June 29, 2017
SegWit and the dispersal of the transaction
 Jimmy Nguyen criticises SegWit on the basis that it breaks the signature of a contract according to US law. This is a reasonable argument to make but it is also not a particularly relevant one. In practice, this only matters in the context of a particularly vicious and time-wasting case. You could argue that all of them are, and lawyers will argue on your dime that you have to get this right. But actually, for the most part, in court, lawyers don’t like to argue things that they know they are going to lose. The contract is signed, it’s just not signed in a particularly helpful fashion. For the most part, real courts and real judges know how to distinguish intent from technical signatures, so it would only be relevant where the law states that a particular contract must be signed in a particular way, and then we’ve got other problems. Yes, I know, UCC and all that, but let’s get back to the real world.
Jimmy Nguyen criticises SegWit on the basis that it breaks the signature of a contract according to US law. This is a reasonable argument to make but it is also not a particularly relevant one. In practice, this only matters in the context of a particularly vicious and time-wasting case. You could argue that all of them are, and lawyers will argue on your dime that you have to get this right. But actually, for the most part, in court, lawyers don’t like to argue things that they know they are going to lose. The contract is signed, it’s just not signed in a particularly helpful fashion. For the most part, real courts and real judges know how to distinguish intent from technical signatures, so it would only be relevant where the law states that a particular contract must be signed in a particular way, and then we’ve got other problems. Yes, I know, UCC and all that, but let’s get back to the real world.
But there is another problem, and Nguyen’s post has triggered my thinking on it. Let’s examine this from the perspective of triple entry. When we (by this I mean to include Todd and Gary) were thinking of the problem, we isolated each transaction as being essentially one atomic element. Think of an entry in accounting terms. Or think of a record in database terms. However you think about it, it’s a list of horizontal elements that are standalone.
When we sign it using a private key, we take the signature and append it to the entry. By this means, the entry becomes stronger - it carries its authorisation - but it still retains its standalone property.
So, with the triple entry design in that old paper, we don’t actually cut anything out of the entry, we just make it stronger with an appended signature. You can think of it as is a strict superset of the old double entry and even the older single entry if you wanted to go that far. Which makes it compatible which is a nice property, we can extract double entry from triple entry and still use all the old software we’ve built over the last 500 years.
And, standalone means that Alice can talk to Bob about her transactions, and Bob can talk to Carol about his transaction without sharing any irrelevant or private information.
Now, Satoshi’s design for triple entry broke the atomicity of transactions for consensus purposes. But it is still possible to extract out the entries out of the UTXO, and they remain standalone because they carry their signature. This is especially important for say an SPV client, but it’s also important for any external application.
 Like this: I’m flying to Shanghai next week on Blockchain Airlines, and I’ve got to submit expenses. I hand the expenses department my Bitcoin entries, sans signatures, and the clerk looks at them and realises they are not signed. See where this is going? Because, compliance, etc, the expenses department must now be a full node. Not SPV. It must now hold the entire blockchain and go searching for that transaction to make sure it’s in there - it’s real, it was expended. Because, compliance, because audit, because tax, because that’s what they do - check things.
Like this: I’m flying to Shanghai next week on Blockchain Airlines, and I’ve got to submit expenses. I hand the expenses department my Bitcoin entries, sans signatures, and the clerk looks at them and realises they are not signed. See where this is going? Because, compliance, etc, the expenses department must now be a full node. Not SPV. It must now hold the entire blockchain and go searching for that transaction to make sure it’s in there - it’s real, it was expended. Because, compliance, because audit, because tax, because that’s what they do - check things.
If Bitcoin is triple entry, this is making it a more expensive form of triple entry. We don’t need those costs, bearing in mind that these costs are replicated across the world - every user, every transaction, every expenses report, every accountant. For the cost of including a signature, an EC signature at that, the extra bytes gain us a LOT of strength, flexibility and cost savings.
(You could argue that we have to provide external data in the form of the public key. So whoever’s got the public key could also keep the sigs. This is theoretically true but is starting to get messy and I don’t want to analyse right now what that means for resource, privacy, efficiency.)
Some might argue that this causes more spread of Bitcoin, more fullnodes and more good - but that’s the broken window fallacy. We don’t go around breaking things to cause the economy to boom. A broken window is always a dead loss to society, although we need to constantly remind the government to stop breaking things to fix them. Likewise, we do not improve things by loading up the accounting departments of the world with additional costs. We’re trying to remove those costs, not load them up, honestly!
Then, but malleability! Yeah, that’s a nuisance. But the goal isn’t to fix malleability. The goal is to make the transactions more certain. Segwit hasn’t made transactions more certain if it has replaced one uncertainty with another uncertainty.
Today, I’m not going to compare one against the other - perhaps I don’t know enough, and perhaps others can do it better. Perhaps it is relatively better if all things are considered, but it’s not absolutely better, and for accounting, it looks worse.
Which does rather put the point on ones worldview. SegWit seems to retain the certainty but only as outlined above: when ones worldview is full nodes, Bitcoin is your hammer and your horizon. E.g., if you’re only thinking about validation, then signatures are only needed for validation. Nailed it.
But for everyone else? Everyone else, everyone outside the Bitcoin world is just as likely to simply decline as they are to add a full node capability. “We do not accept Bitcoin receipts, thanks very much.”
Or, if you insist on Bitcoin, you have to go over to this authority and get a signed attestation by them that the receipt data is indeed valid. They’ve got a full node. Authenticity as a service. Some will think “business opportunity!” whereas others will think “huh? Wasn’t avoiding a central authority the sort of thing we were trying to avoid?”
 I don’t know what the size of the market for interop is, although I do know quite a few people who obsess about it and write long unpublished papers (daily reminder - come on guys, publish the damn things!). Personally I would not make that tradeoff. I’m probably biased tho, in the same way that Bitcoiners are biased: I like the idea of triple entries, in the same way that Bitcoiners like UTXO. I like the idea that we can rely on data, in the same way that Bitcoiners like the idea that they can rely on a bunch of miners.
I don’t know what the size of the market for interop is, although I do know quite a few people who obsess about it and write long unpublished papers (daily reminder - come on guys, publish the damn things!). Personally I would not make that tradeoff. I’m probably biased tho, in the same way that Bitcoiners are biased: I like the idea of triple entries, in the same way that Bitcoiners like UTXO. I like the idea that we can rely on data, in the same way that Bitcoiners like the idea that they can rely on a bunch of miners.
Now, one last caveat. I know that SegWit in all its forms is a political food fight. Or a war, depending your use of the language. I’m not into that - I keep away from it because to my mind war and food fights are a dead loss to society. I have no position one way or the other. The above is an accounting and contractual argument, albeit with political consequences. I’m interested to hear arguments that address the accounting issues here, and not at all interested in arguments based on “omg you’re a bad person and you’re taking money from my portfolio.”
I’ve little hope of that, but I thought I’d ask :-)
October 23, 2016
Bitfinex - Wolves and a sheep voting on what's for dinner
 When Bitcoin first started up, although I have to say I admired the solution in an academic sense, I had two critiques. One is that PoW is not really a sustainable approach. Yes, I buy the argument that you have to pay for security, and it worked so it must be right. But that's only in a narrow sense - there's also an ecosystem approach to think about.
When Bitcoin first started up, although I have to say I admired the solution in an academic sense, I had two critiques. One is that PoW is not really a sustainable approach. Yes, I buy the argument that you have to pay for security, and it worked so it must be right. But that's only in a narrow sense - there's also an ecosystem approach to think about.
Which brings us to the second critique. The Bitcoin community has typically focussed on security of the chain, and less so on the security of the individual. There aren't easy tools to protect the user's value. There is excess of focus on technologically elegant inventions such as multisig, HD, cold storage, 51% attacks and the like, but there isn't much or enough focus in how the user survives in that desperate world.
Instead, there's a lot of blame the victim, saying they should have done X, or Y or used our favourite toy or this exchange not that one. Blaming the victim isn't security, it's cannibalism.
Unfortunately, you don't get out of this for free. If the Bitcoin community doesn't move to protect the user, two things will happen. Firstly, Bitcoin will earn a dirty reputation, so the community won't be able to move to the mainstream. E.g., all these people talking about banks using Bitcoin - fantasy. Moms and pops will be and remain safer with money in the bank, and that's a scary thought if you actually read the news.
Secondly, and worse, the system remains vulnerable to collapse. Let's say someone hacks Mt.Gox and makes a lot of money. They've now got a lot of money to invest in the next hack and the next and the next. And then we get to the present day:
Message to the individual responsible for the Bitfinex security incident of August 2, 2016We would like to have the opportunity to securely communicate with you. It might be possible to reach a mutually agreeable arrangement in exchange for an enormous bug bounty (payable through a more privacy-centric and anonymous way).
So it turns out a hacker took a big lump of Bitfinex's funds. However, the hacker didn't take it all. Joseph VaughnPerling tells me:
"The bitfinex hack took just about exactly what bitfinex had in cold storage as business profit capital. Bitfinex could have immediately made all customers whole, but then would have left insufficient working capital. The hack was executed to do the maximal damage without hurting the ecosystem by putting bitfinex out of business. They were sure to still be around to be hacked again later.It is like a good farmer, you don't cut down the tree to get the apples."
A carefully calculated amount, coincidentally about the same as Bitfinex's working capital! This is annoyingly smart of the hacker - the parasite doesn't want to kill the host. The hacker just wants enough to keep the company in business until the next mafiosa-style protection invoice is due.
So how does the company respond? By realising that it is owned. Pwn'd the cool kids say. But owned. Which means a negotiation is due, and better to convert the hacker into a more responsible shareholder or partner than to just had over the company funds, because there has to be some left over to keep the business running. The hacker is incentivised to back off and just take a little, and the company is incentivised to roll over and let the bigger dog be boss dog.
Everyone wins - in terms of game theory and economics, this is a stable solution. Although customers would have trouble describing this as a win for them, we're looking at it from an ecosystem approach - parasite versus host.
But, that stability only survives if there is precisely one hacker. What happens if there are two hackers? What happens when two hackers stare at the victim and each other?
Well, it's pretty easy to see that two attackers won't agree to divide the spoils. If the first one in takes an amount calculated to keep the host alive, and then the next hacker does the same, the host will die. Even if two hackers could convert themselves into one cartel and split the profits, a third or fourth or Nth hacker breaks the cartel.
The hackers don't even have to vote on this - like the old joke about democracy, when there are 2 wolves and 1 sheep, they eat the sheep immediately. The talk about voting is just the funny part for human consumption. Pardon the pun.
The only stability that exists in the market is if there is between zero and one attacker. So, barring the emergence of some new consensus protocol to turn all the individual attackers into one global mafiosa guild, a theme frequently celebrated in the James Bond movies, this market cannot survive.
To survive in the long run, the Bitcoin community have to do better than the banks - much better. If the Bitcoin community wants a future, they have to change course. They have to stop obsessing about the chain's security and start obsessing about the user's security.
The mantra should be, nobody loses money. If you want users, that's where you have to set the bar - nobody loses money. On the other hand, if you want to build an ecosystem of gamblers, speculators and hackers, by all means, obsess about consensus algorithms, multisig and cold storage.
ps; I first made this argument of ecosystem instability in "Bitcoin & Gresham's Law - the economic inevitability of Collapse," co-authored with Philipp Güring.
July 17, 2016
Ricardian Contracts in the media!
Ricardian Contracts were featured in R3's event on Smart Contract Templates in coordination with Barclays.
 See the deck, pages 44-67. The Riccy formed a big part of that event as the idea of laying out the prose contract alongside the smart code are now becoming evidently necessary as well as just merely necessary. The R3 weekend read pulls quotes from IBTimes / Lee Braine and Richard Gendal Brown:
See the deck, pages 44-67. The Riccy formed a big part of that event as the idea of laying out the prose contract alongside the smart code are now becoming evidently necessary as well as just merely necessary. The R3 weekend read pulls quotes from IBTimes / Lee Braine and Richard Gendal Brown:
The following pull quote is best contrasted with The DAO entry at the beginning of this post:Braine said that one of the motivations for creating smart contracts, together with shared ledgers underneath them, is the opportunity to reduce the number and duration of disputes. Some of the potential improvements could result from simply making the relevant information, such as agreements governing specific trades, more easily accessible.Brown agreed, adding: "If you look at the experience with The DAO recently, one of the key takeaways from that incident was that, in a system that perhaps had an express design goal of having the code be dominant, there is a need to have a broader contract that explains what happens in the event that things do go wrong."
This future of contracting sees a layout of {prose, code, params} which fully describe a smart contract entered into by parties, something I talked about in SOAC a while back.
Instead of the normal boring presentation on 'what' the Ricardian Contract is, I talked about 'why' with the hope that, by understanding the research origins that led to the design pattern, it would be clearer why it has to be so. I hope we can do a voice release or article / paper at some point so a little more context can be explained.
And, to round off the news, we now have the Ricardian Contract's own wikipedia page. Thanks to Arthur Doohan for that hard work!
June 18, 2016
Ethereum is one step away from creating a workable smart contracting community
To live in interesting times!
First TheDAO started up as a crowd funded smart contract which took in about $160m of contributions. Hoorah!Then, a programmer spotted a bug and used it to sweep about $60m across to own account. Howzat!?
Next, the Ethereum coredevs reacted in collective angst and moved to unwind the 'theft.' Hooray!
Finally, someone called "attacker" claimed credit for the actions, and reminded everyone that there was a legal contract in place. YeeHaa!
Ethereum is the reality TV of the new financial cryptographic generation. However, let's not be entirely damning, it is also important to take pause and review what they have achieved. Positively.
Firstly, Ethereum has established beyond a doubt that the smart code needs to be part of a wider agreement at law. You can see this on the Explainer page of TheDAO where it carefully lays out:
"When you click the “I Accept” button or check box presented with the terms you are agreeing that you are taking part in The DAO’s Creation under the terms set forth in The DAO’s smart contract code at your own risk."
By clicking "I Accept", you enter into a legal contract, with the above text as part thereof.
To see that it is a legal contract, imagine if it didn't exist - in the absence of an agreement, there is no party who claims responsibility for TheDAO, and therefore TheDAO is abandoned at law. Which means that anyone can do whatever they like. Indeed, that means whoever can claim the value within can do so - it's like an abandoned ship at sea or unclaimed land; first person to plant a flag is the winner.
Clearly, the founders of TheDAO were smart enough not to want their smart contract to be 'abandoned' so it/they must and did enter into a legal agreement with contributors to (a) exert existence and (b) exert its authority to control the assets on behalf of the beneficiaries.
Having asserted its capacity to act, it also asserts that the smart code dominates over the legal prose:
The terms of The DAO Creation are set forth in the smart contract code existing on the Ethereum blockchain at 0xbb9bc244d798123fde783fcc1c72d3bb8c189413. Nothing in this explanation of terms or in any other document or communication may modify or add any additional obligations or guarantees beyond those set forth in The DAO’s code.
This is the correct order, which you can divine if you follow the logic: the legal agreement is prime over the smart code because it can bind the humans, and the legal agreement then has to defer primacy explicitly to any or all terms in the smart code. In summary, TheDAO has now exemplified 3 principles.
- The smart contract is a contract at law.
- The smart contract includes both code and prose.
- The legal prose asserts the capacity of the contract to act, a role outside the capability of the code;
- a purported smart contract without that capacity is likely abandoned, and also a statement that the authors are not smart enough to defend the property they create;
- the code requests that you click "I agree," a role outside the capability of the legal prose; and
- if you as user haven't clicked "I agree" or otherwise recorded your intent, then the smart contract is at liberty to ignore you - no intent established, no contract entered into.
- The legal prose rules over the smart contract.
- Then, the legal prose may with words pass the legal dominance to any part or all of the smart code; and
- indeed that might be the only thing that the legal prose does! But see below...
With these principles in hand, we are almost at the point of a viable smart contracting industry. And, we can thank the evolutionary efforts of many for this: Nick Szabo for the abstraction now called the smart contract, Satoshi for converting Nick's abstraction into the inspired form in Bitcoin, the Ethereum team for their more Turing-complete environment, and the authors of TheDAO for their big reveal of what it takes to make a real smart contract. What a social experiment!
On behalf of the entire Internet, I thank you. But we are still one step short of a complete smart contracting environment.
Recall that the point of a contract be it smart, simple, dumb or otherwise, is to create certainty over the uncertain agreements of human agents. Think about that statement for a moment - the goal is to create certainty. Got it? Now look at TheDAO and ask what you see?
Uncertainty.
If there is a better example of uncertainty in cryptographic affairs than TheDAO, I do not know of it, off hand. Indeed, the current life of TheDAO is so uncertain, it is likely to become a catchphrase for uncertainty in smart contracting!
Right? Let's list the ways. We have half the community up in arms that the terms of the smart code are going to be overridden and thus their contractual worldview is going to be overturned. We've the other half up in arms over the fact that someone has scarfed up a good chunk of the contents, and thus has breached the intent of the contract. And, now we have the Ethereum coredev team asserting their authority for a hard fork, and "Attacker" reminding them that there is a legal contract:
I am disappointed by those who are characterizing the use of this intentional feature as "theft". I am making use of this explicitly coded feature as per the smart contract terms and my law firm has advised me that my action is fully compliant with United States criminal and tort law. For reference please review the terms of the DAO:"The terms of The DAO Creation are set forth in the smart contract code existing on the Ethereum blockchain at 0xbb9bc244d798123fde783fcc1c72d3bb8c189413. Nothing in this explanation of terms or in any other document or communication may modify or add any additional obligations or guarantees beyond those set forth in The DAO’s code. Any and all explanatory terms or descriptions are merely offered for educational purposes and do not supercede or modify the express terms of The DAO’s code set forth on the blockchain; to the extent you believe there to be any conflict or discrepancy between the descriptions offered here and the functionality of The DAO’s code at 0xbb9bc244d798123fde783fcc1c72d3bb8c189413, The DAO’s code controls and sets forth all terms of The DAO Creation."
A soft or hard fork would amount to seizure of my legitimate and rightful ether, claimed legally through the terms of a smart contract. ...
When we have such strong, valid-on-the-face arguments, at dramatically opposing poles, we have ... a dispute. TheDAO is now in fatal dispute. And what Ethereum lacks is a clear way forward to resolve that dispute.
Let's check the options. "Attacker" suggests a United States reading of the law, which suggests a USA court. USA courts typically accept any case for any nexus. But they will likely not accept the contract as valid under the securities laws in the USA, so Attacker will likely also find surprise in the event that it goes there. No matter, at $60million or whatever it is is well worth this minute, someone might try their luck in court.
And for the most part, Ethereum people are apparently located in Europe - London, Berlin, Switzerland. I'm not saying TheDAO was done by these people, but if Attacker knows who they are, and this seems reasonable, and any lawsuit names the authors and founders of TheDAO, what have we got?
A mess. What we haven't got is resolution. We can see a law suit that ricochets around the globe and locks a lot of people up in a world of pain. Everyone loses. We can see echoes of Assange and Snowden - we'll get articles, books, movies, but the one thing we won't get is ... resolution.
Certainty, this ain't.
And this is the critical step that Ethereum is short of - resolution, certainty. The traditional courts of law are not well suited to resolving this sort of dispute for a myriad of reasons - both good and bad.
Which brings us to the inevitable discovery that Ethereum must now make. There is a way that can give certainty to this mess in the general case; there is a way to resolve this sort of dispute. It is beholden on the community to find that forum of dispute resolution that can bring certainty to the smart contract when the smart contract itself has lost certainty.
Ethereum needs to set up its own forum - its own court - a court of smart contract dispute resolution.
This is not a trivial task; but it is a lot easier than you think. It's a matter of law, the choice is called Arbitration, and if you search around you can find volumes written on it. I'll leave that as an exercise for the reader, but you might want to look at DAMN. That's not how I would do it, but hey - compare and contrast!
Know it now - you face a fork in the road. On the one hand you have the failed social experiment known as TheDAO. On the other hand, you have your own forum of dispute resolution, designed to resolve precisely this mess, the smart contract in trouble. Like some science fiction movie, the choice is clear: choose to repeat the failure in TheDAO, or choose to engage in informed dispute resolution, customised for your disputes.
Choose quickly, before the next big reveal. Good luck.
Some notes.
- I'm handwaving over some elements of the legal arguments above, as I haven't identified precisely where the contract is entered. But that can be left as an exercise to the reader.
- Vitalik argues that there is no cryptographic connection. That's an odd argument, because (a) nobody's argued in court yet that there has to be a cryptographic connnection, (b) that argument reduces to "Vitalik doesn't attest to it being the contract" whereas (c) we need to go much much more, like "it isn't the contract because this other thing is the contract." Oh, and (d) we can guarantee that the court will look favourably on anything that looks like a contract, and will be entirely skeptical of a prose-free lump of code.
- I haven't talked about the parties to the contract at all in the above. That's because we don't need to - in this context. A given case may need to, but actually in TheDAO case, we don't need to. It could be entirely sufficient for the ethcore team to present the evidence as expert witnesses, and the Arbitrator to return a ruling authorising a hard fork. The parties do not need to be examined unless the case demands it.
June 17, 2015
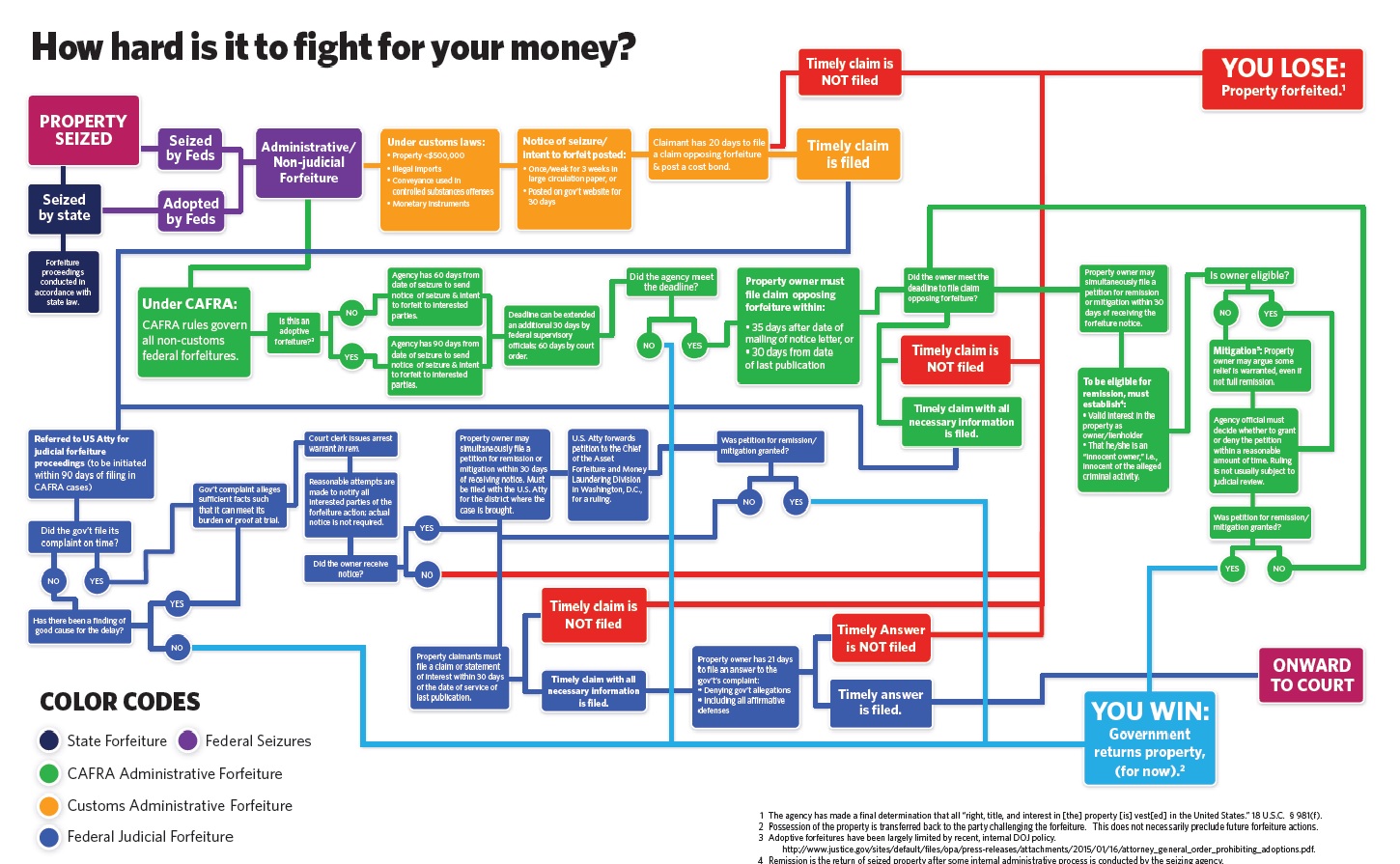
Cash seizure is a thing - maybe this picture will convince you
There are many many people who do not believe that the USA police seize cash from people and use it for budget. The system is set up for the benefit of police - budgetary plans are laid, you have no direct recourse to the law because it is the cash that defends itself, the proceeds are carved up.
Maybe this will convince you - if cash seizure by police wasn't a 'thing' we wouldn't need this chart:
January 17, 2015
Scott on blockchains -- could these fussy smartcontracts change anything?
Brett Scott disassembles the Bitcoin 2.0 visionary concept surrounding contracts:
The political vision 2.0By removing a central point of control, decentralised systems based on code - whether they exist to move Bitcoin tokens around, store files, or build contracts - resemble self-contained robots. Mark Zuckerberg of Facebook or Jamie Dimon of JP Morgan Chase are human faces behind the digital interface of the services they run. They can overtly manipulate, or bow in to pressure to censor. A decentralised currency or a decentralised version of Twitter seems immune from such manipulation.
It is this that gives rise to a narrative of empowerment and, indeed, at first sight this offers an exhilarating vision of self-contained outposts of freedom within a world otherwise dominated by large corruptible institutions. At many cryptocurrency meet-ups, there is an excitable mix of techno-babble infused with social claims. The blockchain can record contracts between free individuals, and if enforcement mechanisms can be coded in to create self-enforcing 'smart contracts', we have a system for building encoded law that bypasses states.
Which is super, on the face of it, until we get to the nub of what contracts actually do for you:
This, of course, appeals to those who believe that powerful institutions operate primarily by breaching property rights and contracts. Who really believes that though? For much of modern history, the key issue with powerful institutions has not been their willingness to break contracts. It has been their willingness to use seemingly unbreakable contracts to exert power. Contracts, in essence, resemble algorithms, coded expressions of what outcomes should happen under different circumstances. On average, they are written by technocrats and, on average, they reflect the interests of elite classes.That is why liberation movements always seek to break contracts set in place by old regimes, whether it be peasant movements refusing to honour debt contracts to landlords, or the DRC challenging legacy mining concessions held by multinational companies, or SMEs contesting the terms of swap contracts written by Barclays lawyers. Political liberation is as much about contesting contracts as it is about enforcing them.
And, boom! Which pretty much destroys the case for contracts on the blockchain as they are currently envisaged, because once enslaved to them there is no breaking them. Now, people aren't so stupid, and once the first person falls badly, the word will spread - DON'T CONTRACT ON THE BLOCKCHAIN!
Building the techno-political vision 3.0.... The concept of the decentralised blockchain is powerful. The cold, distrustful edge of cypherpunk, though, is only empowering when it is firmly in the service of creative warm-blooded human communities situated in the physical world of dirt and grime.
So far, relatively little attention has been paid to the question of returning the blockchain back to the service of warm-blooded humanity. There is a sense of multisig, but its promise is seen in its elegant cryptography not in the underlying need. To paraphrase someone, Bitcoinatics have never seen a societal problem that they couldn't solve with liberal dollops of cryptography, or by redefining the problem to be a non-problem.
Let's look at that underlying. The proof of a contract, pudding-wise, is not the completion of the machinery, the end of the game, but the willingness of the participants to enter again, to hit Play Again. This is predicated on two things, being the economic efficacy of the last round(s) and the fair treatment of any surprises.
Surprisal, the property of a contract to cause issues that are unexpected, have to be dealt with in a fair way, and by this the ultimate test is literally whether society moves on with new trades, new contracts, new business based on this contract, on this set of rules.
I speak of course of dispute resolution. So the challenge then for the blockchain is how to introduce the resolution of surprises into the machinery.
We do not want a future society free from people we have to trust, or one in which the most we can hope for is privacy. Rather, we want a world in which technology is used to dilute the power of those systems that cause us to doubt trust relationships. Screw escaping to Mars.
It's not really a technological imperative but a human one: people don't and won't trust a technology that screws them over. And the Ethereum / Bitcoin / etc smart contracts world are busily building their system in perfect form to do exactly that: let a savvy programmer screw over a stupid customer who perforce can't read computer code.
The good news is that this thing called smartcontracts will not get off the ground when or if it screws over the illiterate. The bad news is that a lot of energy will be wasted up to that point, and then a lot more as the hyperintelligent supernaivetes moan on why the mainstream users don't want a part of it.
We could probably short-circuit that - and ask, how we get some form of surprisal management into these things, before they get broken in the market of public opinion?
November 21, 2014
Banking - licensed to cheat! And whether you'll get away with it.
Research into what most people will feel is so trivially true that the research wasn't needed has been conducted -- are bankers cheats?
The subjects took part in a simple experiment of flipping a coin, and involved around two hundred bankers, including 128 from a single unnamed international bank. They were divided into two groups. The people from the first were asked specifically about their jobs in banking, while the other half were asked unrelated questions."The rules required subjects to take any coin, toss it 10 times, and report the outcomes online," the researchers reported in the journal Nature. "For each coin toss they could win an amount equal to approximately $20 depending on whether they reported 'heads' or 'tails'."
The point is that the players were told ahead of the game whether "heads" or "tails" would win as well as in which case they could keep their winnings.
Given maximum winnings of $200, there was "a considerable incentive to cheat," wrote the team of researchers.
The bankers were asked to fill out questionnaires before tossing each coin. Those who were asked about things unrelated to their job hardly ever cheated in the coin toss, reporting 51.6 percent wins.
But those asked about their banking careers made the cheat rate go up - they reported 58.2 percent as wins. If everyone was completely honest, the proportion of winning tosses in each group would be 50 percent.
That's actually a stunning result. Just talking about banking made the bankers cheat! As an aside, this research is a dead cert for the IgNoble awards, a sort of faux Noble in odd science which celebrates wacky research that on the face of it should not have been conducted, but in actuality reveals some interesting results.
Back to the banking cheats. Up until now, there has been a stunning silence on the behalf of the prosecution authorities for what is likely either the #1 or #2 crisis in modern history. So bankers are confirmed in their skulduggery, they will almost certainly get away with it.
What can we as society do about this? Putting some of them in jail has been commented as what is missing, indeed the reason we're likely confirmed that banking as a whole is a poisoned pot is that nobody's gone to jail for the financial crisis.
In Britain, last month, a crown court in London announced:
"A senior banker from a leading British bank pleaded guilty at Southwark Crown Court on 3 October 2014 to conspiracy to defraud in connection with manipulating Libor," the court said in a statement."This arises out of the Serious Fraud Office investigations into Libor fixing."
And, in Iceland a world-wide first:
Nov 19 (Reuters) - The former chief executive of Landsbanki, one of three banks that racked up $75 billion in debt before collapsing and crashing the economy in 2008, was sentenced to one year in jail on Wednesday for market manipulation.Sigurjon Arnason was convicted of manipulating the bank's share price and deceiving investors, creditors and the authorities in the dying days of the bank between Sept. 29 and Oct. 3, 2008.
The Reykjavik District Court said nine months of Arnason's sentence were suspended. Ivar Gudjonsson, former director of proprietary trading, and Julius Heidarsson, a former broker, were also convicted and received nine-month sentences, six of which were suspended. All pleaded innocent to the charges.
"This sentence is a big surprise to me as I did not nothing wrong," Sigurjon Arnason told Reuters after the sentencing, adding that he and his attorney had not yet decided whether to appeal to the supreme court.
More:
In receiving a one year prison sentence, Sigurjon Arnason officially became the first bank executive to be convicted of manipulating the bank's stock price and deceiving investors, creditors and the authorities between Sept. 29 and Oct. 3, 2008, as the bank's fortunes unwound, crashing the economy with it. Landsbanki was one of three banks that had tallied nearly $75 billion in debt before the final curtain was drawn.All pleaded innocent to the charges...
February 18, 2014
Why Dispute Resolution is hard -- but not so elusive as to escape solutions
 Steven J. Murdoch and Ross Anderson have released a paper entitled "Security Protocols and Evidence: Where Many Payment Systems Fail," to be presented in a few weeks in Financial Cryptography Conference, in Barbados. It is very welcome to point people in the direction of dispute resolution, because it is indeed a make or break area for payment systems.
Steven J. Murdoch and Ross Anderson have released a paper entitled "Security Protocols and Evidence: Where Many Payment Systems Fail," to be presented in a few weeks in Financial Cryptography Conference, in Barbados. It is very welcome to point people in the direction of dispute resolution, because it is indeed a make or break area for payment systems.
The paper itself is a light read, with some discussion of failures, and some suggestions of what to do about it. Where it gets interesting is that the paper tries to espouse some Principles, a technique I often use to get my thoughts in order. Let's look at them:
Principle 1: Retention and disclosure. Protocols designed for evidence should allow all protocol data and the keys needed to authenticate them to be publicly disclosed, together with full documentation and a chain of custody.Principle 2: Test and debug evidential functionality. When a protocol is designed for use in evidence, the designers should also specify, test and debug the procedures to be followed by police officers, defence lawyers and expert witnesses.
Principle 3: Open description of TCB. Systems designed to produce evidence must have an open specification, including a concept of operations, a threat model, a security policy, a reference implementation and protection profiles for the evaluation of other implementations.
Principle 4: Failure-evidentness. Transaction systems designed to produce evidence must be failure-evident. Thus they must not be designed so that any defeat of the system entails the defeat of the evidence mechanism.
Principle 5: Governance of forensic procedures. The forensic procedures for investigating disputed payments must be repeatable and be reviewed regularly by independent experts appointed by the regulator. They must have access to all security breach notifications and vulnerability disclosures.
I have done these things in the past, in varying degrees and fashions, so they are pointing in the right direction, but I feel /as principles/, they fall short.
Let's work through them. With P1, public disclosure immediately strikes an issue. This is similar to the Bitcoin mentality that the blockchain should be public, something which has become so tantalising that regulators are even thinking about mandating it.
But we live in a world of crooks. Does this mean that a new attack is now about to become popular -- using the courts to force the publication of ones victim's secrets? The reason for financial privacy is to stop scumbags knowing where the loot is, and that is a good reason. As we enter a more transparent world for crooks, because of such innovations as Internet data tracking, economic intelligence harvesting, drugs-ML, AML, sharing of seized value by government agencies, monolithic banks incentivised to cross-sell and compete, etc, the need for financial privacy goes up not down.
If you look at M&A's paper, the frustration in the courts that they faced was that the banks argued they couldn't disclose the secrets. Yet, courts readily deal with this already. Lawyers know how to keep secrets, it's their job. So we're really facing a different problem, which is that the banks snowed the judge with bluff and bluster, and the judge didn't blink. As Stephen Mason writes in "Debit Cards, ATMs and the negligence of the bank and customer," in Butterworths Journal of International Banking and Financial Law, March 2012, also Appendix 10, When Bank Systems Fail:
"The only reason the weaknesses have been revealed in some instances, as discussed in this article, is because the banks were required to cooperate with the investigating authorities and explain and provide evidence of such weaknesses before the criminal courts. In civil actions, the banks have no incentive to reveal such weaknesses. The banks will deny that their systems suffer from any weaknesses, placing the blame squarely on the customer."
The real problem here is that banks do not want to provide the evidence; for them, suppression of the evidence is part of their business process, a feature not a bug. Hence, Principle 1 above is not sufficient, and it could be written more simply:
P1. Payment protocols should be designed for evidence.
which rules out the Banks' claims. But even that doesn't quite work. Now, I'm unsure how to make this point in words, so I'll simply slam it out:
P1. Payment protocols should be designed to support dispute resolution.
Which is a more subtle, yet comprehensive principle. To a casual outside observer it might appear the same, because people typically see dispute resolution as the presentation of evidence, and to our inner techie, they see our role as the creation of that evidence.
But, dispute resolution is far more important that that. How are you filing a dispute? Who is the judge? Where are you and what is your law? Who holds the burden of proof? What is the boundary between testimony and digital evidence? In the forum you have chose, what are the rules of procedure? How do they affect your case?
These are seriously messy questions. Take the recent British cases of Shojibur Rahman v Barclays Bank PLC as reported (judgement, appeal) in Digital Evidence and Electronic Signature Law Review, 10 (2013). In this case, a fraudster apparently tricked the victim into handing over a card and also the PIN. This encouraged Barclays to claim no liability for the frauds that followed.
Notwithstanding this claim, the bank is required to show that it authenticated the transactions. In both of the two major transactions conducted by the fraudster, the bank failed to show that they had authenticated the transactions correctly. In the first, Barclays presented no evidence one way or another, and the card was not in use for that transaction, so the bank simply failed to meet its burden of proof, as well as its own standards of authentication as it was undisputed that the fraudster initiated the transaction. In the second, secret questions were asked by the bank as the transaction was suitably huge, and wrong answers were accepted.
Yet, in district court and on appeal the judges held that because the victim had failed in his obligation to keep the card secure, defendant Barclays was relieved of its duty to authenticate the transactions. This is an outstanding blunder of justice -- if the victim makes even one mistake then the banks can rest easy.
Knowing that the banks can refuse to provide evidence, knowing that the systems are so complex that mistakes are inevitable, knowing that the fraudsters conduct sophisticated and elegant social attacks, and knowing that the banks prepared the systems in the first place, this leaves the banks in a pretty position. They are obviously encouraged to hold back from supporting their customer as much as possible.
What is really happening here is a species of deception, and/or fraud, sometimes known as liability shifting or dumping. The banks are actually making a play to control and corral the dispute resolution into the worst place possible for you, and the best place for them -- their local courts. Meanwhile, they are telling you the innocent victim, that they've got it all under control, and your rights are protected.
In terms of P1 above, they are actually designing their system to make dispute resolution tilted in their favour, not yours. They should not.
Then, let's take Principle 2, testing the evidence functionality. The problem with this is that, in software production, testing is always the little lost runt of the litter. Everyone says they will look after her, and promise to do their best, but when it matters, she's just the little squealing nuisance underfoot. Testing always gets left behind, locked in the back room with the aunt that nobody wants to speak to.
But we can take a more systemic view. What us financial cryptographers do for this situation is to flip it around. Instead of repeating the marketing blather of promises of more testing, we make the test part of the protocol. In other words, the only useful test is one that is done automatically as part of the normal routine.
P2. Evidence is part of the protocol.
You can see this with backups. Most backup problems occur because they were never actually used at the time they were created. So good backups open up their product and compare it back to what was saved. That is, part of the cycle is the test.
But we can go further. When we start presenting this evidence to the fraternity of dispute resolution we immediately run into another problem highlighted by the above words: "the designers should also specify, test and debug the procedures to be followed by police officers, defence lawyers and expert witnesses."
M&A were aware of cases such as the one discussed above, and seek to make the evidence stronger. But, the flaw in their proposal is that the process so promoted is *expensive* and it therefore falls into the trap of raising the costs of dispute resolution. Which make them commensurately less effective and less available, which breaches P1.
And to segway, Principle 3 above also fails to the same economic test. If you do provide all that good open TCB stuff, you now need to pull in expert witnesses to attest to the model. And one thing we've learnt over the years is that TCBs are fertile ground for two opposing expert witnesses to disagree entirely, both be right, and both be exceedingly expensive. As before, this approach increases the cost, and therefore reduces the availability of dispute resolution, and thus breaches P1. And, it should be noted that a developing popular theme is that standards and TCBs and audits and other big-costing complicated solutions are used as much to clobber the user as they are to achieve some protection. The TCB is always prepared in advance by the bank, so no prizes for guessing where that goes; the presence of the institution-designed TCB is as much antithetical to the principles of protection of the user, so it can have no place in principles.
Now, combining these points, it should be clear that we want to get the costs down. I can now introduce a third principle:
P3: The evidence is self-evident.
That is, the evidence must be self-proving, and it must be easily self-proving to the judge, who is no technical wizard. This standard is met if the judge can look at it and know instantly what it is, and, likewise, so can a jury. This also covers Principle 5. For an example of P3, look at the Ricardian Contract, which has met this test before judges.
Principle 4 is likewise problematic. It assumes so much! Being able to evidence a fraud, but not stop it is a sort of two-edged sword. Indeed, it assumes so much of an understanding of how the system is attacked that we can also say that if we know that much about the fraud, we should be able to eliminate it anyway. Why bother to be evidence-protected when we can stop it?
So I would prefer something like:
P4: The system is designed to reduce the attack surface areas, and where an attack cannot be eliminated, it should be addressed with a strong evidence trail.
In other words, let's put the horse before the cart.
Finally, another point I would like to bring out which might now be evident from the foregoing, is this:
P5: The system should be designed to reduce the costs to both parties, including the costs and benefits of dispute resolution.
It's a principle because that is precisely what the banks are not doing; without taking this attitude, they will also then go onto breach P1. As correctly pointed out in the paper, banks fight these cases for their own profit motive, not for their customers' costs motives. Regulation is not the answer, as raising the regulatory barriers plays into their hands and allows them to raise prices, but we are well out of scope here, so I'll drift no more into competition. As an example of how this has been done, see this comparison between the systems designed by CAcert and by Second Life. And, Steve Bellovin's "Why the US Doesn't have Chip-and-PIN Credit Cards Yet," might be seen as a case study of P5.
In conclusion, it is very encouraging that the good work that has been done in dispute resolution for payment systems now has a chance of being recognised.
But it might be too early for the principles as outlined, and as can be seen above, my efforts scratched out over a day are somewhat different. What is going to be interesting is to see how the Bitcoin space evolves to deal with the question, as it already has mounted some notable experiments in dispute resolution, such as Silk Road. Good timing for the paper then, and I look forward to reports of lively debate at FC in Barbados, where it is presumably to be presented.
February 09, 2014
Digital Evidence journal is now open source!
 Stephen Mason, the world's foremost expert on the topic, writes (edited for style):
Stephen Mason, the world's foremost expert on the topic, writes (edited for style):
The entire Digital Evidence and Electronic Signature Law Review is now available as open source for free here:Current Issue Archives All of the articles are also available via university library electronic subscription services which require accounts:
EBSCO Host HeinOnline v|lex (has abstracts) If you know of anybody that might have the knowledge to consider submitting an article to the journal, please feel free to let them know of the journal.
This is significant news for the professional financial cryptographer! For those who are interested in what all this means, this is the real stuff. Let me explain.
Back in the 1980s and 1990s, there was a little thing called the electronic signature, and its RSA cousin, the digital signature. Businesses, politicians, spooks and suppliers dreamed that they could inspire a world-wide culture of digitally signing your everything with a hand wave, with the added joy of non-repudiation.
They failed, and we thank our lucky stars for it. People do not want to sign away their life every time some little plastic card gets too close to a scammer, and thankfully humanity had the good sense to reject the massively complicated infrastructure that was built to enslave them.
However, a suitably huge legacy of that folly was the legislation around the world to regulate the use of electronic signatures -- something that Stephen Mason has catalogued here.
In contrast to the nuisance level of electronic signatures, in parallel, a separate development transpired which is far more significant. This was the increasing use of digital techniques to create trails of activity, which led to the rise of digital evidence, and its eventual domination in legal affairs.
Digital discovery is now the main act, and the implications have been huge if little understated outside legal circles, perhaps because of the persistent myth in technology circles that without digital signatures, evidence was worth less.
Every financial cryptographer needs to understand the implications of digital evidence, because without this wisdom, your designs are likely crap. They will fail when faced with real-world trials, in both senses of the word.
I can't write the short primer on digital evidence for you -- I'm not the world's expert, Stephen is! -- but I can /now/ point you to where to read.That's just one huge issue, hitherto locked away behind a hugely dominating paywall. Browse away at all 10 issues!
May 06, 2013
What makes financial cryptography the absolutely most fun field to be in?
Quotes that struck me as on-point: Chris Skinner says of SEPA or the Single-European-Payment-Area:
One of the key issues is that when SEPA was envisaged and designed, counterparty credit risk was not top of the agenda; post-Lehman Brothers crash and it is.
What a delight! Oh, to design a payment system without counterparty risk ... Next thing they'll be suggesting payments without theft!
Meanwhile Dan Kaminsky says in delicious counterpoint, commenting on Bitcoin:
But the core technology actually works, and has continued to work, to a degree not everyone predicted. Time to enjoy being wrong. What the heck is going on here?First of all, yes. Money changes things.
A lot of the slop that permeates most software is much less likely to be present when the developer is aware that, yes, a single misplaced character really could End The World. The reality of most software development is that the consequences of failure are simply nonexistent. Software tends not to kill people and so we accept incredibly fast innovation loops because the consequences are tolerable and the results are astonishing.
BitCoin was simply developed under a different reality.
The stakes weren’t obscured, and the problem wasn’t someone else’s.
They didn’t ignore the engineering reality, they absorbed it and innovated ridiculously
Welcome to financial cryptography -- that domain where things matter. It is this specialness, that ones code actually matters, that makes it worth while.
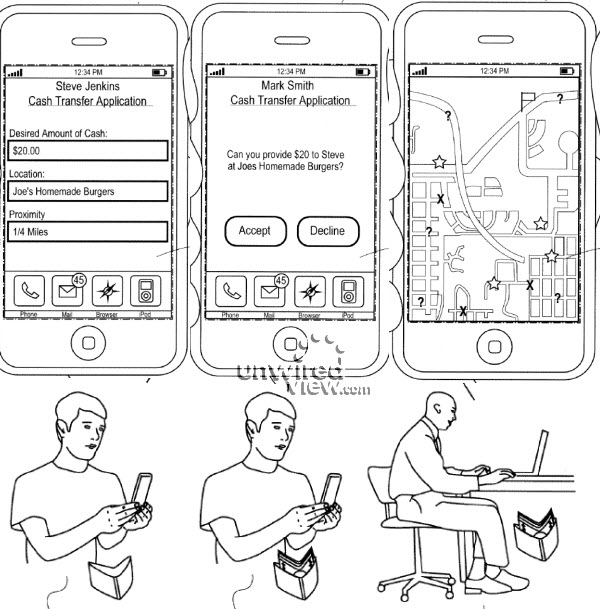
Meanwhile, from the department of lolz, comes Apple with a new patent -- filed at least.
The basic idea, described in a patent application “Ad-hoc cash dispensing network” is pretty simple. Create a cash dispensing server at Apple’s datacenter, to which iPhones, iPads and Macs can connect via a specialized app. Need some quick cash right now and there’s no ATM around? Launch the Cash app, and tell it how much do you need. The app picks up your location, and sends the request for cash to nearby iPhone users. When someone agrees to front you $20, his location is shown to you on the map. You go to that person, pick up the bill and confirm the transaction on your iPhone. $20 plus a small service fee is deducted from your iTunes account and deposited to the guy who gave you the cash.
The good thing about being an FCer is that you can design that one over beers, and have a good belly laugh for the same price. I don't know how to put it gently, but hey guys, don't do that for real, ok?!
All by way of saying, financial cryptography is where it's at!
May 01, 2013
MayDay! MayDay! British Banking Launches new crisis of titanic proportions...
 Yes, it's the first of May, also known as May Day, and the communist world's celebration of the victory over capitalism. Quite why MayDay became the international distress message over radio is not known to me, but I'd like to know!
Yes, it's the first of May, also known as May Day, and the communist world's celebration of the victory over capitalism. Quite why MayDay became the international distress message over radio is not known to me, but I'd like to know!
Meanwhile, the British Banking sector is celebrating its own version of MayDay:
The bank went through their customer base and identified which businesses were asset rich and cash poor.Typically, the SME (small to medium enterprise) would require funding for expansion or to cover short term exposures, and the bank’s relationship manager would work with the business owner on a loan funding cover.
The loan may be for five or ten years, and the relationship manager would often call the client after a short time and say “congratulations, you’ve got the funding”.
The business owner would be delighted and would start committing the funds.
Only then would the relationship manager call them back and say, “ah, we have a concern here about interest rates”.
This would start the process of the disturbance sale of the IRSA.
The rest you can imagine - the bank sold an inappropriate derivative with false information, and without advising the customer of the true costs. This time however the costs were more severe, as it seems that many such businesses went out of business in whole or in part because of the dodgy sale.
In particular, the core issue is that no-one has defined whether the bank will be responsible for contingent liabilities.The liabilities are for losses made by those businesses that were mis-sold these products and, as a result, have now gone into bankruptcy or been constrained so much that they have been unable to compete or grow their business as they would have if they had not taken these products.
 Ouch! I have to applaud Chris Skinner and the Financial Services Club here for coming forth with this information. It is time for society to break ranks here and start dealing with the banks. If this is not done, the banks will bring us all down, and it is not clear at all that the banks aren't going to do just that.
Ouch! I have to applaud Chris Skinner and the Financial Services Club here for coming forth with this information. It is time for society to break ranks here and start dealing with the banks. If this is not done, the banks will bring us all down, and it is not clear at all that the banks aren't going to do just that.
Meanwhile back to the scandal du jour. We are talking about 40k businesses, with average suggested compensation of 2.5 million quid - so we are already up to a potential exposure of 100 billion pounds. Given this, there is no doubt that even the most thickest of the dumbest can predict what will happen next:
Mainly because of the Parliamentary investigation, the Financial Services Authority was kicked into action and, on June 29 2012, announced that it had found "serious failings in the sale of IRSAs to small and medium sized businesses and that this has resulted in a severe impact on a large number of these businesses.”However, it then left the banks to investigate the cases and work out how to compensate and address them .
The banks response was released on January 31 2013, and it was notable that between the June announcement and bank response in January that the number of cases rose from 28,000 to 40,000. It was also noteworthy that of those 40,000 cases investigated, over 90% were found to have been mis-sold. That’s a pretty damning indictment.
Even then the real issue, according to Jeremy [of Bully Banks], is that the banks are in charge of the process.
Not only is the fox in charge of the chickens, it's also paying off them off for their slaughter. Do we really need to say more? The regulators are in bed with the banks in trying to suppress this scandal.
Obviously, this cunning tactic will save poor banks money and embarrassment. But the emerging problem here is that, as suggested many times in this blog (e.g., 2, 3, 4, ...) and elsewhere, the public is now becoming increasingly convinced that banks are not healthy, honest members of society.
 Which is fine, as long as nothing happens.
Which is fine, as long as nothing happens.
But I see an issue emerging in the next systemic shock to hit the financial world: if the public's patience is exhausted, as it appeared to be over Cyprus, then the next systemic shock is going to cause the collapse of some major banks. For right or wrong, the public is not going to accept any more talk of bailouts, taxpayer subsidies, etc etc.
The chickens are going to turn on the foxes, and they will not be satisfied with anything less than blood.
One hopes that the old Lady's bank tear-down team is boned up and ready to roll, because they'll be working hard soon.
February 18, 2012
one week later - chewing on the last morsel of Trust in the PKI business
After a week of fairly strong deliberations, Mozilla has sent out a message to all CAs to clarify that MITM activity is not acceptable.
 It would seem that Trustwave might slip through without losing their spot in the root list of major vendors. The reasons for this is a combination of: up-front disclosure, a short timeframe within which the subCA was issued and used (at this stage limited to 2011), and the principle of wiser heads prevailing.
It would seem that Trustwave might slip through without losing their spot in the root list of major vendors. The reasons for this is a combination of: up-front disclosure, a short timeframe within which the subCA was issued and used (at this stage limited to 2011), and the principle of wiser heads prevailing.
That's my assessment at least.
My hope is that this has set the scene. The next discovery will be fatal for that CA. The only way forward for a CA that has issued at any time in the past an MITM-enabled subCA would be the following:
+ up-front disclosure to the public. By that I mean, not privately to Mozilla or other vendors. That won't be good enough. Nobody trusts the secret channels anymore.
+ in the event that this is still going on, an *fast* plan, agreed and committed to vendors, to withdraw completely any of these MITM sub-CAs or similar arrangements. By that I mean *with prejudice* to any customers - breaching contract if necessary.
Any deviation means termination of the root. Guys, you got one free pass at this, and Trustwave used it up. The jaws of Trust are hungry for your response.
That is what I'll be looking for at Mozilla. Unfortunately there is no forum for Google and others, so Mozilla still remains the bellwether for trust in CAs in general.
That's not a compliment; it's more a description of how little trust there is. If there is a desire to create some, that's possibly where we'll see the signs.
September 25, 2009
Where does anyone (young) want to go, today?
I got some good criticism on the post about accounting as a profession. Clive said this which I thought I'd share:
As an engineer who's father was an accountant I will give you three guesses as to what he told me not to do when I grew up... Oddly it is the same for engineers, we tend to tell our children to do other things. As I've said before if you want to get on in life you should learn to speak the language that the man who cuts your cheque at the end of the month does, or more correctly his boss ;)So even if you are just a humble team leader get yourself three courses,
- MBA,
- Vocal training,
- Psychology or Method acting.
And no I'm not joking about 3.
He's talking about what we do when we get to 30 and beyond, e.g., most readers of this blog. For us older folks looking back, it is depressing that the world looks so sucky; but this is a time-honoured thing. The myths have been stripped away, the rot revealed.
But the youth of today is perpetually optimistic, and the question they ask is eternal and (Spence-like) opinionated: what to study, first?
What then do we recommend for a first degree for someone near 20? It seems that nobody promotes the accountancy field, including the incumbents. Accountants don't practice accountancy, if they are any good. The only accountant I ever knew well committed suicide.
An MBA doesn't work, this is something that should be done after around 5-10 years of experience. Hence, I'm not convinced a straight business degree ("Bachelors in Business Studies" ?) makes sense either, because all that additional stuff doesn't add value until experience is there to help it click into place.
I wouldn't suggest economics. It is like law and accounting, in that it helps to provide a very valuable perspective throughout higher business planes. But it doesn't get you jobs, and it is too divorced from practical life, too hard to apply in detail. Engineering seems far too specialised these days, and a lot of it is hard to work in and subject to outsourcing. Science is like engineering but without the focus.
To my mind, the leading contenders as a first degree are (in no particular order):
⇒ law,
⇒ computer science,
⇒ biotech, and
⇒ marketing.
Firstly, they seem to get you jobs; secondly, law, compsci and marketing are easy to apply generally and broadly, and pay dividends throughout life. I'm not quiet sure about Biotech in the "broad" sense, but it is the next big thing, it is the wave to ride in.
Comp sci was the wave of the 1980s and 1990s. Now it is routine. Any technical degree these days tends to include a lot of comp sci, so if there is a tech you enjoy, do that degree and turn it into a comp sci degree on the inside.
 Law is in my list because it is the ultimate defensive strategy. Headline Law tends to offend with its aggressively self-serving guild behaviour ("a man who represents himself has a fool for a client and a fool for a lawyer") and as a direct practice (courts) the field seems made for crooks. More technically, all disputes are win-lose by definition, and therefore litigation is destructive by definition, not productive. This is offensive to most of humanity.
Law is in my list because it is the ultimate defensive strategy. Headline Law tends to offend with its aggressively self-serving guild behaviour ("a man who represents himself has a fool for a client and a fool for a lawyer") and as a direct practice (courts) the field seems made for crooks. More technically, all disputes are win-lose by definition, and therefore litigation is destructive by definition, not productive. This is offensive to most of humanity.
But litigation is only the headline, there are other areas. You can apply the practical aspects of law in any job or business, and you can much more easily defend yourself and your business against your future fall, if you have a good understanding of the weapons of mutual destruction (a.k.a. lawsuits). About half of the business failures I've seen have occurred because there was no good legal advisor on the team; this is especially true of financial cryptography which is why I've had to pick up some of it; what one person I know calls "bush lawyering."
The downside to studying law is that you can lose your soul. But actually the mythology in law is not so bad because it is grounded in fundamental rights, so keep those in mind, and don't practice afterwards. It's nowhere near as bad as the computing scene (no grounding at all, e.g., open source) or the marketing blah blah (your mission is to unground other's perceptions!).
Marketing is there because every successful business needs it, and you can only be successful with it. MBAs are full of marketing, which reflects its centrality (and also gives a good option for picking it up later). But marketing is also dangerous because it gives you the tools to fool yourself and all around you, and once you've become accustomed to the elixir, your own grounding is at risk.
I don't advise any of the arts (including Clive's points 2,3) as a primary degree for youth, because businesses hire on substance, so it is important to have some to offer. E.g., people who study psychology tend to end up doing HR ("human resources"), badly, perhaps because they lack the marketing sense to make HR the most important part of the business.
Likewise, avoid anything that is popular, soft, fun, nice and that all your touchy-feely friends want to do. When there are too many people and too little substance, the competition suppresses everyone and makes you all poor. That's the best result because at least it is honest; a very few dishonest ones become rich because they figure out the game. The notion that you can study acting, media, history, photography or any of the finer arts, and then make a living, doesn't bear talking about. It is literally gambling with lives, and has no place in advice to young people.