January 29, 2019
How does the theory of terrorism stack up against AML? Badly - finally a case in Kenya: Dusit
Finally, an actual financial system & terrorism case lands before the courts, relating to the Dusit attack. Is this a world first? I don't know because this conjunction is so rare, nobody's tracking it.
The essential gripe is that since 9/11 the financial world decided to slap the terrorism label on their compliance process. Yet to no avail. Very few cases, so small that they fall between bayesian cracks. So misdirected because terrorists have options, and they can adjust their approach to slip under they radar. Backfiring because the terrorists are already outside norms and will do as much damage as needed, thus further harming the financial system.
And so hopeless because your true terrorist doesn't care about being caught afterwards - he's either dead or sacrificed.
Anyway, that's the theory - anti-terrorism applied to the financial system simply won't work. Let's see how the theory stacks against the evidence.
A suspect linked to the Dusit terror attack received Sh9 million from South Africa in three months and sent it to Somalia, the Anti-Terror Police Unit have said. Twenty one people, including a GSU officer, were killed in the January 15 attack. The cash was received through M-Pesa.
So far so good. We have about $90,000 (100 Kenya shillings is 1 USD) sent through M-Pesa, a mobile money system in Kenya, allegedly related to the Dusit attack.
Hassan Abdi Nur has 52 M-Pesa agent accounts. Fourty seven were registered between October and December last year, each with a SIM card. He used different IDs to register the SIM cards.
So (1), the theory of terrorism predicts that the money will be moved safely, whatever the cost. We have a match. In order to move the money, 52 accounts were opened, at the cost of different IDs.
One curiosity here is the cost. In my long running series on the Cost of your Identity Theft we see (or I suggest) an average cost of an Identity set of around $1000. Which would amount to a cost of $52k for 50 odd sets. But this is high for a washed amount of $90k.
Either the terrorists don't care of the cost, or cost of dodgy ID is lower in Kenya, or the alleged middleman amortised the cost over other deals. Interesting for further investigation but not germane to this case.
Then (2), the theory of bayesian statistics and the "base rate fallacy" predict that no terrorists will ever be caught before the fact based on AML/KYC controls.
Clearly this is a match - the evidence is being compiled from after-the-fact forensics. Now, in this the Kenyan authorities are to be applauded for coming out and actually revealing what's going on. In the western world, there is too much of a tendency to hide behind "national secrets" and thus render outside scrutiny, the democratic imperative, an impossibility. One up for the Kenyans, let's keep this investigation transparent and before the courts.
Next (3). The theory predicts that follow the money is a useless tool.
Ambitham was in constant communication with slain lead attacker Ali Salim Gichunge, who died during the attack and his spouse Violent Kemunto Omwoyo.[Inspector] Githaiga yesterday said Ambitham’s phone led to his arrest on Tuesday after detectives established his communication with the Gichunges.
The police are following the social graph and arresting anyone involved. Having traced the phones, they then investigated the M-Pesa evidence, which provided many additional and interesting confirmatory facts.
Which is what they should do. But it was the contact information that cracked this case, not the financial flows. The contact information has always been available to them. And, where there is a credible case of terrorism as is in this case, the financial information has never been withheld. Again, the theory matches the evidence: follow the money is useless before the event, only confirmatory after the event.
Finally (4), the theory of unforeseen consequences says that the damage done by unintelligent responses will haunt the future of anti-terrorism efforts.
These are the agents that received the money, which was later withdrawn at the Diamond Trust Bank, Eastleigh branch, before it was wired to Somalia. ... The manager of the bank where Nur was withdrawing the money,, Sophia Mbogo, was arrested for failing to report Nur’s suspicious transactions. Nur is said to have made huge withdrawals in short intervals, which Mbogo ought to have reported to relevant authorities, but there is no indication she did so.
Without wishing to compromise the investigation - this looks inept. Eastleigh is the Somali district of Nairobi. It's a bustling centre of trade. In some respects the Somalis are better traders than the Kenyans, and a lot of trade is done. And a lot of that is in cash, because the Kenyan banking system is ... not responsive. Lots of legitimate cash would move in and out of that bank branch.
Given the alleged fact that the money man had 52 M-Pesa accounts, he was certainly aware enough to run under the radar of the branch. Thresholds and actions by banks are no secret, especially by those motivated by terrorism to conduct any crime to find out - bribery, extortion, kidnapping are options.
Maybe there is evidence that the branch or the manager is "in" on the deal. Or maybe there is not, and the Kenyan police have just confirmed the theory that FATF anti-terrorism will do more damage. They've sent a message to all branches to drown their customers in pointless compliance, and to not cooperate with the police.
The Kenyan police had better get a clear and undeniable conviction against the branch manager, or they are going to rue the day. The next terrorist attack will surely be harder.
October 21, 2018
ID Dox - now it's getting personal - Andreas spoofed
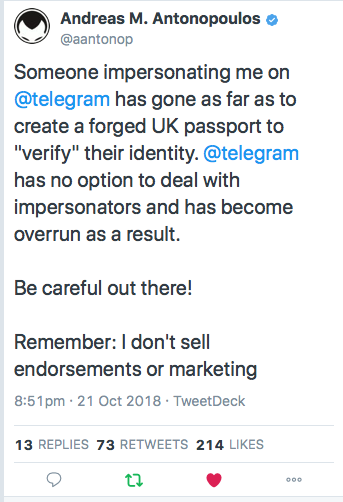 Writes Andreas Antonopolous, a noted Bitcoin commentator, that he has been impersonated with a mere scan!
Writes Andreas Antonopolous, a noted Bitcoin commentator, that he has been impersonated with a mere scan!
More than anything else this points at the fallacy of Identity Documents as the God of our Identity. AA may very well be a victim of our penultimate post on cheap-as-chips scans of your identity.
What's becoming clear is that identity is garnering more attention. Unwittingly, orgs and peoples who thought they had this under control are being dragged into the quagmire caused by firstly the Internet, then the upheavals caused by the great financial crisis and the drugs wars, and finally the devil of all devils, blockchain. Where will it end?
Meanwhile, here comes The Award-Winning David G.W. Birch @dgwbirch another understated twitter persona with slides and solutions for your identity:
The Award-Winning David G.W. Birch @dgwbirch A Short, Strategic Comment on Digital Identity by @chyppings #authentication #authorisation slideshare.net/15Mb/a-short-s… <- A short keynote for the Biometrics Congress in London. People liked it and asked for a copy so I've uploaded it to SlideShare.
I post this for debate not for endorsement ;-)
I'd also like to point out that it is unfortunate that <blockchain> is not a HTML entity, because that's what gets typed these days.
October 10, 2018
Market for Scans

That's the market for scanned passports, not scammed passports, but hey!
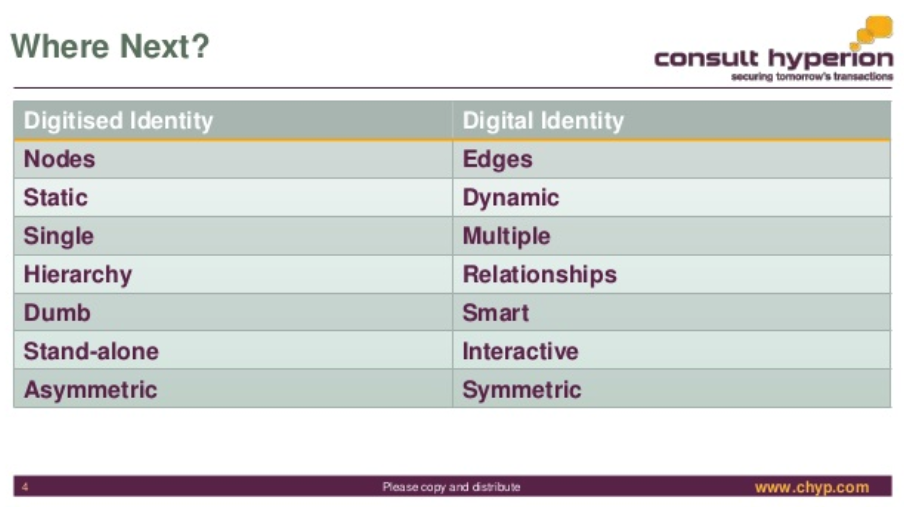
From comparitech comes research on what it takes to get digital scans for opening KYC/AML procedures - presumably bank accounts.
Here are our key findings:
- The average price of a digital passport scan is $14.71.
- If proof of address or proof of identification -- a selfie, utility bill and/or driver’s
- license -- is added to a passport scan, the average price jumps to $61.27.
- Australian passport scans were the most common, and yet, the most expensive ($32).
- The average price of a real, physical passport is $13,567.
- The average price of a counterfeit, physical passport is $1,478.
Aside from a lot of interesting detail on scans and templates, here's the real deal:
Authentic, state-issued passports are hard to come by and cost a lot, ranging from $8,216 (Germany) to $17,116 (UK). The average price of the eight supposedly genuine passports was $13,567. At least one vendor claims these passports came from "our corrupt immigration police contacts," though we have no way of verifying this. In many cases buyers are given the option to specify what details are included in the passport, including stamps for specific countries.
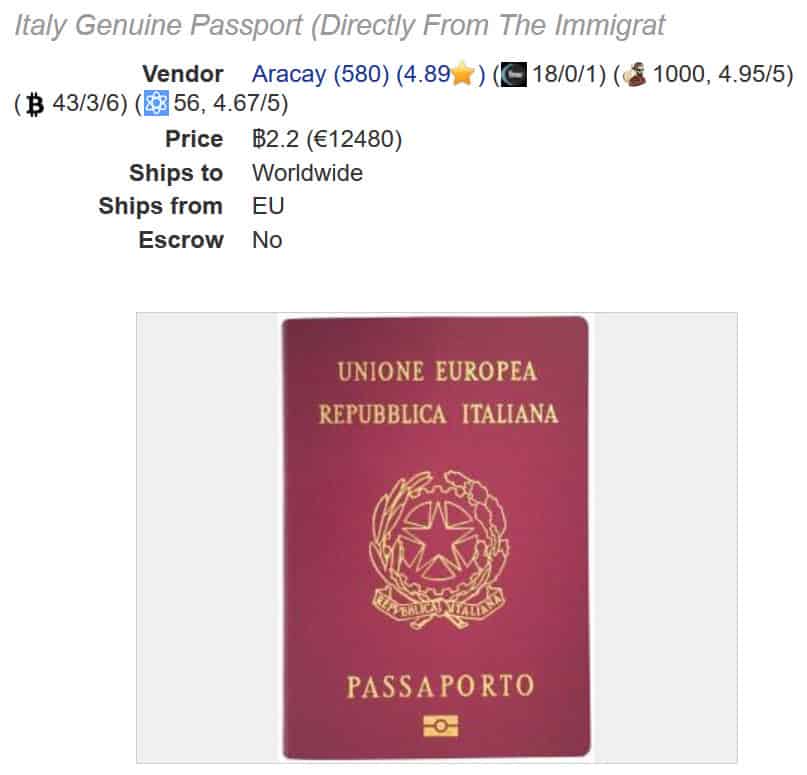
This puts a little more colour on the rough benchmark of a thousand per set - this might predict that any passport in such a deal needs to be a forgery. Or, I suspect there may be several distinct marketplaces - this research by comparitech was over "dark web" online interfaces where you as purchaser exchange your money for the goods/docs online, primarily with Bitcoin. Other research has worked with migrant channels where hard-at-luck locals are giving up their physical documents and reporting them stolen/lost.
Commentary on this will have to wait for another day.
June 26, 2018
Shocking trade in stolen UK passports (really??)
Readers in UK obviously don't read the blog, because the Daily Mail has just published the headline of ignorance:
Shocking trade in stolen UK passports: How gangs sell them for £2,500 – so criminals and terrorists can sneak in to the country
By TOM KELLY INVESTIGATIONS EDITOR IN ISTANBUL FOR THE DAILY MAIL
PUBLISHED: 22:43 BST, 24 June 2018 | UPDATED: 07:34 BST, 25 June 2018
Shocking? This trade has been going on since forever, but because it is in the interests of practically everyone to believe that ID documents are perfect, it doesn't make it past the editor's desk. Check the Identity Cost tag.The only news is that the price might have risen - £2500 is a lot more than the £1000 we are used to.
And in case anyone forgets, here's the rest of the Mail's shocking discovery of reality.
A disturbing trade in stolen British passports is exposed today by the Daily Mail.
Swiped by criminal gangs in Western Europe, they are flown to Istanbul or Athens for sale by people smugglers.
Security experts said owning a genuine British passport was like ‘winning the lottery’ for jihadis and criminals – allowing them to slip across borders undetected.
In response to the Mail’s findings, MPs called for action to address Britain’s ‘shocking vulnerability’ to potentially dangerous illegals.
Dozens of false documents seized by an organised crime unit in Greece, including hundreds of ID cards and scores of passports
Our investigation reveals that British citizens are selling their passports to be bought by migrants of similar appearance.
And fake EU identity cards that can be used to enter the UK are also being made to order within three days in the Balkans.
The Mail bought a UK passport for £2,500 from Abu Ahmad, a people-smuggling kingpin in Turkey. It had been stolen from a Milton Keynes man working in Brussels.
It was one of five passports that Ahmad, who is known as ‘The Doctor’, offered to the Mail.
The others included one stolen from an Oxford graduate visiting Paris and another taken from a 28-year-old Manchester woman who was on holiday in Spain.
Ahmad boasted that seven in ten of his clients succeed in duping immigration staff and making it to the UK.
He is on bail while he appeals against an eight-year sentence for spiriting thousands of migrants into Europe, including suspected jihadis. At its peak, his ‘business’ was bringing in £110,000 a month.
Europol, an EU police agency, warned yesterday that people smugglers operating in Turkey and Greece were ‘frequent’ offenders in the trade in black market documents, which is an ‘important enabler’ of organised crime.
Ahmad said all the passports he sold were genuine – otherwise they would be no use at border control.
They are either stolen or sold by their owners, who agree not to report them as missing for a few months, by which time they have been used by Ahmad’s customers.
He said: ‘Most British passports are stolen. Except if the passport was in the name of someone Arabic or Pakistani or something, that could have been sold.’
Ahmad said he had no qualms about profiting from stolen passports and, despite boasting he has smuggled thousands of people into Britain, insisted he was certain none of them were jihadis or criminals.
Abu Ahmad, who is known as ‘The Doctor’, helps smuggle people across the world by selling them stolen passports
But another Syrian immigrant in Turkey told the Mail at least two people Ahmad helped get into Europe were known Islamists operating in Damascus.
The German authorities were alerted about them after their arrival, he said.
Interpol, an international police agency, has a stolen and lost travel documents database, known as SLTD, which it says was searched more than 1.2billion times in the first nine months of 2016, providing 115,000 ‘hits’.
But on its website, it admits: ‘Interpol is not automatically notified of all passport thefts occurring worldwide, and the SLTD database is not connected to national lists of stolen or lost passports.
‘Despite the potential availability of the SLTD database, not all countries systematically search the database to determine whether an individual is using a fraudulent passport.’
For £7,000 Ahmad books his client a hotel room, gets them food and hands over a stolen passport. This is the full-service package, with the cheapest being just the passport for £2,500
In 2014, the head of the agency said just four in ten passports used for international flights were checked against the database.
Labour MP John Woodcock, a member of the Commons home affairs committee, said: ‘At a time when several hundred potentially highly dangerous jihadis have fled when Islamic State has been deposed it’s highly alarming to learn that this way of entering the UK illegally seems to be so readily available.’
Ed Davey, the Lib Dem home affairs spokesman, said: ‘Criminals who capitalise on the vulnerability of tourists and then profit off refugees and immigrants in desperate need of help must not be allowed to operate so freely.’
David Lowe, a former Special Branch counter-terrorism officer now based at Leeds Beckett University, said: ‘For terrorists and criminals getting a new passport is like winning the lottery.
‘It’s a significant concern with fighters coming from Islamic State or returning British fighters. Once you get in with somebody else’s passport you are very difficult to trace.’
One of the stolen passports used to help get people through passport control and across borders. The Daily Mail bought one from Ahmad in Istanbul for £2,500
Immigration minister Caroline Nokes said: ‘One hundred per cent of passports are inspected at the border.
‘Border Force officers are rigorously trained to prevent the holders of fraudulent documents from entering the country and between 2010 and March 2018, we denied entry to over 144,000 people.
‘Immigration Enforcement constantly monitors and identifies emerging threats in relation to the production and supply of false travel documents, including the use of the internet to facilitate the trade in passports and identity cards.
‘We have a range of interventions to target the criminals involved, including criminal prosecution of crime groups in the UK and overseas.’
April 19, 2018
How Refugees are reducing the cost of processing refugees - for around $2000
Der Spiegel online reports:
At some point Hassan Rahimi * wanted to go back, he tells it. Back to Syria , home, to his wife and two sons. They were starving in the devastated land. Rahimi saw himself as a refugee in Germany failed. The family he was not allowed to catch up, he did not get a job. The hopes that had led him to flee in early 2015 were dashed.And so the 35-year-old sat on a summer day 2017 in Berlin-Tegel in a plane to Thessaloniki, Greece. Once there, he entrusted himself to a smuggler. The man should take him to Turkey, the transit country - as if on the way there.
"Sell your papers!"
A refugee who has been recognized in Germany like Rahimi is not allowed to enter Turkey without further ado. And so the tug Rahimi even before the green border gave an advice: "Sell your papers!" The German documents, refugee card and refugee passport, the AOK card. To deny yourself if border guards suddenly turn up. And to make money.
Rahimi did as he was told. He sent the papers by post to his cousin, who lives in Leipzig. And he sold on to a stranger. For 1500 euros. Rahimi was later sent the sum. He was already back in Syria.
It's almost as if there is a law of identity documents - they work for the middle road of broad society but fail dismally at the edges. In this case, the desperate, but also the criminal, who are two separate classes merged into one in the fairyland fantasy of the bureaucratic mind.
The CDU interior politician Armin Schuster, chairman of the parliamentary control committee in the Bundestag, nevertheless calls sharp sanctions for fraudsters. "Every refugee who participates in a pass trade, has forfeited his right of residence," said Schuster the SPIEGEL. In this case, there must be "an accelerated form of deportation".
Yet - the broad swathe of comfortable society - they (we?) don't really need identity documents, because we already know each other and we already trade and we already have comfortable safe lives and we behave. Remember being taught not to steal as a child? You don't steal because of your identity documents, you behave because you're part of the community, and you want to remain part of the community.
Identity documents work for people who don't need them; they don't work for those that do. What is this product called in marketing or economic terms, the product that sells and works only for those who don't need it? A few terms come to mind: Vanity goods, marketing discrimination, security theatre, entrapment.
There are many discussions and conclusions we can draw from the story of refugees, but some are easy: the authorities will always say, our system is broken, bad people are doing bad things, we must try harder ! Bracelets, implants, biometrics, liveness detection, fingerprints, toeprints, roving police checks, cultural alignment testing! Meanwhile, only refugees will know that the recognition of status without humanity is no recognition. They will drift on in hope, as they are boxed into their new isolated, tolerated but despised class - like gypsies, never finding a real home, always despised.
Yet, perversely again, maybe in the breach we see the flaw:
The scam is therefore quite simple: Recognized in Germany refugees travel to Turkey. Somewhere along the way they sell their papers, apply for replacement at German consulates - if they want to return to their host country - or continue like Hassan Rahimi the journey to their homeland without documents.
Oh, the cunning devils at Der Spiegel - the real trade is different, and Rahimi's story is just to tug at the heart strings. Refugees are bringing back additional refugees!
Let's say the cost of formally processing a refugee through "the system" is X. And let's say the cost of informally running (a.k.a. smuggling) a new refugee through Greece is Y == €2000 = 3 flights + $1000 + the cost of replacement documents.
The cost of processing two refugees under this enhanced scheme is now to X + Y. The fact that refugees are doing this - bringing in new refugees and taking on the risk of right-wing outrage to boot is evidence that X is too high. This formula only works if X is very much greater than €2000.
To take a stab at that, I'll guess that the state's cost is around €100,000. To support that, if we go back to the start - the cost of Rahimi not finding a job is easily €20,000 or more. So, under these finger-in-the-air assumptions, the authorities have set the cost of processing a refugee too high, and therefore the system is breaking at the edges.
Assuming that Rahimi doesn't sell his papers to a terrorist (a vanishingly small probability) everyone wins under this scenario. The state saves $100,000 and the new refugee saves on a year of misery.
One may have moral views on the above - "it's just not right!!!" - but when the economy saves money, the economy follows the money. For more numbers and a slight segue:
Elsewhere, a potential salesman tells that he arrived in Turkey four days ago. "I have a residence permit for three years, with a passport and AOK card." If you are interested, the package of German papers for $ 1000 to have. It is crucial that the photo could be used on the documents. A buyer must look like him. Otherwise the danger would be too great to fly up with the papers..... There, people offered real passports from 500 euros, passes from 200 euros and driver's licenses from 150 euros.
Higher up, €1500 and here, $1000. I guess I've been tracking the cost of stolen documentation for a decade now, and it quickly settled around 1000 ($ € £). In the Spiegel article, we see it hasn't changed in a decade, which I find surprising. It suggests that nothing that has happened over the last decade has changed anything, at least in the supply versus demand.
ps: better translations welcome.
January 04, 2018
Hackers selling access to Aadhar
TRIBUNE INVESTIGATION — SECURITY BREACH
Rs 500, 10 minutes, and you have access to billion Aadhaar details
Group tapping UIDAI data may have sold access to 1 lakh service providers
Rachna Khaira
Tribune News Service
Jalandhar, January 3
It was only last November that the UIDAI asserted that “Aadhaar data is fully safe and secure and there has been no data leak or breach at UIDAI.” Today, The Tribune “purchased” a service being offered by anonymous sellers over WhatsApp that provided unrestricted access to details for any of the more than 1 billion Aadhaar numbers created in India thus far.
It took just Rs 500, paid through Paytm, and 10 minutes in which an “agent” of the group running the racket created a “gateway” for this correspondent and gave a login ID and password. Lo and behold, you could enter any Aadhaar number in the portal, and instantly get all particulars that an individual may have submitted to the UIDAI (Unique Identification Authority of India), including name, address, postal code (PIN), photo, phone number and email.
What is more, The Tribune team paid another Rs 300, for which the agent provided “software” that could facilitate the printing of the Aadhaar card after entering the Aadhaar number of any individual.
When contacted, UIDAI officials in Chandigarh expressed shock over the full data being accessed, and admitted it seemed to be a major national security breach. They immediately took up the matter with the UIDAI technical consultants in Bangaluru.
Sanjay Jindal, Additional Director-General, UIDAI Regional Centre, Chandigarh, accepting that this was a lapse, told The Tribune: “Except the Director-General and I, no third person in Punjab should have a login access to our official portal. Anyone else having access is illegal, and is a major national security breach.”
...
read more.
September 10, 2017
Syrian Passports in hands of ISIS
In the long running thread about controversial identification documents, RT reports:
German authorities believe that Islamic State terrorists have stolen over 11,000 blank Syrian passports, confidential documents seen by the Bild am Sonntag newspaper reportedly reveal. German Investigators have made a list of the serial numbers of the blank passports, the newspaper reported, citing confidential documents of the German Federal Criminal Police Office (BKA), the interior ministry and the country's federal police (BPOL).“According to BKA information, there are 11,100 Syrian blank passports… in the hands of the IS [Islamic State, also known as ISIS/ISIL],” the documents from the interior ministry reportedly state. In total, 18,002 blank Syrian passports were stolen from the Syrian government, Bild am Sonntag reported.
Developments in connection with the refugee question have shown that terrorist organizations are using the opportunity to infiltrate potential IS attackers into Europe undetected, a BKA official told the paper.
Fake or altered passports are mostly used “for illegal entry without further motives like carrying out a terrorist attack,” the official added.
According to the documents seen by Bild, at least 8,625 passports checked by German migration authorities in 2016 turned out to be counterfeits.
No news of prices.
June 16, 2017
Identifying as an artist - using artistic tools to generate your photo for your ID
Copied without comment:
Artist says he used a computer-generated photo for his official ID card
A French artist says he fooled the government by using a computer-generated photo for his national ID card.
Raphael Fabre posted on his website and Facebook what he says are the results of his computer modeling skills on an official French national ID card that he applied for back in April.

| Le 7 avril 2017, j’ai fait une demande de carte d’identité à la mairie du 18e. Tous les papiers demandés pour la carte étaient légaux et authentiques, la demande a été acceptée et j’ai aujourd’hui ma nouvelle carte d’identité française.
La photo que j’ai soumise pour cette demande est un modèle 3D réalisé sur ordinateur, à l’aide de plusieurs logiciels différents et des techniques utilisées pour les effets spéciaux au cinéma et dans l’industrie du jeu vidéo. C’est une image numérique, où le corps est absent, le résultat de procédés artificiels. L’image correspond aux demandes officielles de la carte : elle est ressemblante, elle est récente, et répond à tous les critères de cadrage, lumière, fond et contrastes à observer. Le document validant mon identité le plus officiellement présente donc aujourd’hui une image de moi qui est pratiquement virtuelle, une version de jeu vidéo, de fiction. | On April 7, 2017, I made a request for identity card at the city hall of the 18th. All the papers requested for the card were legal and authentic, the request was accepted and I now have my new French Identity Card.
The Photo I submitted for this request is a 3 D model on computer, using several different software and techniques used for special effects in cinema and in the video game industry. This is a digital image, where the body is absent, the result of artificial processes. The image corresponds to the official requests of the card: it is similar, it is recent, and meets all the criteria for framing, light, background and contrast to be observed. The document validating my most official identity is now an image of me that is practically virtual, a video game version, fiction. The Portrait, the photo booth and the request receipt were shown at the r-2 Gallery for the Exposition Agora |
The image is 100 percent artificial, he says, made with special-effects software usually used for films and video games. Even the top of his body and clothes are computer-generated, he wrote (in French) on his website.
But it worked, he says. He followed guidelines for photos and made sure the framing, lighting, and size were up to government standards for an ID. And voila: He now has what he says is a real ID card with a CGI picture of himself.
"Absolutely everything is retouched, modified, and idealized"
He told Mashable France that the project was spurred by his interest in discerning what's artificial and real in the digital age. "What interests me is the relationship that one has to the body and the image ... absolutely everything is retouched, modified, and idealized. How do we see the body and identity today?" he said.
In an email, he said that the French government isn't aware yet of his project that just went up on Facebook earlier this week, but "it is bound to happen."
Before he received the ID, the CGI portrait and his application were on display at an Agora exhibit in Paris through the beginning of May.
Now, if the ID is real, it looks like his art was impressive enough to fool the French government.
December 04, 2016
Fake US embassy provides full service
It's been a while since I've posted on the cost of false documents, perhaps because I've fooled myself into belief that everyone's got the message: you can pick a full set for about $1000.
But this one is more adventurous:
In Accra, Ghana, there was a building that flew an American flag outside every Monday, Tuesday, and Friday, 7:30 a.m.-12:00 p.m. Inside hung a photo of President Barack Obama, and signs indicated that you were in the U.S. Embassy in Ghana. However, you were not. This embassy was a sham.It was not operated by the United States government, but by figures from both Ghanaian and Turkish organized crime rings and a Ghanaian attorney practicing immigration and criminal law. The "consular officers" were Turkish citizens who spoke English and Dutch. For about a decade it operated unhindered; the criminals running the operation were able to pay off corrupt officials to look the other way, as well as obtain legitimate blank documents to be doctored.
....
The sham embassy advertised their services through flyers and billboards to cultivate customers from Ghana, Cote d'Ivoire, and Togo. Some of the services the embassy provided for these customers included issuance of fraudulently obtained, legitimate U.S. visas, counterfeit visas, false identification documents (including bank records, education records, birth certificates, and others) for a cost of $6,000.
There's no indication as to why it took a decade to find, nor whether the documents were good enough to fool.
Nor is there any indication in the article as to what $6k buys you - and $6000 does seem to be an outlier.
Most of the prior information I have collected suggests $1000 gets you the set. It's important to know the number, roughly, because it sets the bar as to how much security we can expect from the identity documents provided by the state. Whether $1k or $6k is a low bar or a high bar depends, but what is the case is that there is a bar, above which we can expect criminals to leap for profit.
August 13, 2015
Fake Ids - comprehensive prices
 When I was at CAcert, one of the risk analysis questions was how much it costs to provide a fake set of Identity documents. So I started collecting public references to that, and fairly quickly came up with a number -- 1000 as the cost for a good set.
When I was at CAcert, one of the risk analysis questions was how much it costs to provide a fake set of Identity documents. So I started collecting public references to that, and fairly quickly came up with a number -- 1000 as the cost for a good set.
That's a great number as a rule of thumb for risk analysis -- don't build a system that spends 10,000 to protect something that can be stolen for a tenth of that.
Now (via Zerohedge) someone else has picked up my slack and published a lot of info on this cost. Here comes Havocscope!
Prices of Stolen Passports and Fake IDs
Average Price of a Stolen Passport for Sale $3,500 Black Market Driver License – New Jersey $2,500 to $7,000 Black Market Passport – Nepal $6,961 Black Market Passport – Peru $1,750 Black Market Passport – Sweden $12,200 Black Market Passport and Visa – Australia $15,000 Blank Stolen Passport – UK $1,642 Fake Green Card $75 to $300 Fake Birth Certificate – Cuba $10,000 to $50,000 Fake Car License Plate in Cambodia $4.50 to $10 Fake Driver License – California $200 Fake Driver License – Confiscated in New York 1,450 in 2012 Fake ID Card – Malaysia $771 (includes smuggling) Fake ID Card – New York $160 in 90 min Fake ID Confiscated – Arizona 2,064 from students in 2010 Fake ID Confiscated from China 1,700 in 3 months at one airport Fake ID from China $300 for 1, $400 for 2 Fake ID Papers for Residency – USA $2,500 per set Fake IDs for Sale – United States $0.1 Billion ($100 Million) Fake Passport – Australia $806 Fake Passport – China $10,000 to $25,000 Fake Passport – China (Alter Photo) $3,500 to $5,000 Fake Passport – Egypt, Germany, Morocco $6,830 to Syrian Refugees Fake Passport in Thailand – Basic $245 in 2 hours Fake Passport in Thailand – Higher Quality $1,000 to $1,250 Fake Passports in India $294 Fake Social Security Card $75 to $300 Lost or Stolen Passport Reported 11 Million in 2010 Passport Selling – Thailand $200 Stolen ID to buy Health Insurance $1,250
At this stage I can hang up my hat - these guys are doing a better job. But before I retire, I might ask one question - what's up with Cuba? Why does a false birth certificate cost so much? And, they have the answer:
Price to Get a Fake Birth Certificate from CubaA man in the US State of Florida was selling counterfeit Cuban birth certificates to illegal immigrants in the United States. Due to US immigration policy, Cuban nationals are able to apply for a green card after one year of being in the country.
The man was selling fake Cuban birth certificates to migrants from Argentina, Colombia, Costa Rica, El Salvador, Mexico, Peru and Venezuela. Each migrant was already in the United States illegally, and paid between $10,000 to $50,000 for the fake documents. By possessing the fake Cuban birth certificates, the migrants attempted to pass off as Cuban nationals to US immigration officials.
According to court documents, the man sold around 50 fake birth certificates and made over $500,000.
Answered! Looks like I'm out of a job! Maybe I should take up forging Cuban birth certificates... Or, go chase these guys who organised a hit in Bahrain using false ID:

The price of a hit is also tracked by Havocscope, but now we're getting off track.
March 16, 2013
It all started as a noble idea - Identity Cards in Uganda
 Another in an occasional series addressing the cost of identity. It turns out that Uganda has so far spent a whopping 600 million shillings per identity card, as reported by Nicholas Kalungi:
Another in an occasional series addressing the cost of identity. It turns out that Uganda has so far spent a whopping 600 million shillings per identity card, as reported by Nicholas Kalungi:
It all started as a noble idea. Every Ugandan holding a National Identity Card (NIC) that would be acceptable for elections, to financial institutions, travel within East Africa and more. A decade down the road, with about Shs240 billion spent, only 401 identity cards have been issued. Uganda is a country of about 33 million people.
Even converted to USD, that turns out to be $226,642 per card. Oh, and:
Also of concern is the fact that the ID cards yet to be issued is will use barcode technology instead of the smartcard technology that uses a chip.A chip can accommodate a lot more information, such as medical records, criminal records, educational data, driving permits and social security data. It can also authenticate fingerprints and photographs, which are additional safeguards against forgery. Blank ID cards using the barcode technology will cost the government 22.5 million euros (Shs63 billion) for 15 million cards, amounting to $2 per card.
This sounds like one of those frequent cases of inept importing of western notions -- bad enough in their own territory, where the sole justification turns out to be "we can afford it" -- into places where it enters the realm of fantasy.
In somewhat proof of this, the market has responded:
Thousands of Ugandans have resorted to using local council (LC) stamped identification cards (IDs) as national IDs.This comes at the back of the government’s failure to implement the national ID project that would enable citizens have a uniform identification document. For a decade now, the national ID project has been mired in corruption allegations and internal fights over who should be in charge of the multi-billion shilling project.
The multiple delays in the national ID project have left people with no alternatives save for exploiting alternatives and creating their own IDs-labeling them as “Citizens” identifications. One of the booming businesses on the streets of Kampala, taxi parks and at local council offices across the country is making, selling and issuing IDs.
A week-long investigation around Kampala showed that these IDs are of two types. One type bears the word ‘Resident’ on the cover while another brand bears the word ‘Citizen’ on the cover. They are mainly made at Nasser and Nkrumah roads in Kampala.
Several centres along these Streets are famous for originating all sorts of fake documents that include, among others, academic certificates ranging from bachelor’s degrees, diplomas and of recent PhDs. The wholesale price range for ‘’Citizen” and “Resident” IDs are between Shs300 and Shs1, 000.
After buying the card from Nasser Road or any other outlet, you get a passport photo and take it to a local council official who at between Shs3,000 and Shs20,000 approves and stamps it to confirm that you are a citizen of Uganda or a resident of a given area.One John Muyomba, a resident of Kasubi, tells this newspaper that he acquired a citizens ID from his local chairman a year ago and it has been doing wonders for him following the expiry of his university ID. “I paid Shs5,000 and took two passport size photos. I presented a friend at the LC office as a referee and got the ID. ...
At around 2600 shillings to the USD, we are looking at from $1 to $4 for the card, and $12 to $80 or so for the certification. Now divide those numbers by the average daily wage -- about $1 -- to get a view as to their purchasing-power-parity cost.
Prone to abuse
For one to get this acquired ID stamp, all they need is a person to recommend them to an LC leader that he/she is a resident of an area. “We always ask the person seeking our approval to come with a resident of the area to prove that they are Ugandans or resident of that area,” says Bright Kashaka, an LC chairperson in Kisenyi, a Kampala suburb.When this reporter visited a local council office in an area he neither works from nor resides, he was told by the people he found at the office to pay Shs10, 000 and present a passport photo after which he would have one ID issued. From this discovery, it became clear that you only need to have money and passport size photos to a citizen or resident ID.
What's going on here is that the market for documents has stepped in to provide the physical carrier, and the market for local councils has stepped forth to provide the certification. This seems like an efficient solution, especially when we factor in the experience of government-led production experiments.
Curiously, it also makes the case that an ID of any form is a good thing, as shown by the thriving market, evidencing demand from somewhere.
"...It is this ID that I used to register my Sim card and to get an account at one of the banks,” says Muyomba. While, these IDs seem to be serving different purposes, for example, local identification and Sim card registration, among others, the ease at which they are acquired, stamped and issued is worrying.
Worrying? For those who suffer angst from any free-market solution, the trick is to see free-market identity cards as an intermediate between nothing and some hypothetical perfect identity proof. Of course, all forms of identity documents are just that, an intermediate between nothing and perfection, so the argument turns on whether the market can do a better or worse job, for more or less money, than say a given government endeavour.
In Uganda, the answer is strongly in favour of the market.
However, if you are good with numbers, one observation must strike out and slap at the face: why is the cost of the Local Council certification so high? At from 3000 to 20000 shillings, that translates to from one to eight day's worth of average earnings.
The answer is almost certainly corruption. The fact that there are variable prices is a bit tip-off, and the indication of a special price for a newcomer is a dead giveaway. There may, or may not be a local government listed price for the certification, as that is not evidenced in these articles, but any variation of that base price is likely going straight into the pockets of the corrupt local government officials.
If we take the 3000 as a base price, this indicates that corruption is many times more than the honest LC cost-based price alone.
And it is this factor that slows these countries down. Corruption, created almost universally by government mandate. (Effects of corruption in Ghana.) In this case the local council monopoly on certifications, makes the cost of business far higher than it is in western countries, when converted to PPP numbers. And now we find the incestuous circle of government intervention leading to this corruption:
Lately, telecommunications companies and Uganda Communications Commission (UCC) have been blaming the absence of national IDs as the main challenge affecting the on-going Sim card registration process. Even though the process has been extended untill August, millions are still unregistered and the main reason cited is absence of recognised identification mainly in rural areas that are mandatory before anyone registers a Sim card. The effort to procure national IDs has been on for since 2001.
 The requirement for LC-stamped Ids is driven by ... government rules for SIM registration. In what is a widely acknowledged economic miracle -- the rollout of unidentified cell phones across Africa -- someone, somewhere has decided we need identity for each user of a cell phone. Thus putting the brakes on the one thing that Africa got right.
The requirement for LC-stamped Ids is driven by ... government rules for SIM registration. In what is a widely acknowledged economic miracle -- the rollout of unidentified cell phones across Africa -- someone, somewhere has decided we need identity for each user of a cell phone. Thus putting the brakes on the one thing that Africa got right.
What's the benefit to slowing down Africa's economic miracle? Why do we want to slow down the ability of locals to afford necessities like mosquito nets? If we dig a little deeper, it will almost certainly evidence itself once again: inept importation of bad Western notions into a place where they simply make no sense. Which will continue until the locals get a clue:
Until the production and selling of fake IDs is made illegal however, the different between a non-citizen, foreign and criminal holding the fake IDs is only a stamp hit.
These western notions are so easy to believe, and so very wrong.
October 26, 2011
Phishing doesn't really happen? It's too small to measure?
Two Microsoft researchers have published a paper pouring scorn on claims cyber crime causes massive losses in America. They say it’s just too rare for anyone to be able to calculate such a figure.Dinei Florencio and Cormac Herley argue that samples used in the alarming research we get to hear about tend to contain a few victims who say they lost a lot of money. The researchers then extrapolate that to the rest of the population, which gives a big total loss estimate – in one case of a trillion dollars per year.
But if these victims are unrepresentative of the population, or exaggerate their losses, they can really skew the results. Florencio and Herley point out that one person or company claiming a $50,000 loss in a sample of 1,000 would, when extrapolated, produce a $10 billion loss for America as a whole. So if that loss is not representative of the pattern across the whole country, your total could be $10 billion too high.
Having read the paper, the above is about right. And sufficient description, as the paper goes on for pages and pages making the same point.
Now, I've also been skeptical of the phishing surveys. So, for a long time, I've just stuck to the number of "about a billion a year." And waited for someone to challenge me on it :) Most of the surveys seemed to head in that direction, and what we would hope for would be more useful numbers.
So far, Florencio and Herley aren't providing those numbers. The closest I've seen is the FBI-sponsored report that derives from reported fraud rather than surveys. Which seems to plumb in the direction of 10 billion a year for all identity-related consumer frauds, and a sort handwavy claim that there is a ration of 10:1 between all fraud and Internet related fraud.
I wouldn't be surprised if the number was really 100 million. But that's still a big number. It's still bigger than income of Mozilla, which is the 2nd browser by numbers. It's still bigger than the budget of the Anti-phishing Working Group, an industry-sponsored private thinktank. And CABForum, another industry-only group.
So who benefits from inflated figures? The media, because of the scare stories, and the public and private security organisations and businesses who provide cyber security. The above parliamentary report indicated that in 2009 Australian businesses spent between $1.37 and $1.95 billion in computer security measures. So on the report’s figures, cyber crime produces far more income for those fighting it than those committing it.
Good question from the SMH. The answer is that it isn't in any player's interest to provide better figures. If so (and we can see support from the Silver Bullets structure) what is Florencio and Herley's intent in popping the balloon? They may be academically correct in trying to deflate the security market's obsession with measurable numbers, but without some harder numbers of their own, one wonders what's the point?
What is the real number? Florencio and Herley leave us dangling at that point. Are they are setting up to provide those figures one day? Without that forthcoming, I fear the paper is destined to be just more media fodder as shown in its salacious title. Iow, pointless.
Hopefully numbers are coming. In an industry steeped in Numerology and Silver Bullets, facts and hard numbers are important. Until then, your rough number is as good as mine -- a billion.
November 15, 2010
The Great Cyberheist
 The biggest this and the bestest that is mostly a waste of time, but once a year it is good to see just how big some of the numbers are. Jim sent in this NY Times article by James Verini, just to show that breaches cost serious money:
The biggest this and the bestest that is mostly a waste of time, but once a year it is good to see just how big some of the numbers are. Jim sent in this NY Times article by James Verini, just to show that breaches cost serious money:
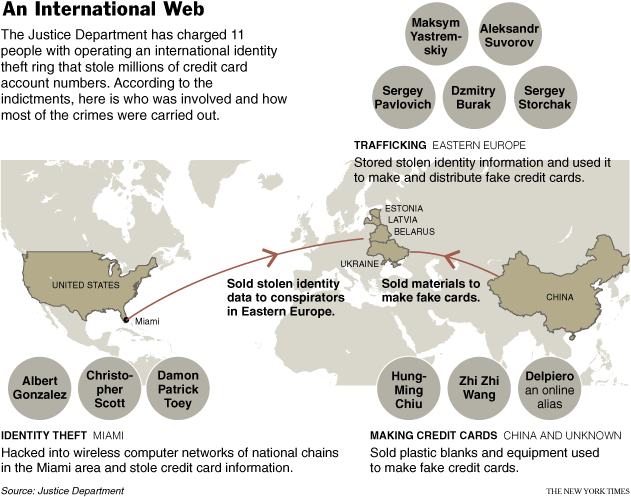
According to Attorney General Eric Holder, who last month presented an award to Peretti and the prosecutors and Secret Service agents who brought Gonzalez down, Gonzalez cost TJX, Heartland and the other victimized companies more than $400 million in reimbursements and forensic and legal fees. At last count, at least 500 banks were affected by the Heartland breach.
$400 million costs caused by one small group, or one attacker, and those costs aren't complete or known as yet.
But the extent of the damage is unknown. “The majority of the stuff I hacked was never brought into public light,” Toey told me. One of the imprisoned hackers told me there “were major chains and big hacks that would dwarf TJX. I’m just waiting for them to indict us for the rest of them.” Online fraud is still rampant in the United States, but statistics show a major drop in 2009 from previous years, when Gonzalez was active.
 What to make of this? It may well be that one single guy / group caused the lion's share of the breach fraud we saw in the wake of SB1386. Do we breathe a sigh of relief that he's gone for good (20 years?) ... or do we wonder at the basic nature of the attacks used to get in?
What to make of this? It may well be that one single guy / group caused the lion's share of the breach fraud we saw in the wake of SB1386. Do we breathe a sigh of relief that he's gone for good (20 years?) ... or do we wonder at the basic nature of the attacks used to get in?
The attacks were fairly well described in the article. They were all through apparently PCE compliance-complete institutions. Lots of them. They start from the ho-hum of breaching the secured perimeter through WiFi, right up to the slightly yawnsome SQL injection.
Here's my bet: the ease of this overall approach and the lack of real good security alternatives (firewalls & SSL, anyone?) means there will be a pause, and then the professionals will move in. And they won't be caught, because they'll move faster than the Feds. Gonzalez was a static target, he wasn't leaving the country. The new professionals will know their OODA.
Read the entire article, and make your own bet :)
November 06, 2010
I am Spartacus! and other dramatic "Identity" scripts
Name collisions are such fun! The apocryphal story of the Spartacus, the slave-turned-revolutionary, has him being saved by all his slave-warriors standing up saying, "I am Spartacus!" The poor Roman Leaders had little grip on the situation, as they couldn't recall any biometrics for the guy.
A short time ago, I wondered into an office to get some service, and a nice lady grabbed me at the door, entered my name in and eventually queued me to a service desk. The poor woman at the computer couldn't work it out though, as having entered my first name into the computer, all the details were wrong. It was finally resolved when an attendant 2 desks away asked why she'd opened up his client's file ... who had the same first name. Apparently, my name is subject to TLCs, three-letter-collisions...
Luckily, that was easy to solve. My 4-letter name reduces to around 2 people in our field. Hopefully, this is all resolved in a seminal paper on the subject:
Global Names Considered Harmful by Mark Miller, Mark Miller, and Mark Miller
As reported by Bill Frantz, that's the paper.
Meanwhile, if you want to purchase one of these fabulous global names, some prices spotted a while back: As reported by Dave Birch somewhere, and I only copied this one line (before the link went south):
Authorities said Lominy charged $1,600 to $2,000 for a state driver's license...
And (this time with the link still working):
The gangs are setting up fake-ID factories using printers bought at high street shops. The Met has shut at least 20 “factories” in the last 18 months and believes more than 30,000 fake identities are in circulation.Police examined 12,000 of them and established they were behind a racket worth £14 million. One £750 printer was withdrawn from sale at PC World after detectives revealed it could produce replicas of the proposed new ID card and EU driving licences.
...
Mr Mawer added: “There are people with dual identities, one real and one for committing crime.” He revealed that specialist printers capable of making convincing ID documents such as EU driving licences could be bought for £750, though others cost £5,000.
I'm currently trying to get my drivers licence back, and so far it has cost $465, with more costs to come. At some point, the above deal looks good, and they throw in a free printer! A steal :)
Speaking of "Identity" I also watched a British drama of that name tonight. In true form, it's "gritty police drama," which is to say, a copy of a dozen other shows which make a habit of implausible scripts woven around too many cross-overs.
September 01, 2010
profound misunderstandability in your employee's psyche
Speaking of profound misunderstandings, this:
BitDefender created a "test profile" of a nonexistent, 21-year-old woman described as a "fair-haired" and "very, very naïve interlocutor" -- basically a hot rube who was just trying to "figure out how this whole social networking thing worked" by asking a bunch of seemingly innocent, fact-finding questions.With the avatar created, the fictitious person then sent out 2,000 "friendship requests," relying on the bogus description and made-up interests as the presumptive lure. Of the 2,000 social networks pinged with a "friendship" request, a stunning 1,872 accepted the invitation. And the vast majority (81 percent) of them did it without asking any questions at all. Others asked a question or two, presumably like, "Who are you?" or "How do I know you?" before eventually adding this new "friend."
...
But it gets worse. An astonishing 86 percent of those who accepted the bogus profile's "friendship" request identified themselves as working in the IT industry. Even worse, 31 percent said they worked in some capacity in IT security.
May 18, 2010
advertising fake passports and other puzzles?
Well.... as frequent readers know, I collect data on how much it costs to purchase a set of Identity documents. I do this so that we know what the rough barrier to totally breaching the so-called "Identity Requirement" costs. So that we can feed that number into our construction of security models, and not get caught out.
In short, my research suggests strongly that the cost is about a thousand, in any of the major currencies.
Some reader in that business has just fed a comment into a post, advertising exactly that. My first thought was to remove it, as I don't like spam and adverts on the site ... but it is precisely on topic! In the spirit of research and data collection, I went to the site (which is at fake passports dot eu) and it has these prices, in Euros:
Australia 800 Austria 900 Belgium 800 Canada 900 Finland 900 France 900 Germany 1000 Israel 700 Malaysia 700 Netherlands 800 New Zealand 800 South Africa 700 Switzerland 1200 UK 1000 USA 1100
I'm guessing that site will be complained about soon enough, and they'll lose their domain, so I've collected the prices quickly.
Which, ruminating over ones morning coffee, as one does, does rather lead to some dilemmas, rather! Is advertising such fake goods against some law, somewhere? Possibly, but advertising is more a problem of pressure than law, as generally, making and selling fake goods is a fraud against the owner of the real ones. The problem with accepting the anti-advertising argument is that it then allows the owners of the real goods to perpetuate a type of deception on the buyers: that the goods are unfakeable, which becomes a serious deception on those who are reliant on the goods.

Alternatively, who does one complain to? One cannot complain to ones local bobby, because he wouldn't know what to do or who to talk to. He's probably unaware of why such a thing is useful, having likely not gone further than Costa del Sol, with his s/o. No such luck at the Federal level, either, because almost certainly they have no jurisdiction, the shop being in some other country. A bit of a central flaw in the whole passport concept, really.
There isn't a sort of global passport policeman, because this is one of those odd areas where each country maintains its own sovereignty, with ferocity, not withstanding their lack of sovereignty in any place the passport is likely to be used.
However, it has been pointed out in the past that people who don't like these fake passports, among other troubling truths found on this site, are watching this site! Aha! Problem solved, so this is perhaps the fastest way to report to all.
 Another problem. We don't know if the goods are real, or a setup to shake out lightweight players. Given that in some countries, the practice of entrapment is considered legal, and evidence derived from entrapment might be entertainable in court, it's not clear how the hapless customer would prove the quality of the wares, before purchasing. At least, none of my readers will take that risk, and especially considering the path beaten by Shahida for Panorama. Good work, that!
Another problem. We don't know if the goods are real, or a setup to shake out lightweight players. Given that in some countries, the practice of entrapment is considered legal, and evidence derived from entrapment might be entertainable in court, it's not clear how the hapless customer would prove the quality of the wares, before purchasing. At least, none of my readers will take that risk, and especially considering the path beaten by Shahida for Panorama. Good work, that!
Finally, for those who've read this far and are looking for the really interesting question, it is this: is the variation of prices seen above a result of supply factors or demand factors?
Now back to your normal channel...
February 15, 2010
The cost of playing red-footed football for European top-league clubs
 An article in the Dutch paper NRC Handelsblad reveals that
An article in the Dutch paper NRC Handelsblad reveals that
A classified Dutch government report has revealed that criminals stole 341,956 passports, identity cards, visa stickers and drivers' licences from European government facilities since 2000.
OK! That would be 34k per year across Europe. It states that purchasers
are willing to pay increasingly high prices for travel documents and passports," the report states. Depending on the country and the type of document sought, prices are said to vary from 500 to 11,000 euros .
That's for documents based on stolen-as-blank European documents (which supports our rule of thumb: 1,000 euros for a good set). Later on the article gives one estimate of costs (to us) or profits (to crooks):
"The damages incurred can amount to at least a hundred times the prices paid for these documents." A couple of years ago, Dutch customs officials estimated that in the Netherlands alone, fraud committed using forged proof of identity cost three billion euros annually.
If one guesses say a tenth of the numbers for Netherlands alone (finger in air, divide European numbers above by 11), then each year, 3000 good identity documents are selling into the Netherlands and chasing 3 billion euros of fraud. That's 3 million bux per identity sale .
That's serious money. This is for the real item, and only the printing would give them away on inspection, which makes those numbers useful. Here's more information.
To combat the abuse of stolen documents, customs offices protecting the Schengen area's outer borders have the so called Schengen Information System (SIS) at their disposal. The SIS lists not only all persons and vehicles wanted by law enforcement in countries party to the Schengen treaty, but also contains data on all blank travel documents that were stolen or went missing from government facilities there. According to the Dutch police, the database contains 341,956 documents in all. However the SIS is not consulted with every entry into the EU.
So the headline 3.4m over Europe, the 2000s decade, would be a floor rather than ceiling. Another remarkable pointer in the article:
The report, entitled Report on Security norms for Diplomatic Posts, lists numerous European embassies and consulates that were robbed around the turn of the century by Eastern and Central European "crime syndicates", bagging large numbers of passports and visa stickers in the process.The gangs "occasionally used extreme violence" to gain access to the "poorly secured" diplomatic posts, the report states. The gangster were privy to "know-how and techniques used by former intelligence agencies". Netherlands, Spain, Austria and Portugal ... Vienna, Geneva, Lausanne, Brussels and other locations. The crime spree was kept under wraps at the time, but the thefts were recently confirmed by the foreign ministry at NRC Handelsblad's request.
Which would point the finger at organised crime. Which means it is serious, it is working, it is making money, and it isn't going away. Add to that observation the above 3 million profit number, and now we something serious: That's a trend we can rely upon .
Who are likely customers? The report lists the usual grab-bag of scumbags & losers such as "criminals, human traffickers and illegal asylum seekers," terrorist(s):
Stolen Belgian passports were used by Abdessatar Dahmane and an accomplice in September 2001 to pose as journalists and gain access to Ahmed Shah Massoud, the leader of Afghanistan's Northern Alliance, and kill him in a suicide bombing.
And this odd one:
Brazilian football star Leonardo Santiago was caught red-handed in 2000 when his Portuguese passport proved to be a fake. The 17-year-old darling of Rotterdam's Feyenoord team had thus been able to circumvent the strict regulations that apply to all non EU-citizens playing for European football clubs.The story is by no means unique in European football. In recent years, law enforcement officials in France, Italy and Spain have caught dozens of 'Leonardos', playing for clubs like Inter Milan, Lazio Roma, AS Monaco and Saint-Etienne.
Shouldn't that be "caught red-footed" ? Joking aside, what exactly is the harm here?
Teams and players alike benefited from the fraudulent documents. In France and Italy, regulations only allow clubs to field a limited number of non-EU players. In the Netherlands, the same foreign nationals can only be signed if they are paid at least 503,000 euros annually.
Exactly. One presumes there is no serious cost to society to fielding a footballer of the wrong colour in a game. Lumping mass entertainment in with serious crime is a misuse of police resources, and we'd rather they be chasing those real criminals mentioned earlier, and now here:
 |
| Police in Dubai have issued arrest warrants for 11 suspects they want to question about the killing of a senior Hamas official in Dubai. The suspects include six men travelling on false British passports. |
 |
October 16, 2009
Chip & pin fallacies
We often print numbers reported in the press and other places, because sometimes these are useful for dealing with the fantasies and fallacies common in this world. I wish they were more used! Stephen Mason and Roger Porkess have just published an article full of such numbers on British chip&pin, and done in a fairly scientific survey fashion:
The findingsForty-six respondents had been contacted by their banks, many of them several times. Most of the transactions had in fact been authorised, but 11 of the 46 people had been contacted about unauthorised transactions. Of the 11 with unauthorised transactions, three could explain them as security lapses (typically losing the card) but nine could not (one person was in both categories).
The survey then went on to ask about unauthorised withdrawals; these cases had not been detected by the banks' detection software. Twenty-one people had had unauthorised withdrawals. Of these nine people could explain them as security lapses and 13 could not (again one person was in both categories).
What this article lays to rest is whether there is any possibility of fraud and breach of the security in the Chip & pin system. Clearly yes: depending on how you view the numbers, the possibility of a person experiencing an "unexplainable" breach is between a lower bound of 6% and an upper bound of 20%.
The total of 29 unexplained attacks were reported by 16 individuals from the 80 respondents. This would suggest a probability of one in five, that a randomly selected individual has experienced an attack.There are two problems with this estimate. If all those who did not return the questionnaire had nothing to report, the probability would reduce to about one in 16. More importantly, the claimant is not a randomly selected individual but one of a very small group of people involved in such cases. However, the importance of this probability is not its actual value, but that it is not zero. Such attacks can happen, and so it is entirely possible that the claimant is telling the truth.
That is a stunning amount of fraud. Another observation made by the article is how efficacious are the bank's systems. Working backwards from the respondents' numbers, it is suggested that:
These figures show that the banks take measures to detect unauthorised transactions, but that their processes are still not very effective. They suggest that only about half of unauthorised transactions are detected in advance; however, to achieve even that level of success, a large number of transactions are investigated, about 90% of which are authorised.That the banks are prepared to bear the considerable costs that are involved in the process of carrying out checks in this manner could be taken as an indication that they recognise that a security problem exists.
What is the point of all this? It is because of a rather stunning observation made in a court in a recent case:
In his judgment, Judge Inglis stated, at [20]: "...that the absence of a history of successful fraudulent attacks on online chip and PIN transactions, and the absence of any evidence of systems failure, as showing that these were transactions that can be taken at face value...are important pieces of evidence from which it is open to the court to draw the inference that these were transactions that took place using Mr Job's card and his PIN."
The authors suggest this as a case of the Prosecutor's fallacy: whether the event happened or not is the same question as whether the person holding the card is innocent or not. I'm not sure I quite follow what this means, but it seems to mean that there is a presumption being made that if the event happened, the cardholder was responsible. But, there are other possibilities:
A thief has stolen the money from the bank following a breach of the card's security.A thief has stolen the money without a breach of the card's security.
The claimant is making a dishonest claim.
The bank has made an error.
And this is what the survey attempts to predict. So the bank in question, Halifax, successfully made the case that there was nothing in wrong with the security of their systems. If there was a fraud, it was caused by the cardholder, in some way or other.
I've worked in this field for a bank, doing smart card work, and I can offer the following observation. During my time there, a stunning piece of open academic work swept through the crypto world and destroyed the "perfect security" belief in the bank's systems. Yet, the bank did not respond, at all. I investigated this, and discovered that there were in fact two beliefs. The bank on the whole believed there was perfect security, but the core security team knew it was not true (and indeed knew about the research for some 5-10 years).
There was cognitive dissonance between a small core group of experts, and the wider bank. Every conversation between the two groups was characterised by careful choice of wordings to allow the beliefs to co-exist in harmony. So consequently, although the academic work was on the face of it highly threatening, it achieved nothing. The two beliefs separated briefly in the face of this evidence, then bypassed it, one each side, and rejoined on the other side. Harmony was restored.
So I would say that the Halifax believes its systems secure, and was able to present enough evidence or absence of evidence to sway the court. However the trick of asking the right person in the Halifax was probably not tried (and of course this is quite problematic, because you need to know who it is, and how to get them to open up, *and* get them to court). We in the security field know that there is a lot of fraud there in chip & pin, but it is only with serious evidence at hand -- this survey for example -- that we can start to attack the castle of convenient beliefs.
Another curious thought of mine: Chip&pin is more risky than cash! In fact, I'm trying to think when was the last time I heard of someone being robbed of cash. I don't mean the Swedish helicopter heist of September, I mean pick-pockets, muggings, etc. So far, I'm thinking zero risk, but maybe that's just cognitive dissonance?
October 01, 2009
Man-in-the-Browser goes to court
Stephen Mason reports that MITB is in court:
A gang of internet fraudsters used a sophisticated virus to con members of the public into parting with their banking details and stealing £600,000, a court heard today.Once the 'malicious software' had infected their computers, it waited until users logged on to their accounts, checked there was enough money in them and then insinuated itself into cash transfer procedures.
(also on El Reg.) This breaches the 2-factor authentication system commonly in use because it (a) controls the user's PC, and (b) the authentication scheme that was commonly pushed out over the last decade or so only authenticates the user, not the transaction. So as the trojan now controls the PC, it is the user. And the real user happily authenticates itself, and the trojan, and the trojan's transactions, and even lies about it!
Numbers, more than ordinarily reliable because they have been heard in court:
'In fact as a result of this Trojan virus fraud very many people - 138 customers - were affected in this way with some £600,000 being fraudulently transferred.'Some of that money, £140,000, was recouped by NatWest after they became aware of this scam.'
This is called Man-in-the-browser, which is a subtle reference to the SSL's vaunted protection against Man-in-the-middle. Unfortunately several things went wrong in this area of security: Adi's 3rd law of security says the attacker always bypasses; one of my unnumbered aphorisms has it that the node is always the threat, never the wire, and finally, the extraordinary success of SSL in the mindspace war blocked any attempts to fix the essential problems. SSL is so secure that nobody dare challenge browser security.
The MITB was first reported in March 2006 and sent a wave of fear through the leading European banks. If customers lost trust in the online banking, this would turn their support / branch employment numbers on their heads. So they rapidly (for banks) developed a counter-attack by moving their confirmation process over to the SMS channel of users' phones. The Man-in-the-browser cannot leap across that air-gap, and the MITB is more or less defeated.
European banks tend to be proactive when it comes to security, and hence their losses are miniscule. Reported recently was something like €400k for a smaller country (7 million?) for an entire year for all banks. This one case in the UK is double that, reflecting that British banks and USA banks are reactive to security. Although they knew about it, they ignored it.
This could be called the "prove-it" school of security, and it has merit. As we saw with SSL, there never really was much of a threat on the wire; and when it came to the node, we were pretty much defenceless (although a lot of that comes down to one factor: Microsoft Windows). So when faced with FUD from the crypto / security industry, it is very very hard to separate real dangers from made up ones. I felt it was serious; others thought I was spreading FUD! Hence Philipp Güring's paper Concepts against Man-in-the-Browser Attacks, and the episode formed fascinating evidence for the market for silver bullets. The concept is now proven right in practice, but it didn't turn out how we predicted.
What is also interesting is that we now have a good cycle timeline: March 2006 is when the threat first crossed our radars. September 2009 it is in the British courts.
Postscript. More numbers from today's MITB:
A next-generation Trojan recently discovered pilfering online bank accounts around the world kicks it up a notch by avoiding any behavior that would trigger a fraud alert and forging the victim's bank statement to cover its tracks.The so-called URLZone Trojan doesn't just dupe users into giving up their online banking credentials like most banking Trojans do: Instead, it calls back to its command and control server for specific instructions on exactly how much to steal from the victim's bank account without raising any suspicion, and to which money mule account to send it the money. Then it forges the victim's on-screen bank statements so the person and bank don't see the unauthorized transaction.
Researchers from Finjan found the sophisticated attack, in which the cybercriminals stole around 200,000 euro per day during a period of 22 days in August from several online European bank customers, many of whom were based in Germany....
"The Trojan was smart enough to be able to look at the [victim's] bank balance," says Yuval Ben-Itzhak, CTO of Finjan... Finjan found the attackers had lured about 90,000 potential victims to their sites, and successfully infected about 6,400 of them. ...URLZone ensures the transactions are subtle: "The balance must be positive, and they set a minimum and maximum amount" based on the victim's balance, Ben-Itzhak says. That ensures the bank's anti-fraud system doesn't trigger an alert, he says.
And the malware is making the decisions -- and alterations to the bank statement -- in real time, he says. In one case, the attackers stole 8,576 euro, but the Trojan forged a screen that showed the transferred amount as 53.94 euro. The only way the victim would discover the discrepancy is if he logged into his account from an uninfected machine.
September 04, 2009
Numbers: CAPTCHAs and Suicide Bombers
 Two hard numbers effecting the attack model. The cost of attacking a CAPTCHA system with people in developing regions, from the Economist's report on the state of the CAPTCHA nation:
Two hard numbers effecting the attack model. The cost of attacking a CAPTCHA system with people in developing regions, from the Economist's report on the state of the CAPTCHA nation:
The biggest flaw with all CAPTCHA systems is that they are, by definition, susceptible to attack by humans who are paid to solve them. Teams of people based in developing countries can be hired online for $3 per 1,000 CAPTCHAs solved. Several forums exist both to offer such services and parcel out jobs. But not all attackers are willing to pay even this small sum; whether it is worth doing so depends on how much revenue their activities bring in. “If the benefit a spammer is getting from obtaining an e-mail account is less than $3 per 1,000, then CAPTCHA is doing a perfect job,” says Dr von Ahn.
And here, outside our normal programme, is news from RAH that people pay for the privilege of being a suicide bomber:
A second analysis with Palantir uncovered more details of the Syrian networks, including profiles of their top coordinators, which led analysts to conclude there wasn't one Syrian network, but many. Analysts identified key facilitators, how much they charged people who wanted to become suicide bombers, and where many of the fighters came from. Fighters from Saudi Arabia, for example, paid the most -- $1,088 -- for the opportunity to become suicide bombers.
It's important to examine security models remote to our own, because it it gives us neutral lessons on how the economics effects the result. An odd comparison there, that number $1088 is about the value required to acquire a good-but-false set of identity documents.
June 21, 2009
Cost of your PC
Some prices on how much it costs to rent your PC, if infected:
Prices vary greatly. Finjan said in Australia 1,000 infections have been sold for $100, while the same number can be picked up for as little as $5 in other countries, but mainly in the Far East.
Although it doesn't say it, your PC is for rent in batches only if it is a Windows machine. Apples Macs are a bit tougher, although their market share must one day get to the point where they justify more attention:
As TrendLabs' technical communications specialist Det Caraig points out in his research note on the attacks, Apple users are still far less likely to have their endpoints owned than their Microsoft Windows using peers. However, as proven over the last year in particular, Apple's growing PC market share has driven a subsequent upswell in the numbers of threats being created to target its OS.
That day may be here soon. Note that the (2) threats mentioned above are based on the user downloading and installing dodgy software. That's generally considered not to be something that Apple Macs or Microsoft can protect a user against. A market-share comment only, not a security-share comment.
Fans for either camp will twist the words whichever way. For my money, the #1 security tip -- buy a Mac -- is still intact.
February 04, 2009
The un-internalised cost of your data breach
 Adam points to a report by Ponemon Institute and old friends PGP Inc on data breaches.
Adam points to a report by Ponemon Institute and old friends PGP Inc on data breaches.
data breach incidents cost U.S. companies $202 per compromised customer record in 2008, compared to $197 in 2007. Within that number, the largest cost increase in 2008 concerns lost business created by abnormal churn, meaning turnover of customers. Since the study’s inception in 2005, this cost component has grown by more than $64 on a per victim basis, nearly a 40% increase.
Frequent readers of this blog will recall that I often post numbers of the average end-user cost of events like phishing. The number is about $1000.
Ignoring the obviously simplistic scientific process here, or better yet, leaving it to someone more scientific ... there is a huge difference between $200 and $1000.
We can take several views on this:
- a "caveat emptor view" has the user taking all the costs, because in libertarian economies, the user takes the responsibility for their choices. The responsible libertarian purchases PGP, of course.
- a "switching view" would have it that the only kick-back to the company is when a smaller proportion of the users switch to other providers, thus causing lessons of pain. This "churn view" is where the Ponemon report suggests the market is.
- the "risk sharing view" would have it that the user pays a smaller but still painful part. Call it 20%, or the opposite of what we see above. This should put the user firmly in the security protocol, and address any risks that the user is lax, but puts the onus on the business to provide the right tools.
- the "insurance view" is that the user pays the first $50 such as happens in credit card purchases. This more or less fixes the user's part in the protocol to little things like "don't lose the card" and passes the rest across to the company.
- "efficient view" would have it that the cost to the users should be close to $0 and the cost to the business should be closer to $1200. This is because the business is better able to manage all of the risk, knowing the business, as it does.
| 1200 | 1100 | 1000 | 900 | 800 | 700 | 600 | 500 | 400 | 300 | 200 | 100 | 000 | User Pays | |
| Caveat emptor | user buys PGP | |||||||||||||
| Switching | "churn" | |||||||||||||
| risk sharing | small but painful | |||||||||||||
| insurance | "don't lose that card" | |||||||||||||
| Efficient | know the business! | |||||||||||||
| Business pays | 000 | 100 | 200 | 300 | 400 | 500 | 600 | 700 | 800 | 900 | 1000 | 1100 | 1200 |
Markets tend to mature towards either the efficient view or the insurance view. The market in your identity is not mature. The reasons for that might be widely debated, but I'll have a quick stab here: we never really wanted to buy and sell our identities. We don't want that market in the first place, so damned if we're going to let it mature.
January 30, 2009
Brit Frauds, the Bezzle, and Signs of Rebellion in Heartland
Payments fraud seems up in Britain:
Matters found that around 26% fell victim to card fraudsters in 2008, up five per cent on the previous year.Kerry D'Souza, card fraud expert, CPP, says: "The dramatic increase in card fraud shows no sign of abating which isn't surprising given the desperate measures some people will resort to during the recession."
The average sum fraudulently transacted is over £650, with one in 20 victims reporting losses of over £2000. Yet 42% of victims did not know about these transactions and only found out they had been defrauded when alerted by their bank.
Online fraud affected 39% of victims, while card cloning from a cash point or chip and pin device accounted for a fifth of cases. Out of all cards that are physically lost and stolen, one in ten are also being used fraudulently.
One in 4 sounds quite high. That's a lot higher than one would expect. So either fraud has been running high and only now are better figures available, or it is growing? They say it is growing.
While researching origins of failure I came across this interesting snippet the other day from Richard Veryard:
The economist J.K Gailbraith used the term "bezzle" to denote the amount of money siphoned (or "embezzled") from the system. In good times, he remarked, the bezzle rises sharply, because everyone feels good and nobody notices. "In [economic] depression, all this is reversed. Money is watched with a narrow, suspicious eye. The man who handles it is assumed to be dishonest until he proves himself otherwise. Audits are penetrating and meticulous. Commercial morality is enormously improved. The bezzle shrinks." [Galbraith, The Great Crash 1929]
If this is true, then likely people will be waking up and demanding more from the payments infrastructure. No more easy money for them. Signs of this were spotted by Lynn:
"Up to this point, there has been no information sharing, thus empowering cyber criminals to use the same or slightly modified techniques over and over again. I believe that had we known the details about previous intrusions, we might have found and prevented the problem we learned of last week."Heartland's goal is to turn this event into something positive for the public, the financial institutions which issue credit/debit cards and payments processors.
Carr concluded, "Just as the Tylenol(R) crisis engendered a whole new packaging standard, our aspiration is to use this recent breach incident to help the payments industry find ways to protect its data - and therefore businesses and consumers - much more effectively."
For the past year, Carr has been a strong advocate for industry adoption of end-to-end encryption - which protects data at rest as well as data in motion - as an improved and safer standard of payments security. While he believes this technology does not wholly exist on any payments platform today, Heartland has been working to develop this solution and is more committed than ever to deploying it as quickly as possible.
Now, if you've read Lynn's rants on naked transactions, you will know exactly what this person is asking for. And you might even have a fair stab at why the payment providers denied Heartland that protection.
December 09, 2008
identity theft numbers (odd source, unusual targets)
Symantec posts an odd report on Phishing. The numbers are very useful:
Turner described visiting online private chat rooms, where underground buyers and sellers did business from June 1, 2007, to July 1, 2008. Credit cards, thousands at a time, would sell or be traded in a matter of seconds. They went from 10 cents to $25 per card, depending on credit limit, expiry date, and the security number on the back of the card.Symantec estimates the sale value of credit cards in the underground economy was over $276 million US. But the potential spending spree on these credit cards would be $5.3 billion.
...
New attack-tool kits sell for as much as $4,000, he said. "We observed a little more than 69,000 distinct advertisers posting more than 44 million ads selling stolen information," said Turner.
"Distinct advertisers" number 69,000? That doesn't make sense, but let's work the numbers. This small country is earning something like $276m over the space of a year, so that makes it $4000 per advertiser, or $333 per month. Hmm, that's possible, but it still seems low for an average monthly salary for a phisher. Can one say "nymous advertisers" ?
But that wasn't the weird bit. This was:
"It's become a self-sustaining business worldwide," said the report's author, Calgary-based Dean Turner, director of Symantec Security Global Intelligence Network, Technology and Response. "What jumped out for us was how much money is being made in this underground economy."
Who are these guys? Where have they been? Well, they may have company sleeping over in Germany, where banks have had the smile wiped off their faces:
Identity thieves who claim they stole details of 21 million German bank accounts are offering to sell the data on the black market for €12 million (US$15.3 million), a German magazine reported over the weekend.
Ouch. That's possibly half the country's households (El Reg suggests 3 out of 4!). Which adds to:
It's Germany's second mega heist of personal information in as many months. In October, T-Mobile admitted losing records belonging to 17 million customers that included their names, addresses, dates of birth, phone numbers, and email addresses.
I wonder if this is a wakeup call for the data protection specialists? Which then leads us to recent USA figures posted on Digital Identity:
The headline results of this study are as follows:
- The study discovered 5% of the children had one or more credit reports using their social security number
- 3% were found to be actual victims of child identity theft, while 2% were victims of file/credit contamination.
- Among the 5%, the children had on average $12,779 in fraudulent or wrongly assigned debt.
- While the study found that children were more likely to find problems in their credit histories as they aged, an astonishing 12% of those with problems were age 5 and under.
- A handful of cases stand out as especially severe: one child had seven identities listed under his SSN, with several thousand dollars in medical bills, apartment rentals, and credit accounts in collections; another child’s SSN was associated with over $325,000 in debt.
- One in four victims in the study had bills or lines of credit in collections or foreclosure, while almost twothirds of these children had fake or wrong names listed under their SSN.
- 42% of those children with erroneous credit reports only had credit files at one credit bureau, meaning their fraud could have gone unnoticed without checking all three bureaus.
Now, one could optimistically say that the kids won't have to pay out the money, but if the trial & suffering that is common with other identity fraud cases is any guide, I wouldn't be so sanguine. OTOH, it should be a lot easier to get a conviction if the perp can be collared.
December 07, 2008
Security is a subset of Reliability
From the "articles I wish I'd written" department, Chandler points to an article by Daniels Geer & Conway on all the ways security is really a subset of reliability. Of course!

I think this is why the best engineers who've done great security things start from the top; from the customer, the product, the market. They know that in order to secure something, they had better know what the something is before even attempting to add a cryptosec layer over it.
Which is to say, security cannot be a separate discipline. It can be a separate theory, a bit like statics is a theory from civil engineering, or triage is a part of medicine. You might study it in University, but you don't get a job in it; every practitioner needs some basic security. If you are a specialist in security, your job is more or less to teach it to practitioners. The alternate is to ask the practitioners to teach you about the product, which doesn't seem sensible.
September 11, 2008
US passports in 36 lots?
People on the crypto list were asking whether prices of street sales of insecurity could tell us stuff, like the drugs czars get from the price of street drugs. Dan Geer reports that the current cost of US passports is: $18k for 36, or $500 per unit. I'm not sure what the "lot of 36" entails.
He also reports a bunch of other things available for sale on the net black markets. Here's a selection of prices that would interest this audience:
 40 compromised windows boxes: $1.60
40 compromised windows boxes: $1.60
42 rich bank accounts: $42,000
42 real fresh emails: $210
40 Full identities: $220
30 Unix roots: $75
etc etc.
There is one really big lesson that these prices can tell you: their persistence and their apparent attention to the laws of supply and demand mean that these are goods that have value, and will probably always have value.
Using legislative tools to squat the goods of value falls foul of Goodhart's law. You can use the tool, but it just pops up somewhere else. Legislation then is like any other drug, every hit gives you less and shorter pleasure, so you need more of it each time. You see where this is going? Think prohibition, etc, and look for other solutions.
If we agree on that, and then ignore the laws of economics, as a society (which is the case with the drugs czars), then all other observations feel rather specious. However, we can glean some insights of the marketplace from the above.
Firstly, those rich bank accounts must be reliable end-to-end, to be worth $1000 each. That is, money laundering at the scale needed is functioning very well, notwithstanding 2 decades' effort to address it. Like the drugs people, the anti-money laundering people would be well advised to study some economics before making their next move.
Secondly, security hasn't improved any, over time, and if anything it has been bedded into a status quo. OK, we knew that, but it is good to have some evidence of it.
Thirdly, the ratios of utility + security remain between Linux boxes and Windows boxes. This is a complex issue, though: on the one hand, Linux boxes are used to run core tasks from high-end ISPs, so their value is much higher. On the other hand, there are some views that Windows might have got more secure, and Linux might still be being compromised in large numbers. We just can't see that possibility from these numbers, because they reflect two things (being the relative utilities and the relative securities).
It would be very useful to show compromise numbers between the various brands. Nothing much else gets people to stop bickering and fluffing up their security feathers, and gets them back to work. If anything, the emergence of universal skepticism of Microsoft's security in the early 2000s was what caused Bill Gates to write his famous memo and attempt a turn-around. The same thing seems to be true of other organisations; the don't burst their own bubble of security hubris, others have to.
My dream metric for someone to produce would be this: Which brand of browser were you using when you were last phished, or otherwise had your bank account stolen? Which email client? And which operating system?
I suspect that only then will the posturing stop and developers start to really work on solutions. The reward is oh-so-much clearer: get those numbers down.
August 07, 2008
Osama bin Laden gets a cosmetic makevover in his British Vanity Passport
 cwe points to this new way to improve your passport profile:
cwe points to this new way to improve your passport profile:
Using his own software, a publicly available programming code, a £40 card reader and two £10 RFID chips, Mr van Beek took less than an hour to clone and manipulate two passport chips to a level at which they were ready to be planted inside fake or stolen paper passports.A baby boy’s passport chip was altered to contain an image of Osama bin Laden, and the passport of a 36-year-old woman was changed to feature a picture of Hiba Darghmeh, a Palestinian suicide bomber who killed three people in 2003. The unlikely identities were chosen so that there could be no suggestion that either Mr van Beek or The Times was faking viable travel documents.
OK, so costs is what we track here at FC-central: we need 60 quid of parts, and let's call it 40 quid for the work. Add to that, a fake or stolen passport, which seems to run to around 100 depending. Call it 200, all-up, for the basic package. The fake may possibly be preferred because you can make it with the right photo inside the jacket, without having to do the professional dicey slicey work. Now that the border people are convinced that the RFID chip is perfectly secure, they won't be looking for that definitively British feel.
Folks, if you are going to try this at home, use your own passport, because using fake passports is a bit naughty! There are all sorts of reasons to improve ones image, and cosmetics is a booming industry these days. Let's say, we change the awful compulsory taliban image to a studio photo by a professional photographer. Easy relaxed pose, nice smile, and with your favourite Italian holiday scenes in the background. Add some photoshop work to smooth out the excess lines, lighten up those hungover dark eyes, and shrink those tubby parts off. We'll be a hit with the senior citizens.
We can also improve your hard details: For the 40-somethings, we'll take 10 years taken off your age, and for the teenager, we'll boost you up to 18 or 21. For the junior industry leader, we can add a title or two, and some grey at the side. Would you prefer Sir or Lord?
Your premium vanity upgrade, with all the trimmings, is likely to set you back around 500, and less if you bring your own base. Think of the savings on gym fees, and all the burgers you can eat!
One small wrinkle: there is a hint in the article that the British Government is offering these special personality units only until next year. Rush now...
August 04, 2008
Blank UK passports in bulk
A heist provides a price for false identities:
The thousands of UK ePassports stolen on Monday are likely to sell for up to £20m on the black market, say privacy experts.A van carrying about 3,000 blank ePassports and visas was hijacked on route to RAF Northolt, near London.
The estimate of £20m seems to come from Simon Davies, the man who started the Big Brother awards, but there is no discussion as to where he got it from. Either way, that would suggest a price of £6-7000 which is an order of magnitude higher than previous numbers. Browse here.
October 25, 2007
My fake passports and me
 Rasika pointed to a serious attempt to research false passports for all of EUs countries by Panorama, a British soft-investigation TV series:
Rasika pointed to a serious attempt to research false passports for all of EUs countries by Panorama, a British soft-investigation TV series:
I am attending an informal seminar led by a passport dealer, along with six hopefuls who are living illegally in the UK. We are told that all our problems can be solved by a "high quality" Czech passport. It will take just two weeks to obtain and cost a mere £1,500.This may already sound surreal enough, but it was just the beginning of my journey across Europe in search of fake passports from all 25 EU member states.
What's lacking here is hard costs of the passports she actually did obtain. That's why it is soft investigation.
I am directed to somebody who introduces me to somebody else, and finally I end up face to face with two innocent-looking pensioners. They say that for just 300 euros they can get me a Polish passport in less than 24 hours.This deal falls through, but another dealer has delivered Polish and Lithuanian passports, complete with my own photos and two different identities.
 But the breadth of the success makes it worthy of reporting:
But the breadth of the success makes it worthy of reporting:
It took me just five months to get 20 fake EU passports. Some of them were of the very best quality and were unlikely to be spotted as fakes by even the most stringent of border controls.
This is probably a good time to remind FC readers that you can find a long running series on the cost of false identity, taken from news articles that specify actual costs, here in the blog. Also note that on the Panorama show there is a video segment, but it is in a format that I cannot read for some reason.
Update: in one of the accompanying articles:
They ranged in price from just #250 to more than #1,500. Some were provided within several days, while others took weeks.
(Currency is unclear, it was shown as #.) Also, from one of the accompanying articles:
Police believe they were on the brink of producing 12,000 fake EU passports - potentially earning them £12m, when they were arrested in November 2005. .... Det Insp Nick Downing, who led the investigation, said the passports could have sold for up to £1,000 each.
Same as FC.
October 16, 2007
Your online Identity supplier
Vlad Miller, our source in Russia, sent:
This is an online fake-document shop. Here's the price list:
- Lithuanian or Latvian passport: €2500 without advance and €2000 with 50% advance payment.
- UK or German passport: €3500 without advance and €3000 with 50%.
- Driver's licenses of these same countries cost €600 and €800 euros, depending on the advance payment as above.
- Russian passports cost $1000 USD with advance and $1300 without.
An additional $500 is required to put the person's name into the gov't database so that the passport checks out online as well.
They use WU and bank transfers for collecting payment, as WebMoney Arbitration has already banned them. For communication (orders, etc. they use email and ICQ, also SMS with returning customers)
Together with fake documents, as a bonus, they offer consulting on crossing borders "in the green", schedules of border patrols, etc.

September 10, 2007
Threatwatch - more data on cost of your identity
In the long-running threatwatch theme of how much a set of identity documents will cost you, Dave Birch spots new data:
Other than data breaches, another useful rule-of-thumb figure, I reckon, might come from identity card fraud since an identity card is a much better representation of a persons identity than a credit card record. Luckily, one of the countries with a national smart ID card just had a police bust: in Malyasia, the police seized fake MyKad, foreign workers identity cards, work permits and Indonesian passports and said that they thought the fake documents were sold for between RM300 and RM500 (somewhere between $100 to $150) each. That gives us a rule-of-thumb of $20 for a "credit card identity" and $100, say, for a "full identity". Since we don't yet have ID cards in the U.K., I thought that fake passports might be my best proxy. Here, the police says that 1,800 alleged counterfeit passports recovered in raid in North London were valued at £1m. If we round it up to 2,000 fakes, then that's £500 each. This, incidentally, was the largest seizure of fake passports in the U.K. so far and vincluded 200 U.K. passports, which, according to police, are often considered by counterfeiters to be too difficult to reproduce. Not!The point I actually wanted make is not that these figures a very variable, which they are, but that they're not comparing apples with apples. Hence the simplistic "what's your identity worth?" question cannot be answered with a simple number.
OK, that's consistent with my long-standing estimate of 1000 (in the major units, pounds, dollars, euros) to get a set of docs. It is important to track this because if you are building a system based on identity, this gives you a solid number on which to base your economic security. E.g., don't protect much more than 1000 on the basis of identity, alone.
As a curious footnote, I recently acquired a new high-quality document from the proper source, and it cost me around 1000, once all the checking, rechecking, couriered documents and double phase costs were all added up. If a data set of one could be extrapolated, this would tell us that it makes no difference to the user whether she goes for a fully authentic set or not!
Luckily my experiences are probably an outlier, but we can see a fairly damning data point here: the cost of an "informal" document is far to similar to the cost of a "formal" document.
Postscript: It turns out that there is no way to go through FC archives and see all the various categories, so I've added a button at the right which allows you to see (for example) the cost of your identity, in full posted-archive form.
July 23, 2007
Threatwatch: how much to MITM, how quickly, how much lost
It costs $500 for a kit to launch an MITM phishing attack. (Don't forget to add labour costs at 3rd world rates...)
David Franklin, vice president for the Europe, Middle East and Africa told IT PRO that these sites are proliferating because they are actually easier for hackers to set up than traditional 'fake' phishing sites because they don't even have to maintain a fake website. He also said man-in-the-middle attacks defeat weak authentication methods including passwords, internet protocol (IP) geolocation, device fingerprinting, cookies and personal security images and tokens, for example."A lot of the attacks you hear about are just the tip of the iceberg. Banks often won't even tell an affected customer that they have been a victim of these man-in-the-middle attacks," said Franklin, adding that kits that guide cybercriminals through setting up a man-in-the-middle attack are now so popular they can be bought for as little as $500 (£250) on the black market now.
He also said "man-in-the-browser" attacks are emerging to compete in popularity with middleman threat.
A couple of interesting notes from the above: it is now accepted that MITM is what phishing is (in the form mentioned above, the original email form, and the DNS form). These MITMs defeat the identity protection of SSL secure browsing, a claim made hereabouts first. and one that is still widely misunderstood: This is significant because SSL is engineered to defeat MITMs, but it only defeats internal or protocol MITMs, and can not stop the application itself being MITM'd. This typical "bypass attack" has important economic ramifications, such that SSL is now shown to be too heavy-weight to deliver value, unless it is totally free of cost and setup.
Secondly, note that the mainstream news has picked up the MITB threat (also reported and documented here first). It's still rare, but in the next 6 months, expect your boss to ask what it's about, because he read it in Yahoo.
More juicy threat modelling numbers:
Analysts at RSA Security early last month spotted a single piece of PHP code that installs a phishing site on a compromised server in about two seconds,
And....
Despite efforts to quickly shut sites down, phishing sites averaged a 3.8-day life span in May, according to the Anti-Phishing Working Group, which released its latest statistics on Sunday.Data from market analyst Gartner released last month showed that phishing attacks have doubled over the last two years.
Gartner said 3.5 million adults remembered revealing sensitive personal or financial information to a phisher, while 2.3 million said that they had lost money because of phishing. The average loss is US$1,250 per victim, Gartner said.
In the past (June 2004: 1, 2), I've reported that phishing costs around one billion per year. Multiply those last two numbers above from Gartner, and we get around a billion over the last three years. Still a good rule of thumb then.
April 20, 2007
Counting Chickens at eTrade, bankruptcy in Europe, and costs in America
Gunnar Peterson posts:
Identity Chickens Coming Home to 8 Figure RoostReason number 2,503,201 why 1995 security architectures based on SSL, network firewalls, and a prayer are not good enough any more. Etrade's 10Q filing (hat tip Dan Geer):
Other expenses increased 97% to $45.7 million and 55% to $101.9 million for the three and nine months ended September 30, 2006, respectively, compared to the same periods in 2005. These increases were primarily due to fraud related losses during the third quarter of 2006 of $18.1 million, of which $10.0 million was identity theft related. The identity theft situations arose from recent computer viruses that attacked the personal computers of our customers, not from a breach of the security of our systems. We reimbursed customers for their losses through our Complete Protection Guarantee. These fraud schemes have impacted our industry as a whole. While we believe our systems remain safe and secure, we have implemented technological and operational changes to deter unauthorized activity in our customer accounts.
Over on EC I suggested that the cost depends on whether you are left or right of the Atlantic. In Europe, the Data Directive mandates fines, I was told it was around 25-50 thousand Euros per record lost . Lose your database, file for bankruptcy.
(OK, so I make this claim. I heard it in a pub... I'd better check on it!)
While we're counting cost, if not coup, here's some US numbers, finally with some serious if unconfirmed attention by Forrester Research:
The average security breach can cost a company between $90 and $305 per lost record, according to a new study from Forrester Research. The research firm surveyed 28 companies that had some type of data breach."After calculating the expenses of legal fees, call centers, lost employee productivity, regulatory fines, stock plummets, and customer losses, it can be dizzying, if not impossible, to come up with a true number," wrote senior analyst Khalid Kark in the report. "Although studies may not be able to determine the exact cost of a security breach in your organization, the loss of sensitive data can have a crippling impact on an organization's bottom line, especially if it is ill-equipped, and it's important to be able to make an educated estimate of its cost."
March 27, 2007
Cost of an identity
Some figures on the cost to build a new identity:
In all, seven defendants pleaded guilty in Corpus Christi this past week to charges of selling their birth certificates and Social Security cards for $100 each. Seven other defendants pleaded guilty to buying or reselling those documents as part of a ring that sold documents to illegal immigrants seeking jobs in Dodge City, Kan.
One other figure:
Tim Counts, an Immigration and Customs Enforcement spokesman in Bloomington, Minn., said that investigation revealed documents were available for a price in places as open as Kmart parking lots. He said genuine documents were the most expensive, costing up to $1,500, and the most effective against detection.
That remark looks suspicious, I'd guess he's talking about something else than SS cards and birth certificates.
Also over in that center of expertise in identity theft, USA, a blog entry by Spire says:
- For as long as we continue to pretend that SSNs are secret and therefore may be used as authenticators, they will be.
- There are over 150,000 people (my estimate) with "defendable" access to your SSN right now. They aren't secret.
- You are more likely by a factor of 10 to be a victim of identity fraud via one of these "authorized" folks.
- The real problem is not how easy it is to get your SSN, but how creditors et.al. allow the SSN to be used as an authenticator (See #1).
- The SSN is fine as an identifier. No, it is not perfect, but its main benefit is that it is already used in so many places.
Right. That's a number we wanted: 150k people in that country have access (legal, he says defendable) to the SSN. Presumably they have access to all the other PII as well.
October 10, 2006
NZ on Identity
It is almost but not quite a truism that if you make identity valuable, then you make identity theft economic, amongst other things. Here's New Zealand's take on the issue, at the end of a long article on government reform:
Let me share with you one last story: The Department of Transportation came to us one day and said they needed to increase the fees for driver's licenses. When we asked why, they said that the cost of relicensing wasn't being fully recovered at the current fee levels. Then we asked why we should be doing this sort of thing at all. The transportation people clearly thought that was a very stupid question: Everybody needs a driver's license, they said. I then pointed out that I received mine when I was fifteen and asked them: "What is it about relicensing that in any way tests driver competency?" We gave them ten days to think this over. At one point they suggested to us that the police need driver's licenses for identification purposes. We responded that this was the purpose of an identity card, not a driver's license. Finally they admitted that they could think of no good reason for what they were doing - so we abolished the whole process! Now a driver's license is good until a person is 74 years old, after which he must get an annual medical test to ensure he is still competent to drive. So not only did we not need new fees, we abolished a whole department. That's what I mean by thinking differently.
The rest of the article is very well worth reading, for a summary of NZ's economics successes.
August 24, 2006
Fraudwatch - how much a Brit costs, how to be a 419-er, Sarbanes-Oxley rises as fraud rises, the real Piracy
A BBC programme reported the cost of Brit identities as extracted from recycled PCs:
Bank account details belonging to thousands of Britons are being sold in West Africa for less than £20 each, the BBC's Real Story programme has found.
Which comes as the EU moves to total passenger tracking:
BIOMETRIC testing is set to be introduced at European airports under plans for stringent new security measures revealed yesterday in the wake of last week's alleged terror plot. Passengers would have their fingerprint or iris scanned under the measures proposed by EU interior ministers, which would also use passenger profiling to try to identify potential terrorists.
Here's some stats on Nigerian 419 scams, another deception with higher risks for the consumer but not the retailer:
He sent 500 e-mails a day and usually received about seven replies. Shepherd would then take over. "When you get a reply, it's 70% sure that you'll get the money," Samuel said. ... By 2003, Shepherd was fleecing 25 to 40 victims a month, Samuel said. Samuel never got the 20%, but still made a minimum of $900 a month, three times the average income here. At times, he made $6,000 to $7,000 a month.Samuel said Shepherd employs seven Nigerians in America, including one in the San Francisco Bay Area, to spy on maghas and threaten any who get cold feet. If a big deal is going off track, he calls in all seven.
"They're all graduates and very smart," Samuel said. "Four of them are graduates in psychology here in Nigeria. If the white guy is getting suspicious, he'll call them all in and say, 'Can you finish this off for me?'
"They'll try to scare you that you're not going to get out of it. Or you're going to be arrested and you will face trial in Nigeria. They'll say: 'We know you were at Wal-Mart yesterday. We know the D.A. He's our friend.' "
"They'll tell you that you are in too deep - you either complete it or you'll be killed."
Anyone want to hazard when crooks will be able to buy European biometric data in Africa? More from the BBC.
Once in a blue moon, using dodgy identity cards seems not to work (dead link):
A Toronto man who wanted a fraudulent driver's licence added to his collection of counterfeit ID was foiled by a sharp-eyed employee with the Ministry of Transportation in Hamilton. .... The convicted man provided a Canadian citizenship card in the name of Rohan Omar Kelly when he showed up with a friend on June 12 to write a driver's exam at the ministry's Kenilworth Avenue office.The employee took a long, hard look at his identification and discreetly slipped away to call the police.
Meanwhile, his friend presented a credit card to pay for the fictitious Kelly's fee. The card, as it would turn out when the pair was arrested a short time later, was a pirated copy. The same was true for a Canadian social insurance card seized from Thomas and a second citizenship card that police found on the dash of the friend's Chev Malibu parked outside.
I wouldn't suggest you do that at home, folks! Fraud responds well to natural selection; the dumb crooks get caught, leaving the smart ones. Actually, the smart ones get caught too, but not before training two more up.
Laws on fraud enjoy no such control, they just get bigger and dumber. CompliancePipeline reports on the anti-climax of Sarbanes-Oxley:
The top-level findings show that even in the more heavily regulated business environment, the incidence of fraud continues to increase. Sixty-seven percent of the respondents indicated that institutional fraud is more prevalent today than five years ago, and another 27 percent said there has been no change level of fraud activity.
Probably, Sarbanes-Oxley supporters will say that they just need to try harder, write more rules, bust more companies, etc etc. Perhaps they should create identity trails as part of their data? New figures suggest identity theft is becoming more valuable, but that's no reason not to store massive amounts of identity information:
Nearly 10 million consumers were victimized by some form of identity theft in 2004 alone. That equals 19,178 people per day, 799 per hour and 13.3 per minute. Consumers have reportedly lost over US$5 million, and businesses have lost an estimated $50 billion or more.
A few years back the accepted figure for identity theft in the USA was around $10bn; maybe it is being revised upwards to 50bn or more (?) with inclusion of internal (unreported) corporate costs.
And, let's close with a curious comparison: Cubicle reports on stats on the real Piracy!
…there is very little financial incentive for both governments and shippers to deal with this crime. Piracy is costing shippers $.32 for every $10,000 of goods shipped estimates David N. Kellerman of Maritime Security. Not only is the economic cost inconsequential to companies, so it is to some governments.Sound familiar? If I’m the corporate owner, the cost is inconsequential. If I’m a sailor on one of these ships, though, the cost is a little more significant:
Merely one year before, in September of 1998, a smaller Japanese-owned freighter named the Tenyu had gone missing soon after departing from the same port of Kuala Tanjung with a similar load of aluminum, and a crew of fifteen. Three months later the Tenyu was discovered under a changed name and flag in a Chinese port, but the cargo was missing, as was the original crew, all of whom are presumed to have been killed.Ship owners can transfer the risk of Piracy with insurance, but sailors only have two options. They can either avoid the risk by finding a new vocation (not sailing on vessels which travel through pirate-prone regions is not really an option) or hope that the shipowners mitigate it by implementing anti-piracy safeguards such as anti-boarding defenses or armed guards, at least for passing through piracy-prone areas.
Somehow, identity theft seems a little more comfortable.
June 24, 2006
Identity 7, watchlist error rate, $300 to get off the watchlist
I love this article, it's cracker-jack full of interesting stuff about a crime family who have industrialised identity document production in the US.
The dominant forgery-and-distribution network in the United States is allegedly controlled by the Castorena family, U.S. Immigration and Customs Enforcement officials say. Its members emigrated from Mexico in the late 1980s and have used their printing skills and business acumen to capture a big piece of the booming industry.
Nice colour, there. Actually the entire article is full of colour, well worth reading. We'll just do the dry facts here:
Federal authorities said that calculating the financial scope of document forgery is virtually impossible but that illicit profits easily amount to millions of dollars, if not billions. One investigation of CFO operations in Los Angeles alone resulted in *the seizure of 3 million documents with a street value of more than $20 million.*"We've hit them pretty hard, but have we shut down the entire operation? I don't think we can say that yet," said Scott A. Weber, chief of the agency's Identity and Benefit Fraud Unit. "We know there are many different cells out there, and they are still providing documents."
Ouch. 20 millions divided by $3 millions is $7. Identity 7, here we come.
Illegal immigrants are often given packages of phony documents as part of a $2,000 smuggling fee. Others can easily make contact with vendors who operate on street corners or at flea markets in immigrant communities in virtually every city. .. . A typical transaction includes key papers such as a Social Security card, a driver's license and a "green card" granting immigrants permanent U.S. residency. Fees range from $75 to $300, depending on quality.
Identity is a throw-in for a $2000 package tour sold out of Mexico. Say no more. Obviously, these numbers are all screwed up as there is a big difference between $75 and $7. But, consider. Even at $300, it would be more cost-effective for the average American business traveller to travel on false documentation than to do the following:
Currently, individuals who want to clear their names have to submit several notarized copies of their identification. Then, if they're lucky, TSA might check their information against details in the classified database, add them to a cleared list and provide them with a letter attesting to their status.More than 28,000 individuals had filed the paperwork by October 2005, the latest figures available, according to TSA spokeswoman Amy Kudwa. She says the system works. "We work rigorously to resolve delays caused by misidentifications," Kudwa says.
...
The TSA's lists are only a subset of the larger, unified terrorist watch list, which consists of 250,000 people associated with terrorists, and an additional database of 150,000 less-detailed records, according to a recent media briefing by Terrorist Screening Center director Donna Bucella. The unified list is used by border officials, embassies issuing visas and state and local law enforcement agents during traffic stops.
This programme is of interest because its identity keystone drives other programmes. We are looking at a 7% error rate as a minimum, which should come as no surprise - of course, there are unlikely to be more than a 100 people on the list that really qualify as "terrorists who are likely to do some damage on a plane" so if the error rate is anything less than 99% then we should probably be stopping the planes right now. About the best we can conclude is that the strategy of stopping terrorists by identifying them doesn't seem worth emulating in financial cryptography.
And Darren points out the statistical unwisdom of relying on such programmes:
Suppose that NSA's system is really, really, really good, really, really good, with an accuracy rate of .90, and a misidentification rate of .00001, which means that only 3,000 innocent people are misidentified as terrorists. With these suppositions, then the probability that people are terrorists given that NSA's system of surveillance identifies them as terrorists is only p=0.2308, which is far from one and well below flipping a coin. NSA's domestic monitoring of everyone's email and phone calls is useless for finding terrorists.
Sure. But the NSA are not using the databases to find terrorists. Instead, when other leads come in, they look to see what they have in their databases -- to add to the lead they already have. Simple. With this strategy, clearly, the more data, the more databases, the better this works.
But, again, it doesn't seem a strategy that we'd emulate in FC.
February 04, 2006
The Price for Your Identity
So what does it cost to forge an identity? Here's a list of costs (with updates moved to end) that lead us to the answer. First off, in Britain:
When interviewed the duo said they were conducting at least eight transactions a day, totalling around 5,000 sales over two years. A passport would cost £350, a national insurance card or a driving license would cost £50 to £75.
In Japan, driver's licences are no trouble if you know a Colombian (sorry, URL is duff, see below for full story).
The Hyogo prefectural police and other police headquarters have arrested 12 members of the ring, nine of them Colombians. The police reported that some of the suspects said that in addition to the forged passports, they bought bogus driver's licenses and cash cards before entering Japan for only 20 dollars.
Back to Britain, and the Sunday Herald dives into the business of undercover policework. Here's a heavily redacted snippage indicating a top-drawer contender.
He tells us one passport costs just over £1000, but if we buy more, the price drops to around £800. ... There, Pavel brings out a sample of the kind of passport he will be able to get for us. The passports are 100% authentic to the eye. ... British immigration and passport experts who examined the document on guarantee of anonymity said it was “the very best [they’d] ever seen”. It even passed an ultraviolet light test which British passport controllers use to show up hidden watermarks which are in every genuine document.They said it was “real” and could easily be used to open a bank account without alerting any suspicion.
...
The officer, who takes the lead on ID theft within the SDEA, added: “There has been an upswing in the trade in fake documentation.
Addendums. Just found some numbers from an old post on EC:
Social Security cards run about $20, green cards about $70 and a California driver's license between $60 and $250. The price jumps up for higher-quality documents, such as IDs with magnetic strips containing real information — often from victims of identity theft.
Maybe that's where I got the idea from...
Please note that the purpose of collecting this information is for security researchers to form a validated view of what it costs an attacker to breach their designs (so I won't bother to point out where you can buy them).
Most security designs simply assume that collecting the identity of someone grants the holder magical security properties; unfortunately the truth is far less encouraging and the result is that relying on identity collection is probably only reliable for stopping honest people and your poorer class of criminal from defrauding the system.
Here's my predicted benchmark - forging any identity costs approximately 1000 (in today's major units). I'll update that as we get better into it.
20 dollars IDs foil immigration officials The Yomiuri Shimbun
Colombians arrested here over their suspected involvement in a burglary ring entered Japan on fake passports and other forms of counterfeit identification purchased for only 20 dollars, police learned Thursday.
The Hyogo prefectural police quoted one of the suspects as saying there is an organization in Colombia that forges such documents.
The ring is suspected of committing more than 100 burglaries in 11 prefectures, including Osaka and Hyogo, over the last three years, netting items and cash worth hundreds of millions of yen.
The Hyogo prefectural police and other police headquarters have arrested 12 members of the ring, nine of them Colombians. The police reported that some of the suspects said that in addition to the forged passports, they bought bogus driver's licenses and cash cards before entering Japan for only 20 dollars.
Some of the suspects reportedly told the police that many houses are left unlocked in Japan, and people here pay little thought to crime prevention.
The suspects are believed to have sold electrical appliances and other stolen items and sent the money to relatives in Colombia.
According to the Hyogo prefectural police, one of the suspects previously had been deported from Japan, but returned on a fake passport.
The police arrested the alleged ringleader Akihiro Nagashima, 36, and two Colombian men in November on suspicion of stealing a television and other items from a house in Wakayama. Nagashima has been indicted on the charge.
The burglary ring is believed to comprise about 20 members, about 80 percent of whom are believed to be Colombians.
(Jan. 28, 2006)
¿ The Yomiuri Shimbun.
http://www.yomiuri.co.jp/dy/national/20060128tdy02001.htm
Addendums.
20060305 USA reports how much it costs to find false identities:
Glendining offers his doormen $20 gift certificates for each fake ID pulled. In recent years, the fake IDs have gotten better. “You really gotta make the best effort you can,” Glendining said.The bar keeps a sample of real and fake IDs around for doormen to learn from. Telltale signs of a fake include IDs that crack when bent, eye color or height that doesn’t match or a nervous person shuffling. But oftentimes, it comes down to the feel of the ID.
Spotted in EC.
20060223. Israel:
The Israeli passport is considered to be one of the easiest passports to forge and can be purchased in Asia, and especially in Thailand's markets, for anywhere from USD 500 to 2000. The Israeli passport is in great demand because people carrying it can enter Asian countries without a visa. .... During interrogation, [six Iranians] confessed that they purchased the passports in Thailand for USD 1,000 for the purpose of entering Macau easily.
20060216, Britain:
LONDON: The head of security at Arsenal’s new stadium ran a racket supplying guards on the site with fake passports. Ademola Adeniran, 39, an illegal immigrant, supplied documents stamped with "indefinite leave to remain" for men working there. Adeniran, of Hackney, was caught with more than 100 fake Nigerian and South African passports when police raided his home. They are thought to be worth £200 each on the black market.
20060212. In Britain
London is a major centre for Asian and African gangs based in Thailand to sell counterfeit European passports, mostly to people from the Middle East, immigration police chief Pol Lt-Gen Suwat Thamrongsrisakul says. Immigration police last year seized 572 fake passports, of which 184 were Belgian, 155 Portuguese, 139 Spanish and 94 French, he said yesterday. All the counterfeits were printed in Bangkok, taken to London and sold for about 1,000 (about 68,000 baht) each by brokers who made about 20% profit on them, he said.
20060516. In Britain
"I charge £700 for each one but can give you a £100 discount if you order two. I can do most EU countries including Greece, Denmark, Spain, Italy, Poland, Latvia and Lithuania."
June 07, 2005
Identity is an asset. Assets mean theft ... and Trade!
This is a good article. It describes what happens when you make a simple number the core of your security system. If you control the number, it becomes valuable. If it becomes valuable then it will either be stolen or traded. Valuable things are assets - which means trade or theft. (See also EC.)
In this case we we see the trade, and this sits nicely alongside the identity theft epidemic in the US: all there because the system made the number the control.
All security is based on assets. Perversely, if you make a number the core of your security system, then it becomes an asset, thus adding one more thing to protect, so you need a security system to secure your security system.
The lesson is simple. Do not make your security depend on a number. Identify what the asset is and protect that. Don't protect stuff that isn't relevent, elsewise you'll find that the costs of protecting might skyrocket, while your asset walks off unprotected.
Some Immigrants Are Offering Social Security Numbers for Rent
By EDUARDO PORTER
Published: June 7, 2005
TLALCHAPA, Mexico - Gerardo Luviano is looking for somebody to rent his Social Security number.
Mr. Luviano, 39, obtained legal residence in the United States almost 20 years ago. But these days, back in Mexico, teaching beekeeping at the local high school in this hot, dusty town in the southwestern part of the country, Mr. Luviano is not using his Social Security number. So he is looking for an illegal immigrant in the United States to use it for him - providing a little cash along the way.
"I've almost managed to contact somebody to lend my number to," Mr. Luviano said. "My brother in California has a friend who has crops and has people that need one."
Mr. Luviano's pending transaction is merely a blip in a shadowy yet vibrant underground market. Virtually undetected by American authorities, operating below the radar in immigrant communities from coast to coast, a secondary trade in identities has emerged straddling both sides of the Mexico-United States border.
"It is seen as a normal thing to do," said Luis Magana, an immigrant-rights activist assisting farm workers in the agriculture-rich San Joaquin Valley of California.
The number of people participating in the illegal deals is impossible to determine accurately. But it is clearly significant, flourishing despite efforts to combat identity fraud.
Hundreds of thousands of immigrants who cross the border from Mexico illegally each year need to procure a legal identity that will allow them to work in the United States. Many legal immigrants, whether living in the United States or back in Mexico, are happy to provide them: as they pad their earnings by letting illegal immigrants work under their name and number, they also enhance their own unemployment and pension benefits. And sometimes they charge for the favor.
Martin Mora, a former migrant to the United States who these days is a local politician preparing to run for a seat in the state legislature in next October's elections, said that in just one town in the Tlalchapa municipality, "of about 1,000 that fixed their papers in the United States there might be 50 that are here and lending their number."
Demand for American identities has blossomed in the cracks between the nation's increasingly unwelcoming immigration laws and businesses' unremitting demand for low-wage labor.
In 1986, when the Immigration Reform and Control Act started penalizing employers who knowingly hired illegal immigrants, most employers started requiring immigrants to provide the paperwork - including a Social Security number - to prove their eligibility to work.
The new law did not stop unauthorized immigrant work. An estimated 10 million illegal immigrants live in the United States today, up from some 4 million before the law went into effect. But it did create a thriving market for fake documents.
These days, most immigrants working unlawfully buy a document combo for $100 to $200 that includes a fake green card and fake Social Security card with a nine-digit number plucked out of thin air. "They'll make it for you right there at the flea market," said David Blanco, an illegal immigrant from Costa Rica who works as an auto mechanic in Stockton, Calif.
This process has one big drawback, however. Each year, Social Security receives millions of W-2 earning statements with names or numbers that do not match its records. Nine million poured in for 2002, many of them just simple mistakes. In response the agency sends hundreds of thousands of letters asking employers to correct the information. These letters can provoke the firing of the offending worker.
Working with a name linked to a number recognized by Social Security - even if it is just borrowed or leased - avoids these pitfalls. "It's the safest way," said Mario Avalos, a Stockton accountant who every year does tax returns for dozens of illegal immigrants. "If you are going to work in a company with strict requirements, you know they won't let you in without good papers."
While renting Social Security numbers makes up a small portion of the overall use of false papers, those with close ties to the immigrant communities say it is increasingly popular. "It used to be that people here offered their number for somebody to work it," said Mr. Mora in Tlalchapa. "Now people over there are asking people here if they can use their number."
Since legal American residents can lose their green cards if they stay outside the country too long, for those who have returned to Mexico it is useful to have somebody working under their identity north of the border.
"There are people who live in Mexico who take $4,000 or $5,000 in unemployment in the off season," said Jorge Eguiluz, a labor contractor working in the fields around Stockton, Calif. "They just lend the number during the season."
The deals also generate cash in other ways. Most identity lending happens within an extended family, or among immigrants from the same hometown. But it is still a hard-nosed transaction. Illegal immigrant workers usually earn so little they are owed an income tax refund at the end of the year. The illegal immigrant "working the number" will usually pay the real owner by sharing the tax
refund.
"Sometimes the one who is working doesn't mind giving all the refund, he just wants to work," said Fernando Rosales, who runs a shop preparing income taxes in the immigrant-rich enclave of Huntington Park, Calif. "But others don't, and sometimes they fight over it. We see that all the time. It's the talk of the place during income tax time."
Done skillfully, the underground transactions are virtually undetectable. They do not ring any bells at the Social Security Administration. Nor do they set off alarms at the Internal Revenue Service as long as the person who lends the number keeps track of the W-2's and files the proper income tax returns.
In a written response to questions, the audit office of Social Security's inspector general acknowledged that "as long as the name and S.S.N. on an incoming wage item (i.e., W-2) matches S.S.A.'s record" the agency will not detect any irregularity.
The response noted that the agency had no statistics on the use of Social Security numbers by illegal immigrants. It does not even know how many of the incorrect earnings reports it receives every year come from immigrants working unlawfully, though immigration experts estimate that most do.
Meanwhile, with the Homeland Security Department focused on terrorism threats, it has virtually stopped policing the workplace for run-of-the-mill work violations. Immigration and Customs Enforcement arrested only 450 illegal immigrants in the workplace in 2003, down from 14,000 in 1998.
"We have seen identity fraud," said John Torres, deputy assistant director for investigations. But "I haven't heard of the renting of identities."
Immigrants on both sides of the transactions are understandably reluctant to talk about their participation.
A 49-year-old illegal immigrant from Michoacan who earns $8.16 an hour at a waffle factory in Torrance, Calif., said that she had been using a Social Security number she borrowed from a friend in Mexico since she crossed illegally into the United States 15 years ago. "She hasn't come back in this time," the woman said.
There are risks involved in letting one's identity be used by someone else, though, as Mr. Luviano, the beekeeping instructor, learned through experience.
Mr. Luviano got his green card by a combination of luck and guile. He says he was on a short trip to visit his brother in California when the 1986 immigration law went into effect and the United States offered amnesty to millions of unauthorized workers.
Three million illegal immigrants, 2.3 million of them from Mexico, ultimately received residence papers. Mr. Luviano, who qualified when a farmer wrote a letter avowing he had worked for months in his fields, was one. Once he had his papers, though, he returned to Tlalchapa.
He has entered the United States several times since then, mostly to renew his green card. But in the early 1990's, concerned that long absences could put his green card at risk and spurred by the chance to make a little extra money, he lent his Social Security number to his brother's friend. "I kept almost all the income tax refund," Mr. Luviano said.
Mr. Luviano decided to pull the plug on the arrangement, however, when bills for purchases he had not made started arriving in his name at his brother's address. "You lend your number in good faith and you can get yourself in trouble," he said.
But Mr. Luviano is itching to do it again anyway. He knows that Social Security could provide retirement income down the line. And there's always the tax refund.
"I haven't profited as much as I could from those documents," he said ruefully.
Copyright 2005 The New York Times Company
http://www.nytimes.com/2005/06/07/business/07immigrant.html
January 09, 2005
Identity Theft: Why Hollywood has to take one for the team.
The Year of the Phish has passed us by, and we can relax in our new life swimming in fear of the net. Everyone now knows about the threats, even the users, but what they don't know is what happens next. My call: it's likely to get a lot worse before it gets better. And how it gets better is not going to be life as we knew it. But more on that later.
First... The Good News. There is some cold comfort for those not American. A recent report had British phishing loses under the millions. Most of the rich pickings are 'over there' where credit rules, and identity says 'ok'. And even there, the news could be construed as mildly positive for those in need of good cheer. A judge recently ruled a billion dollar payout against spammers who are identified in name, if not in face. We might never see their faces, but at least it feels good. AOL reported spam down by 75% but didn't say how they did it.
Also, news that Microsoft is to charge extra for security must make us believe they have found the magic pixie dust of security, and can now deliver an OS that's really, truly secure, this time! Either that, or they've cracked the conundrum of how to avoid the liability when the masses revolt and launch the class action suit of the century.
All this we could deal with, I guess, in time, if we could as an industry get out collective cryptographic act together and push the security models over to protecting users (one month's coding in Mozilla should do it, but oh, what a long month it's been!). But there is another problem looming, and it's ...
The Bad News: the politicians are now champing at the bit, looking for yet another reason to whip today's hobby horse of 'identify everyone' along into more lather. Yes, we can all mangle metaphors, just as easily as we can mangle security models. Let me explain.
The current project to identify the humanity of the world will make identity theft the crime of the century. It's really extraordinarily simple. The more everything rests on Identity, the more value will Identity have. And the more value it has, the more it will be worth to steal.
To get a handle on why it is more valuable, put yourself in the shoes of an identity thief. Imagine our phisher is three years old, and has a sweet tooth for data.
How much sugar can there be found in a thousand cooperating databases? Each database perfectly indexed with your one true number and bubbling over with personal details, financial details, searchable on demand. A regulatory regime that creates shared access to a thousand agencies, and that's before they start sharing with other countries?
To me, it sounds like the musical scene in the sweets factory of Chitty Chitty Bang Bang, where the over indulgent whistle of our one true identity becomes our security and dentistry nightmare. When the balance is upset, pandemonium ensues. (I'm thinking here the Year of the Dogs, and if you've seen the movie you will understand!)
Now, one could ask our politicians to stop it, and at once. But it's too late for that, they have the bits of digital identity between their teeth, and they are going to do it to us to save us from phishing! So we may as well be resigned to the fact that there will be a thousand interlinked identity databases, and a 100 times that number of people who have the ability to browse, manipulate, package, steal and sell that data. (This post is already too long, so I'm going to skip the naivete of asking the politicians to secure our identity, ok? )
A world like that means credit will come tumbling down, as we know it. Once you know everything about a person, you are that person, and no amount of digital hardware tokens or special biometric blah blahs will save the individual from being abused. So what do people do when their data becomes a phisher's candyfest?
People will withdraw from the credit system and move back to cash.This will cost them, but they will do it if they can. Further, it means that net commerce will develop more along the lines of cash trading than credit trading. In ecommerce terms, you might know this better as prepaid payment systems, but there are a variety of ways of doing it.
But the problem with all this is that a cash transaction has no relationship to any other event. It's only just tractable for one transaction: experienced FCers know that wrapping a true cash payment into a transaction when you have no relationship to fall back to in event of a hiccup is quite a serious challenge.
So we need a way to relate transactions, without infecting that way with human identity. Enter the nym, or more fully known as the psuedonymous identifier. This little thing can relate a bunch of things together without needing any special support.
We already use them extensively in email, and in chat. There are nyms like iang which are short and rather tricky to use because there are more than one of us. We can turn it into an email address, and that allows you to send a message to me using one global system, email. But spam has taught us a lesson with the email address, by wiping out the ease and reliability of the email nym ... leading to hotmail and the throw away address (for both offense and defense) and now the private email system.
Email has other problems (I predict it is dying!) which takes us to Instant Messaging (or chat or IM). The arisal of the peer-to-peer (p2p) world has taken nyms to the next level: disposable, and evolutionary.
This much we already know. P2P is the buzzword of the last 5 years. It's where the development of user activity is taking place. (When was the last time you saw an innovation in email? In browsing?)
Walking backwards ... p2p is developing the nym. And the nym is critical for creating the transactional framework for ecommerce. Which is getting beaten up badly by phishing, and there's an enveloping pincer movement developing in the strong human identity world.
But - and here's the clanger - when and as the nymous and cash based community develop and overcome their little difficulties, those aforementioned forces of darkness are going to turn on it with a vengeance. For different reasons, to be sure. For obvious example, the phishers are going to attack looking for that lovely cash. They are going to get rather rabid rather quickly when they work out what the pickings are.
Which means the mother of all security battles is looming for p2p. And unfortunately, it's one that we have to win, as otherwise, the ecommerce thing that they promised us in the late nineties is looking like a bit more like those fairy tales that don't have a happy ending. (Credit's going to be squeezed, remember.)
The good news is that I don't see why it can't be won. The great thing about p2p is the failure of standards. We aren't going to get bogged down by some dodgy 80's security model pulled out of the back pages of a superman comic, like those Mr Universe he-man kits that the guy with the funny name sold. No, this time, when the security model goes down in flames (several already have) we can simply crawl out of the wreckage, dust off and go find another fighter to fly into battle.
Let's reel off those battles already fought and won and lost. Napster, Kazaa, MNet, Skype, BitTorrent. There are a bunch more, I know, I just don't follow them that closely. Exeem this week, maybe I do follow them?
They've had some bad bustups, and they've had some victories, and for those in the systems world, and the security world, the progress is quite encouraging. Nothing looks insurmoutable, especially if you've seen the landscape and can see the integration possibilities.
But - and finally we are getting to the BIG BUT - that means whoever these guys are defeating ... is losing! Who is it? Well, it's the music industry. And hollywood.
And here's where it all comes together: ecommerce is going to face a devastating mix of over rich identity and over rich phishers. It'll shift to cash based and nym based, on the back of p2p. But that will shift the battle royale into p2p space, which means the current skirmishes are ... practice runs.
And now we can see why Hollywood is in such a desperate position. If the current battle doesn't see Hollywood go down for the count, that means we are in a world of pain: a troubling future for communication, a poor future for ecommerce, and a pretty stark world for the net. It means we can't beat the phisher.
Which explains why Hollywood and the RIAA have found it so difficult to get support on their fight: everyone who is familiar with Internet security has watched and cheered, not because they like to see someone robbed, but because they know this fight is the future of security.
I like Hollywood films. I've even bought a few kilograms of them. But the notion of losing my identity, losing my ability to trade and losing my ability to communcate securely with the many partners and friends I have over the net fills me with trepidation. I and much of the academic and security world can see the larger picture, even if we can't enunciate it clearly. I'd gladly give up another 10 years of blockbusters if I can trade with safety.
On the scales of Internet security, we have ecommerce on one side and Hollywood on the other. Sorry, guys, you get to take one for the team!
Addendum: I've just stumbled on a similar essay that was written 3 weeks before mine: The RIAA Succeeds Where the Cypherpunks Failed by Clay Shirky.
May 25, 2004
Identity Theft - the American Disease
Identity theft is a uniquely American problem. It reflects the massive - in comparison to other countries - use of data and credit to manage Americans' lives. Other countries would do well to follow the experiences, as "what happens there, comes here." Here are two articles on the modus operandi of the identity thief [1], and the positive side of massive data collection [2].
First up, the identity thief [1]. He's not an individual, he's a gang, or more like a farm. Your identity is simply a crop to process. Surprisingly, it appears that garbage collected from the streets (Americans call it trash) is still the seed material. Further, the database nation's targetting characteristics work for the thief as he doesn't need to "qualify" the victim any. If you receive lots of wonderful finance deals, he wants your business too.
Once sufficient information is collected (bounties paid per paper) it becomes a process of using PCs and innocent address authorities to weezle ones way into the prime spot. For example, your mail is redirected to the farm, the right mails are extracted, and your proper mail is conveniently re-delivered - the classic MITM. We all know paper identity is worthless for real security, but it is still surprising to see how easily we can be brought in to harvest.
[Addendum: Lynn Wheeler reports that a new study by Professor Judith Collins of Michigan State University reveals up to 70% of identity theft starts with employee insider theft [1.b]. This study, as reported by MSNBC, directly challenges the above article.]
Next up, a surprisingly thoughtful article on how data collection delivers real value - cost savings - to the American society [2]. The surprise is in the author, Declan McCullagh, who had previously been thought to be a bit of a Barbie for his sallacious use of gossip in the paparazzi tech press. The content is good but very long.
The real use of information is to make informed choices - not offer the wrong thing. Historically, this evolved as networks of traders that shared information. To counteract fraud that arose, traders kept blacklists and excluded no-gooders. A dealer exposed as misusing his position of power stood to lose a lot, as Adam Smith argued, far more indeed than the gain on any one transaction [3].
In the large, merchants with businesses exposed to public scrutiny, or to American-style suits, can be trusted to deal fairly. Indeed, McCullagh claims, the US websites are delivering approximately the same results in privacy protection as those in Europe. Free market wins again over centralised regulations.
Yet there is one area where things are going to pot. The company known as the US government, a sprawling, complex interlinking of huge numbers of databases, is above any consumer scrutiny and thus pressure for fair dealings. Indeed, we've known for some years that the policing agencies did an endrun around Congress' prohibition on databases by outsourcing to the private sector. The FBI's new purchase of your data from Checkpoint is "so secret that even the contract number may not be disclosed." This routine dishonesty and disrespect doesn't even raise an eyebrow anymore.
Where do we go from here? As suggested, the challenge is to enjoy the benefits of massive data conglomeration without losing the benefit of privacy and freedom. It'll be tough - the technological solutions to identity frauds at all levels from financial cryptographers have not succeeded in gaining traction, probably because they are so asymmetric, and deployment is so complicated as to rule out easy wins. Even the fairly mild SSL systems the net community put in place in the '90s have been rampantly bypassed by phishing-based identity attacks, not leaving us with much hope that financial cryptographers will ever succeed in privacy protection [4].
What is perhaps surprising is that we have in recent years redesigned our strong privacy systems to add optional identity tokens - for highly regulated markets such as securities trading [5]. The designs haven't been tested in the full, but it does seem as though it is possible to build systems that are both identity strong and privacy strong. In fact, the result seems to be stronger than either approach alone.
But it remains clear that deployment against an uninterested public is a hard issue. Every company selling privacy to my knowledge has failed. Don't hold your breath, or your faith, and keep an eye on how this so-far American disease spreads to other countries.
[1] Mike Lee & Brian Hitchen, "Identity Theft - The Real Cause,"
http://www.ebcvg.com/articles.php?id=217
[1.b] Bob Sullivan, "Study: ID theft usually an inside job,"
http://www.msnbc.msn.com/id/5015565
[2] Declan McCullagh, 'The upside of "zero privacy,"'
http://www.reason.com/0406/fe.dm.database.shtml
[3] Adam Smith, "Lecture on the Influence of Commerce on Manners," 1766.
[4] I write about the embarrassment known as secure browsing here:
http://iang.org/ssl/
[5] The methods for this are ... not publishable just yet, embarrassingly.
May 05, 2004
Cost of Phishing - Case in Texas
Below is the first quantitative estimate of costs for phishing that I have seen - one phisher took $75,000 from 400 victims. It's a number! What is needed now is a way to estimate what the MITM attack on secure browsing has done in terms of total damages across the net.
U.S. shuts down Internet 'phishing' scam
Monday, March 22, 2004 Posted: 3:59 PM EST (2059 GMT)
WASHINGTON (Reuters) -- The U.S. government said Monday it had arrested a Texas man who crafted fake e-mail messages to trick hundreds of Internet users into providing credit card numbers and other sensitive information.
Zachary Hill of Houston pleaded guilty to charges related to a "phishing" operation, in which he sent false emails purportedly from online businesses to collect sensitive personal information from consumers, the Federal Trade Commission said.
According to the FTC, Hill sent out official-looking e-mail notices warning America Online and Paypal users to update their accounts to avoid cancellation.
Those who clicked on a link in the message were directed to a Web site Hill set up that asked for Social Security numbers, mothers' maiden names, bank account numbers and other sensitive information, the FTC said.
Phishing has emerged as a favorite tool of identity thieves over the past several years and experts say it is a serious threat to consumers.
Hill used the information he collected to set up credit-card accounts and change information on existing accounts, the FTC said. He duped 400 users out of at least $75,000 before his operation was shut down December 4, FTC attorneys said.
Hill will be sentenced on May 17, according to court documents.
A lawyer for Hill was not immediately available for comment.
Scam artists have posed as banks, online businesses and even the U.S. government to gather personal information, setting up Web pages that closely mirror official sites.
FTC officials said consumers should never respond to an e-mail asking for sensitive information by clicking on a link in the message. "If you think the company needs your financial information, it's best to contact them directly," FTC attorney Lisa Hone said.
Those who believe they may be victims of identity theft should visit the FTC's Web site (www.consumer.gov/idtheft), she said.
America Online is a division of Time Warner Inc., as is CNN. Paypal is owned by eBay Inc.
Addendum: The FTC appears to have settled with Zachary. The amount phished is now set at $125k but is unrecovered. (This is over the *two* cases charged below, who appear to be the same case.)
"Phishers" Settle Federal Trade Commission Charges
Friday, June 18 2004 @ 06:17 AM Contributed by: ByteEnable
Operators who used deceptive spam and copycat Web sites to con consumers into turning over confidential financial information have agreed to settle Federal Trade Commission charges that their scam violated federal laws.
The two settlements announced today will bar the defendants from sending spam, bar them from making false claims to obtain consumers' financial information, bar them from misrepresenting themselves to consumers, and bar them from using, selling, or sharing any of the sensitive consumer information collected.
Based on financial records provided by the defendants, the FTC agreed to consider the $125,000 judgments in each case satisfied. If the court finds that the financial documents were falsified, however, the defendants will pay $125,000 in consumer redress. One of the defendants also faces 46 months in prison on criminal charges filed by the Justice Department.
The scam, called "phishing," worked like this: Posing as America Online, the con artists sent consumers e-mail messages claiming that there had been a problem with the billing of their AOL accounts. The e-mail warned consumers that if they did not update their billing information, they risked losing their accounts. The messages directed consumers to click on a hyperlink in the body of the e-mail to connect to the "AOL Billing Center." When consumers clicked on the link they landed on a site that contained AOL's logo, AOL's type style, AOL's colors, and links to real AOL Web pages. It appeared to be AOL's Billing Center. But it was not. The defendants had hijacked AOL's identity and used it to steal consumers' identities. The defendants ran a similar scam using the hijacked identity of PayPal.
The FTC charged the defendants with violating the FTC, which bars unfair and deceptive practices, and the Gramm Leach Bliley Act, which bars using false or fictitious statements to obtain consumers' financial information.
The settlements bar the defendants from sending spam for life. They bar the defendants from:
- Misrepresenting their affiliation with a consumer's ISP or online payment service provider;
- Misrepresenting that consumers' information needs to be updated;
- Using false "from" or "subject" lines; and
- Registering Web pages that misrepresent the host or sponsor of the page.
The settlements bar the defendants from making false, fictitious, or fraudulent statements to obtain financial information from consumers. They bar the defendants from using or sharing the sensitive information collected from consumers and require that all such information be turned over to the FTC. Financial judgments were stayed based on financial disclosure documents provided by the defendants showing they currently are unable to pay consumer redress. Should the court find that the financial disclosure documents were falsified, the defendants will be required to give up $125,000 in ill-gotten gains. The settlements contain standard record keeping provisions to allow the FTC to monitor compliance with the orders.
The defendant named in one of the complaints is Zachary Keith Hill. The Hill case was filed in December 2003, in the U.S. District Court for the Southern District of Texas. The other case, filed in May 2004, charged an unnamed minor in U. S. District Court for the Eastern District of New York.
These cases were brought with the invaluable assistance of the Department of Justice Criminal Division's Computer Crimes and Intellectual Property Section, Federal Bureau of Investigation's Washington Field Office, and United States Attorney for the Eastern District of Virginia's Computer Hacking and Intellectual Property Squad.
The Commission vote to accept the settlements was 5-0.
A newly revised FTC Consumer Alert, "How Not to Get Hooked by a 'Phishing' Scam" warns consumers who receive e-mail that claims an account will be shut down unless they reconfirm their billing information not to reply or click on the link in the e-mail. Consumers should contact the company that supposedly sent the message directly. More tips to avoid phishing scams can be found at http://www.ftc.gov/bcp/conline/pubs/alerts/phishingalrt.htm.
Consumers who believe they have been scammed by a phishing e-mail can file a complaint at http://www.ftc.gov, and then visit the FTC's Identity Theft Web site at www.consumer.gov/idtheft to learn how to minimize their risk of damage from ID theft. Consumers can also visit www.ftc.gov/spam to learn other ways to avoid e-mail scams and deal with deceptive spam.
NOTE: Stipulated final judgments and orders are for settlement purposes only and do not constitute an admission by the defendant of a law violation. Consent judgments have the force of law when signed by the judge.
Copies of the complaints and stipulated final judgments and orders are available from the FTC's Web site at http://www.ftc.gov and also from the FTC's Consumer Response Center, Room 130, 600 Pennsylvania Avenue, N.W., Washington, D.C. 20580. The FTC works for the consumer to prevent fraudulent, deceptive, and unfair business practices in the marketplace and to provide information to help consumers spot, stop, and avoid them. To file a complaint in English or Spanish (bilingual counselors are available to take complaints), or to get free information on any of 150 consumer topics, call toll-free, 1-877-FTC-HELP (1-877-382-4357), or use the complaint form at http://www.ftc.gov. The FTC enters Internet, telemarketing, identity theft, and other fraud-related complaints into Consumer Sentinel, a secure, online database available to hundreds of civil and criminal law enforcement agencies in the U.S. and abroad.





