy one, get two free.
Does anyone know any data brokers? Does anyone have hooks into google that can estimate this?
May 14, 2006
Markets in Imperfect Information - Lemons, Limes and Silver Bullets
Twan points to a nice slate/FT article on the market for lemons:
In 1966 an assistant economics professor, George Akerlof, tried to explain why this is so in a working paper called "The Market for 'Lemons.'" His basic insight was simple: If somebody who has plenty of experience driving a particular car is keen to sell it to you, why should you be so keen to buy it?Akerlof showed that insight could have dramatic consequences. Buyers' perfectly sensible fears of being ripped off could, in principle, wipe out the entire used-car market: There would be no price that a rational seller would offer that was low enough to make the sale. The deeper the discount, the more the buyer would be sure that the car was a terrible lemon.
If you are unfamiliar with Akerlof's market for lemons, you should read that article in full, and then come back.
This whole area of lemons is sometimes called markets in asymmetric information - as the seller of the car has the information that you the buyer doesn't. Of course, asymmetries can go both ways, and sometimes you have the information whereas the other guy, the seller, does not. What's up with that?
Well, it means that you won't be able to get a good deal, either. This is the market in insurance, as described in the article, and also the market in taxation. These areas were covered by Mirlees in 1970, and Rothschild & Stiglitz in 1976. For sake of differentiation, as sometimes these details matter, I call this the market for limes.
But there is one final space. What happens when neither party knows the good they are buying?
Our gut reaction might be that these markets can't exist, but Michael Spence says they do. His example was the market for education, specifically degrees. In his 1973 paper entitled "Job Market Signalling" he described how the market for education and jobs was stable in the presence of signals that had no bearing on what the nominal goal was. That is, if the market believed a degree in arts was necessary for a job, then that's what they looked for. Likewise, and he covers this, if the market believed that being male was needed for a job, then that belief was also stable - something that cuts right to the core of our beliefs, because such a belief is indeed generally irrelevant but stable, whether we like it or not.
This one I term the Market for Silver Bullets, a term of art in the computing field for a product that is believed to solve everything. I came to this conclusion after researching the market for security, and discovering that security is a good in Spence's space, not in Akerlof's nor Rothschild and Stiglitz's spaces. That is, security is not in the market for lemons nor limes - it's in the tasteless spot in the bottom right hand.
Yup, because it is economics, we must have a two by two diagram:
| The Market for Goods, as described by Information and by Party | Buyer Knows | Buyer Lacks |
|---|---|---|
| Seller Knows | Efficient Goods | Lemons (used cars) |
| Seller Lacks | Limes (Tax, Insurance) | Silver Bullets (Security) |
Michael Spence coined and explored the sense of signals as being proxies for the information that parties were seeking. In his model, a degree was a signal, that may or may not reveal something of use. But it's a signal because we all agree that we want it.
Unfortunately, many people - both economists and people outside the field - have conflated all these markets and thus been lead down the garden path in their search for fruit. Spence's market in silver bullets is not the same thing as Akerlof's market in lemons. The former has signals, the latter does not. The latter has institutions, the former does not. To get the full picture here we need to actually do some hard work like read the original source papers mentioned above (Akerlof and Spence aren't so bad, but Rothschild & Stiglitz were tougher. I've not yet tried Mirrlees, and I got bogged down in Vickery. All of these require a trip to the library, as they are well-pre-net papers.)
In particular, and I expand on this in a working draft paper, the bitter-sweet truth is that the market for security is a market for silver bullets. This has profound implications for security research. But for those, you'll have to read the paper :)
April 12, 2006
Worldwide Internet boom to finish by 2009
From a BBC article sent by Daniel, we find these figures:
| Worldwide: | 12.8% |
| USA: | 68.1% |
| UK: | 62.9% |
| EU: | 49.8% |
| Russia: | 16.5% |
| Ukraine: | 11.4% |
| China: | 8.5% |
| Uzbekistan: | 3.3% |
Also, this comment:
By the turn of the century, Russia had about two million users and now, 10 years later, it accounts for nearly 24 million. At 16.5% of the population, Russia's web community is still small compared to the European Union, where the average is nearly 50%, and about 30% in newer member-states from the east, such as Hungary and Poland.
Which tells us that Internet growth in Russia is running around 70% per annum. At that rate, Russia will cross 50% within 2 years. If the rest of the world is growing at the same rate, it will cross 50% within 3 years. China will be there within months, middle of 2009.
Crossing the halfway mark is strategically important - growth generally has to slow down, and generally it hits a brick wall. You rarely get to 100%, and the US and UK are still stuck between 60-70% - a good working number.
(This is what happened in 2000. Those who saw it coming will recall that PC and Internet sizes both passed the 50% mark around the turn of the century in the western economies. The bubble ended, like clockwork.)
PS: the rest of the article is laughable, a reason in and of itself for reading blogs not traditional news feeds.
January 07, 2006
Our Private Bayesian Rules Engine
The Economist has a great article on how psychologists are looking at how computer scientists are using Bayesian prediction engines for things like help wizards and spam filters. The Psychologists asked an unusual question - maybe people use Bayesian logic?
Of course! Er, well, maybe. Science needs to test the hypothesis, and that's what they set out to do:
Dr Griffiths and Dr Tenenbaum conducted their experiment by giving individual nuggets of information to each of the participants in their study (of which they had, in an ironically frequentist way of doing things, a total of 350), and asking them to draw a general conclusion. For example, many of the participants were told the amount of money that a film had supposedly earned since its release, and asked to estimate what its total “gross” would be, even though they were not told for how long it had been on release so far.Besides the returns on films, the participants were asked about things as diverse as the number of lines in a poem (given how far into the poem a single line is), the time it takes to bake a cake (given how long it has already been in the oven), and the total length of the term that would be served by an American congressman (given how long he has already been in the House of Representatives). All of these things have well-established probability distributions, and all of them, together with three other items on the list—an individual's lifespan given his current age, the run-time of a film, and the amount of time spent on hold in a telephone queuing system—were predicted accurately by the participants from lone pieces of data.

There were only two exceptions, and both proved the general rule, though in different ways. Some 52% of people predicted that a marriage would last forever when told how long it had already lasted. As the authors report, “this accurately reflects the proportion of marriages that end in divorce”, so the participants had clearly got the right idea. But they had got the detail wrong. Even the best marriages do not last forever. Somebody dies. And “forever” is not a mathematically tractable quantity, so Dr Griffiths and Dr Tenenbaum abandoned their analysis of this set of data.The other exception was a topic unlikely to be familiar to 21st-century Americans—the length of the reign of an Egyptian Pharaoh in the fourth millennium BC. People consistently overestimated this, but in an interesting way. The analysis showed that the prior they were applying was an Erlang distribution, which was the correct type. They just got the parameters wrong, presumably through ignorance of political and medical conditions in fourth-millennium BC Egypt. On congressmen's term-lengths, which also follow an Erlang distribution, they were spot on.
Which leaves me wondering what an Erlang distribution is... Wikipedia doesn't explain it in human terms, but it looks like a Poisson distribution:
Curious footnote - look at who they credited as the source of their graph of distributions.
December 24, 2005
A new security metric?
I have a sort of draft paper on security metrics - things which I observe are positive in security projects. The idea is that I should be able to identify security projects, on the one hand, and on the other provide some useful tips on how to think past the press release. Another metric just leaped out and bit me from that same interview with Damien Miller:
Why did you increase the default size of new RSA/DSA keys generated by ssh-keygen from 1024 to 2048 bits?Damien Miller: Firstly, increasing the default size of DSA keys was a mistake (my mistake, corrected in the next release) because unmodified DSA is limited by a 160-bit subgroup and SHA-1 hash, obviating the most of the benefit of using a larger overall key length, and because we don't accept modified DSA variants with this restriction removed. There are some new DSA standards on they way that use larger subgroups and longer hashes, which we could use once they are standardized and included in OpenSSL.
We increased the default RSA keysize because of recommendations by the NESSIE project and others to use RSA keys of at least 1536 bits in length. Because host and user keys generated now will likely be in use for several years we picked a longer and more conservative key length. Also, 2048 is a nice round (binary) number.
Spot it?
Here it is again in bold:
Damien Miller: Firstly, increasing the default size of DSA keys was a mistake (my mistake, corrected in the next release) because [some crypto blah blah]
A mistake! Admitted in public! Without even a sense of embarrassment! If that's not a sign that the security is more important than the perception then I don't know what is...
Still not convinced? When was the last time you ever heard anyone on the (opposing) PKI side admit a mistake?
December 13, 2005
GP2 - Growth and Fraud - Instructing Security at GP
In the previous discourse (Meet at the Grigg Point), we discussed how growth works, and said that GP was the tipping point at which the demo became a system. From this model, we can make a number of observations, chief of which is about Security to which we now turn.
One of the security practitioner's favourite avisos is to suggest that the security is done up front, completely, securely, with strong integration, not to mention obeisance. Imagine the fiercely wiggling finger at this point. Yet, this doctrine has proven to be a disaster and the net's security pundits are in the doldrums over it all. Let's examine some background before getting to how GP helps us with this conundrum.
Hark to the whispering ghosts of expired security projects. Of those that took heed of the doctrine, most failed, and we do mean most. Completely and utterly, and space does not permit a long list of them, but it is fair to say that one factor (if not the sole or prime factor) is that they spent too much on security and not enough on the biz.
Some systems succeeded though, and what of them? These divide into three:
- those that implemented the full model,
- those that implemented a patchwork or rough security system, and
- those that did nothing.
Of those few systems that heeded the wiggling finger and succeeded, we now have some substantial experience. Heavily designed and integrated systems that succeeded initially went on to expose themselves to ... rather traumatic security experiences. Why? In the worst cases, when the fraud started up (around GP) it simply went around the security model, but by that time the model was so cast in mental concrete that there was no flexibility to deal with it. One could argue that these models stopped other forms of fraud, but these arguments generally come from managers who don't admit the existence of the current fraud, so it's an argument designed to be an argument, not something that pushes us forwards.
Perversely, those systems that did nothing had an easier time of it than even those that implemented a patchwork, because they had nothing to battle.
fig 4. Investment directs the Revenue Curve
Why is this? I conjecture that at the beginning of a project the business model is not clear. That is, none of us really knows what to do, but darn it we're inspired! Living and dreaming in Wonderland as we are, this suggests that the business model migrates very quickly, which means that it isn't plausible to construct a security model that lasts longer than a month. Which means several interlinked things:
- until the business model is proven, there is little point in building a security model for security per se as an unproven model doesn't deserve to be protected,
- the more attention that is put into the security model, the more the security model kicks back and insists that the business model stop changing, dammit!,
- the more money that is put into the security model, the less money there is available for business activity, and
- the security system puts a cost on the whole system, slowing growth.
Now, anyone who's aware of compounding knows where to put the value: building the business, and security rarely if ever builds business, what it does is protect business that is already there. It's the issue of compounding we turn to now. Figure 4 depicts the cost of investment down below the horizontal axis, and the growth above. Investment isn't exponential, so it's not a straight line. Initially it grows well, but then hits limits to growth which doom it to sub-exponential growth, which is probably just as well as any investor I've met prefers less than exponential growth in contributions!
While not well depicted in that figure, consider that the pattern of investment fundamentally sets the growth model. The Orange line dictates the slope and placement of the Blue!
Now let's fiddle a bit in figure 5. Assume that investment is fixed. But we've decided to invest upfront in a big way in security, because that's what everyone said was the only way to sleep well at nights. Now the Orange Region of total investment over time is divided into two - above the thin line is what we invest in the business, and below the line is the security. The total is still the same, so security investment has squeezed us upfront.
fig 5. More Costs means Growth is Flatter and GP is Later
See what happens? Because resources were directed away from business, into security, the growth curve started later, and when the security model kicked in, the curve flattened up. That's because all security has a cost. If you're lucky, and your security team is hot (and I really do mean blistering here, see what I wrote about "most" above...) the kink won't be measurable.
Why is it so big? And why don't managers wade in there with mallet and axe and bash it back into forward growth before we can say hedonism is the lifeblood of capitalism? Oddly, the chances of a manager seeing it are pretty remote because seeing drivers to growth is a very hard art, most people just can't see things like that and assume that either today goes for ever, or tomorrow will solve everything. The end users often notice it, and respond in one of two ways: they scream and holler or they stop using the system. An example of the former is from the old SSL days when businesses screamed that it sucked up 5 times the CPU ... so they switched to hybrid SSL/raw sites. An example of the latter is available every time you click on a link and it asks you to register for your free or paid account to read an article or to respond to an article.
Students of security will be crying foul at this point because security does good. So they say. In fact what it does is less bad: until we draw in the fraud curve which security nicely attempts to alleviate the bad done by fraud, security is just a cost. And a deadweight one at that. Which brings us to our third observation: the upfront attention to security has pushed GP way over to the right, as it must do if you agree with the principle of GP.
So where is all this leading us? At this point we should understand that security is employed too early if employed at the beginning - the costs incur a dramatic shift of the curve of growth. Both to the right, and a flattening due to the additional drain. And we haven't even drawn in the other points above: restarts and kickback.
This logic says that we should delay security as long as we can, but this can't go on forever. The point where the security really kicks in and does less bad is when the bad kicks in: the fraud curve that slides up and explodes after GP. Then, the ideal point in which to kick security is after GP and before the fraudulent red line runs in ink onto the balance sheet.
Which leads us to question - finally, for some, no doubt - When is GP?. That is saved to another day :-)
December 11, 2005
GP1 - Growth and Fraud - Meet at the Grigg Point
Imagine if you will a successful FC system on the net. That means a system with value, practically, but for moment, keep close in your mind your favourite payments system. Success means solid growth, beyond some point of survival, into the area where growth is assured. It looks like this:
fig 1. Exponential Growth
That's an exponential curve, badly drawn by hand. It's exponential because that's what growth means; all growth and shrinkage is exponential. Let's draw that as a logarithmic curve, so we see a straight line:
fig 2. Growth Crosses the Value Tipping Point
I've observed in many businesses of monetary nature that there is a special tipping point. This is where the system transitions from being a working demo that is driven forwards by the keenness of its first 100 or so users, to being a system where the value in the system is inherent and cohesive. In and of itself, the value in the system is of such value that it changes the dynamics of the system.
That's why I labelled it the Self-Sustaining Value Growth Tipping Point, or GP for short. Before this point, the system will simply stop if we the founders or we the users stop pushing. After this point, there is a sustained machine that will keep rolling on, creating more and more activity. In short, it's unstoppable, at least as compared to beforehand.
The shortened term indicates who to blame when you reach that point, because there is something else that is going to happen here: fraud! When the system passes GP, and the value is now inherently stealable for its value, then someone will come along and try to steal it.

fig 3. Fraud Kicks Off then Levels Off
And that theft will probably work, if history is any judge. You'll get a rash of frauds breaking out, either insider or outsider fraud, and all will appear to be chaos. Actually, it's not chaos, it's just competition for different fraud models, and soon it will settle down to a set of best practices in fraud. At this point, when all the mistakes have been made and the surviving crooks know what they are about, fraud will rise rapidly, then asymptotically approach its long run standard level. Ask any credit card company.
Remember that the graph above has a logarithmic vertical axis, so vertical distances of small amounts mean big distances in absolute amounts. The long run gap between those lines - red to blue - is about two if the vertical was log 10. Assuming that, 102 gives us 100 which means fraud is 1% of total at any time. 1% is a good benchmark, a great number to use if you have no other number, even if the preceeding mathematics are rather ropey. Some systems deliver less, some deliver more, it all depends, but we're in the right area for a log chart.
Now that we have the model in place, what can we do with GP? Quite a lot, it seems, but that waits for the next exciting installment of Growth and the Big GP!
This is Part 1 of Growth and Fraud:
November 27, 2005
The Kula Ring - Nick Szabo on why two counter-rotating circulations
Nick Szabo writes on the Kula ring. This is a trade cycle in the literal sense where goods and money (collectibles) rotate around a set of islands. What is curious about this is that there are two monies, one rotating counter-clockwise and the other clockwise. I wondered why this would be so, and Nick may have provided an answer. Click there for the graphics to better understand what we are discussing.
I think Nick has figured out at least one good reason why this is, but in true academic spirit, he's made us figure it out! It took me a few minutess to fill in the gaps. Here's my rendition (which you should ignore until you've read his).
Consider a ring of islands where everyone trades. Goods move around the ring and so does money, and this is not illuminating. Now, consider what happens when one node in the ring has no desire to trade. At this point, we end up with a break in the ring as although this island can still trade in merchant style, back and forth, it has no desire to do so unless it makes a profit.
Even assuming a profit, it has a problem in that it has to hold goods which it can only benefit from when the island in the other direction sends a boat in to trade; in otherwords, one leg of its trade is always in goods it cannot use itself, so it is now engaging in a much more risky transaction. If it is self-sufficient in those goods, then it is unlikely to want to take on that risk except for larger profits. (Or, as Nick suggested, our island could simply pass the money on to the next, for a cut, but that involves a leap of faith.)
Now imagine that there are two kinds of money, one in each direction. Our non-interested node could simply trade the two sorts of money. As both the monies are presumably good, in a way that fish and baskets are not, the risks and leap of faith is removed by money's property. Our anti-trade island can still trade, and not take on any risk. It takes a profit, the kula ring starts moving again, and the efficiency of the system improves overall thus accounting for the profit that our island takes on.
Neat. The opposing rings are stable in a way that a single ring could not be.
(This notion of a single island that does not desire to trade is imaginary of course. The situation lends itself to all moments, and all places. The efficiency improvement is likewise available to all.)
Which simply leaves the question of why the monies rotate at all. I'm guessing that this is an artifact of ensuring as large a group of people as possible is unified on one money! Where there is no network, a ring effect will achieve the same thing, albeit in a longer time frame.
Nice one Nick! Having re-read the above, I think my explanation is no model of clarity, and I wonder if I've got it yet. Maybe it's just one of those puzzles with which to tease amateur economists.
November 21, 2005
Frank Hecker goes to the Mountain - mapping the structure of the Certificate Authority
Frank takes aim at the woeful business known as certificate authorities in an attempt to chart out their structural elements and market opportunities.
Frank argues that CAs can be viewed as providers of one of encryption, DNS-fixes, site identity proofs, or as anti-fraud services. Depending on which you choose, this has grave ramifications for what follows next -- Frank's thesis implicitly seems to be that only one of those can be pursued, and each have severe problems, if not inescapable and intractable contradictions. In the meantime, what is a browser manufacturer supposed to do?
For those who have followed the PKI debate this will not surprise. What is stunningly new -- as in news -- is that this is the first time to my knowledge that a PKI user organisation has come out and said "we have a problem here, folks!" Actually, Frank doesn't say that in words, but if you understand what he writes, then you'd have to be pre-neanderthalic not to detect the discord.
What to do next is not clear -- so it would appear that this essay is simply the start of the debate. That's very welcome, albeit belated.
October 29, 2005
The Economist on the FATF - a net 'bad'
I haven't time to write a proper blog entry on the net 'bad' that is the FATF and the anti-money laundering people. Economists know that anti-money laundering is unlikely to work just from common sense - the procedures proposed and implemented will probably cause more costs than benefits.
But nobody wants to be the messenger writing against one of the world's most powerful, entrenched - and now damaging - bureaucracies. Which makes the Economist's recent article all the more welcome. Read it and spread it:
For now the burden of implementation appears likely to rest with the private sector. “Banks are going to have to start behaving like the FBI and CIA,” contends David Porter of Detica, a Britain-based consultancy with expertise in financial crime. “They need to start connecting the dots.” This “risk-based” approach—concentrating time and energy on checking a smaller number of individuals or businesses based upon their transaction histories, sources of funding and other factors—is gaining wider acceptance.For KPMG's Mr Dillon, the resources already spent on the effort have handed a victory to the terrorists. “The cost to our global economy is so large, they've already had the effect they wanted,” he says. “The increasing costs of compliance and technology are a form of terrorism. We're damaging ourselves.”
The championing of terrorism is an easy soundbite - it can't possibly be wrong can it? Unfortunately, it's dead wrong and in time people will come to think about terrorism in an common sense way. Anyone who is familiar with finance, war or expatriatism can tell you that trying to control flows that small is futile, and all you are doing is adding costs to your own people while arguably providing cover to the people you are trying to catch.
The Economist pulls its punches - but that's because no economist wants to sit down and take the risky job of documenting how the FATF and the OECD are damaging the economy and life in general. As Financial Cryptographers we know how this is the case because we see the rules and regulations, and we see real crooks. There is little connection! But sometimes we can also spot where the anti-money laundering agencies have done palpable and painful damage. Here's such a case:
The gang reportedly stole customer login ids and passwords using keylogging software and then used the information to steal cash from Web banking accounts. The stolen funds were then transferred into the accounts of "mules" who were offered cash in exchange for the use of their bank accounts.
I first spotted this new money laundering technique a year or so back, and no doubt it has been used more extensively before that. What happens is that innocent people are approached with a business deal that just happens to launder funds. The deal is dressed up in such a fashion that the innocent can't tell what the real purpose is, so they go for it. Everyone needs a job, and maybe your lucky break just turned up?
The damage done by the FATF has been to move money laundering out of the domain of the banks - where it can be watched - into the domain of the people. Goodhart's Law, in other words. People who have no clue what is happening are now being used as 'mules' in a crime which when uncovered - and of course that's a very high probability - will do immense damage to their lives and livelihoods.
I've seen it used on students, on expats and others. If you asked those people whether they'd preferred not to have to deal with such a complex fraud, then I'm sure they'd have begged for the chance.
Our thanks go to the FATF and OECD for making business unsafe for all of us. Is asking us all to behave like the FBI and the CIA really worth it? When you do get around to doing the benefit analysis, don't forget the costs that we have to pick up.
October 11, 2005
Is technical trading a Schelling point?
When I first learnt of technical trading I puzzled over it for a long time. By own admission it ignored the rules of theory; yet the technical traders believe in it immensely, and profitably one supposes, and they consider the alternate to be useless. (In this at least, they are in agreement with the efficient markets hypothesis.)
I eventually came to the conclusion that in the absence of any good theory, then a theory of another sort must evolve. Some sort of shared understanding must evolve to permit a small interested community to communicate on a sort of insider basis. There is probably, I postulated, some economics or psychology law somewhere that says that a group of insiders is somewhat contiguous with a shared language, shared theory and eventually shared beliefs.
That sounds like a Schelling point. Is technical trading - flags, pennants, head&shoulders, etc - a Schelling point?
Footnote: wikipedia describes technical analysis which is close. In the above I'm more referring to what they describe as charting.
October 10, 2005
Schelling points
Thomas Schelling and Robert Aumann have won this year's Nobel Prize in Economics for "having enhanced our understanding of conflict and cooperation through game-theory analysis."
See Adam's blog for an explanation of Schelling points, which I was to learn as a daily strategy in Spain. There, when meeting for some social event, various factors made all plans unreliable and sophisticated strategies based on shared knowledge were required just to meet up and have a beer. For example, on finding one bar shut, a thirsty traveller would spiral outwards from that bar to the nearest, and then to the next until the crowd had been found.
Their work goes well beyond such triflings and one day I might find time to understand even a little of it. For now, I cut & paste wiser words:
[Their work] was essential in developing non-cooperative game theory further and bringing it to bear on major questions in the social sciences. Approaching the subject from different angles -- Aumann from mathematics and Schelling from economics -- they both perceived that the game-theoretic perspective had the potential to reshape the analysis of human interaction. Perhaps most importantly, Schelling showed that many familiar social interactions could be viewed as non-cooperative games that involve both common and conflicting interests, and Aumann demonstrated that long-run social interaction could be comprehensively analyzed using formal non-cooperative game theory.
While on economics, Jean sends news that Jimmy Tseng is looking for a PhD candidate to work on the economic aspects of privacy. It is a fully funded position for 4 years in the Netherlands. full details.
Given political news from the lowlands, the Dutch are hell-bent on tarnishing their reputation on privacy, so well done, Jimmy and Jean.
Happy World Standards Day
Allan points out that World Standards Day is coming up:
In case you were not aware, World Standards Day is coming up. This holiday, commemorating the first meeting of the International Organization for Standardization (ISO), is supposed to "raise awareness of the importance of global standardization to the world economy and to promote its role in helping meet the needs of business, industry, government, and consumers worldwide." The topic of my undergrad thesis, IT standards have always been near and dear, so I wanted to plan a party. But when?In Canada and Europe, it will be held on October 14, which is the date of the original meeting. In the US, it will be held on October 6 of this year. Last year, the US observance was on October 13, while in 2003 it was on September 30.
Yes, that's right. The date of World Standards Day is not standardized, and it appears to be the US and ANSI screwing things up.
Friday, down the pub then, unless you are east of the pond, in which case you missed it.
October 09, 2005
Journal of Internet Banking and Commerce
Vol 10 No. 2 Summer 2005 of JIBC is out now:
- From JIBC Publisher Nahum Goldmann
- From Editor-in-Chief Nikhil Agarwal
General and Review Articles
- Belgium EEMA: Focus on Technical and Legal Issues of e-Business in the European Union (By: Edwin JACOBS,University of Leuven)
- China Current Development Situation of E-Commerce in China (By: Alamusi, ChinaEClaw.com)
- USA B2B Marketers Integrate Precision Search to Boost Profitability and Increase Satisfaction Across the eCommerce Value Chain (By: Larry R. Harris, EasyAsk, a division of Progress Software)
- Canada Trust and Confidence and the Digital Economy: Issues and Challenges (By: Prabir K. Neogi and Arthur J. Cordell, Industry Canada)
Research Papers
- Belgium Security as a Legal Obligation: About EU Legislation Related to Security and Sarbanes Oxley in the European Union (By: Edwin JACOBS, University of Leuven)
- Belgium The Law on Electronic Medical Prescription (By: Francis de Clippele, Lawyer in Antwerp, Assistant Lecturer at the University of Antwerp)
- Canada Trust and Confidence and the Digital Economy: Issues and Challenges (By: Prabir K. Neogi, Arthur J. Cordell, Electronic Commerce Branch, Industry Canada)
- India Technical and Entrepreneurial Research Information System: An Applied e-Model for Sustainable Entrepreneurship Development (By: Dhrupad Mathur, S P Jain Institute of Management & Research, Mumbai)
- India A Framework for Evaluating e-Business Models and Productivity Analysis for Banking Sector in India (By: NVM Rao, Prakash Singh, and Neeru Maheshwari, BITS, Pilani)
- Malaysia Do Foreign Banks Lead in Internet Banking Services (By: Boon Han YEAP, Monash University Malaysia, and Kooi Guan CHEAH, Universiti Sains, Malaysia)
- Malaysia Marketing Mix: A Review of 'P' (By: Chai Lee GOI, Curtin University of Technology, Malaysia)
- Qatar E-banking Service Quality: Gaps in the Qatari Banking Industry (By: Norizan M. Kassim, University of Qatar)
- USA and Singapore A Case Study of Electronic Bill Presentment and Payment (EBPP) Integration Using the COIN Mediation Technology (By: Sajindra Jayasena, National University of Singapore, Stephane Bressan, Sloan School of Management and Stuart Madnick, Massachussets Institute of Technology)
Read on for abstracts....
General and Review Articles
BELGIUM: EEMA: Focus on Technical and Legal Issues of e-Business in the European Union
(By Edwin Jacobs)
http://www.aaraydev.com/commerce/JIBC/EdwinJacobs_EEMA_210705,asp
EEMA is Europe's leading independent association for e-Business and promotes collaboration concerning all technical (ICT), legal and business aspects of e-business. EEMA puts the emphasis on today's practical issues. In this respect, EEMA's Legal Interest Group, headed by Prof. Jos Dumortier, focuses on all legal aspects of e-business, i.e. electronic signature, e-invoice, identity management, security legislation (e.g. Sarbanes Oxley in the EU), privacy, etc. On November 22nd and 23 rd this year EEMA will organise a two-day seminar about electronic invoicing and electronic archiving in Brussels.
CHINA: Current Development Situation of e-Commerce in China
(By Alamusi)
http://www.arraydev.com/commerce/JIBC/2005-08/china.htm
The Chinese government puts a great deal of emphasis on E-Commerce work extremely. Generally speaking, the China E-Commerce market contains huge commercial opportunity, the development prospect of which is extremely broad. The relevant organizations are complying with and guiding commercial transformation tendency, absorbing latest international achievement of technical platform, payment system, creditability system, platform construction and safety guarantee system in E-Commerce, further optimizing the external environment, and speeding up development and innovating application complying with national features.
USA: B2B Marketers Integrate Precision Search to Boost Profitability and Increase Satisfaction Across the e-Commerce Value Chain
(By Larry R. Harris)
http://arraydev.com/commerce/JIBC/2005-08/Harris.asp
This article will describe the central role that site search and navigation plays in B2B eCommerce, as well as the defining characteristics of a successful search implementation from both a technical and marketing perspective. This article will also outline how integrating precision search into an existing eCommerce infrastructure can result in higher productivity, streamlined processes, increased conversion rates, greater commercial buyer and partner satisfaction, and higher profits per transaction.
Research Papers
BELGIUM: Security as a Legal Obligation: About EU Legislation Related to Security and Sarbanes Oxley in the European Union
(By Edwin Jacobs)
http://www.arraydev.com/commerce/JIBC/2005-08/security.htm
Since the Sarbanes-Oxley Act there is a worldwide focus on security issues in general. This new focus seems to emphasize that security is a new kind of legal obligation. However, security is already a legal obligation for all EU companies since the early nineties. On top of that, in electronic banking there is a whole range of legal obligations in some way related to security, that were already (and remain) applicable, notwithstanding a possible application of the Sarbanes-Oxley Act on some EU companies. The criterion of what can be 'reasonably expected' as 'bonus pater familias' from service providers, but equally also from their customers, becomes increasingly important.
BELGIUM: The Law on Electronic Medical Prescription
(By Francois de Clippele)
http://www.arraydev.com/commerce/JIBC/2005-08/EMV.HTM
Health care is one of the most important economic and business areas. The European Union has therefore worked out an e-health care strategy to achieving stronger growth and increased effectiveness of services. The application of information and communications technologies (ICT) that affect the health care sector is developing fast in Europe. In this respect various countries have launched pilot projects in order to modernize their medical prescription practices. A model of the electronic medical prescription must respect patient's rights and can only be deployed in a system of security in order to protect the confidentiality.
CANADA: Trust and Confidence and the Digital Economy: Issues and Challenges
(By Prabir K. Neogi and Arthur J. Cordell)
http://www.arraydev.com/commerce/JIBC/2005-08/Negi.htm
Globalization and technological change continue to profoundly affect economic growth and wealth creation. Information and Communications Technologies (ICTs) have been a key enabler and driver of globalization, which is likely to continue as trade and investment barriers continue to fall and communications become ever cheaper, easier and more functional. Every economy requires a physical, institutional and legal infrastructure, as well as understandable and enforceable marketplace rules, in order to function smoothly. In this paper the authors maintain that such an infrastructure must be developed for the new digital economy and society, one that provides trust and confidence for all those who operate in or are affected by it.
INDIA: Technical and Entrepreneurial Research Information System: An Applied e-Model for Sustainable Entrepreneurship Development
(By Dhrupad Mathur)
http://www.arraydev.com/commerce/JIBC/2005-08/DhrupadMathur.asp
This article stresses on the need for an e-application like Technical and Entrepreneurial Research Information System (TERIS), which enables interaction among academia, industry and various agencies related to researchers for sustainable entrepreneurship development. The functional details of the model are also discussed. This article is based on inputs with reference to the state of Rajasthan. However, the model can very well be replicated elsewhere.
INDIA: A Framework for Evaluating e-Business Models and Productivity Analysis for Banking Sector in India
(BY N.V.M. Rao, Prakash Singh ans Neeru Maheshwari)
http://www.arraydev.com/commerce/JIBC/2005-08/maheshwari.htm
This study is an effort to draw together some of the e-Business models and real-life experiments that has been circling around the e-business models. To study the sweeping changes brought about by e-initiative measures in the banking sector some banks were chosen, from public sector like SBI, BOB etc and from private sector like ICICI, HDFC etc.
MALAYSIA: Do Foreign Banks Lead in Internet Banking Services
(By Boon Han Yeap and Kooi Guan Cheah)
http://www.arraydev.com/commerce/JIBC/2005-08/JIBC_yeap%20&%20cheah.asp
Internet banking has been increasingly used as a delivery channel in retail consumer banking. As far as the provision of internet banking services in developing countries is concerned, foreign banks definitely enjoy distinct advantages over domestic banks due to their experiences in other, more advanced financial markets. This paper reports a study that examined the levels of retail internet banking services provided by foreign and domestic commercial banks in Malaysia over a period of two years. The study found that while foreign banks are marginally more sophisticated at information provision level, domestic banks offer a significantly higher level of transactional facilities in both years.
MALYASIA: Marketing Mix: A Review of "P"
(By Chai Lee Goi)
http://www.arraydev.com/commerce/JIBC/2005-08/goi.HTM
There has been a lot of debate in identifying the list of marketing mix elements. The traditional marketing mix by McCarthy (1964) has regrouped Borden's (1965) 12 elements and has comprised to four elements of product, price, promotion and place. A number of researchers have additionally suggested adding people, process and physical evidence decisions (Booms and Bitner, 1981; Fifield and Gilligan, 1996). The other suggested Ps are personnel, physical assets and procedures (Lovelock, 1996; Goldsmith, 1999); personalization (Goldsmith, 1999); publications (Melewar and Saunders, 2000); partnerships (Reppel, 2003); premium price, preference of company or product, portion of overall customer budget and permanence of overall relationship longevity (Arussy, 2005); and 2P+2C+3S formula (Otlacan, 2005), therefore personalisation, privacy, customer Service, community, site, security and sales promotion.
QATAR: E-Banking Service Quality: Gaps in the Qatari Banking Industry
(By Norizan M. Kassim)
http://www.arraydev.com/commerce/JIBC/2005-08/KassimTry.asp
Financial liberalization and technology revolution have allowed the developments of new and more efficient delivery and processing channels as well as more innovative products and services in banking industry. Banking institutions are facing competition not only from each other but also from non-bank financial intermediaries as well as from alternative sources of financing, such as the capital markets. Another strategic challenge facing banking institutions today is the growing and changing needs and expectations of consumers in tandem with increased education levels and growing wealth. Consumers are becoming increasingly discerning and have become more involved in their financial decisions. For this reason, they are demanding a broader range of products and services at more competitive prices through more efficient and convenient channels. This study investigates the discrepancy between customer's expectation and perception towards the e-banking services.
USA/SINGAPORE: A Case Study of electronic Bill Presentment and Payment (EBPP) Integration Using the CON Mediation Technology
(By Sajindra Jayasena and Stephane Bressan)
http://arraydev.com/commerce/JIBC/2005-08/Jayasema.asp
By its very nature, financial information, like the money that it represents, changes hands. Therefore the interoperation of financial information systems is the cornerstone of the financial services they support. In this paper we illustrate the nature of the problem in the Electronic Bill Presentment and Payment industry. In particular, we describe and analyze the difficulty of the integration of services using four different formats: IFX, OFX and SWIFT standards, and an example proprietary format. We then propose an improved way to accomplish this integration using the Context Interchange (COIN) framework.
Administrative Notice
Journal of Internet Banking and Commerce
JIBC is a leading edge publication that informs banking and electronic commerce professionals and executives on principal developments, benchmark practices, and future trends in the Internet-based marketing practices of governments and industry. This free online interactive journal is a way to keep in touch, to share information, and to establish business contacts (networking) for worldwide professionals that specialize in electronic commerce, governance and banking
solutions.
In JIBC you will find informed discussion of the latest internet-based banking and electronic trends and practices from around the world. Our priority is quality, not quantity. We want to maintain JIBC as a service that provides substantial information and an effective forum for your articles, your letters, your insights and ideas.
JIBC invites banking and electronic commerce professionals, academicians and publishers to submit important announcements, original articles, guest columns and significant feature presentations. We also welcome surveys, book reviews and letters to the Editor. Technical discussions in highly specialized areas of expertise will be kept to an absolute minimum.
JIBC is formally issued three to four times a year when an email summary of current articles is distributed to subscribers. The full text of current articles is posted on the JIBC Web site at
http://www.ARRAYdev.com/commerce/JIBC/current.asp.
The publication is complemented by the Compendium of Internet Banking and Commerce Initiatives at:
http://www.arraydev.com/frames/f-guest_comp.htm.
We invite readers to provide brief descriptions of products, books, and services that they think others will find interesting.
The Journal of Internet Banking and Commerce (JIBC) is provided as a service by ARRAY Development based in Ottawa, Canada. Views expressed are those of the authors and are not necessarily shared by ARRAY Development. Firms or individuals interested in sharing sponsorship of this project may contact array (at) ARRAYdev.com.
The JIBC Web Archive
http://www.arraydev.com/commerce/jibc/articles.htm contains all articles published to date.
You can reach the Editor-in-Chief Nikhil Agarwal with any questions or comments by email at:
nikhil.jibc (at) gmail.com
Publisher Nahum Goldmann is at:
Nahum.Goldmann (at) ARRAYdev.com.
Editorial Board
Publisher and Member of the Editorial Board: Nahum Goldmann
Chief Editor: Nikhil Agarwal
Founding Chief Editor Emeritus and Member of the Editorial Board: Gord Jenkins
Assistant Editor: Xin "Robert" Luo
Mailing List Managing Editor: Anne-Marie Jennings
Contributing Editors
U.K. Contributing Editor: David G.W.Birch
Australia Contributing Editor: Dale Pinto
Japan Contributing Editor: Carin Holroyd
Nordic Countries Contributing Editor: Minna Mattila
Legal Contributing Editor: Edwin Jacobs
Middle East Contributing Editor: Raed Awamleh
Africa Contributing Editor: Alemayehu Molla
France Contributing Editor: Jean-Michel Sahut
Please send any questions related to maintenance of this Web site to:
array (at) ARRAYdev.com
Information and subscription for JIBC mailing list is available via:
http://groups.yahoo.com/group/JIBC/
August 31, 2005
The HR Malaise in Britain - 25% of CVs are fiction
As discussed here a while back in depth, there is an increasing Human Resources problem in some countries. Here's actual testing of the scope of the issue whereby job employers ask for people to lie to them in the interview, and jobseekers happily oblige:
One CV in four is a work of fictionBy Sarah Womack, Social Affairs Correspondent (Filed: 19/08/2005)
One in four people lies on their CV, says a study that partly blames the "laxity" of employers.
The average jobseeker tells three lies but some employees admitted making up more than half their career history.
A report this month from The Chartered Institute of Personnel and Development highlights the problem. It says nearly a quarter of companies admitted not always taking up candidates' references and a similar percentage routinely failed to check absenteeism records or qualifications.
Example snipped...The institute said that the fact that a rising number of public sector staff lie about
qualifications or give false references was a problem not just for health services and charities, where staff could be working with vulnerable adults or children, but many public services.The institute said a quarter of employers surveyed ''had to withdraw at least one job offer. Others discover too late that they have employed a liar who is not competent to do the job."
Research by Mori in 2001 showed that 7.5 million of Britain's 25.3 million workers had misled potential employers. The figure covered all ages and management levels.
The institute puts the cost to employers at £1 billion.
© Copyright of Telegraph Group Limited 2005.
If it found 25% of the workers admitted to making material misrepresentations, that shows it is not an abnormality, rather lying to get a job is normal. Certainly I'd expect similar results in computing and banking (private) sectors, and before you get too smug over the pond, I'd say if anything the problem is worse in the US of A.
There is no point in commenting further than to point to this earlier essay: Lies, Uncertainty and Job Interviews. I wonder if it had any effect?
July 16, 2005
"Acceptable Risk" - a Euphemism for Selling Fraud?
The "acceptable risk" concept [writes guest financial cryptographer Ed Gerck] that appears in recent threads has been for a long time a euphemism for that business model that shifts the burden of fraud to the customer.
The dirty little secret of the credit card industry is that they are very happy with 10% of credit card fraud, over the Internet or not.
In fact, if they would reduce fraud to zero today, their revenue would decrease as well as their profits. So, there is really no incentive to reduce fraud. On the contrary, keeping the status quo is just fine.
This is so because of insurance -- up to a certain level, which is well within the operational boundaries of course, a fraudulent transaction does not go unpaid through VISA, American Express or Mastercard servers. The transaction is fully paid, with its insurance cost paid by the merchant and, ultimately, by the customer.
Thus, the credit card industry has successfully turned fraud into a sale. This is the same attitude reported to me by a car manufacturer representative when I was talking to him about simple techniques to reduce car theft -- to which he said: "A car stolen is a car sold." In fact, a car stolen will need replacement that will be provided by insurance or by the customer working again to buy another car. While the stolen car continues to generate revenue for the manufacturer in service and parts.
Whenever we see continued fraud, we should be certain: the defrauded is profiting from it. Because no company will accept a continued loss without doing anything to reduce it. Arguments such as "we don't want to reduce the fraud level because it would cost more to reduce the fraud than the fraud costs" are just a marketing way to say that a fraud has become a sale.
That's because fraud is an hemorrhage that adds up, while efforts to fix it -- if done correctly -- are mostly an up front cost that is incurred only once. So, to accept fraud debits is to accept that there is also a credit that continuously compensates the debit. Which credit ultimately flows from the customer -- just like in car theft.
What is to blame? Not only the twisted ethics behind this attitude but also that traditional security school of thought which focus on risk, surveillance and insurance as the solution to security problems.
There is no consideration of what trust really would mean in terms of bits and machines[*], no consideration that the insurance model of security cannot scale in Internet volumes and cannot even be ethically justifiable.
"A fraud is a sale" is the only outcome possible from using such security school of thought. Also sometimes referred to as "acceptable risk" -- acceptable indeed, because it is paid for.
Cheers,
Ed Gerck
[*] Unless the concept of trust in communication systems is defined in terms of bits and machines, while also making sense for humans, it really cannot be applied to e-commerce. And there are some who use trust as a synonym for authorization. This may work in a network, where a trusted user is a user authorized by management to use some resources. But it does not work across trust boundaries, or in the Internet, with no common reporting point possible.
June 26, 2005
Nick Szabo - Scarce Objects
Nick Szabo is one of the few people who can integrate contracts into financial cryptograpy. His work with smart contracts echoes around the net, and he last year he gave the keynote presentation at the Workshop on Electronic Contracts. In this paper he seeks to integrate scarcity and property constructs with the object oriented model of programming.
Scarce objects, a.k.a. conserved objects, provide a user and programmer friendly metaphor for distributed objects interacting across trust boundaries. (To simplify the language, I will use the present tense to describe architectures and hypothetical software). Scarce objects also give us the ability to translate user preferences into sophisticated contracts, via the market translator described below. These innovations will enable us for the first time to break through the mental transaction cost barrier to micropayments and a micromarket economy.
A scarce object is a software object (or one of its methods) which uses a finite and excludable resource -- be it disk space, network bandwidth, a costly information source such as a trade secret or a minimally delayed stock quotes, or a wide variety of other scarce resources used by online applications. Scarce objects constrain remote callers to invoke methods in ways that use only certain amounts of the resources and do not divulge the trade secrets. Furthermore, scarce object wrappers form the basis for an online economy of scarce objects that makes efficient use of the underlying scarce resources.
Scarce objects are also a new security model. No security model to date has been widely used for distributing objects across trust boundaries. This is due to their obscure consequences, their origins in single-TCB computing, or both. The security of scarce objects is much more readily understood, since it is based on duplicating in computational objects the essential security features of physical objects. This architecture is "affordable" in Donald Norman's sense, since human brains are designed to reason in much more sophisticated ways about physical objects than about computational objects. It is thus also "affordable" in terms of mental transaction costs, which are the main barrier to sophisticated small-scale commerce on the Net. Finally, it will solve for the first time denial of service attacks, at all layers above the primitive scarce object implementation.
Comments below please!
June 20, 2005
US Banks lobby to enter Real Estate - Hubris or an Invitation to end the Franchise?
In a stunning display of hubris, the American Banking Association is lobbying to let banks enter into the real estate business.
Quick refresher: banking is the business of borrowing and lending money to and from the public. Unlike almost all other goods, loans can go south due to circumstances beyond the control of the parties, to whit the economy. For this reason banks are regulated in a special way, because, so the theory goes, if they are not regulated they will be tempted to ignore the future dangers of an unbalanced balance sheet in pursuit of short term profits. In banking there are always short term profits there for the taking...
Banks therefore are granted a franchise. In economic terms, a subsidy. Banks are protected from competitors so as to make the regulation easier. This also makes it easier to make profits, as there are no nasty little upstarts coming to cherry pick and make trouble. But such a subsidy comes with limits - banks are supposed to only be in the business of banking.
Which then turns on the definition of banking. As I suggested, banking is the borrowing of demand deposits and lending them out as loans to the public. If it is not the public, then it is a building society, S&L, credit association or the like - the members only borrow and lend to themselves, so that's not banking, nor is it so deserving of special treatment. If they are not taking deposits or not making loans, then they are not entering the special risk scenario where the term nature of the deposit does not match the term nature of the loan. That is, the bank borrows funds on demand terms and loans them out on long terms. Clearly a mismatch there, and that's part of the rationale for the regulation and subsidy.
The problem with this is that banks then grow big and powerful within their communities and also come to know a little about lots of things. They have dramatic power over their community in that they have access to the balance sheets of their borrowers. Where does this lead? Of course it leads to cherry picking.
Banks know that real estate can be profitable. They figure that with their local knowledge they could swipe those lucrative percentage fees - generally from 5 to 10% of the house sale price around the world. A very rich, luscious juicy cherry, that.
Problem is, it flies in the face of the subsidy. And in order to get around that, enter 'definition of banking, number two!' In many countries, the practical, de facto and sometimes legal definition of banking is not as I described it above, but it is this: Banking is what banks do. And, banks are those that do banking.
Whoops! A circular definition, which means there is no definition. And this is what is happening in the US banking structure at the moment:
"Duke said that the Realtor's insistence that Congress block banks from entering the real estate market would reverse the progress made by the 1999 Gramm- Leach-Bliley Act. The act adopted a process where the Federal Reserve and Treasury Department would determine which activities are financial in nature and therefore allowable for banks to pursue."
In a sentence, the Fed and the Treasury determine banking as "activities [that] are financial in nature!" Which of course is everything, pretty much, as anything with a price sticker is financial at some level.
As an invitation to drop the banking subsidy and give all businesses the right to enter into banking, it doesn't get much clearer than that. If the subsidy is to have any meaning, it must be tightly curtailed. If not, then it should be dopped as a matter of public policy. You simply don't let one group do A & B, but another group only do B.
It may seem even odder, but this is indeed the way things are going in the US. Several institutions can enter parts of banking already:
"Duke said that combining real estate brokerage and banking services is not a new concept in the marketplace, citing that real estate firms, insurance companies, and securities firms already have the authority to do so. She added that state-chartered banks in more than half the states also can offer real estate services."
And the theory of banking - especially that of Free Banking - decidedly supports the notion that there is no economic rationale for the subsidy, only the combined weight of historical mistakes.
Maybe, then, this is what we are seeing: the long term dismantling of US banking as a franchise.
June 16, 2005
Miller & Shapiro on Hayek's market - explaining object orientations
I was struck how the Introduction to Miller & Shapiro's new paper on concurrency control sought to integrate economics and programming. Here's the Introduction, stolen in fine Hayekian tradition for your reading pleasure. The paper is for full publication in proceedings of Trustworthy Global Computing (so it will miss out on the bona fide FC++ advantage) but I couldn't help from letting slip this teaser!
The fundamental constraint we face as programmers is complexity. It might seem that the systems we can successfully create would be limited to those we can understand. Instead, every day, massive numbers of programmers successfully contribute code towards working systems too complex for anyone to understand as a whole. Instead, we make use of mechanisms of abstraction and modularity to construct systems whose components we can understand piecemeal, and whose compositions we can again understand without fully understanding the components being composed.
To understand these twin problems, of separating components and of composing them, we draw on Friedrich Hayek's examination of how markets address the twin problems of plan coordination: bringing about the cooperative alignment of separately conceived plans, while simultaneously avoiding disruptive plan interference [Hayek45]. His explanation of the need for property rights parallels the rationale for encapsulation in object-oriented systems: to provide a domain (an object's encapsulation boundary) in which an agent (the object) can execute plans (the object's methods) that use resources (the object's private state), where the proper functioning of these plans depends on these resources not being used simultaneously by conflicting plans. By dividing up the resources of society (the state of a computational system) into separately owned chunks (private object states), we enable a massive number of plans to make use of a massive number of resources without needing to resolve a massive number of conflicting assumptions.But a single object cannot do much by itself. Instead, both objects and markets use abstraction to compose plans together into vast cooperative networks, such as subcontracting graphs, where one agent, employing only its local knowledge, will subcontract out subtasks to others, often in great ignorance of how each subtask will be carried out [Lachmann, Lavoie, Tulloh02].
"Programmers are not to be measured by their ingenuity and their logic but by the completeness of their case analysis. Alan Perlis"The problem Hayek was concerned with, how humans coordinate their plans with each other, certainly has many differences from the world of programming. For purposes of this paper, the most interesting difference is that, in the human world, the intelligence of the entity who formulates a plan is comparable to the entity who executes the plan. Therefore, the plan doesn't have to prepare for every possible contingency. If something unusual happens, you'll probably be better able to figure out what to do then anyway. By contrast, when writing a program, we must express a plan that can deal with all possible relevant contingencies. Even under sequential and benign conditions, the resulting case analysis can be quite painful. As we extend our reach into concurrency, distribution, and mutual suspicion, each of these dimensions threatens an explosion of new cases. To succeed at all three simultaneously, we must find ways to reduce the number of additional cases we need to worry about.
Mark later pointed out that he and Bill Tulloh have an entire paper on the Austrian market process, Institutions as Abstraction Boundaries.
June 01, 2005
Software Licensing and the Know-how to Issue
Software charging for big ticket sellers is getting more complex again, as dual cores from AMD and Intel start to invade the small end. Oracle, which made billions charging on the muscle power of CPUs, will have to do something, and we've by now all seen IBM's adverts on TV suggesting "on demand" with its concommitant charging suggestion: You demand, we charge.
I've done a lot of thinking over the years about how to licence big ticket items like issuance software. In practice it is very difficult, as the only revenue model that makes sense for the supplier is for large up front licence fees to recover large up front capital and sunk costs. But for the demander (issuer and user of the software) the only model that makes sense is to pay later, when the revenues start flowing...
Issuance software has all the hallmarks of an inefficient market and I don't think there has been successful case of issuance licencing yet, as those two "sensible" options do not leave any room for agreement. This may be rational but it's very frustrating. Time and again, we see the situation of people wanting to get into the issuance market who think they can produce the software themselves for a cheaper price. And they always end up spending more and getting a lesser quality product.
In practice what we (Systemics) have been doing is this: running the software ourselves as "operator", and charging operating costs, with some future licencing or transaction flow revenues. Yet, the deal for future revenues is always based on a promise and a prayer, which is already asymmetrical given that most startups do no more than start up. (And it isn't just me bemoaning here - if you look back through history there are literally hundreds of companies that tried to build value issuance and sell it.)
Which leads to the freeware model. In the freeware world, big ticket items are given away and money is made on the consulting. This has worked relatively well in some areas, but doesn't work so well in issuance. I'm unclear of the full reason why open source software doesn't work in issuance, but I think it is mostly the complexity, the sort of complexity I wrote about in FC7. It's not that the software can't capture that complexity but that the financial cryptography business often finds itself so squeezed for management complexity that partnering with a strong software supplier are beyond capabilities.
What will potentially help is p2p issuance. That is, "everyone an issuer." We've always known this model existed even as far back as 1995, but never really considered it seriously because too many questions arose. Little things like how we teach grandma to sign a digital contract. We've now done enough experiments in-house to confirm that the corporate internal issue and the individual issue are workable, sustainable economic models but we have to get other companies and individuals to do that and for the most part they still don't do anything they don't understand.
I'm guessing the way forward here is to turn client software into issuance software. This brings up a whole host of issues in financial cryptographic architecture. For a start it can never seriously scale simply because people do silly things like turn off their laptops at night.
But, more and more, the barriers to issuance and financial cryptography in general I believe are spreading the knowledge, not the tools and tech. Every year our tools and tech get better; but every year our real barriers seem the same - how to get users and customers to make their first tentative issue of a currency of value. Oh, and how to make money so as to keep us all alive, which was the starting point on this long rant of liberal licence.
A couple of footnotes: In a similar thread over at PGP Inc, Will Price reveals how they've managed to get out of the legacy freeware version trap:
"When the 30 Day Trial version of PGP Desktop Home expires, it reverts to a set of functionality comparable to what used to be known as Freeware, and said functionality remains available indefinitely -- under the same license conditions as Freeware used to be under."
Nice one. That works for client software, not for server software.
Here's a further article on how the big companies are also working out how big ticket software isn't the way to go:
May 04, 2005
Lies, Uncertainty and Job Interviews
I was recently chatting to a HR ("human resources") person who complained that "the banks are having trouble getting good people." This struck me as odd, as I've seen plenty of evidence that they happily reject good people (and I'm not just talking about my own experiences). Having mused on it, I think one of the problems is that the HR process is riddled with lying. Check out what the IHT reports on Cleo reporting on how to lie to get a job.
This would be funny, except it's not. Anecdotes I've heard indicate that the rate of lying in job interviews and on CVs is higher than it should be. I won't suggest my numbers ... partly because it is unscientific research, and partly because that will just give people an excuse to disbelieve. Baxter, the guy quoted in the article, does say numbers: "I would say 10 percent to 15 percent have issues that require attention," and that 3 percent to 4 percent had "serious discrepancies" like falsely reporting university attendance. That's just the ones he picked up on.
Why is lying so prevalent? And another question - has it always been this way? I have a rosey perception that it wasn't like this when I was young. Is that my own factors? Is that instead my own naivete?
Here's what I have picked up over time. Firstly, all cultures lie. People who say they don't lie are lying. (Try teaching that one to your children.) In fact, one of the research topics that academics have conducted over the last decade or two is to try and map out how different cultures develop shared but buried understandings of when it is ok to lie.
In the anglo culture this is sometimes called the white lie. As examples of the white lie, it is ok for the husband to lie about his wife's weight, or that gawd-awful dress that makes her look like a matron, if she lies about how he's good enough in bed.
Cultures differ. In Spain for example, it is ok to lie about an appointment. This is because it is necessary, indeed obligatory to insist that you take someone for a drink or you offer them a meal; the acceptable and polite way out of this is to say you have another appointment already, so you are apparently trapped in breaking one committment for another. Another aspect of Spanish politeness is that asking for directions or help is fraught with helpful lies.
In America it is ok to lie if it is about some marketing issue, which includes themselves. That is, the listener shouldn't be so stupid as to believe marketing, and if they do, then it's morally right to part their money from them. One non-american put it like this "Americans lie when it comes to admitting shortcomings or weaknesses. They will rarely admit that they do not know, they will come up with an answer, no matter what."
Americans are always marketing themselves, as distinct to the Spanish who are afraid of disappointing you. To Americans, a question must be answered, no matter what. A product must be marketed, and if there isn't one on the table, then put yourself there. America as a country now has an endemic problem with lying, as it is now at the point where government is assumed to be lying because their job is to sell the program, and that requires marketing to the people, right? Here's a Wired article where the government is knowingly lying about some security stuff it is trying to sell, even though everyone knows it is lying. Now, the gravity of this might not be apparent until one considers that America again unique amongst peers has a perverse dependency on honesty.
Apparently it remains impolite in all societies to suggest that someone is lying. Which of course suggests the obvious strategy - lie, and dare people to call you on it. Here's another one: security people lie when they say something is secure. Aside from the basic characteristic of security being a relative term not an absolute (so the statement makes no sense) most security people do not carry out the proper analysis to ground any statement in security, so a short cut is taken, and we hope that it works out. And nobody notices before we've changed jobs.
(Which diverts us briefly back to financial cryptography. In our art we make people part of the process, and issuers as parties to contracts, escrow partners as protectors of value, and techies as operators of systems are all in a position to lie. What leads them to lie and what we can do to make it very hard to lie are things we have to understand in order to protect value. We could just assume honesty like other systems, but that's just naive. That's why you read a lot of postings here about various new and interesting frauds: how and why people lie to commit frauds is part of the governance layer, it is part of the job.)
For my own culture, I cannot answer how they/we lie; believe me as you will! I'm interested in hearing how you all perceive how other cultures lie, my suspicion is that only the outsider can work it out. I really only became interested in lying when I'd hit my third culture. The discovery of new forms of lying is by contrast and comparison, then, and sometimes by an awful sinking feeling you get when you discover some totally new experience that catches you out completely.
For the British, it is ok to "make something up" if you don't actually know how you are going to do it anyway. So for example, some event in the future: I'll pick you up in my car next tuesday ... is a fine thing to say even if it never happens. Even if you would not promise it anyway, it is ok to say it, because it is outside the time horizen of reliability.
Back to the market for employment, which Spence identified as being peculiarly inefficient. In Britain, lying in job interviews is called "blagging" and is quite acceptable. Indeed in some cases an agent who puts a candidate forward will instruct the candidate to lie. The dividing line seems to be as thin as whether they can get away with it, for example on a CV or on a written test.
Which brings me around to the original question of why exactly is lying so much a part of the job process? I think it comes down to a failure of HR in general and a failure of requirements in particular. The experiences I have heard of have shown an obsessive tendency for employers in some cultures to look for perfection in candidates. This means that candidates are rejected when some answer isn't to their liking; this can be a wide range of perceptional things such as "would not fit in" or it can be simply a narrow failure to answer a particular question. No matter, it seems that if you do not get everything right, you are 'not good enough'. So lie on your CV, or your written test, or blag your way through the question, because any failure means you are dropped whereas a successful lie gets you through.
This desire for perfection is pervasive. In fact, it's positively correlated with the amount of effort put in by employers as those that conduct many interviews commonly give every interviewer the ability to say no! This of course sends the wrong signal; if you don't know something, there is no point in admitting it, and you are better off "blagging" your way through it so as to get to the next interview. And now we see why this is a failure in HR: if lying is rewarded, your company will end up full of liars. And the harder you try in your HR process, the more you are assuring that only the better quality of liar will be able to get through!
What is the underlying failure here? To an engineer this is an easy one to explain: uncertainty is what we do, and the employer should learn to appreciate it and not run from it. Seeking for perfection is perverse, it means we are likely to reject fresh approaches and end up stifled in group-think, assuming that we managed to avoid the liars. It also means that when the interviewer is limited in some way, those very limitations are imposed on the candidate, and this then gives us a feedback cycle similar to the one Spence pointed at in his seminal "Job Market Signaling" paper - except that this time even though the characteristic reaches equilibrium, neither employee nor employer will recognise the signal.
Most people will be offended by this, because implicit in today's essay is that you lie, or that your company is full of liars. Consider it more then as rejecting diversity, if looking for a politer label. (Or, more simply, assume that I'm lying and you can ignore everything written here. For those who are curious on that point, we'll leave it to the reader to decide where the lies are herein.)
Regardless of any particular lies either here or in your next interview, it should be as much a part of the employment process to discover and revel in uncertainty as any other quality, and any process that tries to avoid it is doomed. Why perfection always results in disaster and uncertainty is the foundation of survival will have to wait for another day.
Addendum: It seems I was right: 25% of CVs are Fiction!.
May 03, 2005
Security as a "Consumer Choice" model or as a sales (SANS) model?
In thoughts about how to do Internet security - something the world fails at dismally for the present time - it is sometimes suggested that a "consumer choice" model would work. This model sets up independent non-profit organisations that conduct unbiased reports on products. They promulgate strict rules designed to ensure their independence, such as the separation of advertising revenue or even not taking money for advertising at all. (Will's history lesson)
By way of example, in today's Lighthouse, The Independent Institute suggests that the american Food and Drug Administration ("FDA") should be replaced with this model:
"If aspirin were invented today, the U.S. Food and Drug Administration might not approve it. We should keep this in mind when thinking about Vioxx, Bextra and other pain-relief drugs that have recently been taken off the market. This is not to say that the new pharmaceuticals are “safe,” but rather that all pharmaceuticals involve tradeoffs. The real question is: who is to make those tradeoffs, patients and doctors or the FDA?"
There are already plenty of security groups and more pop up every year, but they are generally platforms for sales. SANS for instance just released an update for its top 20 threats (but still doesn't mention phishing as a threat, confirming its status as a dinosaur).
From historical pre-Internet times, the list divides the threats into a top 10 list for Microsoft and a top 10 for Unix. Reading the Microsoft list gives the overwhelming impression that it is sanitised and softened. The clue is the use of brand - when being critical, the wrong terminology is used. So, we find that "Windows" has a bug, which aside from confusing me as to whether my X Windows or my KDE windows or Mac's windows have an issue, avoids the obviously harsher connotations of the correct brand of "Microsoft Windows."
Why? Fear of offending companies. SANS is really a seller of conferences, as one can see from the front page, it is not an independent security organisation. And conferences are attended by companies, not by individuals. Better not offend a very large company then.
Which brings up the problem with the "consumer choice" model - what is the revenue model? How are all these reports to be funded? Thinking about the old model, magazine sales created the revenue, but that doesn't work today because the net operates at zero marginal cost.
So maybe we need to turn to net models of cooperation, and create an open source-like culture of security reports? Would it be possible to craft a set of criteria for security reports where the product was covered by Creative Commons licence, any group could create one and a few volunteers sit in the middle and mentor and collate?
An intriguing thought. People are doing the work anyway; why not publish it and share the benefit? Throw in a reputation system to stop Microsoft from inserting their own "SANS report" and we're away. Would it work? I don't know, but it's at least worth a second cup of coffee.
Addendum: the comments below remind me of Will's history lesson. Well worth reviewing as it sets the scene for the wider discussion.
#2 Whoops, spoke to soon. The press release from SANS actually uses the proper brand names and gives Microsoft a bad rep. Good one!
May 01, 2005
Tracking Reputation - CACert
I wrote before on how blogshares is one way to do the meta-blog tracking; a mark of a successful innovation is the springing up of "institutions" that provide cross-society services. Blogs have crossed that bridge and are now serious stuff, then. Adam, who's upset at mindless trackbacks consuming his time, points at Technorati as another version. (Also, Alacrity.)
Before I get to today's main contender, CACert, let me declare my skepticism up front. I have to say I have low hopes for some of these institutions, including Technorati.
I'd spent 10 minutes browsing, and still have little clue what it's about. Apparently it offers more of the same, ability to have a photo, more links, more ho hum. Another thing that is pretty annoying is their login procedure that insists on too many details ("what country is your blog in?" who the hell cares? what is this perverse obsession with national stereotypes?) and also asks for your login to the blog itself. What, are you nuts? Or just another smart bunch of spammers harvesting the this year's growth of veggie matter?
Reputation systems generally don't work. The reason for this is complex; and I'm not sure whether I am able to voice why it is that the "that'll never work" thing pops up so frequently. It would require a full essay I suppose. But here are some reasons.
The big reason is of course that they all require attention. This means cost. So there has to be a benefit, and a significant one at that. To pay for the cost - simple economics, that.
Yet, few of them promise much in the way of benefit. Most of them are way too small in mind to suggest why you would bother. Consider LinkedIn, which is a rather successful network where people run around and link each other in. Having linked people in you are now in contact with everyone. You can send messages. But, you can send messages anyway; all this does is allow you to search their database. If you get a hit you can send a message, but we can already do that other ways. So I conclude that the real benefit accrues to the company running it which has now amassed a huge database which it now sells for the employment purposes.
Knowing that LinkedIn is about employment market rather than your relationship needs is a thought that is obvious if you are aware of Granovetter's theory of weak links. So we have another reason why reputation systems don't work - if they are just oriented to more and more links, then they raise more and more pointless costs (unless you are after a job), as indicated by Alacrity. Perhaps the principle should be that additional links relate clearly to additional benefit.
Then, the metrics are almost always flawed. Sometimes they are completely flawed, and other times they are just so incomplete as to be laughable. I recall trying out Advogato and being asked to rate myself; so I stuck myself in the middle. Now, if it was a true reputation system, it would rate me up or down. So when I checked other people I knew, they had rated themselves at the top; which then had perpetuated and been accepted by all the other people who'd simply agreed! In one easy step, Advogato had reduced itself to a self-aggrandisation scheme in the most american of ways. IOW, useless for real tests of reputation (a complaint that has also been levelled against eBay's system). Admittedly, this is to ignore other benefits that might have been there.
To bring us to today's topic, one reputation system starting to make a mark is CACert. Now for a start this promises a benefit: free PKI certificates. They are not really free, as the time and hassle factor of PKI (more costly than any other Internet operation known to mankind!) is still there. But they are free of monetary cost. Which is quite welcome as this meant I was able to create several over the weekend and simply discard the ones that didn't work. Security how it should be - aligned to *my* needs!
(And yes, FC is now more secure thanks to CACert! switch to https and simply accept the cert 'Forever' and you'll be protected from eavesdroppers.)
The metrics at CACert are interesting. They've taken the "strong government Identity" route which is bound to make some people nervous. Since when does the government have a monopoly in good identity? As it happens, in some countries they do have good strong systems - Id cards. So as a stab at a basis they are a starting point, although if you've lived in places like I've lived in, you would know not to trust anything more than a beer's worth on a government issued Id.
CACert also has an issue with privacy and databases that I haven't quite worked out. I really couldn't give two hoots what happens to their root key, but if their identity database gets hacked, I'm looking for my shotgun; the fact that they store all this info, and have good systems in place to make it reliable means that they have to be a single point of failure in the future.
But what they do have funnily enough far and away exceeds the practices of most other CAs. This is simply because they use a points system that is based on personal member checking. (I haven't tried it out as yet, but because I've been checked out by two members, I can now start checking out others. I'll report back as things develop.)
Which means we now have a web of trust based on 'strongish Id'. This is one of those puzzle pieces that we've been waiting to arise, and it now has - OpenPGP's web of trust didn't do it because it was deliberately not mandated to use 'strong Id'. This leads to two things to look out for in the future: what are the ways in which this can be utilised (other than the free certs) and, what are the ways this web of trust can be attacked?
April 17, 2005
First Impressions on reading Spence on Signaling
I just this morning finished Michael Spence's seminal 1973 article entitled "Job Market Signaling [1]." I'm still musing on it, as it has a lot to chew through. Here are some early comments.
Firstly, Spence introduced the term signaling, but he explicitly didn't define it [2]. I say this to lead into some later remarks. His view was that signaling was something that was undertaken only infrequently; he was specifically looking at the case where the signaler did not acquire the ability to signal well.
Next. The asymmetric information school - which may or may not claim to incorporate signaling - assumes that there is an asymmetry of information, and thus the task is to incentivise the sharing of that information; to whit, reduce the asymmetry and thus make the allocative decision more efficient.
That's not what Spence and Job market signaling is about. Spence explicitly accepts that the market in jobs is symmetric and insufficient; something I had noticed and developed more strongly in my (draft) market for silver bullets. That is, the task here is not to get the individual to reveal information that he holds to his advantage, but to predict something that is otherwise only found out at extreme cost (risk investment in employment decisions).
Which means, amongst other things, that I now have to rewrite my silver bullets paper to take into account that I'm 32 years behind Spence on this point. Lucky it wasn't 33 years, is all I can say. Also luckily for me, his market in education mirrors my market in silver bullets, which leads to the next point: The equilibria in this market arises without reference to the original import of the signal. My model was based on herding, his is based on confirmatory feedback (perhaps like Senge or even Boyd) [3]. The two sit side by side, which means I can build on his and incorporate the two together. I still have a chance of a paper, then!
One point is widely understood; the signal must be expensive for one group and cheap for another. If the costs of acquiring the education are the same for all, there is no value in the signal. This might mean that there is a desire to make sure this is not the case; but this search for apparent differentiation is countered by the feedback equilibria being reached without resort as above.
Finally, Spence actually suggests that markets based on signaling are inefficient, and the signals themselves are not especially correlated with productivity. If his implicit unwritten definition is accepted, signaling is not a good to be pursued, rather a bad to be avoided. That is, the question for the job market, and the education market, is how to avoid the product of education being reduced to the 'bad' of a signal.
This was a surprise for me. I had simply assumed that signals were positive things. Perhaps it is the literature that suggests this, or perhaps it is the crossover to Akerlof, where the lemons market signals positively. This underscores the dictum of going back to the source. Secondary references such as Wikipedia and the Nobel site just don't bring this out.
To underscore this, the paper shows that in some equilibria, it is reasonable to postulate that all parties are strictly worse off in the presence of stable signaling. Further, indices - those signals that cannot be changed and are assumed a priori irrelevant - can create the same equilibria.
Now, that makes sense. That's precisely what I've suggested with some of the much vaunted products that masquerade as security, which is what got us started on this whole signaling kick in the first place. And, if we can recognise that the market for security is one of signaling, and signals are an inferior allocative mechanism, then at least we are some way along in finding ways to deal with that.
[1] Michael Spence, "Job Market Signalling," Quarterly Journal of Economics, v 87(3), 355-374.
[2] It turns out that there are two spellings for signalling or signaling. I haven't as yet worked out the distinction, but I suspect another American English difference here. Here I'll try out his spelling rather than the English I was brough up with.
[3] Spence refers to Myrdal's vicious cycles, which Google puts at a 1957 paper.
March 28, 2005
IP versus Economics - the Google Trademarks disputes
Googles sales of other people's trademarks for advertising purposes gets right to the core of Intelletual Property. As the economics of coordination shifts, some age-old institutions such as intellectual property devices (trademarks, patents, copyright) discover they are too clunky to ease commerce in the new world. Whether they migrate, adjust, survive or die won't be seen for a few years yet, but here's an interesting article that lays out the fault lines in the war of IP versus the Internet and economics.
Google ensnared in a war of words
By Doreen Carvajal International Herald Tribune
Monday, March 28, 2005
PARIS Fabrice Dariot's travel agency, Bourse des Vols, boasts a terrace lined with potted plants and sweeping views of 17th-century apartments in the center of the city.
The compact fifth-floor office is an unlikely front line for a battle of words with the online search engine Google - or "Omnigoogle," as some French critics scornfully call the giant company.
Dariot, a mathematician turned Internet entrepreneur, is an even more unlikely standard-bearer for a series of proliferating lawsuits and legal disputes that challenge Google's sacrosanct business routines.
"Google is a giant, but they cannot dictate the law," said Dariot, 41, a chief executive in a casual sweater and denim who took on the international company with some inspiration, he said, from independent French icons like Joan of Arc who were not afraid to challenge authority.
This month, Dariot triumphed in his year-and-a-half-old lawsuit against Google's French subsidiary, which has been ordered to pay him €75,000, or $97,000, in fines and legal costs. Dariot and his travel companies, Luteciel and Viaticum, successfully challenged Google's practice of selling Internet advertising from rivals designed to appear with Web searches for his trademarked Web site name, Bourse des Vols, which means flight exchange.
Keyword advertising, as it is known, is the main source of revenue for Google, which posted $3.19 billion in sales in 2004, largely through charges of a few cents each time a user clicks on an ad.
The growing number of lawsuits against Google around the world could diminish that advertising revenue by reducing the number of search words that could be sold to competitors - a threat to Google's business model that the company has acknowledged in regulatory filings.
Dariot's company is one of the first to win against Google; similar cases in the United States and Germany that challenged the search engine's use of keywords have failed.
But more companies are piling on. France is home to as many as 15 cases, according to lawyers involved.
Elsewhere, other companies are pressing Google with varying results on different legal points.
The Associated Press in New York and Kyodo News Agency in Tokyo have been negotiating with Google in connection with what they contend is its unauthorized use of material from the two news services.
Agence France-Presse, which had been talking to Google for almost six months in the same kind of dispute, sued the search engine in France in February and in the United States this month for $17.5 million in damages.
"The core issue is the same," said Joshua Kaufman, AFP's lawyer in Washington. "Google is using AFP pictures and stories without authorization in violation of copyright."
The keyword lawsuits have been filed by companies ranging from the hotel chain Accor to LVMH Moët Hennessy Louis Vuitton, the luxury goods manufacturer, which in February won its case. Keyword advertising is particularly sensitive for luxury retailers because manufacturers of knockoffs and counterfeits could advertise alongside trademarked names.
That has quietly changed in France, where rival advertising has been eliminated on Google's French Web site next to search results for prominent brand perfumes like Dior or Chanel. Yet similar advertising still surfaces with the same brand names on Google's Web sites in Britain and Germany.
Asked about those international differences in advertising from rivals, Google's spokeswoman in France, Myriam Boublil, said: "I can't really get into technical specifics. What I can tell you is that it was necessary to take down when a trademark issue is raised in France. Companies get back to us and let us know, and then we take it down."
She said that it was likely that companies had raised the trademark issue in some countries but not others.
Google itself is keenly aware of the perils of its keywords policy, which took effect in the spring of 2004 in the United States and Canada.
Basically, Google abandoned its policy of screening for trademarks when companies choose keywords for its popular advertising program, a gamble that could increase revenue but, as the company acknowledged, could also create legal problems.
According to Google's Web site: "When we receive a complaint from a trademark owner, we will only investigate whether the advertisements at issue are using the trademarked term in ad text. If they are, we will require the advertiser to remove the trademarked term from the text of the ad and prevent the advertiser from using the trademarked term in ad text in the future."
In Dariot's case, that meant that if users searched for his trademarked name, "Bourse des Vols," rival advertising would emerge alongside the name of his Web site.
In a Google filing with the U.S. Securities and Exchange Commission, the company admitted that the new policy could lead to more legal attacks. "Adverse results in these lawsuits," it said, "may result in, or even compel, a change in this practice, which could result in a loss of revenue for us, which could harm our business."
When companies do try to raise complaints about trademark or copyright issues, some complain that the issues can drag for months or even years.
In a recent California case, Norm Zada, the chief executive and founder of Perfect 10, a publisher of nude photographs and adult material based in Beverly Hills, said he started sending legal notices to Google about the unauthorized use of his images in 2001.
"After 16 notices, they said they couldn't do anything," Zada said.
Since then, he said, his attorney has issued a blizzard of 44 notices in the past two years that covered 9,000 unauthorized images. In January, he sued Google in U.S. court in Los Angeles.
Dariot, the owner of the French online travel agency, said that he also had resorted to a lawsuit out of frustration that his complaints were largely being ignored. Other search engines, he said, responded to similar complaints and withdrew rival advertising.
"First, Google said to give them proof of the trademark, and I did," he said. "And then a month passed. And then two more months passed and two more. Nothing happened."
Now, when a Google search is conducted for his company name, Bourse des Vols, the right side of the screen is as empty as the white sand beaches in the ads for vacation packages that he sells online. Google still can appeal Dariot's judicial victory. The French subsidiary's spokeswoman, Boublil, said last week that "for the moment Google is thinking of appealing, but I haven't gotten any confirmation yet."
Dariot's attorney, Cyril Fabre, is not waiting. He said he already had four other cases against Google, including one on behalf of Hotels Méridien.
Copyright © 2005 The International Herald Tribune | www.iht.com
March 24, 2005
VCs Suck, but you can still store your data on FreeBSD
Adam points to an essay by Paul Graham on A Unified Theory of VC Suckage. Sure, I guess, and if you like learning how and why, read it and also Adam's comments. Meanwhile, I'll just leave you with this amusing footnote:
[2] Since most VCs aren't tech guys, the technology side of their due diligence tends to be like a body cavity search by someone with a faulty knowledge of human anatomy. After a while we were quite sore from VCs attempting to probe our nonexistent database orifice.No, we don't use Oracle. We just store the data in files. Our secret is to use an OS that doesn't lose our data. Which OS? FreeBSD. Why do you use that instead of Windows NT? Because it's better and it doesn't cost anything. What, you're using a freeware OS?
How many times that conversation was repeated. Then when we got to Yahoo, we found they used FreeBSD and stored their data in files too.
Flat files rule.
(It turns out that the term of art for "we just use files on FreeBSD" is flat files. They are much more common than people would admit, especially among old timers who've got that "been there, done that" experience of seeing their entire database puff into smoke because someone plugged in a hair dryer or the latest security patch just blew away access to that new cryptographic filesystem with journalling mirrored across 2 continents, a cruise liner and a nuclear bunker. Flat files really do rule OK. Anyway, back to debugging my flat file database ...)
February 19, 2005
IEEE's Economics of Information Security
IEEE Security & Privacy magazine has a special on _Economics of Information Security_ this month. Best bet is to simple read the editor's intro.
There are two on economimcs of disclosure, a theme touched upon recently:
Two I've selected for later reading are:
This is because they speak to a current theme - how to model information in attacks.
January 31, 2005
Security Breach Disclosure is required for the consumer to adjust risk assessment
I was knowingly guilty of asking an innocent question last week on economics of disclosure. My penance will be forthcoming, no doubt, but in the meantime the question rebounds in the RFID breach post of yesterday. Jim posted:
"If the owner of a car parks it with the idea that it is safe, leaving his Picasso etchings in the backseat only to return to find that the Picassos were picked, then the courts will come into play. They will ask TI and this wonderful team of developers what the risk scenario was on this damn thing that did not work.""The team can say many things but what they cannot say is the risk is or was acceptable. So the classic issue of notification to all owners of the now cracked security system is in order so they might be made aware of the shortcoming. Also a prudent reserve should be placed aside by the TI team for claims against their flawed product."
(Read the post for the full context. Disclosure: My emphasis above, and I edited the original post for style!)
What Jim is challenging is the assumption in security thinking that the designer can predict the user's risk profile. When placed in terms like that, it sounds clearly bogus.
How is it possible for the designer to know what the user is up to? Is she trading oil futures, chatting about shopping lists or viewing porn? These activities have wildly different risk profiles and it is also evident that different products would be suited for different activities.
Classically, as Jim implies but does not state, a 'good' discloses its capabilities and its weaknesses in the sales event. Yet those capabilities and weaknesses - the product profile - change over time. So the crux of security breach disclosure is to permit the consumer to readjust their risk analysis. It is, and perhaps this is more important still, not directly purposed to the product manufacturer's needs.
So any economics of disclosure would be between the information holder and the end-user. That is, the seller of the good does not need to be in the loop, and only might be present if the seller has a convenient way to disclose (and/or a fiduciary duty to same, as is expressed in some laws).
And, another insight that I am having is that the essential economics of disclosure of a security breach are the same as the disclosure on the sales event. The purpose is the same: to give the consumer the ability to construct her risk analysis suited to her profile.
And thus, any attempt by the manufacturer (or the law or anyone else) to reduce disclosure is thereby reducing the ability of the end-user to readjust their risk profiles. Drawing from Hayek's information market, this is an a priori information 'bad.'
(Postscript: I wrote earlier on this flawed assumption in Who are you?)
January 30, 2005
How Ideas Evolve as a Shared Resource
Recently, I stumbled across a logical economics space where a decision had to be made and no rational information was available. It wasn't exactly that there was no information, but that there was too much noise, and the working hypothesis was that risky decisions would be made without any rational process being successful or potential, for the average participant. (I defined 'rational' as being related to the needs in some direct positive sense.)

Which led me to ponder how shared memes arise outside any framework of feedback. Is this a sales activity? A hype activity? A long search (ok, surf) brought me to the following list of possibilities. They are scattered, and tangential, and to cut a long story short, I remain irrationally indecisive on this process. I actually don't know where to look for this, so comments are also searched for?!
(Links: 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15)
I posted one theory a week back, the Big Lie, and I was somewhat surprised at the heckles raised. In a perverse sense, the response proved one thing, that information and truth can be hidden behind a subject of revulsion (and there are plenty of contempory revulsions with which to hide behind). Coincidentally, the Big Lie also provides one theory on how the shared memes arise, that of the conspiracy by the original big liars. It's a theory, but I'm not convinced it explains the space adequately or even in more than a small minority of cases of the Big Lie itself.
The next thread is what happens when a person knows the truth, and the world ignores him. For example, the case of Tsunami Smith, who warned in 1998 that a tsunami could hit in the Indian ocean; we know now he was ignored.
Another thread is how to extract the info. You could go and ask people, but people don't want to reveal their information. Here's two links (Educated Guesswork, and sharad) on how to extract sensitive information from users. Such games remind me of the old british army technique of the firing squad - 6 privates line up and are handed 5 bullets and one dummy. As none of them know which is the dummy, none of them are totally sure that they were responsible for the death of the victim.
Which leads us to the evolving science of the Ideas market. This is an idea by Robin Hanson whereby many people aggregate their opinions, but there are some tricks to overcome the barriers. Firstly, people get rewarded in some fashion for voting on ideas. Of course, few of us can predict the future, so most of the votes are non-useful. But some of the voters actually know what they are talking about. So, in order to overcome the 'popular vote' effect (which is close to what I'm looking at above), people who vote correctly are rewarded by increased value in their 'shares' in the idea's future, and those who vote incorrectly lose their investment. It's "put your money where your mouth is" time. (I have to of course mention my own contribution, the Task Market where you get to own the results of the choices as well.)
Memes are an idea that have been around for a long time - concepts or ideas that pass from person to person. I know this was a hot concept years ago, but I never paid attention to it. Wikipedia has some good starters on it, but it doesn't answer my question; how do these things arise? I do not know, but Wikipedia has a great example of the most popular net meme of all. If only it were that simple!?

You're probably facing some meme resistance by now. Karl Popper advocated this in the strongest possible terms: "the survival value of intelligence is that it allows us to extinct a bad idea, before the idea extincts us." I liked that quote so much I posted it on my SSL page. The only problem is, I don't know where and when he said it, which probably shows its memity.
The self as a meme - I am reminded of a habit I had (have?) when engaging a particularly stupid idea by someone convinced of same. This habit became known by those punished with it, and replicated. So much so that one day I was sitting beside a woman who did it, without realising where it came from ... No, I decline to document the meme, but those who know will.
This post on Boyd and Military Strategy provides an interpretation of what we are observing in certain security goods within OODA (observation-orientation-decision-action) loops. In brief: Observation has initially failed to reward observers, so alternate strategies are formed within Orientation. As there is insufficient feedback in the loop, the Orientation gets more and more powerful, until it is no longer capable of dealing with Observations. That is, those Observations that are in accord with the Orientation are accepted and trumpeted, and those against are discarded. (Those that are ambiguous are open to misinterpretation!)
And finally, Crowds and Power is a book I am reading by Elias Canetti. The mob ruleth, and I shall report back when I've discovered how to rule the mob. Also on the list is Extraordinary Popular Delusions. With a title like that, it just has to have some secrets hidden within.
Which, all tantalising snippets aside, gets me no closer to understanding how decisions are made when there is insufficient information. Maybe that's the way it has to be...
Addendum #1: Adam reminds me to add the Keynesian Beauty Contest:
The Keynesian beauty contest is the view that much of investment is driven by expectations about what other investors think, rather than expectations about the fundamental profitability of a particular investment. John Maynard Keynes, the most influential economist of the 20th century, believed that investment is volatile because investment is determined by the herd-like “animal spirits” of investors. Keynes observed that investment strategies resembled a contest in a London newspaper of his day that featured pictures of a hundred or so young women. The winner of the contest was the newspaper reader who submitted a list of the top five women that most clearly matched the consensus of all other contest entries. A naïve strategy for an entrant would be to rely on his or her own concepts of beauty to establish rankings. Consequently, each contest entrant would try to second guess the other entrants’ reactions, and then sophisticated entrants would attempt to second guess the other entrants’ second guessing. And so on. Instead of judging the beauty of people, substitute alternative investments. Each potential entrant (investor) now ignores fundamental value (i.e., expected profitability based on expected revenues and costs), instead trying to predict “what the market will do.” The results are (a) that investment is extremely volatile because fundamental value becomes irrelevant, and (b) that the most successful investors are either lucky or masters at understanding mob psychology – strategic game playing. “Animal spirits” are now known as “irrational exuberance,” and this beauty contest model is an explanation for such phenomena as stock market bubbles. Contrast this model with efficient markets and present value.
January 28, 2005
The Coming Collapse of the Dollar
I expected to be disappointed and frustrated at the new book by Turk & Rubino, but I have to say I was positively surprised. It's good. This is a book that will be read avidly by all American journalists seeking for the answer before today's deadline as to why the dollar bombed so badly. (Links 1)
It's concise, it's well written, and it's also pretty darn accurate. Of course, it is a little loose in the economics, but given its conciseness that can be expected, and nothing is fatal in its layout of the basic story. Lots of nice graphics, and neat sections at the back telling you what to do about it.
The central message is this: Americans borrowed too much, exported too many dollars and too few goods. Hey, it was good while it lasted, but now the combined effect of the rise of the Euro (only 5 years old and already as big as the dollar!) and the ribald profligacy of the Bush Administration have given the world an alternate as well as a reason. By my guess, there has been an adjustment of about 10% in dollar reserves worldwide, with another 10% to come. Doesn't sound like much? Consider that about 60% of those dollars were overseas, 10% already went looking for a new home and another 10% to come.
The bad news is that you (yanks) don't own your own currency. The worse news is you're about it own more of it! Oh, and add to that the pent up pressures of decades of central bank manipulation of the gold unit, the sell-of of reserves, mucked up leasing programs and no doubt other scandals, and gold might just burst its sensible barriers.
How low will the dollar go? It's tough to say. It's currently out of balance, and another 20-30% seems reasonable. I however do not believe "it's all over" for the dollar. The reason is simple; no matter how badly the people have borrowed their future away, there are still 250 million of them sitting on top drawer capital assets and possessing a capability to work. Yes it will readjust, but no, it isn't all over, unless they close the borders like they did in the 1930s. If they start shipping the Mexicans back, then watch out, America (do the maths, there are more Mexican workers than there are unemployed "americans").
Anyways, I digress slightly. If you are an American, and if you're looking for a view of what's happening without having to spend your days being depressed by what passes for American media, pick up _The Coming Collapse of the Dollar_. It's only $27 at the local book store, and the clear and concise message will give you valuable pause for thought. Even if you don't quite subscribe to the message, consider it a valuable thought exercise in where America is going next.
January 27, 2005
Towards an Economic Analysis of Disclosure
Adam says an economic analysis of Disclosure (of security bugs) has never been done, and makes a good start at it (perhaps in order to distract me from the stock market losses...). His list of costs are: 1. researcher, 2. primary vendor, 3. user patching, 4. secondary (layered) vendors, 5. attacker.
To which I would add this:
A. there is a cost to the user if they *don't* patch. That is, the user faces costs regardless, and in the decision to patch or not patch, they face one of two possibilities. Patching costs are low, but in the aggregate high. Not-patching costs are high individually, but in the aggregate, low(er). The question arises what the probability for breach event is, and what the cost of that breach is. This (multiplied) would then be compared against the user's patch costs.
B. there is also the decision not to disclose. In the event of not disclosing, we are essentially taking a gamble that nobody else figures it out (i.e., the decision not to disclose is the same as the decision to use security by obscurity, but by a different party). The key question I suppose is, "what is the probability that the information will still find its way to an attacker?" If that probability is low, then there might be merit in not disclosing. But, if one can show that this is information that is likely to get to the attacker, that merit disappears.
Once we identify all these different costs .. and probabilities, it should be a snap to develop a model that gives us some predictions! So yes I'm happy, especially as the economics of stock market shifts is so much voodoo anyway ;-)
January 26, 2005
The market punishes bad news, not bad not-news
Adam responded over on his blog to my claim that it was FUD that the market was shifting to, not the loss of confidentiality. So I'll try and argue my case more.
The market responds to news. It doesn't respond to not-news. Why not? The reason for that is that the not-news is already factored in. That is, Bank of America is known to have the potential for branch bank robbery, and the market puts a risk premium on it for that. Bank of America may be big enough to face a bank robbery a day, but the market knows that and doesn't respond to any individual event.
The news that a confidentiality breach has occurred then is either news or not-news. In the case of the measured companies, that dropped 5% in one study, 2% in another, it was clearly news.
Yet, confidentiality breaches are occurring all the time. Visa and Mastercard and all the banks are being raided on a routine basis. What happens when some bank announces it has arrested an insider for selling account information for $10 or $20 a pop? Nothing. That's not-news. It's not news because the market already understands that the banks and retail credit and identity systems have a huge insider problem. So it's factored in. No shift in market price, even if 100,000 accounts have been compromised.
Then, when some poor muggins who is doing something different - not the usual suspects listed above - and discovers their account database has been lifted, that is ... different! That's news - not because its bad. In fact, we can probably empirically show that it is way less bad than the above not-news because it is much rarer and the compromises are generally lighter. But no matter, the journos write about it, the righteous point fingers, and the market sells.
What the news is in this case is that the market has not understood and has not factored in the possibility of a loss of confidentiality in the new player. It might be an Internet bank, or it might be a telco, or it might be a government department. Either way, all this data sitting there and nobody knew about it nor understood that it could leak ... well, when *that* data gets lifted by a sneaky hacker, we are all surprised.
Try it some time. Look at a particular case and look deeply. I'd suggest you will come to the conclusion that there was a storm in a teacup. As in, "so what was all the fuss about?" Consider the recent Mobile-T thing. 400 users had their account information lifted. What was the scandal? What had really attracted the attention of the press was that the hack had occurred against a Secret Service agent! Very sexy! What's more, famous names had their photos downloaded. Better and better. And, shock horror, telcos are amassing huge databases of our personal lives!
If only 400 boring accounts from a telco had been lifted, what would you write about? I think that story showed a definate press bias on the "new and scary" and the market to some extent follows that. To be fair we'd need a bank insider story to compare this to - and there are quite a few. Problem is, they are so mundane that even I forget them.
Also, you can look at those X accounts and propose some metric as to how much that confidentiality is worth. Say the 400 account hack dropped Mobile-T's share price by 5%. (Hypothetically, I don't know if they got hit or not.) Now, they have many more accounts than that. I'd guess they have something in the millions.
What happens if they lose a million accounts? Does that mean their share price goes down by 100 * 5% * 1,000,000/400 = 12500% ? No of course not. Firstly, they can't go down below 100%. Secondly, even if they opened up every account they had, they still haven't got a loss of revenue stream.
Which is to say that whatever is being said by the stock market, it is *not* anything quantifiable: it is not measuring an _amount_ of confidentiality. I guess my point here is that it is the meta-loss, not the confidentiality itself that is the crime.
January 25, 2005
Do security breaches drop the share value?
According to those that think WiKID thoughts, yes. Quoting a paper by Campbell et al, there can be measured a 5% drop in stock price when confidentiality is breached. Adam demurs, thinking the market is unconcerned about the breaches of confidentiality, rather, is concerned about a) loss of customers or b) lawsuits.
I demur over both! I don't think the market cares about any of those things.
In this case, I think the market is responding to the unknown. In other words, fear. It has long been observed that once a cost is understood, it becomes factored in, and I guess that's what is happening with DDOS and defacements/viruses/worms. But large scale breaches of confidentiality are a new thing. Previously buried, they are now surfaced, and are new and scary to the market.
And the California law makes them even scarier, forcing the companies into the unknown of future litigation. But, I think once these attacks have run their course in the public mind, they will stop causing any market reaction. That isn't to say that the attacks stop, or the breaches in confidentiality stop, but the market will be so used to them that they will be ignored.
Otherwise I have a problem with a 5% drop in value. How is it that confidentiality is worth 5% of a company? If that were the case, companies like DigiCash and Zero-Knowledge would have scored big time, but we know they didn't. Confidentiality just isn't worth that much, ITMO (in the market's opinion).
The full details:
"The economic cost of publicly announced information security breaches: empirical evidence from the stock market," Katherine Campbell, Lawrence A. Gordon, Martin P. Loeb and Lei Zhou Accounting and Information Assurance, Robert H. Smith School of Business, University of Maryland, 2003.
Abstract This study examines the economic effect of information security breaches reported in newspapers or publicly traded US corporations. We find limited evidence of an overall negative stock market reaction to public announcements of information security breaches. However, further investigation reveals that the nature of the breach affects this result. We find a highly significant negative market reaction for information security breaches involving unauthorized access to confidential data, but no significant reaction when the breach does not involve confidential information. Thus, stock market participants appear to discriminate across types of breaches when assessing their economic impact on affected firms. These findings are consistent with the argument that the economic consequences of information security breaches vary according to the nature of the underlying assets affected by the breach.
Also over on Ross Anderson's Econ & Security page there are these:
Two papers, "Economic Consequences of Sharing Security Information" (by Esther Gal-Or and and Anindya Ghose) and "An Economics Perspective on the Sharing of Information Related to Security Breaches" (by Larry Gordon), analyse the incentives that firms have to share information on security breaches within the context of the ISACs set up recently by the US government. Theoretical tools developed to model trade associations and research joint ventures can be applied to work out optimal membership fees and other incentives. There are interesting results on the type of firms that benefit, and questions as to whether the associations act as social planners or joint profit maximisers.
Which leads to "How Much Security is Enough to Stop a Thief?," Stuart Schechter and Michael Smith, FC03 .
January 02, 2005
Security Signalling - the market for Lemmings
Adam continues to grind away at his problem: how to signal good security. It's a good question, as we know that the market for security is highly inefficient, some would say dysfunctional. E.g., we perceive that many security products are good but ignored, and others are bad but extraordinarily popular, and despite repeated evidence of breaches, en masse, users flock to it with lemming-like behaviour.
I think a real part of this is that the underlying question of just what security really is remains unstudied. So, what is security? Or, in more formal economics terms, what is the product that is sold in the market for security?
This is not such an easy question from an economist's point of view. It's a bit like the market for lemons, which was thought to be just anomalous and weird until some bright economist sat down and studied it. AFAIK, nobody's studied the market for security, although I admit to only having asked one economist, and his answer was "there's no definition for *that* product that I know of!"
Let's give it a go. Here's the basic issue: security as a product lacks good testability. That is, when you purchase your standard security product, there is no easy way to show that it achieves its core goal, which is to secure you against the threat.
Well, actually, that's not quite correct; there are obviously two sorts of security products, those that are testable and those that are not. Consider a gate that is meant to guard against dogs. You can install this in a fence, then watch the rabid canines try and beat against the gate. With a certain amount of confidence you can determine that the gate is secure against dogs.
But, now consider a burglar alarm. You can also install it with about the same degree of effort. You can conduct the basic workability tests, same as a gate. One opens and goes click on closing; the other sets and resets, with beeping.
But there the comparison gets into trouble, as once you've shown the burglar alarm to work, you still have no real way of determining that it achieves its goal. How do you know it stops burglars?
The threat that is being addressed cannot be easily simulated. Yes, you can pretend to be a burglar, but non-burglars are pretty poor at that. Whereas one doesn't need to be a dog to pretend to be a dog, and do so well enough to test a gate.
What then is one supposed to do? Hire a burglar? Well, let's try that: put an ad in the paper, or more digitally, hang around IRC and learn some NuWordz. And your test burglar gets in and ... does what? If he's a real burglar, he might tell you or he might just take the stuff. Or, both, it's not unreasonable to imagine a real burglar telling you *and* coming back a month later...
Or he fails to get in. What does that tell you? Only that *that* burglar can't get in! Or that he's lying.
Let's summarise. We have these characteristics in the market for security:
- a test of the product by a simulated threat is:
- expensive, and
- the results cannot be relied upon to predict defence against a real threat;
- a test of the product by a real threat is:
- difficult to arrange,
- could be destructive, and
- the results cannot be relied upon to predict defence against any _other_ real threat.
Perhaps some examples might help. Consider a security product such as Microsoft Windows Operating System. Clearly they write it as well as they can, and then test it as much as they can afford. Yet, it always ships with bugs in it, and in time those bugs are exploited. So their testing - their simulated threats - is unsatisfactory. And their ability to arrange testing by real threats is limited by the inefficient market for blackhats (another topic in itself, but one beyond today's scope).
Closer to (my) home, let's look at crypto protocols as a security product. We can see that it is fairly close as well: The simulated threat is the review by analysts, the open source cryptologists and cryptoplumbers that pore through the code and specs looking for weaknesses. Yet, it's expensive to purchase review of crypto, which is why so many people go open source and hope that someone finds it interesting enough. And, even when you can attract someone to review your code, it is never ever a complete review. It's just what they had time for; no amount of money buys a complete review of everything that is possible.
And, if we were to have any luck in finding a real attacker, then it would only be by deploying the protocol in vast numbers of implementations or in a few implementations of such value that it would be worth his time to try and attack it. So, after crossing that barrier, we are probably rather ill-suited to watching for his arrival as a threat, simply due to the time and effort already undertaken to get that far. (E.g., the protocol designers are long since transferred to other duties.) And almost by default, the energy spent in cracking our protocol is an investment that can only be recouped by aggressive acquisition of assets on the breach.
(Protocol design has always been known to have highly asymmetric characteristics in security. It is for this reason that the last few years have shown a big interest in provability of security statements. But this is a relatively young art; if it is anything like the provability of coding that I did at University it can be summarised as "showing great potential" for many decades to come.)
Having established these characteristics, a whole bunch of questions are raised. What then can we predict about the market for Lemmings? (Or is it the market for Pied Pipers?) If we cannot determine its efficacy as a product, why is it that we continue to buy? What is it that we can do to make this market respond more ... responsibly? And finally, we might actually get a chance to address Adam's original question, to whit, how do we go about signalling security, anyway?
Lucky we have a year ahead of us to muse on these issues.
December 04, 2004
The SEC's NMS: One Price to rule them all, One Price to find them, One Price to bring them all and in the market bind them
With apologies to JRR Tolkein! Still, the comparison seems apt - the SEC is blessing the market with a new regulation. And this time they are apparently serious about binding the market to the old "one price" rule found in the legislation of the National Market System.
The one price rule probably needs some explanation. We have to go right back to the days of the 1929 crash, the Great Depression, and the creation of the SEC. The Congress of the day decided it would be a mighty fine idea if all investors should have one only price for a given stock, across all markets. So they wrote in the SEC's defining act a rule that said that all exchanges must work to one price. To be sure, what they said was "best price" but we can skip over the 3rd grade analysis here.
It was called, in essence, the National Market System ("NMS"). This was always known to be a mistake. For some reason, within the bastion of modern capitalism's most exalted high temple of the market process - the American trading markets - Congress thought that they should turn off the very notion of competition by flicking the regulatory switch. Why they thought that competitive markets could be improved by non-competitive prices is not recorded, but the SEC wisely ignored the regulation. Or, to be more precise, what the SEC did was to craft an exception, or many exceptions, and allow participants to find themselves in the exceptions.
Now, however, it seems that they've changed their minds. Or their minds have been changed for them. Now, the SEC has decided to turn off competition between markets. Why now, of all times, can only be wondered at.
http://www.financetech.com/utils/www.wallstreetandtech.com/story/enews/showArticle.jhtml?articleID=54202039
November 30, 2004
Economics is isomorphic with risk?
Adam Shostack writes, commententing on AMS's aphorism directly below, that
" [it must be] Economics. There's more to our dismal work than risk management: There's the study of signaling, investment choices, and a host of issues which are broader than just risks."
Which, I feel, just underscores the point! Signalling is how we say that we are a good risk; choice of investments is a choice of risk & return; and my original claim of risk being an isomorphism for the popular term of economics derived from something like this:
"when you say 'it's economics' that means I'm not going to get my money back, right?"
November 01, 2004
Halloween and The Candy Economy
Jeffrey Tucker has penned his observations of The Candy Economy, direct from the streets of Halloween. Some might be horrified at the conduct of Misean experiments on innocent children, but it sure beats the "Mice-like" experiments that are frequently conducted on adults by well meaning governments. After discussing all the evils and woes of such pagan festivals, he leaps into how the children discover prices and reinvent free trade:
"What children truly adore about Halloween is what takes place after the candy has been brought back to home base: the trading. Here is where the excitement begins.""No child can fully control what he or she is given, so it is up to that child to make exchanges with others in order to obtain what he or she really wants, and to do so in a strategic manner so that overall wealth is enhanced."
Read it all and laugh: http://www.mises.org/blog/archives/002672.asp
October 22, 2004
New Tack Wins Prisoner's Dilemma
Here's a classic example of how a competition based on the economics problem known as the Prisoner's Dilemma has been exploited: A seemingly complete theory has once again been turned on its head. All's fair in love and war, and the best attacks come when we challenge the other guy's assumptions.
New Tack Wins Prisoner's Dilemma
By Wendy M. Grossman
Story location: http://www.wired.com/news/culture/0,1284,65317,00.html
02:00 AM Oct. 13, 2004 PT
Proving that a new approach can secure victory in a classic strategy game, a team from England's Southampton University has won the 20th-anniversary Iterated Prisoner's Dilemma competition, toppling the long-term winner from its throne.
The Southampton group, whose primary research area is software agents, said its strategy involved a series of moves allowing players to recognize each other and act cooperatively.
The Prisoner's Dilemma is a game-theory problem for two players. As typically described, two accomplices are arrested and separated for interrogation by the police, who give each the same choice: confess to authorities (defect) or remain silent (cooperate). If one defects and the other cooperates, the defector walks free and the cooperator gets 10 years in jail. If both cooperate, both get six months. If both defect, both get six years. Neither suspect knows the other's choice.
"The Prisoner's Dilemma is this canonical problem of how to get cooperation to emerge from selfish agents," said Nick Jennings, a professor in computer science at Southampton University and leader of the winning team along with his Ph.D. student, Gopal Ramchurn. "People are very keen on it because they can see so many parallels in real life."
Before Southampton came along, a strategy called Tit for Tat had a consistent record of winning the game. Under that strategy, a player's first move is always to cooperate with other players. Afterward, the player echoes whatever the other players do. The strategy is similar to the one nuclear powers adopted during the Cold War, each promising not to use its weaponry so long as the other side refrained from doing so as well.
The 20th-anniversary competition was the brainchild of Graham Kendall, a lecturer in the University of Nottingham's School of Computer Science and Information Technology and a researcher in game theory, and was based on the original 1984 competition run by a University of Michigan political scientist, Robert Axelrod.
The Iterated Prisoner's Dilemma is a version of the game in which the choice is repeated over and over again and in which the players can remember their previous moves, allowing them to evolve a cooperative strategy. The 2004 competition had 223 entries, with each player playing all the other players in a round robin setup. Because Axelrod's original competition was run twice, Kendall will run a second competition in April 2005, for which he hopes to attract even more entries.
Teams could submit multiple strategies, or players, and the Southampton team submitted 60 programs. These, Jennings explained, were all slight variations on a theme and were designed to execute a known series of five to 10 moves by which they could recognize each other. Once two Southampton players recognized each other, they were designed to immediately assume "master and slave" roles -- one would sacrifice itself so the other could win repeatedly.
If the program recognized that another player was not a Southampton entry, it would immediately defect to act as a spoiler for the non-Southampton player. The result is that Southampton had the top three performers -- but also a load of utter failures at the bottom of the table who sacrificed themselves for the good of the team.
Another twist to the game was the addition of noise, which allowed some moves to be deliberately misrepresented. In the original game, the two prisoners could not communicate. But Southampton's design lets the prisoners do the equivalent of signaling to each other their intentions by tapping in Morse code on the prison wall.
Kendall noted that there was nothing in the competition rules to preclude such a strategy, though he admitted that the ability to submit multiple players means it's difficult to tell whether this strategy would really beat Tit for Tat in the original version. But he believes it would be impossible to prevent collusion between entrants.
"Ultimately," he said, "what's more important is the research."
"What's interesting from our point of view," he said, "was to test some ideas we had about teamwork in general agent systems, and this detection of working together as a team is a quite fundamental problem. What was interesting was to see how many colluders you need in a population. It turns out we had far too many -- we would have won with around 20."
Jennings is also interested in testing the strategy on an evolutionary variant of the game in which each player plays only its neighbors on a grid. If your neighbors do better than you do, you adopt their strategy.
"Our initial results tell us that ours is an evolutionarily stable strategy -- if we start off with a reasonable number of our colluders in the system, in the end everyone will be a colluder like ours," he said.
The winners don't get much -- an unexpected $50 check and a small plaque. But, says Kendall, "Everybody in our field knows the name of Anatol Rapoport, who won the Axelrod competition. So if you can win the 20th-anniversary one, in our field there's a certain historical significance."
October 14, 2004
de Soto's _The Mystery of Capital_ afflicted by poor title
Hernando de Soto has done what I think is the most significant work in economics in the last decade. He has researched what makes people poor. Travelling many poor countries and looking at many impoverished economies, he believes he has found the answer: poverty of title.
de Soto's book, the Mystery of Capital, is about how the lack of clear and open title to assets is the rock that crushes the poor. Without good title, the poor cannot raise capital. Without good title, the poor have to sit on their assets, and resort to physical security at their own cost. Without good title, there is no possibility of economic and efficient allocation of resources.
It was then with some sadness that I saw this ironic development in some chat room on the net: the poverty of title over the book itself has been exploited. Ironically, someone has OCR'd the book and is now selling the electronic versions.
I would hope that Hernando would shrug his shoulders and carry on, realising that the fundamental title to books and knowledge is as weak already as the title a poor mother holds over her shack in a shanty town. That which we call intellectual property, which some claim to derive from the belief that man has the right to what was created in his own head, has over-extended itself, and technology is now in the process of destroying it.
Title is no such beliefs-based right. It is an economic practicality, we create title as a society to protect that which is naturally protectable. Law follows economics, and economics follows physics.
This sad path may well be the path to its future success, and I can think of no higher accolade for a work than to be sacrificed on its own altar. The Mystery of Capital is needed in any place where the poor have no strong title, and thus they lack the money to buy the book.
-------- Original Message --------
Subject: The Mystery of Capital, eBook
Date: Thu, 14 Oct 2004 09:28:36 00200 (CEST)
From: Nostra
I have recently completed the conversion of the excellent economics
book, The Mystery of Capital, by Hernando de Soto, to Adobe Acrobat
format. http://www.amazon.com/exec/obidos/ASIN/0465016154
The 8.91 MB book is available for download at a cost of 0.1 grams of
e-gold from the File Exchange at
https://www.meshmx.com/fe/download_get.php?file=FE:d7c1ecf8b3e460de8a2f9ce1003595f0c2344cb2
For instructions on funding a File Exchange Pay Token needed for
downloading the book, download the free Acrobat document at:
https://www.meshmx.com/fe/download_get.php?file=FE:ab2e4d29a46088a8c3ed4c21a8baf9041f93d29c
This conversion easily required over 80 hours of intense OCR, Photoshop
and MSWord editing. I ask that anyone downloading not post the eBook
or share with friends (you are, of course, as free to ignore this as I
have been in ignoring Mr. DeSoto's publisher's request that I honor
their copyright.) I intend to offer the author a share of the proceeds
should they become significant.
Discussion in Distributed City regarding this e-publication can be found
at
https://www.distributedcity.com/forums/?action=thread_view&thread_id=f304a9b748efdc04a3e5f949be30b277
Nostra
May 24, 2004
The Myth of Systemic Risk
At a St. Louis Banking Conference, Professor George Kaufman presented a thesis of his that "systemic risk" is a myth [1]. It goes like this: Systemic Risk is that risk of contagion, whereby a failure causes a domino-like collapse of large segments of the system. Professor Kaufman makes the claim that an institution that is financially sick should fail, and that isn't a case of systemic risk. Those that are financially healthy should not fail, and if they do, it could be systemic risk.
He then goes on to challenge his listeners to find an example of an economically solvent bank that was brought down by a run, anywhere in the world. So far, no joy - he's not been presented with any such cases, although like myself and the MITM, he holds out hope.
Which leaves us rethinking the S&L scandal, the Asian crisis, and sundry other squillion dollar collapses (in another paper, he presents just how devastating these collapses are [2]). If all those countries in Asia back in the late 90s were insolvent, or at least financially unsound, then he asserts that they shouldn't have been propped up. When the Asian dominos wobbled and fell, that was an example of proper bankrupcy procedures, albeit at a national level, rather than systemic risk.
What are the consequences of this? One of the underlying justifications for central banking was that they could protect the system from systemic risk. That crutch is now removed from the Central Banks and their role as centralised regulators. Other crutches such as monopoly issuance of money, and the myth of "banking is special" have been under stress for many a year.
To some extent this has already been predicted; it's been clear for some time that the 20th century was the Golden Age of Central Banks and now everyone is posturing for, or at least fearing, a gradual waning of their influence and place in financial society.
On a more personal note, when we built Ricardo and our real time gross settlement system of trading, we used to say that we'd eliminated sources of systemic risk. Maybe we should back off from that and just claim the elimination of other classes of risk, and a reliance on the supreme savings of cheap RTGS trades (one or two orders of magnitude, but who's counting?). Or maybe not; is there a contradiction in claiming the elimination of something that doesn't exist?
[1] Professor George Kaufman, "The Myth of Systemic Risk," remarks presented at the St Louis Banking Conference,
http://www.fed-soc.org/Publications/practicegroupnewsletters/financialservices/myth-finv3i3.htm
[2] Professor George Kaufman, "Banking and currency crises and systemic risk: Lessons from recent events," Federal Reserve Bank of Chicago,
http://www1.worldbank.org/economicpolicy/managing volatility/contagion/documents/3qep2.pdf
May 14, 2004
Ross Anderson's "Economics and Security Resource Page"
For those interested in the intersection of security and economics, Ross Anderson's page has a wealth of links.
"Do we spend enough on keeping `hackers' out of our computer systems? Do we not spend enough? Or do we spend too much? For that matter, do we spend too little on the police and the army, or too much? And do we spend our security budgets on the right things?"
"The economics of security is a hot and rapidly growing field of research. More and more people are coming to realise that security failures are often due to perverse incentives rather than to the lack of suitable technical protection mechanisms. (Indeed, the former often explain the latter.) While much recent research has been on `cyberspace' security issues - from hacking through fraud to copyright policy - it is expanding to throw light on `everyday' security issues at one end, and to provide new insights and new problems for theoretical computer scientists and `normal' economists at the other. In the commercial world, as in the world of diplomacy, there can be complex linkages between security arguments and economic ends."
"This page provides links..."
April 26, 2004
Rates II - Mortgages and Musical Chairs
Dismal Science - By SUSAN LEE - April 26, 2004; Page A15
Financial crises usually come from left field. But that doesn't stop swamis from searching for the next trigger. Right now, the prospect of rising interest rates is focusing swamis on trouble in the bond market. Not a bad bet, since the past few years of falling rates have produced a ton of complicated ways to extract profits from fixed-income securities. Also not a bad bet since a forecast of higher rates is driving investors to unwind positions -- presenting a perfect moment to expose flaws in hedging and other strategies.
So it's hardly surprising that concentration of risk is Topic One. Consider, for example, a recent speech by the new head of the Federal Reserve Bank of New York. In lovely Fed-speak, Timothy Geithner blended concerns about the increasing vulnerability of the financial system to the growth in Fannie Mae and Freddie Mac and the high degree of concentration in the market for interest-rate options.
Mr. Geithner was vague in the extreme, but the details of his concern are laid out in a report from Credit Suisse First Boston. Here are the mechanics of a possible crisis scenario in which the particular nature of risk in the mortgage market becomes concentrated in the market for interest-rate options.
The chain of transmission starts with the mortgage market. (Bear in mind that, at some $7 trillion, this market is enormous.) Mortgages are of course wondrous financial instruments. They allow people, even those with humble means, to own a big asset -- a house -- without having to pay the full price up-front. But mortgages have an almost as wondrous property -- they give home buyers the opportunity to pay off before maturity. This prepayment option allows homeowners to transfer interest-rate risk to mortgage holders.
Holders of mortgage securities borrow money to buy those securities. If all goes according to plan, holders buy securities that yield more than they pay on their debt. However, when interest rates fall and homeowners prepay, mortgage holders find that cash flows have changed. What was a nice deal of, say, receiving 6% on mortgages and paying 5% on debt could become a less comfortable arrangement of receiving 5% on mortgages and paying 5% on debt. Not good. Or say that interest rates go up; then homeowners keep their mortgages and holders could find themselves getting 6% on assets but paying 6% on debt. Also not good.
Thus, having taken on interest-rate risk, owners of mortgage securities must hedge against that risk. One route to insure against a change in the spread between assets and liabilities is to use a derivative, usually involving Treasuries like interest-rate options. With these options, one party can insure itself against rising rates (or against falling rates).
All this is very cozy and safe in theory, but what about the real world?
The market for interest-rate options has two distinguishing properties. First, it is huge -- with a notional value of roughly $6 trillion -- larger than the amount of Treasury debt outstanding. Second, it is the only derivative market in which broker-dealers, collectively, take a position. Ordinarily, dealers just match buyers and sellers of risk, but in the interest-rate options market, dealers sell a lot more than they buy.
Simply put, prepayment risk has now been shifted to dealers. Dealers, in turn, try to dynamically hedge that risk. But their exposure is not symmetrical. Because they carry an inventory of Treasuries, they have a structural long position that gives them a natural hedge when interest-rates fall, but works against them when rates rise (they have to sell a lot of Treasuries -- and fast.)
This creates a powerful feedback loop. For example, dealers buy Treasuries when rates are falling, putting further downward pressure on rates -- and sell Treasuries when rates are rising, putting further upward pressure on rates. Although dynamic hedging is less likely to be a systemic issue when rates are falling, either way changes in rates are amplified by dealers covering exposure to interest-rate options.
What makes this feedback loop potentially lethal is that a change in rates requires an even larger adjustment in hedging portfolios. The CSFB report calls this "the embedded accelerator effect." The market had a tiny taste of this feedback loop last summer when interest-rates suddenly shot up and spreads in the swap market almost doubled in a few weeks. It was a stunning demonstration of just how sensitive the market is to rising rates.
Scary, sure, but two other aspects conspire to make the situation positively frightening. Over the past several years, coupons in the mortgage market have become concentrated, as owners rushed to refinance at the same time. Instead of a wide array of interest rates, coupons have collapsed to a very narrow range. This concentration increases the amount of hedging adjustments necessary for even a small move in rates.
Moreover, interest-rate options have become concentrated among a small number of dealers. Five, to be exact. And three of those five hold more than two-thirds of the options outstanding among FDIC-insured banks: JPMorgan Chase, Bank of America and Citigroup. (Even scarier, JPMorgan alone holds a notional amount of $4.5 billion -- that's 40% of the options held by banks and 27% of the total interest-rate options market.)
Simply put, any swami who wants to worry about the concentration of risk need not look beyond the mortgage market. Two highly leveraged hedge funds, Fannie and Freddie, are laying off giant amounts of risk in the interest-rate options market, where that risk is then redistributed to a handful of dealers. Throw in a little feedback loop, where changes in rates can quickly become a crack-the-whip situation causing massive instability -- and viola, giant liquidity risk.
Of course, Mr. Geithner isn't forecasting the end of the world or even a liquidity crisis. Nonetheless, his concerns should remind us that financial markets, no matter how sophisticated, cannot extinguish risk. Indeed, risk can be only moved around, from one player to another. But just like in musical chairs, when the music stops somebody is left standing.
Ms. Lee is a member of the editorial board of The Wall Street Journal.
Rates I - US moves to raise rates
Scuttlebut has it that banks have heard Mr G's suggestions and are responding. A month or so back he said "banks are missing out on the opportunity to sell variable rate product to consumers."
What strange language! Yet insiders knew that what he was saying was that the time to balance your books is now, and sharpish, before he raises rates. Now comes rumour that the banks are moving to consolidate their customers into variable rate packages.
Here's how one bank does it. Take a customer who's awash with credit card debt, but has some equity on a fixed rate loan. Offer them the chance to switch their credit card debt (variable) and their mortgage (fixed) into a new mortgage (variable) with a higher valuation (90% instead of 80%).
Bingo, the bank has got rid of two headaches in one. The consumer "benefits" because they have expunged their credit card debt. There's only one problem left: if the variable rate mortgage suffers an increased default rate as the interest rates rise to pay back the 90's hangover, the banks might be left holding a lot of collapsed real estate. (This sort of sweet deal may only be available in coastal, stable areas....).
And here's the clincher: no, even that doesn't happen, because the banks don't hold the loan. They've already sold the securitized packages off into the market, by the time the rate increase bites. So not only have they got rid of their credit card debt (uncollateralised, so not saleable) they've repaired the prior securitised portfolios with the chance to take a new origination fee.
Banks in the US no longer do much in the way of banking. That is, they don't borrow and lend to the public. What they do instead is originate loans which are sold to the market. Each group of a thousand mortgages becomes its own little community IPO. Which means, banks are in the process of selling securities (or, is it buying securities? no matter). They've solved the balance sheet problem - the term rate misbalance - that made banking special.
As sellers of securities, banks are now more like brokers. Yet, they are still supervised by the bank regulators. Expect more mystical and godly pronouncements from the regulatory sector, as they catch up to the recognition of the Arrow observation: as the cost of transactions shrinks to zero, banking disappears and everyone goes to market.