December 21, 2013
Dan Bernstein rises to the Shamir-Grigg-Gutmann challenge: show me the money!
In an invited talk at the March 2013 FSE in Singapore, Dan Bernstein highlighted a challenge expressed in distinct ways:
2011 Grigg-Gutmann: In the past 15 years "no one ever lost money to an attack on a properly designed cryptosystem (meaning one that didn't use homebrew crypto or toy keys) in the Internet or commercial worlds".2002 Shamir: "Cryptography is usually bypassed. I am not aware of any major world-class security system employing cryptography in which the hackers penetrated the system by actually going through the cryptanalysis."
H/t to Twan for pointing this presentation out. DJB then went on to ask about this challenge:
- Do these people mean that it's actually infeasible to break real-world crypto?
- Or do they mean that breaks are feasible but still not worthwhile for the attackers?
- Or are they simply wrong: real-world crypto is breakable; is in fact being broken; is one of many ongoing disaster areas in security?
Fair questions, one supposes! Let's break it down.
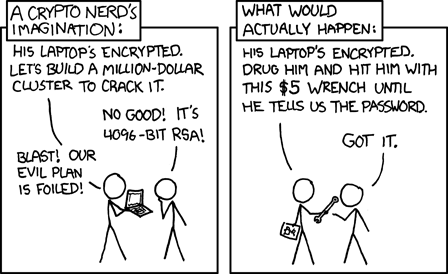
Adi Shamir stated that "Cryptography is usually bypassed." From this, we can suggest that the security job in real life is typically done if the economic results of attacking the crypto happens to be less than the economic results of some other attack.
This is the old sage advice about your door locks -- they don't have to be great, they just have to be better than your neighbours' locks.
This assumes several things: that for the particular business of real life, most of us aren't typically aware of who our attacker is, and further, that any attacker is economically motivated. That is, they want to steal money, by one means or another, and they are not motivated necessarily by the more esoteric of threats that us geeks wish we had to take seriously: revenge, espionage, sabotage, massive crunching farms, exploitation of deep bugs, etc.
Further, it assumes that we are all doing risk analysis. So it's about money, in the simplified world of general purpose crypto. Which brings us to the more practical question:
how strong shall a system be?
There are two answers: the cryptographer's answer and the business answer. The former's answer is: infeasible to break.
The latter's answer is more nuanced, and in order to understand that answer we have to get into how business operates.
In the world of business, we do risk analysis. In quick words, this starts from a model of the business, and from business experience we posit a model of threats. Then, we use risk analysis to estimate the likelihood of each threat, by looking at history and expected cost to the attacker, and multiply it by the consequences (a.k.a. monetary damages) to us to get an expected value.
risk = likelihood * consequences
The result is a set of risks, which we can then order by expected damages. We then start working on the highest priorities, being the highest expected damages. And, similar to our lock model, as long as the priorities are mitigated such that the attacker feels it more economic to move elsewhere, we're good.
In even shorter words, we concentrate our defences where we are currently losing money. It is therefore all about money, which is a completely different answer to the cryptographer's answer of infeasible to break.
So, what about the money? Now, as it happens, in the Internet, there is remarkably little reporting of money being stolen by breaching a cryptosystem! Which leaves us with a dilemma. If nobody has ever reported any money, why are we bothering to protect?
Hence the Gutmann-Grigg comment that puts the point: "no one ever lost money..." and we have the answer to the first two questions:
- Do these people mean that it's actually infeasible to break real-world crypto?
NO!- Or do they mean that breaks are feasible but still not worthwhile for the attackers?
YES!
Now we can address the third question. We can probably state with some confidence that someone has lost some money, somewhere, from some attack on a crypto system, but has never reported those losses. So we now must ask what do we do about non-reported losses?
The answer to that is clear: nothing.
Unreported losses don't exist. The reason for this is simple: risk analysis is based on what we know. What we don't know is not a good basis for assessing risks. In the crypto business, we refer to this as FUD, security theatre, snake oil, bogeymen, bla bla, movie plots, perverted & interested parties, etc. If we rely on a claim that we cannot show then we are lost, totally. If we work on a hypothetical, we're not doing risk analysis, we're not doing science, and we've no integrity. Hence, the answer to the third question,
- Or are they simply wrong: real-world crypto is breakable; is in fact being broken; is one of many ongoing disaster areas in security?
"show us the money!"
This is really what the challenge is about. Because if you can't do that, you're doing something other than business. Call it cryptography or call it voodoo, it doesn't really matter, because only business is business, business is about analysing risks, and you can't analyse risks without facts. Chief amongst those facts is how much money is lost.
Which many have tried to do, gamely, and failed (look at the history of SB1386, in which the reported losses were most or all attributed to non-crypto, non-thefts). Dan also:
Let's look at some examples.
Having established what we all meant by those challenges, I'll leave Dan's examples to another post.
ps; this post was written by Iang. Peter and Adi have not actually written a word here, so any errors in interpretation of their position are mine and mine alone.
Posted by iang at December 21, 2013 11:00 AM | TrackBack