February 08, 2005
4 Corners in Identity
Adam & Michael discovered Stefan Brands' new blog called the Identity Corner. Stefan is of course the cryptographer who picked up from David Chaum and created a framework of mathematical formulas to deliver privacy control. Stefan's formulas as described in his book are rather complete, way too complete for all except talented mathematicians to understand, but his introductory 1st chapter remains a landmark in privacy literature.
Stefan points at another Identity blog, which postulates something called the Laws of Identity. For my money, there are too many MUSTs in the list to be reasonable.
Especially, I think a description like Zooko's Triangle is a much clearer starting point. Zooko says that we can have any two of the following three: decentralised, secure and human meaningful. But we can't have all three; he put forth a challenge to prove him wrong and to date nobody's managed to do that.
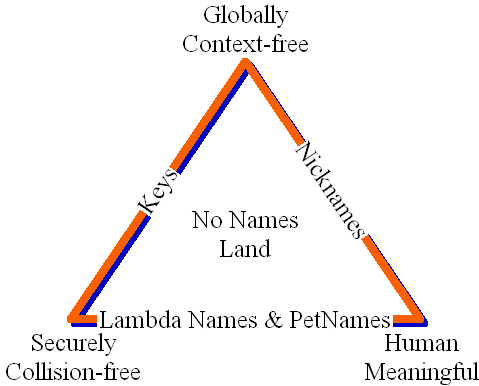
Which of course brings us to Ricardo, which chooses secure and decentralised as its requirements (as have a lot of other systems, see the link for a list). That's because each client can then do a more or less transparent mapping for the user; although the problems that occur with this have sparked some thoughts and designs. In Ricardo we have generally told the user what contracts are named and let the user choose their account names, but there is a more powerful way to solve this is: use pet names.
These are words or phrases that the user chooses herself to label things her software agent knows about. Because the user invented the name, by herself, she and her agent are the only ones who know. So when a secure global name turns up trying to phish her, the hope is that the absence of any familiar pet name will complete the security model conundrum left by Zooko above.
So far so good, and if you've kept pace with the phishing season, this is analogous to what Amir & Ahmad propose for site logos - except with logos and images rather than words. It's *not* analogous to what I propose with branded CAs (also adopted in A&A's paper) but that's because the CAs exist in a centralised, not global space - we don't need to drop the meaningful name then. (Put the two together and we have a quite powerful solution. It's the best I've seen so far at least.)

Which brings us full square back to Stefan who's proposals have little to do with the basic nymous technique that is pervasive in these concepts. It will be interesting to see how he integrates his proposals with those behemoths of PKI and the replacement, Federated Identity.
Posted by iang at February 8, 2005 07:08 PM | TrackBack